Few days ago a surprisingly simple method was released that allows attacking dependencies in applications which are developed using internal package repositories. The researchers who identified the problem they were able to run your code on the internal servers of 35 companies, including PayPal, Microsoft, Apple, Netflix, Uber, Tesla, and Shopify.
The hacks were carried out as part of the Bug Bounty programs, in coordination with the attacked companies, and the perpetrators have already received $ 130.000 in bonuses for identifying vulnerabilities.
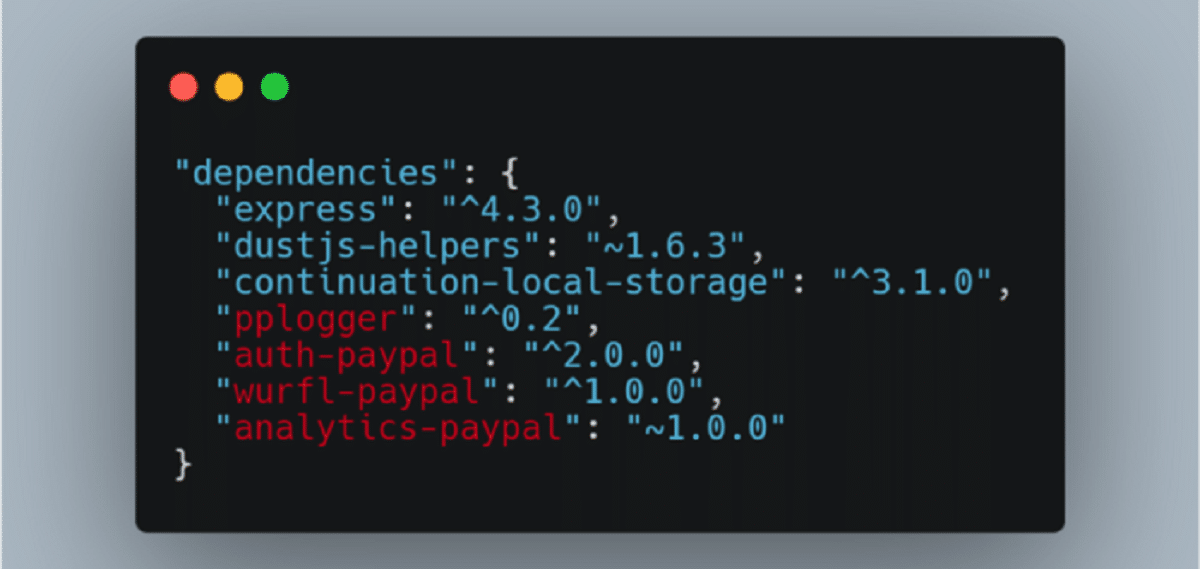
The method is based on the fact that many companies use standard repository dependencies of NPM, PyPI and RubyGems in their internal applications, as well as internal dependencies that are not publicly distributed or downloaded from their own repositories.
The problem is that package managers like npm, pip and gem They try to download the internal dependencies of the companies, even from the public repositories. For an attack, just define the names of the packages with internal dependencies and create your own packages with the same names in the public repositories of NPM, PyPI and RubyGems.
The problem is not specific to NPM, PyPI, and RubyGems, and it also manifests itself on other systems such as NuGet, Maven, and Yarn.
The idea for the proposed method came after a researcher accidentally noticed that in publicly available code posted on GitHub, many companies do not remove the mention of additional dependencies from their manifest files used in internal projects or when implementing extended functionalities. Similar traces have been found in the JavaScript code of web services, as well as in the Node.JS, Python, and Ruby projects of many companies.
The main leaks were related to the embedding of the content from the package.json files in publicly available JavaScript code during the build process, as well as with the use of actual path elements in require () calls, which can be used to judge dependency names.
Scanning of several million corporate domains revealed several thousand JavaScript package names which were not in the NPM repository. Having compiled a database of internal package names, the researcher decided to conduct an experiment to hack the infrastructure of companies participating in Bug Bounty programs. The results were surprisingly effective and the researcher was able to run his code on many development computers and servers responsible for building or testing based on continuous integration systems.
When downloading dependencies, the package managers npm, pip, and gem mainly installed packages from the primary public repositories NPM, PyPI, and RubyGems, which were considered higher priority.
The presence of similar packages with the same names in private company repositories was ignored without showing any warning or causing crashes that could attract the attention of administrators. In PyPI, the download priority was influenced by the version number (regardless of the repository, the most recent version of the package was downloaded). In NPM and RubyGems, the priority was only repository dependent.
The researcher has placed packages in repositories of NPM, PyPI and RubyGems that cross the names of the found internal dependencies, adding code to the script that runs before installation (pre-installed in NPM) to collect information about the system and send the information received to the external host.
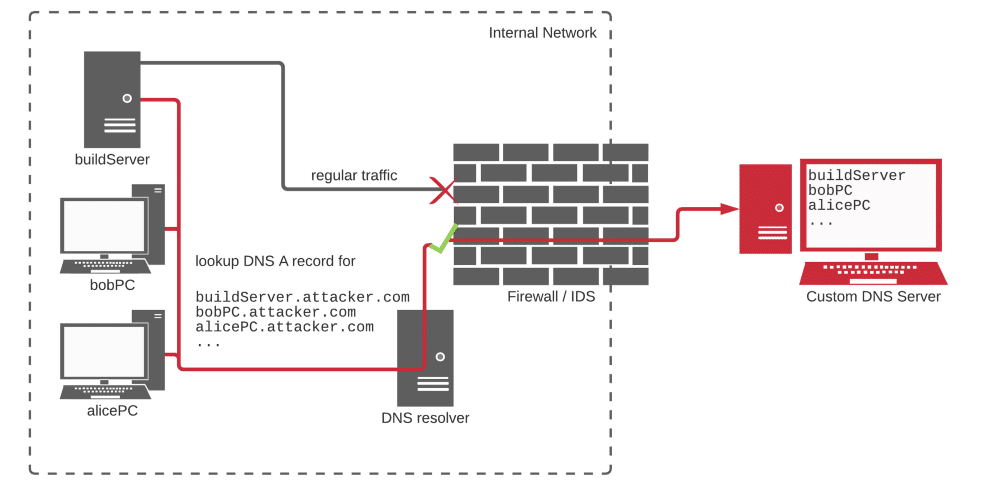
To convey information on the success of the hack, bypass firewalls blocking external traffic, the method of organizing covert channel communications over the DNS protocol. The code that was running resolved the host in the attacking domain under the control of the attacking domain, which made it possible to collect information about successful operations on the DNS server. Information about host, username and current path was passed.
75% of all recorded code executions were associated with NPM package downloads, primarily due to the fact that there were significantly more internal JavaScript module names than Python and Ruby dependency names.
Source: https://medium.com/