Let's suppose that for some reason we cannot access our server with a terminal, because perhaps, we are walking down the street and we only have our cell phone on top, and since we are not geeks or anything, we have not installed any application of this type .
Then what do we do? Well, nothing, we cannot do anything until we get home or work, access our server and install shellinabox. But what is that, do you eat?
shellinabox
shellinabox implements A server web that can to export line tools command to a terminal emulator web-based. This emulator it is accessible from any browser that supports JavaScript and CSS y it does not require No kind of Plugin additional to function.
Although the original project was discontinued, there are a fork on Github that allows us to install it if we don't have it in the repositories. In the case of Ubuntu 14.04 it is, so we just have to open a terminal and put:
$ sudo apt install shellinabox openssl ca-certificates
In the case of the last two packages, it is in case we do not already have them installed. And once this is done, we can now access our terminal on the web by putting in the browser:
http://la_ip_o_nombre_del_servidor:4200
Use Shellinabox through port 80
As you can see, by default Shellinabox uses the port 4200 and we may not be able to access it if it is blocked by our service provider. We can use a variant that is unsafe but works, which is to use shellinabox By the port 80, although later I will show how to use the 443 if we have it available.
What we will do is access Shellinabox by putting in our browser:
http://la_ip_o_nombre_del_servidor/terminal
To do this, the first thing we do is install NGinx:
$ sudo apt install nginx
Now we create the file / etc / nginx / sites-enabled / shellinabox and we put it inside:
server {proxy_set_header Host $ http_host; proxy_set_header X-Forwarded-Host $ http_host; proxy_set_header X-Real-IP $ remote_addr; proxy_set_header X-Forwarded-For $ proxy_add_x_forwarded_for; location / terminal / {proxy_pass http: // localhost: 4200 /; }}
We edit the file / etc / default / shellinabox and we put at the end:
SHELLINABOX_ARGS="--localhost-only --disable-ssl"
We reboot Nginx y shellinabox:
$ sudo /etc/init.d/shellinabox restart $ sudo /etc/init.d/nginx restart
And ready!!
Use Shellinabox through port 443
This process is a bit more cumbersome, because we have to create our SSL certificates. For this we will do the following:
First we install OpenSSL:
$ Apt-get install openssl
We create a private key:
openssl genrsa -out server.key 2024
We create the base of the certificate, where we will put a series of data:
openssl req -new -key server.key -out server.csr
The data that we will fill in will be:
- Country Name (2 letter code): Country code in two-letter ISO format (eg: ES, US, CU, MX ..).
- State or Province Name (full name): State or province (ex: Florida).
- Town Name: Town or city (ex: Miami).
- Organization Name: Name of the organization, (ex: DesdeLinux).
- Organizational Unit Name: Organization sector (ex: Blogs).
- Common Name: Domain name or FQDN. It is important to know that there is a difference between a blog.desdelinux.net and desdelinux.net. You must register the certificate for one, or the other.
- Email address: Contact email address.
- A challenge password: In white.
- An optional company name: In white.
Now we generate the SSL certificate, which will take the data we entered:
openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt
We copy the certificates to the SSL folder inside / etc:
$ sudo cp server.crt /etc/ssl/certs/ssl.crt $ sudo cp server.key /etc/ssl/certs/ssl.key
We edit the file again the file / etc / default / shellinabox and we change what we had put, putting at the end:
SHELLINABOX_ARGS="--no-beep"
Now we edit the file / etc / nginx / sites-enabled / shellinabox and we put it inside:
server {listen 80; return 301 https: // $ host $ request_uri; } server {listen 443; server_name myvps.com; ssl_certificate /etc/ssl/certs/ssl.crt; ssl_certificate_key /etc/ssl/certs/ssl.key; ssl on; ssl_session_cache builtin: 1000 shared: SSL: 10m; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_ciphers HIGH:! aNULL:! eNULL:! EXPORT:! CAMELLIA:! DES:! MD5:! PSK:! RC4; ssl_prefer_server_ciphers on; access_log /var/log/nginx/shellinabox.access.log; location / terminal {proxy_set_header Host $ host; proxy_set_header X-Real-IP $ remote_addr; proxy_set_header X-Forwarded-For $ proxy_add_x_forwarded_for; proxy_set_header X-Forwarded-Proto $ scheme; # Fix the “It appears that your reverse proxy set up is broken" error. Proxy_pass http: // localhost: 4200 /; proxy_read_timeout 90; proxy_redirect http: // localhost: 4200 https://myvps.com/terminal/;} }
We restart the services:
$ sudo /etc/init.d/shellinabox restart $ sudo /etc/init.d/nginx restart
and we access
http://la_ip_o_nombre_del_servidor/terminal
which should redirect us to:
https://la_ip_o_nombre_del_servidor/terminal
And that's it.
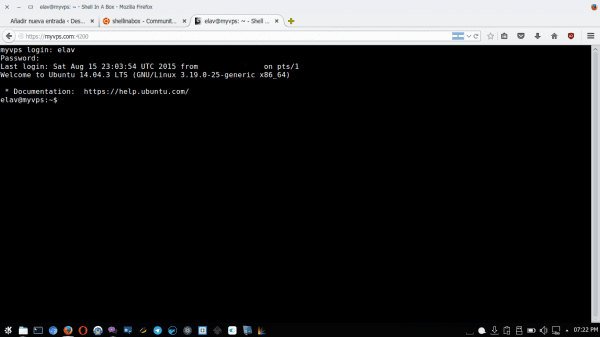
It reminded me of what comes out in the CSI series
A most interesting post; I had never heard of this utility and the truth is that it is most curious and useful ... I have to assume that just as this concept has been applied to Ngix, it can also be applied to Apache, right?
It reminds me of how Butterfly works, especially when using the terminal from the browser. Of course, not with as much complexity as what they show here 🙂
«Let's suppose that for some reason we cannot access our server with a terminal, because perhaps, we are walking down the street and we only have our cell phone on top, and since we are not geeks or anything, we have not installed any application of this kind."
How are we going to want to enter our server if we are not geeks? hahaha
It seems to me much faster to use an ssh app than to use a browser and you avoid installing software on the server, but it is still an interesting option.
Advantage when you are in a place with pure Windows.
"Advantage when you are in a place with pure Windows."
entoses ……………… putty or kitty.
excellent men this super thanks for the contribution