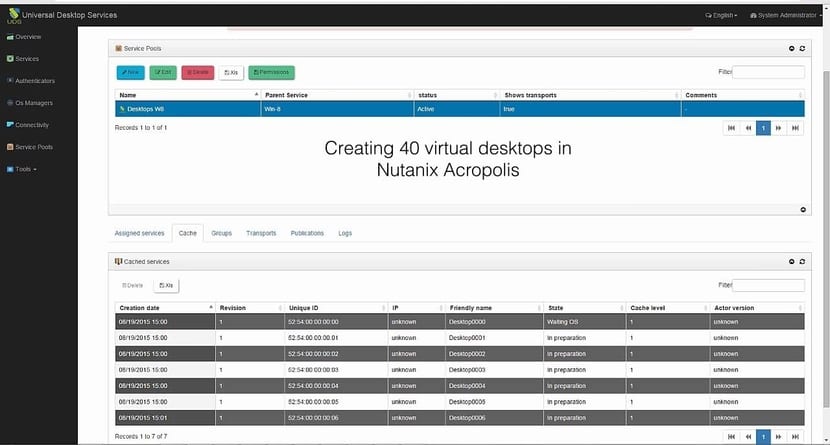
You may have heard of this type of software. But ... what is a connection broker? Basically it is software that acts as an intermediary between users and resources, whether they are physical or virtual. Normally, these types of resources that are accessed are located in the cloud, that is, hosted in a data center and the customer of that service needs to access these resources remotely.
There are some connection borkers that only implement functions of desktop virtualization (VDI) and nothing else, others contribute some functionalities beyond that. For example, some of those compatible with Linux, such as UDS Enterprise, can provide you with tools so that remote users or groups can access those resources and also define how much time or what privileges they will have when exploiting those resources. Furthermore, with UDS Enterprise you can decide the virtual desktop OS to which each user will have access, as well as deciding whether the connection will be made using one or another protocol, and even which authentication system will be used. And you can not only provision and manage VDI, but also facilitate centralized administration and management for application virtualization (vApp), telephony, IP cameras, etc. Therefore, it offers great flexibility in configuring how these remote resources will be exploited.
Other connection brokers alternatives that you will find on the market are Citrix XenDesktop, VMWare Horizon View, Dell vWorkspace, etc., as well as UDS Enterprise, which is a Spanish developer and is totally free (without support), compared to thousands of euros for other similar products. However, if you want support, they also have a paid service for it. An important saving that can be a major boost for your business.