
Linux Permissions for System Administrators and Developers
The issue of permissions in Linux and its correct use through the "chmod" command is something very commonly exposed and discussed in the SL Communities. by Advanced Users, Technicians and Administrators of Servers and Systems. For example in our Blog we have 2 very good publications about it, which are: Permissions and Rights in Linux (01/12) y Basic permissions in GNU / Linux with chmod (08/16).
But many times SW Developers who are the ones who create the Applications and Systems, most of them Systems and Websites, when developing them, they do not usually consider which are the correct permissions to be implemented on them, leaving the task almost always on the side of the Server and System Administrators. In this publication we will try to give a little orientation about it for them.

Introduction
The command "chmod»Is very useful and important for advanced use of Linux-based Operating Systems. However, as such "chmod" is not a standalone package, but is integrated into the package "coreutils«. The "coreutils" package is a package that provides the Operating System with many basic tools for file management, command interpreters, and word processing. And in general, it is already installed by default in most Linux Distros.
Specifically, this package contains, in addition to the "chmod" command, the following commands: arch base64 basename cat chcon chgrp chmod chown chroot cksum comm cp csplit cut date dd df dir dircolors dirname du echo env expand expr factor false flock fmt fold groups head hostid id install join link ln logname ls md5sum mkdir mkfifo mknod mktemp mv nicec noh noh numfmt od paste pathchk pinky pr printenv printf ptx pwd readlink realpath rm rmdir runcon sha * sum seq shred sleep sort split stat stty sum sync tac tail tee test timeout touch tr true truncate tsort tty uname unexpand uniq unlink users vdir wc who whoami yes.
In summary, the "chmod" command allows the all-important task of managing file and folder permissions to all users managed by the Operating System. This is because Linux as an Operating System is multi-user, and therefore, it needs to provide the work environment with a permission system to control the set of authorized operations on files and directories, which includes all system resources and the devices.
Contents
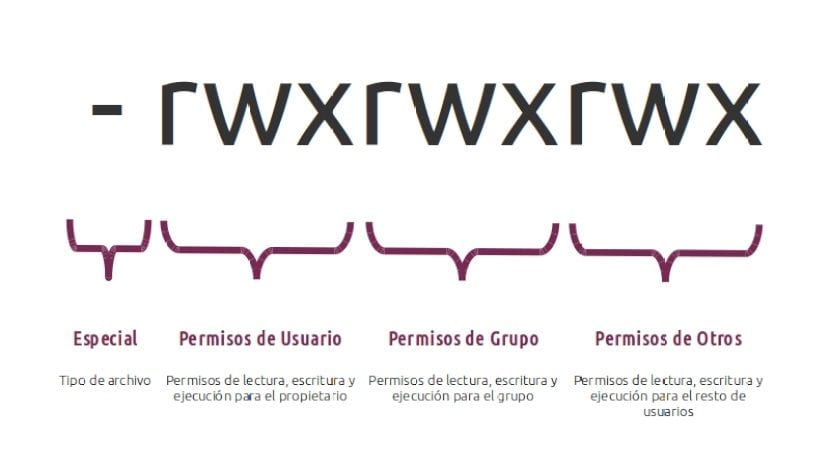
Use for SW Developers
A Server and Systems Administrator (Sysadmin) when deciding what permissions to grant a X-level User or profile on X file or folder, needs to know exactly what type of operations or processes they need to perform on them. In the case of a Web Server, Users can be classified into 2 types:
- Admin Users: Who have a user account on the server to log in, have specific privileges, and who generally carry out certain changes (copy / delete / modify) in the System or Website installed via SSH or SFTP, for example.
- Non-Administrator Users: That they do not have a user account on the server, since they are only visitors to the Site and Web System. And therefore, they do not have permissions to access files and folders directly, but rather interact with them, through the web interface of the Site or installed Web System.
However, when a Sysadmin does not receive enough or adequate information, documentation, or support by SW Developers on the capabilities, functionalities or file structure of the Web Sites and Systems to be installed ends up executing the reliable maximum, which in this case is usually:
chmod 777 -R /var/www/sistema-webAnd many times it ends with:
chown root:root -R /var/www/sistema-web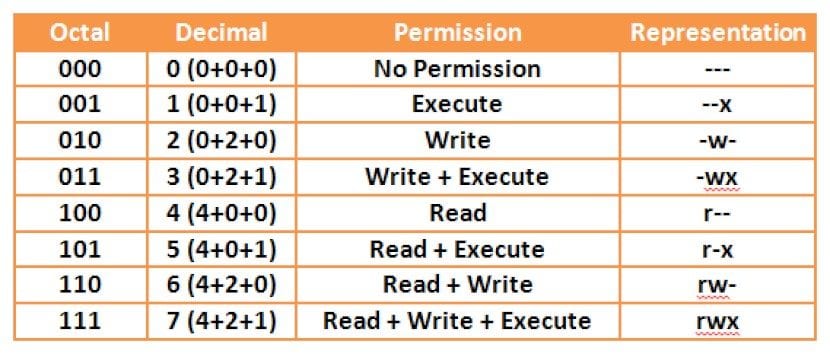
Warning
This is usually a bad practice, but it usually avoids any problem of permission and bad execution of the installed Web Sites and Systems. A bad practice, since when the command chmod 777 is executed in this way on the folder and files of a Site or Web System, there is no security at all about it.
Making it possible for any user of the Site or Web System online to change or delete any file within the file structure of the Site or Web System within the Web Server or beyond, without major obstacles. Since it must be remembered that it is the Web Server that acts on behalf of the visiting users, and that it is capable of changing the same files that are being executed.
And in case the user is an attacker, and gets some vulnerability in the Site or Web System, he could easily exploit it to deface it, disable it, or worse yet, insert malicious code to execute phishing attacks, or steal information from the server without anyone easily knowing.
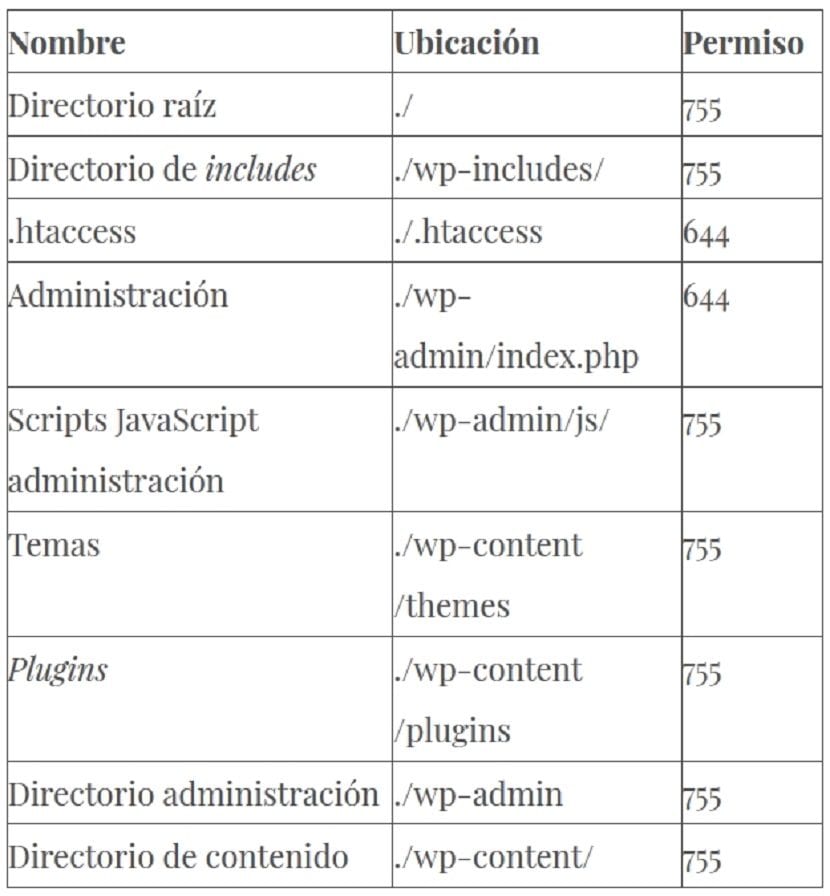
Recommendations
To avoid these types of measures, either The Sysadmin or the SW Developer, must ensure that the folders and files of the various Systems or Websites carry the correct and necessary permissions and users to avoid future security and privacy issues.
At the permission level, the following 3 commands can be carried out to restore the permissions and users of an installed System or Website to normal., that is, set the value 755 to all directories and 644 to files.
Always remembering to execute them within the System or Website folder, since if they are executed in a higher folder (directory), such as, for example, the server's root, the command commands will recursively modify all the Server's permissions, leaving it most likely inoperative.
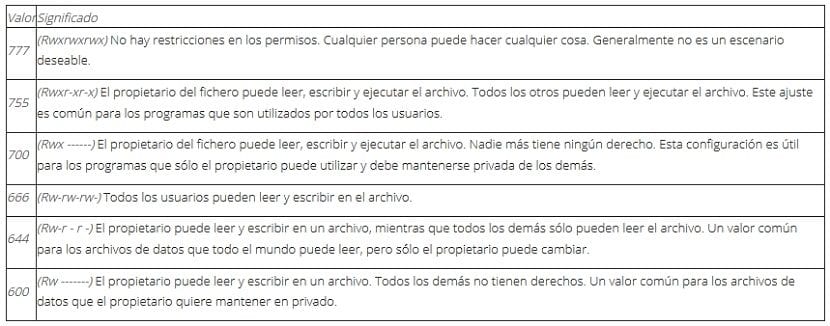
Permissions applied to Folders (Directories)
Examples
Directories and files permissions
find . -type d -exec chmod 755 {} \;find . -type f -exec chmod 644 {} \;y
chmod 777 -R .o
chmod 777 -R /var/www/sistema-webIn case of being outside the folder (directory) of the System or Website.
System or Website Users
chown www-data:www-data -R .o
chown www-data:www-data -R /var/www/sistema-webIn case of being outside the folder (directory) of the System or Website. And the user www-data is only used as an example, since it is the most used or suitable as far as the use of Apache2 is concerned.

Permissions applied to Files (Files)
Once the permissions changes have been made, we can proceed to modify the permissions of the directories and files that we want to have different permissions manually. And if it is necessary to also change the owner users of the necessary ones. Therefore, at this point, both the Sysadmin and the SW Developers must agree on what the necessary permissions should be for each folder and file in the System or Website structure.
Conclusion
The administration of the permissions on the files and folders of the Linux or UNIX operating systems, is one of the great advantages and benefits of the same, since they allow a better, precise and safe control of the different levels of access, edition and execution on the files and folders.
And much more, when it comes to the level of Web Servers, that is, where the Systems or internal and external Websites of an Organization are hosted, since it is a higher priority to know what permissions should be assigned to each directory or file, to achieve the best balance between privacy, security and functionality.
Good morning how are you?
I'm dabbling in linux, I have an application that can import files from it, the user uploads a .zip containing a folder with xml files, after unzipping the files they are inserted into the database. In windows I have no problems, when passing the application to linux I would be missing some permissions, in principle to test everything I have done what they say in this article and it should not be done haha (but I will change once I can validate all the functionalities) .
The fact is that the files are decompressed but I see that they are downloaded only with read and write permissions for the owner, read for the owner group and without permissions for others. When the files are owned by the user who uses the application. I understand that by not having the execution permissions, it is not being able to follow the normal flow of the process and proceed to insert the xml in the database. To which my question comes, how can I give permissions to files that I do not have on the system yet? In the folder that is downloaded (tmp) it has all the permissions, it is applied in a re-italic way but each time files are downloaded within that folder they only have the permissions mentioned. Is there any way that the files that appear in that folder can be left with execute permissions as well?
I hope I have been clear, thank you very much in advance and excellent blog
I assume that the folder / tmp or… / tmp has 755 permissions but even so when the user who owns the application deposits them, he leaves them with other permissions. I am not a developer but I assume that in the language of the application or another one could indicate to it a routine that executes the command command (bash) of the necessary permissions (chmod) and the owner of the files (chown). Otherwise, you could run a script every minute it runs.