Did you want red pills with cyanide? Here I bring them to you.
A year and a half ago I said that the postman cannot send the letter if the address was encrypted. At the time, the Silent Circle blog (who had shut down their email service at the time) explained why email will never be totally secure, and it's because of the metadata. You will be able to encrypt the body of the message, but you will not be able to encrypt things like the recipient's email address, the day and time it was sent, the subject, etc.
Perhaps that is why the Dark Mail Alliance, founded by Ladar Levison, Michael Janke, Jon Callas and Phil Zimmermann, said in late 2013 that you had to collect money to be able to think of a new protocol for sending emails.
Now, it can be said that there is not just an initial specification (still incomplete but open to the public) but also code that implements it. There are three things: The DIME (Dark Internet Mail Environment) environment and the DMTP and DMAP protocols (which would be substitutes for SMTP and IMAP).
And how it works?
Well, none of the language in the spec is high-level but the key points are:
- Automatic key handling
- Transparent encryption and signing
- Resistance to manipulation by Advanced Persistent Threats
- Relate security to user password and endpoint defenses
- Minimize exposed metadata
- Give user control
And how is it achieved?
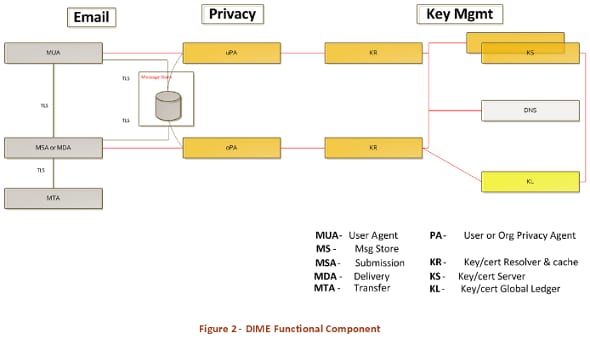
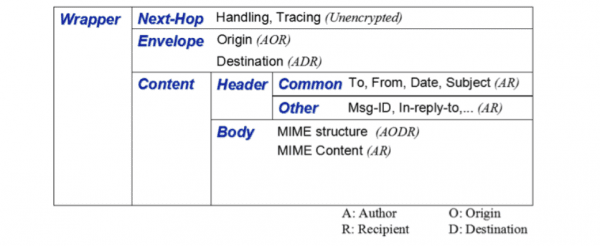
The representation of the message is made up of four elements:
- The wrapper that wraps everything.
- The next hop (Next-Hop) that contains the transport management information (which is in plain text)
- The envelope containing the information of the hosts, encrypted separately (the hosts can only see the information of their own hosts, while the author and the receiver can see the information of both hosts)
- The content that contains the body of the message, the addresses, and the rest of the metadata, also encrypted separately (only accessible to author and recipient)
In turn, DIME distrusts the certification authorities, recommending the use of DNSSEC (Security Extensions for DNS) for the validation of the keys.
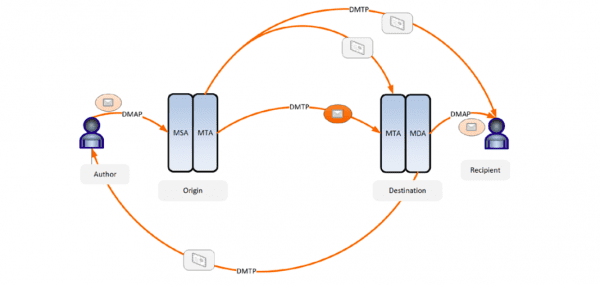
Regarding the protocols, DMTP is almost the same as SMTP except that the mailbox is not included as part of the protocol conversation, the same are the email addresses (which must be extracted from the encrypted message) and that the support for TLS (not because I use it exclusively but to add more security). From DMAP they did not put anything, except that they pretend that it is similar to IMAP but without the server-side search.
The specification also talks about other things like DNS handling record, signet usage, message format, and potential threats handled. And as an ironic icing, a dedication to the NSA for motivating all the effort. If you are interested, you can follow everything in darkmail forums

difficult for it to succeed outside of academic environments of experimentation, or in the field of security, makes the easy difficult ...
As long as Microsoft, Google or Yahoo do not adopt this protocol, it is difficult for darkmail to succeed, since more than 90% of people have an email account in these companies.
I already see a real case: «ok, send me an email ... ahhh I forgot, but you have to have an email account with the darkmail protocol so that we can talk», and if the person is not very knowledgeable in computing, they will look at you as a rare bug.
There is a good niche where to create a new service, for example, where it has both possibilities, by asking first, from the sending host, the receiving host if it has said protocol, but rather asking the user if they want to send it in an "insecure" way.
Does anyone from the community sign up?
in fact, the specifications talk about 4 modes for the server: legacy, experimental, mixed and strict, and based on the modes of the source server and the destination server, you decide whether to send using DMTP or SMTP.
It would be very interesting if this protocol was implemented. Another thing is that it is adopted by the companies mentioned above.