
|
Linux is often used to rescue Windows installations ... or yes. What a great paradox, precisely, there are several free tools to remove malware and rootkits. Let's see some of them. |
chkrootkit
Chkrootkit or Check Rootkit is a famous open source program, it is a tool used for the digitization of rootkits, botnets, malware, etc. on your server or Unix / Linux system. It is tested on: Linux 2.0.x, 2.2.x, 2.4.x, 2.6.x, and 3.xx, FreeBSD 2.2.x, 3.x, 4.x, 5.x and 7.x, OpenBSD 2.x , 3.x and 4.x, 1.6.x NetBSD, Solaris 2.5.1, 2.6, 8.0 and 9.0, HP-UX 11, Tru64, BSDI and Mac OS X. This tool is pre-installed in BackTrack 5 in the Forensic Tools part and anti-virus.
To install chkrootkit on an Ubuntu or Debian based distro, you can type:
sudo apt-get install chkrootkit
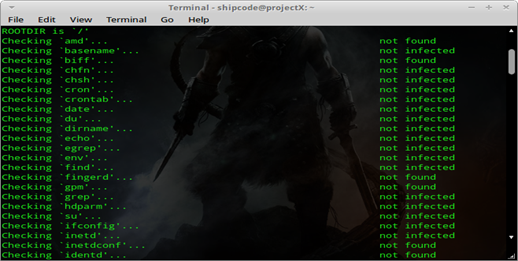
To start checking the system for possible rootkits and backdoors, type the command:
sudo chkrootkit
Rootkit Hunter
Rootkit Hunter or rkhunter is an open source rootkit scanner similar to chkrootkit that is also pre-installed in BackTrack 5 under Forensic and Anti-Virus Tools. This tool analyzes for rootkits, backdoors and local exploits by running tests such as: comparison of MD5 hash, search for default files used by rootkits, wrong file permissions of binaries, search for suspicious strings in LKM modules and KLD, hidden file search, and optional scanning within text and binary files.
To install rkhunter on an Ubuntu or Debian based distro, you can type:
sudo apt-get install rkhunter
To start the file system scan, type the command:
sudo rkhunter --check
And if you want to check for updates, run the command:
sudo rkhunter --update
After rkhunter has finished scanning your filesystem, all results are logged in /var/log/rkhunter.log.
ClamAV
ClamAV is a popular Linux anti-virus software. It is the most famous Linux antivirus that has a GUI version designed for easier detection of Trojans, viruses, malware and other malicious threats. ClamAV can also be installed on Windows, BSD, Solaris, and even MacOSX. Security Research Fellow Dejan de Lucas has a tutorial detailed on the InfoSec Resource Institute page on how to install ClamAV and how to work with its interface on the command line.
BotHunter
BotHunter is a system based on botnet network diagnostics that follows the path of two communication flows between the personal computer and the Internet. It is developed and maintained by the Computer Science Laboratory, SRI International, and is available for Linux and Unix, but they have now released a private trial version and a pre-release for Windows.
If you want to download this program you can do it from here . BotHunter infection profiles are typically found in ~ cta-bh / BotHunter / LIVEPIPE / botHunterResults.txt.
Usage example for BotHunter2Web.pl:
perl BotHunter2Web.pl [date YYYY-MM-DD] -i sampleresults.txt
avast! Linux Home Edition
avast! Linux Home Edition is an antivirus engine offered for free, but only for the home and not for commercial use. It includes a command line scanner and based on the experience of the author of the original note, it detects some of the Perl IRC bots that contain malicious functions such as the udpflood and tcpflood functions, and allows its master or controller of the bot to run Arbitrary commands with the use of the system () function for Perl.
You can download this antivirus software here .
NeoPI
NeoPI is a Python script useful for detecting corrupt and encrypted content within text files or scripts. The purpose of NeoPI is to aid in the detection of hidden code in the web shell. NeoPI's development focus was to create a tool that can be used in combination with other common signature- or keyword-based detection methods. It is a cross-platform script for Windows and Linux. It not only helps users detect possible back doors, but also malicious scripts such as IRC botnets, udpflood shells, vulnerable scripts, and malicious tools.
To use this Python script, simply download the code from its official github site and navigate through its directory:
git clone https://github.com/Neohapsis/NeoPI.git cd NeoPI
ourmon
Ourmon is an open source Unix-based program and a common network packet sniffing tool on FreeBSD, but it can also be used for botnet detection as Ashis Dash explains in her article titled 'Botnet Detection Tool: Ourmon' in Clubhack or Chmag magazine.
Grep
And last but not least, we have the grep command, which is a powerful command line tool on Unix and Linux. Used to find and test probe data sets for lines that match a regular expression. In short, this utility was coded by Ken Thompson on March 3, 1973 for Unix. Today, Grep is known for detecting and searching for annoying backdoor shells and malicious scripts as well.
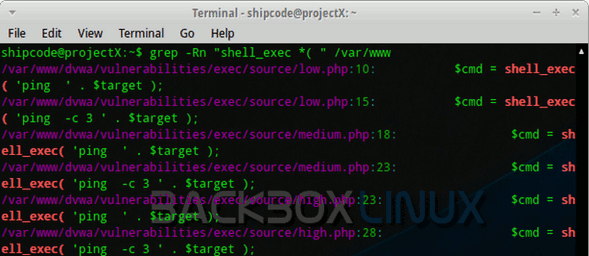
Grep can also be used to detect vulnerable scripts (for example, PHP's shell_exec function which is a risky PHP function that allows remote code execution or command execution). We can use the grep command to look for the shell_exec () to advantage in our / var / www directory to check for possible PHP files vulnerable to ICE or command injection. Here is the command:
grep-Rn "shell_exec * (" / var / www
Grep is a good tool for manual detection and forensic analysis.



About #Avast it's awful… I've had it installed and it doesn't really work at all.
Excellent article… I must try the other tools!
wow! Excellent tools but the avast has not worked for me, it only slows the pc and takes 20 min. to start
Articulation, Pablo 😀
Good day,,
The article is interesting, I am a newbie in this topic, so I ask, in the first option you say how to install chkrootkit, and then the command to check the possible rootkits and back doors in the system, and then what do I do? I delete them, cancel them, block them, and if so, how do I delete or block them?
Thank you
Good article
Hi, I'm Fede, I'm on your very useful page, long live Linux and free software thanks to thousands of programmers and hackers from around the world. Thank you LINUS TOORVALD, RICHARD STALLMAN, ERICK RAIMOND and many others, see you soon and sorry for mistakes in the names THANK YOU.
I do not understand anything the fucking mother!
Look, I don't understand much either, but the other comment said it was good. Clam av apart that it has a tutorial, I think it's best to try that, right? XD
debcheckroot (https://www.elstel.org/debcheckroot/) from elstel.org is missing in this list. It is currently the best tool out there to spot rootkits. Most programs like rkhunter and chkrootkit can no longer detect a rootkit as soon as it has been slightly modified. debcheckroot is different. It compares the sha256sum of every installed file against the package header.