General index of the series: Computer Networks for SMEs: Introduction
Hello friends!. The main objective of this article is to show how we can integrate the DNS service based on the BIND9 in a Microsoft network, very common in many SMEs.
It arises from the official request of a friend who lives in La Tierra del Fuego -The Fuegian- specialized in Microsoft® Networks -Certificates included- to guide you in this part of the migration of your servers to Linux. The costs of Support Technician who pay Microsoft® are already Unbearable for the Company in which he works and of which he is his Main Shareholder.
My friend The Fuegian he has a great sense of humor, and since he saw the series of three films «The Lord of the Rings»He was captivated by many of the names of his dark characters. So, Reader friend, do not be surprised by the names of your domain and your servers.
For newcomers to the topic, and before continuing reading, we recommend that you read and study the three previous articles on SME Networks:
- DNS and DHCP in openSUSE 13.2 "Harlequin"
- DNS and DHCP on CentOS 7
- DNS and DHCP in Debian 8 "Jessie"
It's like watching three of the four parts of «Underworld»Published until today, and that this is the fourth.
General parameters
After several exchanges via e-mailAt last I was clear about the main parameters of your current network, which are:
Domain name mordor.fan LAN Network 10.10.10.0/24 ==================================== =========================================== Servers IP Address Purpose (Servers with OS Windows) ================================================ =============================== sauron.mordor.fan. 10.10.10.3 Active Directory® 2008 SR2 mamba.mordor.fan. 10.10.10.4 Windows file server darklord.mordor.fan. 10.10.10.6 Proxy, gateway and firewall on Kerios troll.mordor.fan. 10.10.10.7 Blog based on ... can't remember shadowftp.mordor.fan. 10.10.10.8 FTP server blackelf.mordor.fan. 10.10.10.9 Full e-mail service blackspider.mordor.fan. 10.10.10.10 WWW service palantir.mordor.fan. 10.10.10.11 Chat on Openfire for Windows
I asked permission to The Fuegian to set as many Aliases as necessary to clear my mind and gave me his permission:
Real CNAME ============================== sauron ad-dc mamba fileserver darklord proxyweb troll blog shadowftp ftpserver blackelf mail blackspider www palantir openfire
I declared all the important DNS records in my installation of an Active Directory Windows 2008 that I was forced to implement to guide me in the making of this post.
About Active Directory DNS SRV records
The registers SRV o Service Locators - widely used in Microsoft Active Directory - are defined in the Request for Comments RFCs 2782. They allow the location of a service based on the TCP / IP protocol through a DNS query. For example, a customer on a Microsoft network can locate the location of Domain Controllers - Domain controllers that provide the LDAP service over the TCP protocol on port 389 through a single DNS query.
It is normal that in the Forests - forests, and Trees - Trees of a large Microsoft Network there are several Domain Controllers. Through the use of SRV records in the different Zones that make up the Domain Name Space of that Network, we can maintain a List of Servers that provide similar well-known services, ordered by preference according to the transport protocol and port of each one of the servers.
At Lóleo Eventos, Request for Comments RFCs 1700 Defining Universal Symbolic Names for Well-Known Services - Well Known Service, and names such as «_telnet","_smtp»For services telnet y SMTP. If a symbolic name is not defined for a Well Known Service, a local name or another name can be used according to the user's preferences.
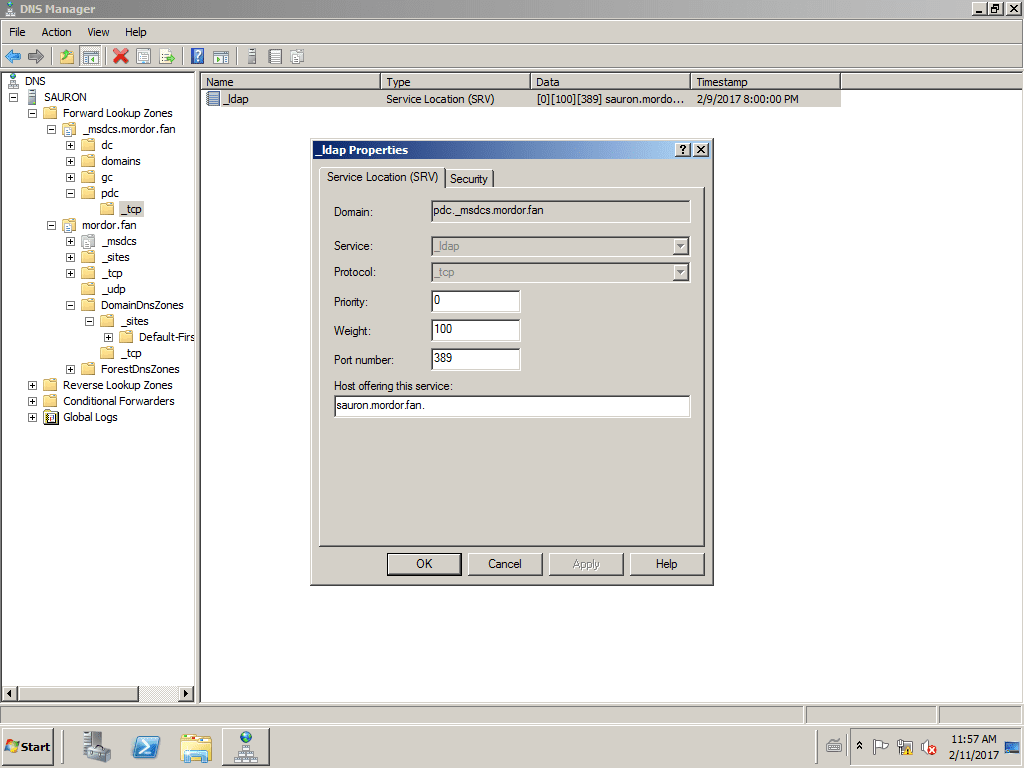
The purpose of each field «special»Used in the declaration of an SRV Resource Record is the following:
- Domain: "Pdc._msdcs.mordor.fan.«. DNS name of the service to which the SRV record refers. The DNS name in the example means -more or less- Primary Domain Controller from the area _msdcs.mordor.fan.
- Service: "_Ldap". Symbolic name of the service that is provided defined according to Request for Comments RFCs 1700.
- Protocol: "_Tcp". Indicates the type of transport protocol. Typically can take the values _tcp o _udp, although -and in fact- any type of transport protocol indicated in the Request for Comments RFCs 1700. For example, for a service chat protocol-based XMPP, this field would have the value of _xmpp.
- Priority: "0«. Declare the priority or preference for the Host offering this service that we will see later. The DNS queries of the clients about the service defined by this SRV record, upon receiving the appropriate response, will try to contact the first available host with the lowest number listed in the field. Priority. The range of values that this field can take is 0 to 65535.
- Weight: "100«. Can be used in combination with Priority to provide a load balancing mechanism when there are several servers that provide the same service. There should be a similar SRV record for each server in the Zone file, with its name declared in the field Host offering this service. Before servers with equal values in the field Priority, the field value Weight it can be used as an additional level of preference to obtain an exact server selection for load balancing. The range of values that this field can take is 0 to 65535. If load balancing is not required, for example as in the case of a single server, it is recommended to assign the value 0 to make the SRV record easier to read.
- Port number - Port: "389«. Port number in Host offering this service that provides the service indicated in the field Service. The port number that is recommended for each type of Well Known Service is indicated in the Request for Comments RFCs 1700, although it can take a value between 0 and 65535.
- Host offering this service - Target: "sauron.mordor.fan.«. Specifies the FQDN that unequivocally identifies the host that provides the service indicated by the SRV record. A record type «A»In the domain namespace for each FQDN from the server or host that provides the service. Simpler, a type record A in the direct zone (s).
- Note:
To authoritatively indicate that the service specified by the SRV record is not provided on this host, a single (.) point.
- Note:
We just want to repeat that the correct operation of a network or Active Directory® relies heavily on the correct operation of the Domain Name Service.
Active Directory DNS records
To make the Zones of the new DNS Server based on BIND, we must obtain all the DNS records from Active Directory®. To make life easier, we go to the team sauron.mordor.fan -Active Directory® 2008 SR2- and in the DNS Administration Console we activate the Zone Transfer -direct and reverse- for the main zones declared in this type of service, which are:
- _msdcs.mordor.fan
- mordor.fan
- 10.10.10.in-addr.harp
Once the previous step has been carried out and preferably from a Linux computer whose IP address is within the range of the subnet used by the Windows Network, we execute:
buzz @ sysadmin: ~ $ dig @ 10.10.10.3 _msdcs.mordor.fan axfr> temp /rrs._msdcs.mordor.fan buzz @ sysadmin: ~ $ dig @ 10.10.10.3 mordor.fan axfr> temp / rrs.mordor.fan buzz @ sysadmin: ~ $ dig @ 10.10.10.3 10.10.10.in-addr.arpa axfr> temp / rrs.10.10.10.in-addr.arpa
- Recall from previous articles that the IP address of the device sysadmin.desdelinux.fan is 10.10.10.1 or 192.168.10.1.
In the three previous commands we can eliminate the option @10.10.10.3 -ask the DNS server with that address- if we declare in the file / Etc / resolv.conf to server IP sauron.mordor.fan:
buzz@sysadmin:~$ cat /etc/resolv.conf # Generated by NetworkManager search desdelinux.fan nameserver 192.168.10.5 nameserver 10.10.10.3
After editing with extreme care, as corresponds to any zone file in a BIND, we will obtain the following data:
RRs records from the original zone _msdcs.mordor.fan
buzz @ sysadmin: ~ $ cat temp / rrs._msdcs.mordor.fan ; Relating to SOA and NS _msdcs.mordor.fan. 3600 IN SOA sauron.mordor.fan. hostmaster.mordor.fan. 12 900 600 86400 3600 _msdcs.mordor.fan. 3600 IN NS sauron.mordor.fan. ; ; GLOBAL CATALOG gc._msdcs.mordor.fan. 600 IN A 10.10.10.3; ; Aliases -in the modified and private LDAP database of an Active Directory- of SAURON 03296249-82a1-49aa-a4f0-28900f5d256b._msdcs.mordor.fan. 600 IN CNAME sauron.mordor.fan. ; ; Modified and private LDAP of an Active Directory _ldap._tcp.Default-First-Site-Name._sites.dc._msdcs.mordor.fan. 600 IN SRV 0 100 389 sauron.mordor.fan. _ldap._tcp.dc._msdcs.mordor.fan. 600 IN SRV 0 100 389 sauron.mordor.fan. _ldap._tcp.18d3360d-8fdb-40cf-a678-d7c420b6d775.domains._msdcs.mordor.fan. 600 IN SRV 0 100 389 sauron.mordor.fan. _ldap._tcp.Default-First-Site-Name._sites.gc._msdcs.mordor.fan. 600 IN SRV 0 100 3268 sauron.mordor.fan. _ldap._tcp.gc._msdcs.mordor.fan. 600 IN SRV 0 100 3268 sauron.mordor.fan. _ldap._tcp.pdc._msdcs.mordor.fan. 600 IN SRV 0 100 389 sauron.mordor.fan. ; ; KERBEROS modified and private from an Active Directory _kerberos._tcp.Default-First-Site-Name._sites.dc._msdcs.mordor.fan. 600 IN SRV 0 100 88 sauron.mordor.fan. _kerberos._tcp.dc._msdcs.mordor.fan. 600 IN SRV 0 100 88 sauron.mordor.fan.
RRs records from the original zone mordor.fan
buzz @ sysadmin: ~ $ cat temp / rrs.mordor.fan ; Relating to SOA, NS, MX and the A record that it maps; the Domain Name to the IP of SAURON; Things from an Active Directory mordor.fan. 3600 IN SOA sauron.mordor.fan. hostmaster.mordor.fan. 48 900 600 86400 3600 mordor.fan. 600 IN A 10.10.10.3 mordor.fan. 3600 IN NS sauron.mordor.fan. mordor.fan. 3600 IN MX 10 blackelf.mordor.fan. _msdcs.mordor.fan. 3600 IN NS sauron.mordor.fan. ; ; Also important A records DomainDnsZones.mordor.fan. 600 IN A 10.10.10.3 ForestDnsZones.mordor.fan. 600 IN A 10.10.10.3; ; GLOBAL CATALOG _gc._tcp.mordor.fan. 600 IN SRV 0 100 3268 sauron.mordor.fan. _gc._tcp.Default-First-Site-Name._sites.mordor.fan. 600 IN SRV 0 100 3268 sauron.mordor.fan. ; ; Modified and private LDAP of an Active Directory _ldap._tcp.mordor.fan. 600 IN SRV 0 100 389 sauron.mordor.fan. _ldap._tcp.Default-First-Site-Name._sites.DomainDnsZones.mordor.fan. 600 IN SRV 0 100 389 sauron.mordor.fan. _ldap._tcp.DomainDnsZones.mordor.fan. 600 IN SRV 0 100 389 sauron.mordor.fan. _ldap._tcp.Default-First-Site-Name._sites.mordor.fan. 600 IN SRV 0 100 389 sauron.mordor.fan. _ldap._tcp.Default-First-Site-Name._sites.ForestDnsZones.mordor.fan. 600 IN SRV 0 100 389 sauron.mordor.fan. _ldap._tcp.ForestDnsZones.mordor.fan. 600 IN SRV 0 100 389 sauron.mordor.fan. ; ; Modified and private KERBEROS from an Active Directory _kerberos._tcp.Default-First-Site-Name._sites.mordor.fan. 600 IN SRV 0 100 88 sauron.mordor.fan. _kerberos._tcp.mordor.fan. 600 IN SRV 0 100 88 sauron.mordor.fan. _kpasswd._tcp.mordor.fan. 600 IN SRV 0 100 464 sauron.mordor.fan. _kerberos._udp.mordor.fan. 600 IN SRV 0 100 88 sauron.mordor.fan. _kpasswd._udp.mordor.fan. 600 IN SRV 0 100 464 sauron.mordor.fan. ; ; A records with fixed IPs -> Blackelf.mordor.fan servers. 3600 IN A 10.10.10.9 blackspider.mordor.fan. 3600 IN A 10.10.10.10 darklord.mordor.fan. 3600 IN A 10.10.10.6 mamba.mordor.fan. 3600 IN A 10.10.10.4 palantir.mordor.fan. 3600 IN A 10.10.10.11 sauron.mordor.fan. 3600 IN A 10.10.10.3 shadowftp.mordor.fan. 3600 IN A 10.10.10.8 troll.mordor.fan. 3600 IN A 10.10.10.7; ; CNAME records ad-dc.mordor.fan. 3600 IN CNAME sauron.mordor.fan. blog.mordor.fan. 3600 IN CNAME troll.mordor.fan. fileserver.mordor.fan. 3600 IN CNAME mamba.mordor.fan. ftpserver.mordor.fan. 3600 IN CNAME shadowftp.mordor.fan. mail.mordor.fan. 3600 IN CNAME balckelf.mordor.fan. openfire.mordor.fan. 3600 IN CNAME palantir.mordor.fan. proxy.mordor.fan. 3600 IN CNAME darklord.mordor.fan. www.mordor.fan. 3600 IN CNAME blackspider.mordor.fan.
RRs records from original zone 10.10.10.in-addr.arpa
buzz @ sysadmin: ~ $ cat temp / rrs.10.10.10.in-addr.arpa ; Relating to SOA and NS 10.10.10.in-addr.arpa. 3600 IN SOA sauron.mordor.fan. hostmaster.mordor.fan. 21 900 600 86400 3600 10.10.10.in-addr.arpa. 3600 IN NS sauron.mordor.fan. ; ; PTR records 10.10.10.10.in-addr.arpa. 3600 IN PTR blackspider.mordor.fan. 11.10.10.10.in-addr.arpa. 3600 IN PTR palantir.mordor.fan. 3.10.10.10.in-addr.arpa. 3600 IN PTR sauron.mordor.fan. 4.10.10.10.in-addr.arpa. 3600 IN PTR mamba.mordor.fan. 5.10.10.10.in-addr.arpa. 3600 IN PTR dnslinux.mordor.fan. 6.10.10.10.in-addr.arpa. 3600 IN PTR darklord.mordor.fan. 7.10.10.10.in-addr.arpa. 3600 IN PTR troll.mordor.fan. 8.10.10.10.in-addr.arpa. 3600 IN PTR shadowftp.mordor.fan. 9.10.10.10.in-addr.arpa. 3600 IN PTR blackelf.mordor.fan.
Up to this point we can think that we have the necessary data to continue in our adventure, not without first observing the TTL's and other data that in a very concise way the output and direct observation of the DNS of a Microsft® Active Directory® 2008 SR2 64 bits provides us.
Images of the DNS Manager in SAURON
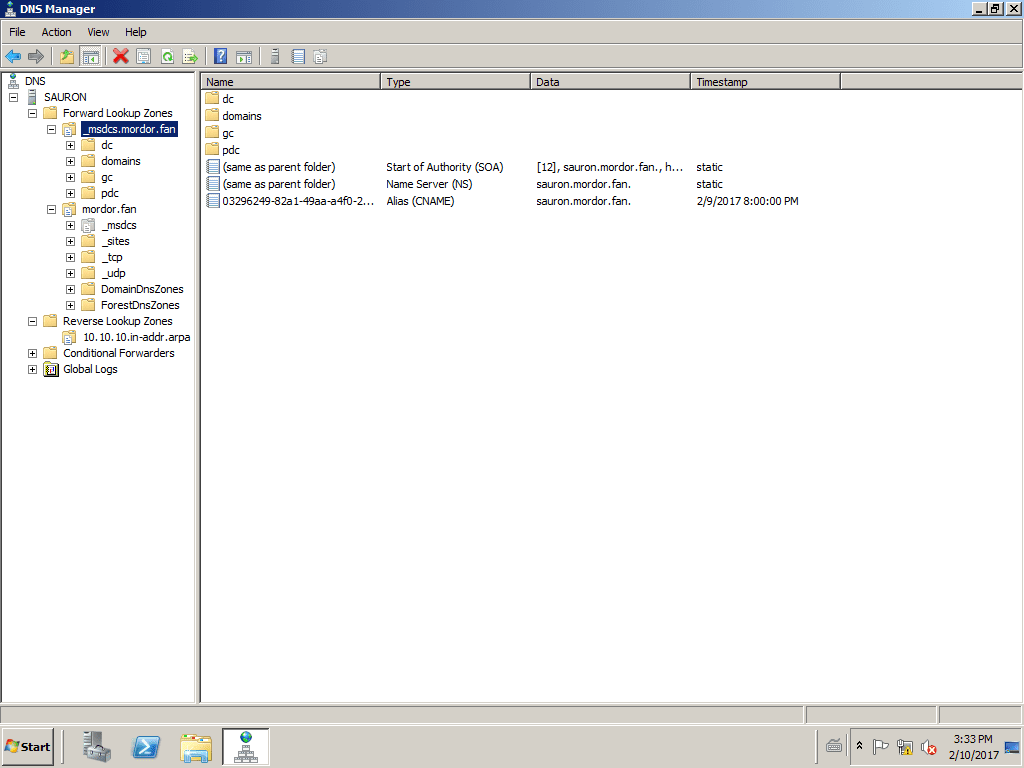
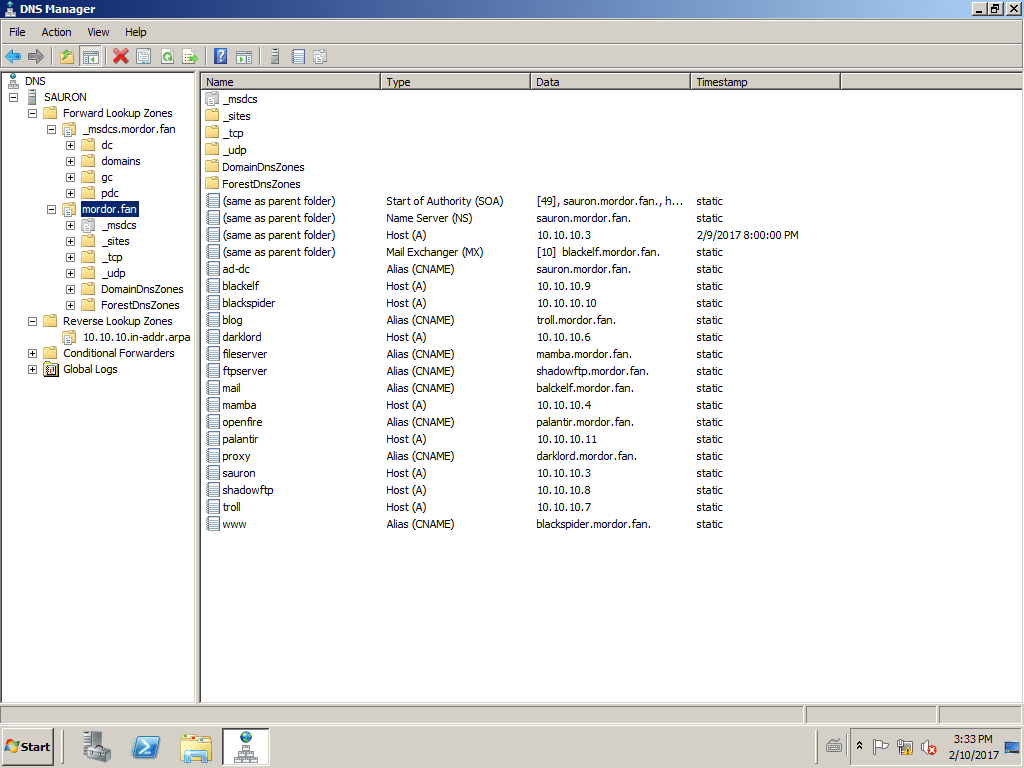
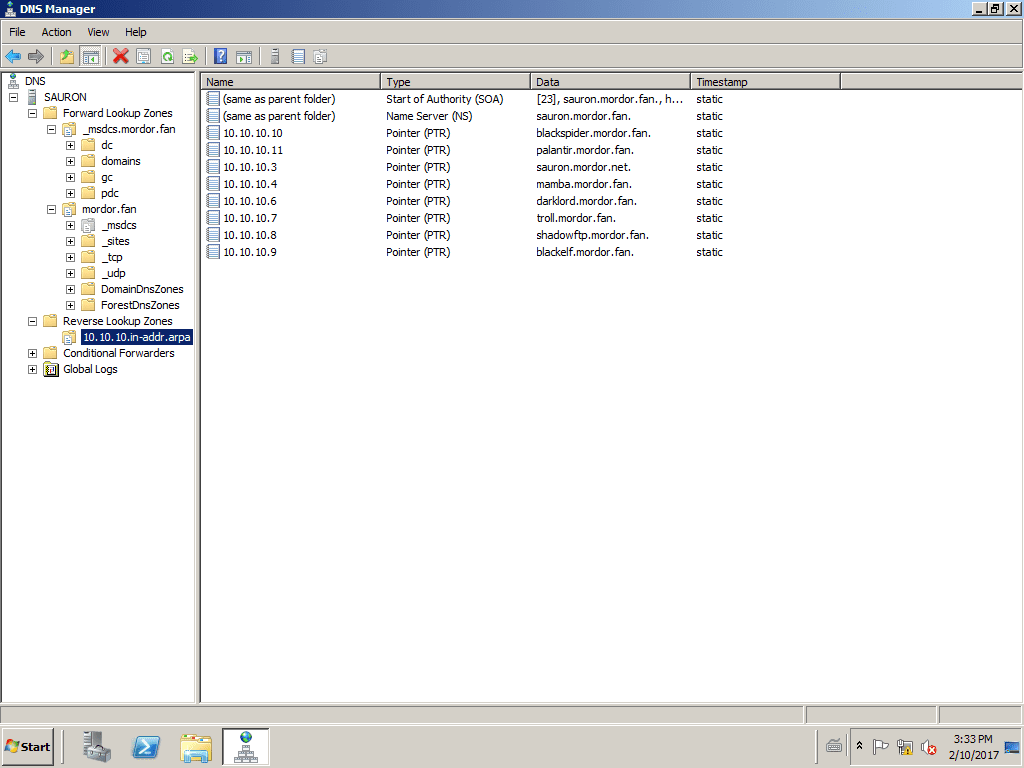
Dnslinux.mordor.fan team.
If we look closely, to the IP address 10.10.10.5 no name was assigned to it precisely so that it would be occupied by the name of the new DNS dnslinux.mordor.fan. To install the DNS and DHCP pair we can be guided by the articles DNS and DHCP in Debian 8 "Jessie" y DNS and DHCP on CentOS 7.
Base operating system
My friend The FuegianIn addition to being a true specialist in Microsoft® Windows - he has a couple of Certificates issued by that company - he has read and put into practice some of the articles about desktops published in DesdeLinux., and he told me that he expressly wanted a Debian-based solution. 😉
To please you, we'll start with a fresh, clean installation of a server based on Debian 8 "Jessie". However, what we will write next is valid for the CentOS and openSUSE distributions whose articles we mentioned earlier. BIND and DHCP are the same on any distro. Slight variations are introduced by the package maintainers in each distribution.
We will do the installation as indicated in DNS and DHCP in Debian 8 "Jessie", taking care to use the IP 10.10.10.5 and the network 10.10.10.0/24., even before configuring the BIND.
We configure the BIND in the Debian style
/etc/bind/named.conf
The file /etc/bind/named.conf we leave it as it is installed.
/etc/bind/named.conf.options
The file /etc/bind/named.conf.options should be left with the following content:
root @ dnslinux: ~ # cp /etc/bind/named.conf.options /etc/bind/named.conf.options.original
root @ dnslinux: ~ # nano /etc/bind/named.conf.options
options {directory "/ var / cache / bind"; // If there is a firewall between you and nameservers you want // to talk to, you may need to fix the firewall to allow multiple // ports to talk. See http://www.kb.cert.org/vuls/id/800113 // If your ISP provided one or more IP addresses for stable // nameservers, you probably want to use them as forwarders. // Uncomment the following block, and insert the addresses replacing // the all-0's placeholder. // forwarders {// 0.0.0.0; //}; // =============================================== ===================== $ // If BIND logs error messages about the root key being expired, // you will need to update your keys. See https://www.isc.org/bind-keys // ================================= =================================== $
// We don't want DNSSEC
dnssec-enable no;
//dnssec-validation self;
auth-nxdomain no; # conform to RFC1035
// We don't need to listen for IPv6 addresses
// listen-on-v6 {any; };
listen-on-v6 {none; };
// For checks from localhost and sysadmin
// through // dig mordor.fan axfr // dig 10.10.10.in-addr.arpa axfr // dig _msdcs.mordor.fan axfr // We don't have Slave DNS ... until now
allow-transfer {localhost; 10.10.10.1; };
};
// BIND logging
log {
channelqueries {
file "/var/log/named/queries.log" versions 3 size 1m;
severity info;
print-time yes;
print-severity yes;
yes print-category;
};
channel query-error {
file "/var/log/named/query-error.log" versions 3 size 1m;
severity info;
print-time yes;
print-severity yes;
yes print-category;
};
category queries {
wanted;
};
category query-errors {
query-error;
};
};
- We introduce the capture of the BIND logs as a NEW appearance in the series of articles on the subject. We create la folder and files required for the Logging of the BIND:
root @ dnslinux: ~ # mkdir / var / log / named root @ dnslinux: ~ # touch /var/log/named/queries.log root @ dnslinux: ~ # touch /var/log/named/query-error.log root @ dnslinux: ~ # chown -R bind: bind / var / log / named
We check the syntax of the configured files
root @ dnslinux: ~ # named-checkconf root @ dnslinux: ~ #
/etc/bind/named.conf.local
We create the file /etc/bind/zones.rfcFreeBSD with the same content as indicated in DNS and DHCP in Debian 8 "Jessie".
root @ dnslinux: ~ # nano /etc/bind/zones.rfcFreeBSD
The file /etc/bind/named.conf.local should be left with the following content:
// // Do any local configuration here // // Consider adding the 1918 zones here, if they are not used in your // organization
include "/etc/bind/zones.rfc1918"; include "/etc/bind/zones.rfcFreeBSD";
zone "mordor.fan" {type master; file "/var/lib/bind/db.mordor.fan"; }; zone "10.10.10.in-addr.arpa" {type master; file "/var/lib/bind/db.10.10.10.in-addr.arpa"; };
zone "_msdcs.mordor.fan" {type master;
check-names ignore; file "/etc/bind/db._msdcs.mordor.fan"; }; root @ dnslinux: ~ # named-checkconf
root @ dnslinux: ~ #
Zone File mordor.fan
root @ dnslinux: ~ # nano /var/lib/bind/db.mordor.fan $ TTL 3H @ IN SOA dnslinux.mordor.fan. root.dnslinux.mordor.fan. (1; serial 1D; refresh 1H; retry 1W; expire 3H); minimum or; Negative caching time to live; ; BE VERY CAREFUL WITH THE FOLLOWING RECORDS @ IN NS dnslinux.mordor.fan. @ IN A 10.10.10.5 @ IN MX 10 blackelf.mordor.fan. @ IN TXT "Wellcome to The Dark Lan of Mordor"; _msdcs.mordor.fan. IN NS dnslinux.mordor.fan. ; dnslinux.mordor.fan. IN A 10.10.10.5 ; END VERY CAREFULLY WITH THE FOLLOWING RECORDS; DomainDnsZones.mordor.fan. IN A 10.10.10.3 ForestDnsZones.mordor.fan. IN A 10.10.10.3; ; GLOBAL CATALOG _gc._tcp.mordor.fan. 600 IN SRV 0 0 3268 sauron.mordor.fan. _gc._tcp.Default-First-Site-Name._sites.mordor.fan. 600 IN SRV 0 0 3268 sauron.mordor.fan. ; ; Modified and private LDAP of an Active Directory _ldap._tcp.mordor.fan. 600 IN SRV 0 0 389 sauron.mordor.fan. _ldap._tcp.Default-First-Site-Name._sites.DomainDnsZones.mordor.fan. 600 IN SRV 0 0 389 sauron.mordor.fan. _ldap._tcp.DomainDnsZones.mordor.fan. 600 IN SRV 0 0 389 sauron.mordor.fan. _ldap._tcp.Default-First-Site-Name._sites.mordor.fan. 600 IN SRV 0 0 389 sauron.mordor.fan. _ldap._tcp.Default-First-Site-Name._sites.ForestDnsZones.mordor.fan. 600 IN SRV 0 0 389 sauron.mordor.fan. _ldap._tcp.ForestDnsZones.mordor.fan. 600 IN SRV 0 0 389 sauron.mordor.fan. ; ; Modified and private KERBEROS of an Active Directory _kerberos._tcp.Default-First-Site-Name._sites.mordor.fan. 600 IN SRV 0 0 88 sauron.mordor.fan. _kerberos._tcp.mordor.fan. 600 IN SRV 0 0 88 sauron.mordor.fan. _kpasswd._tcp.mordor.fan. 600 IN SRV 0 0 464 sauron.mordor.fan. _kerberos._udp.mordor.fan. 600 IN SRV 0 0 88 sauron.mordor.fan. _kpasswd._udp.mordor.fan. 600 IN SRV 0 0 464 sauron.mordor.fan. ; ; Records A with fixed IP -> Servers blackelf.mordor.fan. IN A 10.10.10.9 blackspider.mordor.fan. IN A 10.10.10.10 darklord.mordor.fan. IN A 10.10.10.6 mamba.mordor.fan. IN A 10.10.10.4 palantir.mordor.fan. IN A 10.10.10.11 sauron.mordor.fan. IN A 10.10.10.3 shadowftp.mordor.fan. IN A 10.10.10.8 troll.mordor.fan. IN A 10.10.10.7; ; CNAME records ad-dc.mordor.fan. IN CNAME sauron.mordor.fan. blog.mordor.fan. IN CNAME troll.mordor.fan. fileserver.mordor.fan. IN CNAME mamba.mordor.fan. ftpserver.mordor.fan. IN CNAME shadowftp.mordor.fan. mail.mordor.fan. IN CNAME balckelf.mordor.fan. openfire.mordor.fan. IN CNAME palantir.mordor.fan. proxy.mordor.fan. IN CNAME darklord.mordor.fan. www.mordor.fan. IN CNAME blackspider.mordor.fan. root @ dnslinux: ~ # named-checkzone mordor.fan /var/lib/bind/db.mordor.fan zone mordor.fan/IN: loaded serial 1 OK
The times TTL 600 of all the SRV registers we will keep them in case we install a Slave BIND in times to go. Those records represent Active Directory® services that mostly read data from your LDAP database. Since that database changes frequently, the sync times must be kept short, in a Master - Slave DNS scheme. According to the Microsoft philosophy observed from Active Directory 2000 to 2008, the value of 600 is maintained for these types of SRV records.
The TTL's of the servers with fixed IP, they are under the declared time in the SOA of 3 hours.
Zone File 10.10.10.in-addr.arpa
root @ dnslinux: ~ # nano /var/lib/bind/db.10.10.10.in-addr.arpa $ TTL 3H @ IN SOA dnslinux.mordor.fan. root.dnslinux.mordor.fan. (1; serial 1D; refresh 1H; retry 1W; expire 3H); minimum or; Negative caching time to live; @ IN NS dnslinux.mordor.fan. ; 10 IN PTR blackspider.mordor.fan. 11 IN PTR palantir.mordor.fan. 3 IN PTR sauron.mordor.fan. 4 IN PTR mamba.mordor.fan. 5 IN PTR dnslinux.mordor.fan. 6 IN PTR darklord.mordor.fan. 7 IN PTR troll.mordor.fan. 8 IN PTR shadowftp.mordor.fan. 9 IN PTR blackelf.mordor.fan. root @ dnslinux: ~ # named-checkzone 10.10.10.in-addr.arpa /var/lib/bind/db.10.10.10.in-addr.arpa zone 10.10.10.in-addr.arpa/IN: loaded serial 1 OK
Zone File _msdcs.mordor.fan
Let's take into account what is recommended in the file /usr/share/doc/bind9/README.Debian.gz About the location of the files of the Master Zones not subjected to dynamic updates by DHCP.
root @ dnslinux: ~ # nano /etc/bind/db._msdcs.mordor.fan $ TTL 3H @ IN SOA dnslinux.mordor.fan. root.dnslinux.mordor.fan. (1; serial 1D; refresh 1H; retry 1W; expire 3H); minimum or; Negative caching time to live; @ IN NS dnslinux.mordor.fan. ; ; ; GLOBAL CATALOG gc._msdcs.mordor.fan. 600 IN A 10.10.10.3; ; Aliases -in the modified and private LDAP database of an Active Directory- of SAURON 03296249-82a1-49aa-a4f0-28900f5d256b._msdcs.mordor.fan. 600 IN CNAME sauron.mordor.fan. ; ; Modified and private LDAP of an Active Directory _ldap._tcp.Default-First-Site-Name._sites.dc._msdcs.mordor.fan. 600 IN SRV 0 100 389 sauron.mordor.fan. _ldap._tcp.dc._msdcs.mordor.fan. 600 IN SRV 0 100 389 sauron.mordor.fan. _ldap._tcp.18d3360d-8fdb-40cf-a678-d7c420b6d775.domains._msdcs.mordor.fan. 600 IN SRV 0 100 389 sauron.mordor.fan. _ldap._tcp.Default-First-Site-Name._sites.gc._msdcs.mordor.fan. 600 IN SRV 0 100 3268 sauron.mordor.fan. _ldap._tcp.gc._msdcs.mordor.fan. 600 IN SRV 0 100 3268 sauron.mordor.fan. _ldap._tcp.pdc._msdcs.mordor.fan. 600 IN SRV 0 100 389 sauron.mordor.fan. ; ; KERBEROS modified and private from an Active Directory _kerberos._tcp.Default-First-Site-Name._sites.dc._msdcs.mordor.fan. 600 IN SRV 0 100 88 sauron.mordor.fan. _kerberos._tcp.dc._msdcs.mordor.fan. 600 IN SRV 0 100 88 sauron.mordor.fan.
We check the syntax and we can ignore the error it returns, since in the configuration of this Zone in the file /etc/bind/named.conf.local we include the statement check names ignore;. The zone will be correctly loaded by the BIND.
root @ dnslinux: ~ # named-checkzone _msdcs.mordor.fan /etc/bind/db._msdcs.mordor.fan /etc/bind/db._msdcs.mordor.fan:14: gc._msdcs.mordor.fan: bad owner name (check-names) zone _msdcs.mordor.fan/IN: loaded serial 1 OK root @ dnslinux: ~ # systemctl restart bind9.service root @ dnslinux: ~ # systemctl status bind9.service ● bind9.service - BIND Domain Name Server Loaded: loaded (/lib/systemd/system/bind9.service; enabled) Drop-In: /run/systemd/generator/bind9.service.d └─50-insserv.conf- $ named.conf Active: active (running) since Sun 2017-02-12 08:48:38 EST; 2s ago Docs: man: named (8) Process: 859 ExecStop = / usr / sbin / rndc stop (code = exited, status = 0 / SUCCESS) Main PID: 864 (named) CGroup: /system.slice/bind9.service └─864 / usr / sbin / named -f -u bind Feb 12 08:48:38 dnslinux named [864]: zone 3.efip6.arpa/IN: loaded serial 1 Feb 12 08:48:38 dnslinux named [864 ]: zone befip6.arpa/IN: loaded serial 1 Feb 12 08:48:38 dnslinux named [864]: zone 0.efip6.arpa/IN: loaded serial 1 Feb 12 08:48:38 dnslinux named [864]: zone 7.efip6.arpa/IN: loaded serial 1 Feb 12 08:48:38 dnslinux named [864]: zone mordor.fan/IN: loaded serial 1 Feb 12 08:48:38 dnslinux named [864]: zone example .org / IN: loaded serial 1 Feb 12 08:48:38 dnslinux named [864]: zone _msdcs.mordor.fan/IN: loaded serial 1 Feb 12 08:48:38 dnslinux named [864]: zone invalid / IN : loaded serial 1 Feb 12 08:48:38 dnslinux named [864]: all zones loaded Feb 12 08:48:38 dnslinux named [864]: running
We consult the BIND
Before After installing DHCP, we must carry out a series of checks that includes even joining a Windows 7 client to the domain mordor.fan represented by the Active Directory installed on the computer sauron.mordor.fan.
The first thing we must do is stop the DNS service on the computer sauron.mordor.fan, and declare in your network interface that from now on your DNS server will be the 10.10.10.5 dnslinux.mordor.fan.
In a console of the server itself sauron.mordor.fan we execute:
Microsoft Windows [Version 6.1.7600] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C: \ Users \ Administrator> nslookup Default Server: dnslinux.mordor.fan Address: 10.10.10.5 > gc._msdcs Server: dnslinux.mordor.fan Address: 10.10.10.5 Name: gc._msdcs.mordor.fan Address: 10.10.10.3 > mordor.fan Server: dnslinux.mordor.fan Address: 10.10.10.5 Name: mordor.fan Address: 10.10.10.3 > 03296249-82a1-49aa-a4f0-28900f5d256b._msdcs Server: dnslinux.mordor.fan Address: 10.10.10.5 Name: sauron.mordor.fan Address: 10.10.10.3 Aliases: 03296249-82a1-49aa-a4f0-28900f5d256b._msdcs.mordor.fan > set type = SRV > _kerberos._tcp.Default-First-Site-Name._sites.dc._msdcs Server: dnslinux.mordor.fan Address: 10.10.10.5 _kerberos._tcp.Default-First-Site-Name._sites.dc._msdcs.mordor.fan SRV serv ice location: priority = 0 weight = 100 port = 88 svr hostname = sauron.mordor.fan _msdcs.mordor.fan nameserver = dnslinux.mordor.fan sauron.mordor.fan internet address = 10.10.10.3 dnslinux.mordor.fan internet address = 10.10.10.5 > _ldap._tcp.18d3360d-8fdb-40cf-a678-d7c420b6d775.domains._msdcs Server: dnslinux.mordor.fan Address: 10.10.10.5 _ldap._tcp.18d3360d-8fdb-40cf-a678-d7c420b6d775.domains._msdcs.mordor.fan SRV service location: priority = 0 weight = 100 port = 389 svr hostname = sauron .mordor.fan _msdcs.mordor.fan nameserver = dnslinux.mordor.fan sauron.mordor.fan internet address = 10.10.10.3 dnslinux.mordor.fan internet address = 10.10.10.5 > exit C: \ Users \ Administrator>
DNS queries made from sauron.mordor.fan are satisfactory.
The next step will be to create another virtual machine with Windows 7 installed. As we still do not have the DHCP service installed, we will give the computer with the name «win7»The IP address 10.10.10.251. We also declare that your DNS server will be the 10.10.10.5 dnslinux.mordor.fan, and that the search domain will be mordor.fan. We will not register that computer in DNS because we will also use it to test the DHCP service after we install it.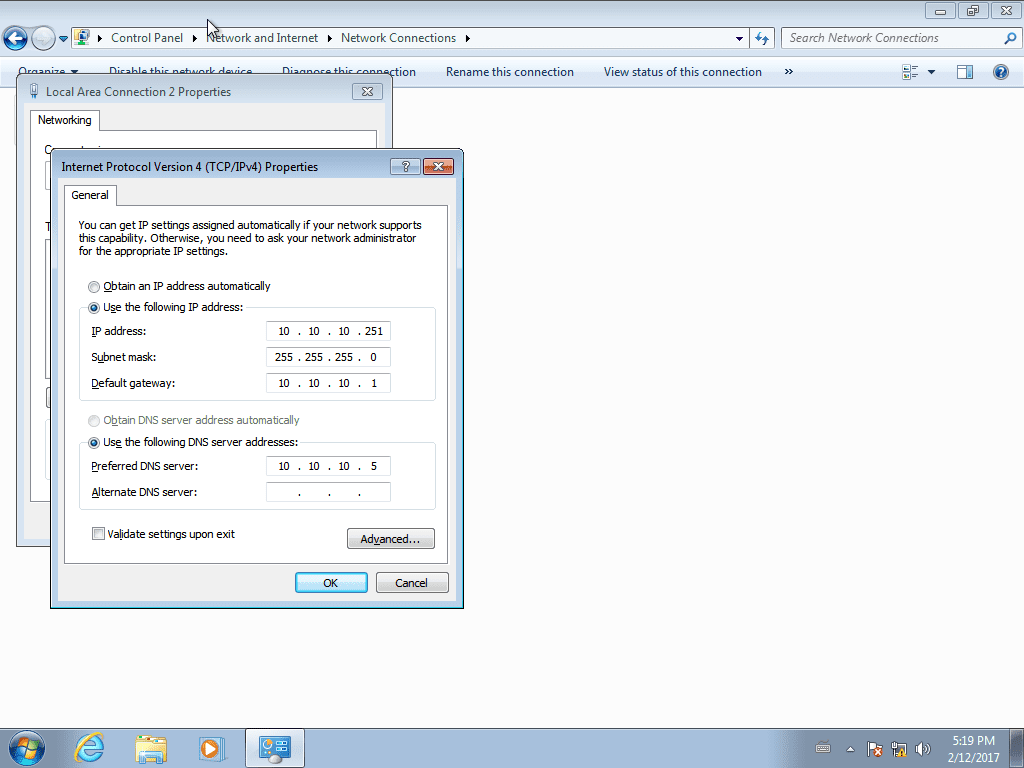
Next we open a console DCM and in it we execute:
Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C: \ Users \ buzz> nslookup Default Server: dnslinux.mordor.fan Address: 10.10.10.5 > mordor.fan Server: dnslinux.mordor.fan Address: 10.10.10.5 Name: mordor.fan Address: 10.10.10.3 > set type = SRV > _ldap._tcp.DomainDnsZones Server: dnslinux.mordor.fan Address: 10.10.10.5 _ldap._tcp.DomainDnsZones.mordor.fan SRV service location: priority = 0 weight = 0 port = 389 svr hostname = sauron.mordor.fan mordor.fan nameserver = dnslinux.mordor .fan sauron.mordor.fan internet address = 10.10.10.3 dnslinux.mordor.fan internet address = 10.10.10.5 > _kpasswd._udp Server: dnslinux.mordor.fan Address: 10.10.10.5 _kpasswd._udp.mordor.fan SRV service location: priority = 0 weight = 0 port = 464 svr hostname = sauron.mordor.fan mordor.fan nameserver = dnslinux.mordor.fan sauron.mordor.fan internet address = 10.10.10.3 dnslinux.mordor.fan internet address = 10.10.10.5 > _ldap._tcp.Default-First-Site-Name._sites.ForestDnsZones Server: dnslinux.mordor.fan Address: 10.10.10.5 _ldap._tcp.Default-First-Site-Name._sites.ForestDnsZones.mordor.fan SRV serv ice location: priority = 0 weight = 0 port = 389 svr hostname = sauron. mordor.fan mordor.fan nameserver = dnslinux.mordor.fan sauron.mordor.fan internet address = 10.10.10.3 dnslinux.mordor.fan internet address = 10.10.10.5 > exit C: \ Users \ buzz>
DNS queries made from the client «win7»Were also satisfactory.
In Active Directory we create the user «Saruman«, With the aim of using it when joining the client win7 to the domain mordor.fan., using the method «Network ID«, Using usernames saruman@mordor.fan y administrator@mordor.fan. The join was successful and is proven by the following screenshot: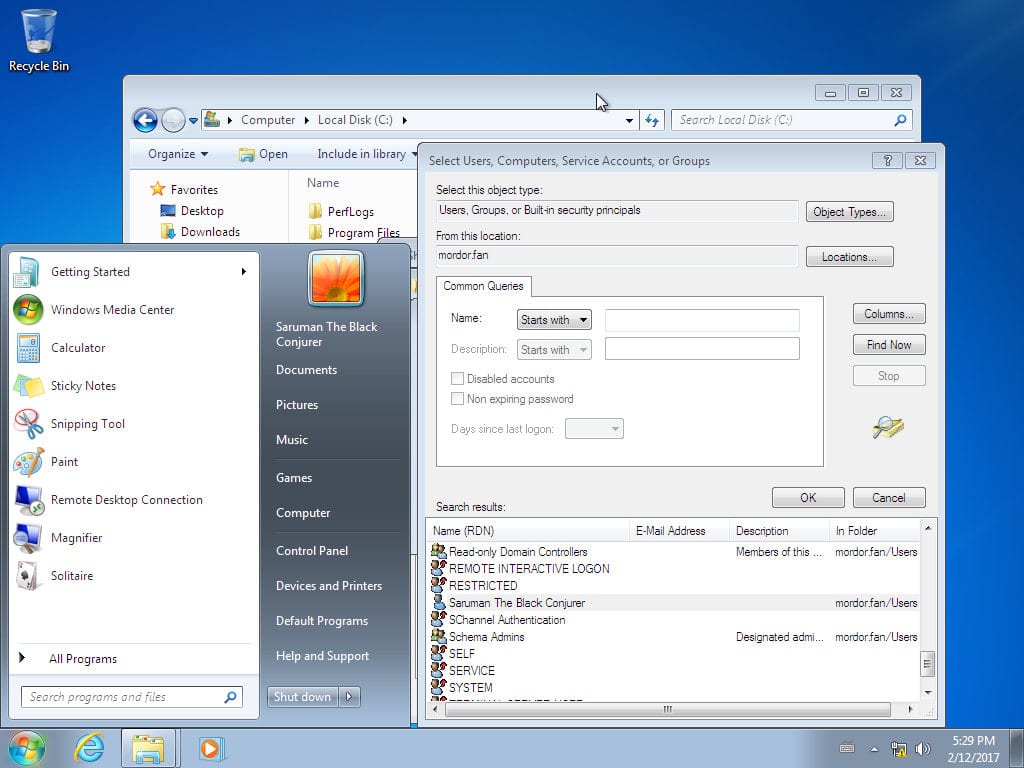
About Dynamic Updates in Microsoft® DNS and BIND
As we have the DNS service stopped in the Active Directory® it was not possible for the client «win7»Register your name and IP address in that DNS. Much less in dnslinux.mordor.fan since we didn't make any statement allow update for any of the areas involved.
And this was where the good fight with my friend was formed The Fuegian. In my first email about this aspect I commented:
- Microsoft's articles on the use of BIND and Active Directory® recommend that, especially the Direct Zone, be allowed to be updated -penetrated- directly by Windows clients that are already joined to the Active Directory domain.
- That is why, by default, in the DNS zones of an Active Directory® Secure Dynamic Updates are allowed. by Windows clients already joined to the Active Directory domain. If they are not united, they refrain from the consequences.
- The DNS of an Active Directory supports the dynamic updates "Secure only", "Nonsecure and secure", or "None" which is the same as saying NO Updates or None.
- Yes, really the Microsoft Philosophy does not agree that its customers will NOT update their data in their DNS (s), it would not leave open the possibility of disabling dynamic updates in their DNS (s), unless that option will be left for more hidden purposes.
- Microsoft offers "Security" in exchange for Darkness, as a colleague and friend who passed Microsft® Certificates courses told me. True. In addition, El Fueguino confirmed it to me.
- A client that acquires an IP address through DHCP installed on a UNIX® / Linux machine for example, will not be able to resolve the IP address of his own name until you are joined to the Active Directory domain, as long as Microsoft® or a BIND is used as DNS without dynamic updates by DHCP.
- If I install DHCP in the Active Directory® itself, then I must declare that the Zones are updated by Microsoft® DHCP.
- If we are going to use BIND as the DNS for the Windows network, it is logical and recommended that we install the BIND-DHCP duo, with the latter dynamically updating the BIND and the matter concluded.
- In the world of LAN networks on UNIX® / Linux, ever since dynamic updates were invented on BIND, only Mr. DHCP is allowed «penetrate»To Mrs. BIND with her updates. The relaxation that is with order, please.
- When I declare in the zone mordor.fan for example: allow-update {10.10.10.0/24; };, BIND itself informs me when starting or restarting it that:
-
zone 'mordor.fan' allows updates by IP address, which is insecure
-
- In the sacrosanct UNIX® / Linux world, such saucy with DNS is simply inadmissible.
You can imagine the rest of the exchange with my friend The Fuegian through emails, Telegram Chat, telephone calls paid for by him (of course man, I don't have a kilo for that), and even messages through carrier pigeons in the XXI century!
He even threatened not to send me a son of his pet, his Iguana «Petra»That he had promised me as part of the payment. There I really got scared. So I started again, but from another angle.
- The "almost" Active Directory that can be achieved with Samba 4, solves this aspect in a masterly way, both when we use its Internal DNS, or the BIND compiled to support DLZ zones - Dynamic Loaded Zones, or Dynamically Loaded Zones.
- It continues to suffer from the same: when a client acquires an IP address through a DHCP installed in otra UNIX® / Linux machine, you will not be able to resolve the IP address of your own name until it is joined to the domain of the Samba 4 AD-DC.
- Integrate the BIND-DLZ and DHCP duo on the same machine where the AD-DC Samba 4 it's a job for a real specialist.
The Fuegian He called me to chapter and yelled at me: We are NOT talking about AD-DC Samba 4, but the Microsoft® Active Directory® !. And I humbly replied that I was delighted with part of the following articles that I was going to write.
That's when I told him that, the final decision on dynamic updates of client computers on his network was left to his free will. That I would only give him the type written before about allow-update {10.10.10.0/24; };, and more nothing. That I was not responsible for what resulted from that promiscuity that each Windows client -or Linux- in their network «will penetrate»With impunity to the BIND.
If you knew, my friend, Reader that that was the end point of the brawl, you wouldn't believe it. My friend The Fuegian he accepted the solution - and he will send me the iguana «Pete«- that now I share with you.
We install and configure DHCP
For more details read DNS and DHCP in Debian 8 "Jessie".
root @ dnslinux: ~ # aptitude install isc-dhcp-server
root @ dnslinux: ~ # nano / etc / default / isc-dhcp-server .... # On what interfaces should the DHCP server (dhcpd) serve DHCP requests? # Separate multiple interfaces with spaces, eg "eth0 eth1". INTERFACES = "eth0" root @ dnslinux: ~ # dnssec-keygen -a HMAC-MD5 -b 128 -r / dev / urandom -n USER dhcp-key
Kdhcp-key. + 157 + 29836
root @ dnslinux: ~ # cat Kdhcp-key. +157 + 29836.private
Private-key-format: v1.3 Algorithm: 157 (HMAC_MD5) Key: 3HT / bg / 6YwezUShKYofj5g == Bits: AAA = Created: 20170212205030 Publish: 20170212205030 Activate: 20170212205030
root @ dnslinux: ~ # nano dhcp.key
key dhcp-key {algorithm hmac-md5; secret "3HT / bg / 6YwezUShKYofj5g =="; };
root @ dnslinux: ~ # install -o root -g bind -m 0640 dhcp.key /etc/bind/dhcp.key
root @ dnslinux: ~ # install -o root -g root -m 0640 dhcp.key /etc/dhcp/dhcp.key
root @ dnslinux: ~ # nano /etc/bind/named.conf.local
// // Do any local configuration here // // Consider adding the 1918 zones here, if they are not used in your // organization include "/etc/bind/zones.rfc1918"; include "/etc/bind/zones.rfcFreeBSD";
// Don't forget ... I forgot and paid with mistakes. ;-)
include "/etc/bind/dhcp.key";
zone "mordor.fan" {type master;
allow-update {10.10.10.3; key dhcp-key; };
file "/var/lib/bind/db.mordor.fan"; }; zone "10.10.10.in-addr.arpa" {type master;
allow-update {10.10.10.3; key dhcp-key; };
file "/var/lib/bind/db.10.10.10.in-addr.arpa"; }; zone "_msdcs.mordor.fan" {type master; check-names ignore; file "/etc/bind/db._msdcs.mordor.fan"; };
root @ dnslinux: ~ # named-checkconf
root @ dnslinux: ~ #
root @ dnslinux: ~ # nano /etc/dhcp/dhcpd.conf
ddns-update-style interim; ddns-updates on; ddns-domainname "mordor.fan."; ddns-rev-domainname "in-addr.arpa."; ignore client-updates; authoritative; option ip-forwarding off; option domain-name "mordor.fan"; include "/etc/dhcp/dhcp.key"; zone mordor.fan. {primary 127.0.0.1; key dhcp-key; } zone 10.10.10.in-addr.arpa. {primary 127.0.0.1; key dhcp-key; } shared-network redlocal {subnet 10.10.10.0 netmask 255.255.255.0 {option routers 10.10.10.1; option subnet-mask 255.255.255.0; option broadcast-address 10.10.10.255; option domain-name-servers 10.10.10.5; option netbios-name-servers 10.10.10.5; range 10.10.10.30 10.10.10.250; }} # END dhcpd.conf
root @ dnslinux: ~ # dhcpd -t
Internet Systems Consortium DHCP Server 4.3.1 Copyright 2004-2014 Internet Systems Consortium. All rights reserved. For info, please visit https://www.isc.org/software/dhcp/ Config file: /etc/dhcp/dhcpd.conf Database file: /var/lib/dhcp/dhcpd.leases PID file: / var / run /dhcpd.pid
root @ dnslinux: ~ # systemctl restart bind9.service
root @ dnslinux: ~ # systemctl status bind9.service
root @ dnslinux: ~ # systemctl start isc-dhcp-server.service
root @ dnslinux: ~ # systemctl status isc-dhcp-server.service
What is related to Checks with clients, and the Manual modification of Zone files, we leave it for you, reader friend, to read it directly from DNS and DHCP in Debian 8 "Jessie", and apply it to your actual conditions. We did carry out all the necessary checks and obtained satisfactory results. Of course we send a copy of all of them to The Fuegian. There will be no more!
Tips
General
- Get a good deal of patience before you start.
- Install and configure the BIND first. Check everything and see all the records you declared in each file of the three -or more- zones, both from the Active Directory and from the DNS server itself on Linux. If possible, from a Linux machine that is not joined to the domain, make the necessary DNS queries to the BIND.
- Join a Windows client with a fixed IP address to the existing domain, and recheck all BIND settings from the Windows client.
- After you are undoubtedly sure that your brand new BIND configuration is completely correct, venture out to install, configure, and start the DHCP service.
- In case of errors, repeat the whole procedure from zero 0.
- Be careful with the copy & paste! and the remaining spaces in each line of the named.conf.xxxx files
- Afterwards, he did not complain - much less to my friend the Fuegian - that he was not properly advised.
Other tips
- Divide and conquer.
- In a SME Network it is safer and more beneficial to install an Authoritative BIND for the Internal LAN Zones that does not recur to any root server: recursion not;.
- In a SME Network located under an Internet Access Provider - ISP, perhaps the services proxy y SMTP they need to resolve domain names on the internet. He Squid you have the option of declaring your DNS to be external or not, while on a mail server based on Postfix o MDaemon® We can also declare the DNS servers that we will use in that service. In cases like this, that is, cases that do not provide services to the Internet and that are under a Internet Service Providers, you can install a BIND with forwarders pointing to the DNS of the ISP, and declare it as secondary DNS in the servers that need to resolve external queries to the LAN, otherwise it is possible to declare them through their own configuration files.
- If you have a Delegated Zone under your entire responsibilityThen another rooster crow:
- Install a DNS server based on NSD, which is an Authoritative DNS server by definition, that responds to queries from computers on the Internet. For some information aptitude show nsd. 😉 Please protect it very well with as many fire walls as necessary. Both hardware and software. It will be a DNS for the Internet, and that «Tsar»We must not give it with low pants. 😉
- As I have never seen myself in a case like this, that is, the person in charge of a Delegated Zone, I would have to think very well what to recommend for the resolution of domain names external to our LAN for the services that need it. SME Network Clients don't really need it. Consult specialized literature, or a specialist in these subjects, as I am far from being one of them. Seriously.
- Recursion does not exist on Authoritarian servers. Okay?. In case someone happens to do it with a BIND.
- Although we explicitly specify in the file /etc/dhcp/dhcpd.conf the declaration ignore client-updates;, if we run on a computer console dnslinux.mordor.fan the order journalctl -f, we will see that when starting the client win7.mordor.fan we get the following error messages:
-
Feb 12 16:55:41 dnslinux named [900]: client 10.10.10.30 # 58762: update 'mordor.fan/IN' denied Feb 12 16:55:42 dnslinux named [900]: client 10.10.10.30 # 49763: update 'mordor.fan/IN' denied Feb 12 16:56:23 dnslinux named [900]: client 10.10.10.30 # 63161: update 'mordor.fan/IN' denied - To eliminate these messages, we must go to the advanced options of the network card configuration and uncheck the option «Register this connection's addresses in DNS«. That will prevent the client from trying to self-register in Linux DNS forever and the problem ends. Sorry, but I don't have a copy of Windows 7 in Spanish. 😉
-
- To find out about all the serious - and crazy - queries a Windows 7 client makes, check out the logqueries.log that for something we declare it in the BIND configuration. The order would be:
-
root @ dnslinux: ~ # tail -f /var/log/named/queries.log
-
- If you do not allow your client computers to connect directly to the Internet, then why do you need the Root DNS Servers? This will significantly decrease the output of the command journalctl -f and from the previous one, if your Authoritarian DNS server for the Internal Zones does not connect directly to the Internet, which is highly recommended from a security point of view.
root @ dnslinux: ~ # cp /etc/bind/db.root /etc/bind/db.root.original root @ dnslinux: ~ # cp / dev / null /etc/bind/db.root
- If you don't need the declaration of the root servers, then why do you need Recursion - recursion?
root @ dnslinux: ~ # nano /etc/bind/named.conf.options options { ... recursion not; ... };
Specific advice of which I am still not very clear
El dhcpd.conf man tells us the following among many -many- other things:
The update-optimization statement
update-optimization flag;
If the update-optimization parameter is false for a given client, the server will attempt a DNS update for that client each time the client renews its lease, rather than only attempting an update when it appears to be necessary. This will allow the DNS to heal from database inconsistencies more easily, but the cost is that the DHCP server must do many more DNS updates. We recommend reading this option enabled, which is the default. This option only affects the behavior of the interim DNS update scheme, and has no effect on the ad-hoc DNS update scheme. If this parameter is not specified, or is true, the DHCP server will only update when the client information changes, the client gets a different lease, or the client's lease expires.
The more or less exact translation or interpretation is left to you, dear reader.
Personally, it has happened to me - and it happened during the writing of this article - that when I link a BIND to an Active Directory®, it is from Microsft® or Samba 4, if I change the name of a client computer registered in the Active Directory® domain or of AD–DC of Samba 4, it keeps its old name and IP address in the Direct Zone, and not the other way around, which is correctly updated with the new name. In other words, the old and new names are mapped to the same IP address in the Direct Zone, while in reverse only the new name appears. To understand me well, you must try it yourself.
I think it is a kind of revenge towards The Fuegian -not to me, please- for trying to migrate your services to Linux.
Of course the old name will disappear when its TTL 3600, or the time that we have declared in the DHCP configuration. But we want it to disappear immediately as it happens in a BIND + DHCP without an Active Directory through.
The solution to that situation I found by inserting the statement update-optimization false; at the end of the top of the file /etc/dhcp/dhcpd.conf:
ddns-update-style interim; ddns-updates on; ddns-domainname "mordor.fan."; ddns-rev-domainname "in-addr.arpa."; ignore client-updates; update-optimization false;
If any Reader knows more about it, please enlighten me. I will appreciate it a lot.
Summary
We have had a lot of fun with the subject, right? No suffering because we have a BIND working as a DNS server in a Microsoft® network, offering all the SRV records and responding appropriately to the DNS queries made. On the other hand we have a DHCP server granting IP addresses and dynamically updating the BIND Zones correctly.
But we cannot ask ... for the moment.
I hope my friend The Fuegian be happy and satisfied with the first step in your migration to Linux to make the unbearable costs of Microsft® Technical Support bearable.
Important note
Character "The Fuegian»Is completely fictional and a product of my imagination. Any resemblance or coincidence with real people is the same thing: Pure Involuntary Coincidence on my part. I only created it to make the writing and reading of this article a bit enjoyable. Now if you can tell me that the DNS issue is dark,
Very strong, no comment. Since Microsoft's DNS is not needed. Be careful not to sue, hahahaha. Thanks for the delivery Fico.
Sue me? Let them be seen with EL Fueguino. 😉
Thanks friend!!!
Wasn't it easier to install zentyal, for all this part of the active directory?
Haha, great articulation to mount the powerful bind and I see that Zentyal was recommended to you in the comment above, I'm leaving before the shooting breaks out.
PS: The domain based on Windows is Mordor but if we mount a pure Samba it would be Gondor or Rohan right? 😉
I do not recommend the use of Zentyal to anyone. Use Windows because its use is a reality in many SMEs. About the stability of the Zentyal, ask my friend and colleague Dhunter. 😉
Sure you do, dhunter friend. With Samba 4 it will be called tierramedia.fan. 😉
For those who have already downloaded the article, be very careful with the following:
Where says
; BE VERY CAREFUL WITH THE FOLLOWING RECORDS
@ IN NS dnslinux.mordor.fan.
@ IN A 10.10.10.3
Must say correctly
; BE VERY CAREFUL WITH THE FOLLOWING RECORDS
@ IN NS dnslinux.mordor.fan.
@ IN A 10.10.10.5
The colleague Eduardo Noel was the one who realized my involuntary mistake.
For those who have already downloaded the article, be very careful with the following:
Where says
; BE VERY CAREFUL WITH THE FOLLOWING RECORDS
@ IN NS dnslinux.mordor.fan.
@ IN A 10.10.10.3
Must say correctly
; BE VERY CAREFUL WITH THE FOLLOWING RECORDS
@ IN NS dnslinux.mordor.fan.
@ IN A 10.10.10.5
The colleague Eduardo Noel was the one who realized my involuntary mistake.
For those who plan to use Zentyal for something serious I warn you to be very careful, I am using two Zentyal 4.2 drivers (on 14.04), updated everything and be careful to the maximum, very rare bugs (and more rare are the answers in the project bugzilla, you They make you feel stupid for using something that you have so little appreciation for), they were without tremendous feedback for a while that I thought they had disappeared and suddenly they release 5.0 without possible migration from 4.2… lovely….
Reporting bugs to the community version does not make sense unless you run alongside the developers always using the latest, check this out: https://tracker.zentyal.org/issues/5080#comment:14
In the end you have to die with a relatively stable version and beat it until it lasts, look at the things that my zentyal has in the cron:
0 7 * * 1-6 /sbin/shutdown -r now
As I said ... lovely!
PS: Supposedly I spend all this work to use the free version, supposedly the paid version is serious, but I think it is not the best strategy to gain users, another product with a similar business model is Proxmox and I compared its paid version for such to give money to the project and not because the free version falls short, Proxmox is a gem.
Hello Federico:
With each new article you raise the stop, go as if it were not enough with everything covered in the 3 previous posts about the BIND + DHCP duo, now you publish this "trunk" (excuse me the expletive) of article on how to migrate Microsoft's DNS to the BIND, how to update it from a DHCP in Linux and to top all of the above coexist with a Microsoft Active Directory.
. Great everything related to the DNS SRV records of an Active Directory, its direct zone "_msdcs.domain", how to capture desde Linux the records of the zones - or more - of the Microsoft AD DNS to create the Databases of said Zones in the BIND.
. It is very useful to enable the Logs of the queries in the BIND configuration.
. VERY VALUABLE the advice that: A client who acquires an IP address through a DHCP installed on Linux, will not be able to resolve the IP address of his own name until he is joined to the Active Directory domain. In the example of the Laboratory of the article, first the "win7" computer is assigned the IP address 10.10.10.251 to make DNS checks of the domain "mordor.fan", then it joins from that fixed IP to the Microsoft AD so that finally when If DHCP is installed in Linux, this is the one that assigns its IP and at the same time updates "penetrate" the BIND to write the registry of the equipment in the Forward and Reverse Zones. GO MORE DETAILED YOU WILL NOT FIND!
. Very good all the considerations on the Dynamic Updates in the Microsoft® DNS and in the BIND; as well as all the advice explained in the final section and specifically all the development and the proposed solution to the "Specific Council of which I am still not very clear.
! 5 STARS FOR THE AUTHOR! and I follow the PYMES Series with more and more interest!
Dhunter: Wrote the Voice of Experience. "Practice is the best criterion of truth."
Wong: I already missed your comment - article complement. Hope that one about dnsmasq will be out soon.
Thank you both for your comments.
You have not spoken + about the partner called «El Fueguino», nor about his decision to start the migration of his servers. You stole another from Microsoft, hahaha !!!! ????
hahahaha friend crespo88. I see you liked the wave of the fictional character. If others like you, it could make articles on dense topics more entertaining. Let's wait for other comments about it.