I explained some time ago how to configure the SSH service to work on a different port than 22, which is the default port. The objective of this was that all bots, cracking attacks to SSH are by default to port 22 (which I repeat, is the default), so by changing the port we will obtain more security.
But what to do if I want to configure SSH through another port BUT keeping SSH also on port 22? That is, having the need for the server to have SSH on more than one port, say for example on 22 and also on 9122
For this we modify the configuration file of the SSH daemon:
nano /etc/ssh/sshd_config
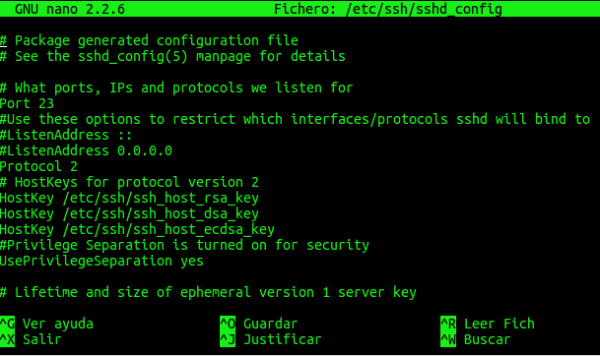
There we will see something like this:
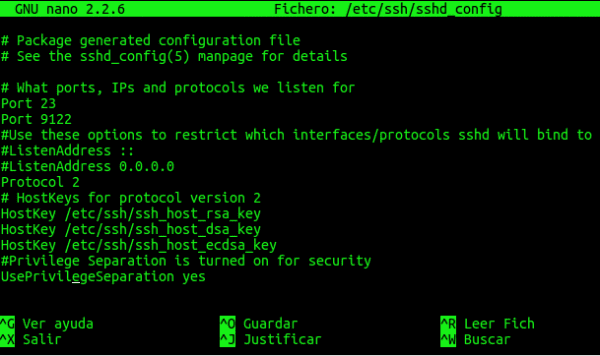
You will see that on line 5 there is something that says: "Port 22", well, we just have to duplicate that line below and change the port number. In other words, for our SSH service to also work for 9122 we must leave it like this:
Then we must restart the service:
service ssh restart
If they use Arch it would be:
systemctl restart sshd
When you want to connect through a port other than 22 remember, you must add -p $ PORT in the connection line, something like this:
ssh usuario@servidor -p 9122
By the way, I recommend you check the sshd_config file from before, there are some very interesting options 😉
regards
Good tips to change the default port of ssh ... to prevent attacks on port 22.
I think that only one port should be left ... and this has to be different from 22 so that the attacks have no effect.
regards
Thanks for reading 🙂
My latest findings have been:
PermitRootLogin on
y
AllowUsers john jack chester…. etc
With this I limit enough the possibilities of cracking, if you add a good iptables ... well we are.
In fact, I prefer to use PortKnocking 😀
As always KZKG ^ Gaara, excellent your articles on SSH. With your guides we are losing the fear of TERMINAL
Thank you
OOOOOOOOhhhh !!!!
Very good article, wild !!!
Apart from changing the port number, to further limit the attacker's options it is also recommended to disable the login with USER: PASS
Password Authentication no
and use private / public key authentication.
Good post.
Salu2