Researchers at the Free University of Amsterdam they made known recently found one new vulnerability that is an extended version of the Spectre-v2 vulnerability on Intel and ARM processors.
This new vulnerability, to which have baptized as BHI (Branch History Injection, CVE-2022-0001), BHB (Branch History Buffer, CVE-2022-0002) and Spectre-BHB (CVE-2022-23960), is characterized by allowing circumvention of the eIBRS and CSV2 protection mechanisms added to the processors.
The vulnerability is described in different manifestations of the same issue, as BHI is an attack that affects different privilege levels, for example, a user process and the kernel, while BHB is an attack at the same privilege level, for example , eBPF JIT and the kernel.
About vulnerability
Conceptually, BHI is an extended variant of the Spectre-v2 attack, in which to bypass additional protection (Intel eIBRS and Arm CSV2) and orchestrate data leakage, the substitution of values in the buffer with a global branch history (Branch History Buffer), which is used in the CPU for improve branch prediction accuracy by taking into account the history of past transitions.
In the course of an attack through manipulations with the history of transitions, conditions are created for the incorrect prediction of the transition and speculative execution of the necessary instructions, whose result is deposited in the cache.
With the exception of using a version history buffer instead of a version target buffer, the new attack is identical to Spectre-v2. The attacker's task is to create such conditions that the address, when performing a speculative operation, it is taken from the area of the data being determined.
After performing a speculative indirect jump, the jump address read from memory remains in the cache, after which one of the methods for determining the contents of the cache can be used to retrieve it based on an analysis of the change in cache access time and uncached data.
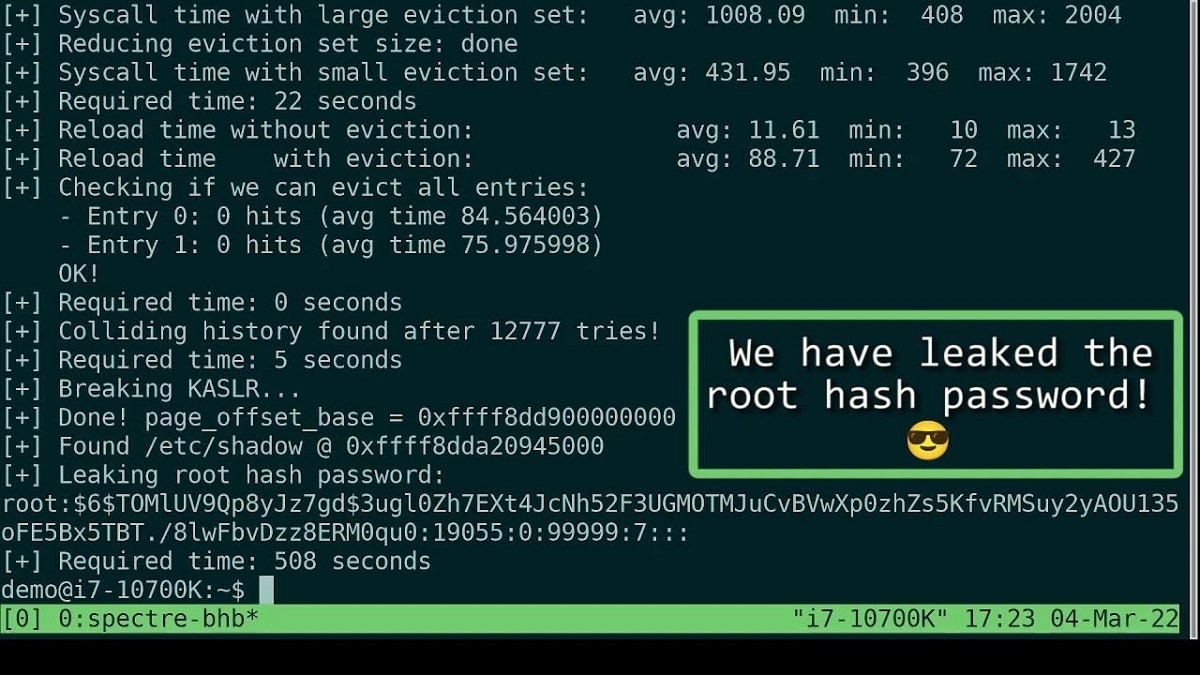
Researchers have demonstrated a functional exploit that allows user space to extract arbitrary data from kernel memory.
For example, it shows how, using the prepared exploit, it is possible to extract from the kernel buffers a string with a hash of the root user's password, loaded from the /etc/shadow file.
The exploit demonstrates the ability to exploit the vulnerability within a single privilege level (kernel-to-kernel attack) using a user-loaded eBPF program. The possibility of using existing Specter gadgets in the kernel code, scripts that lead to the speculative execution of instructions, is also not ruled out.
Vulnerability appears on most current Intel processors, with the exception of the Atom family of processors and in several of the ARM processors.
According to research, the vulnerability does not manifest itself on AMD processors. To solve the problem, several methods have been proposed. software to block the vulnerability, which can be used before the appearance of hardware protection in future CPU models.
To block attacks through the eBPF subsystem, sIt is recommended to disable by default the ability to load eBPF programs by unprivileged users by writing 1 to the file “/proc/sys/kernel/unprivileged_bpf_disabled” or by running the command “sysctl -w kernel .unprivileged_bpf_disabled=1”.
To block attacks through gadgets, it is recommended to use the LFENCE instruction in sections of code that potentially lead to speculative execution. It is noteworthy that the default configuration of most Linux distributions already contains the necessary protection measures sufficient to block the eBPF attack demonstrated by the researchers.
Intel's recommendations to disable unprivileged access to eBPF also apply by default starting with Linux kernel 5.16 and will be ported to earlier branches.
Finally, if you are interested in being able to know more about it, you can consult the details in the following link