Two days ago we share here on the blog the announcement of the release of the latest version of Firefox, which is version 72 which arrives with various features and news of which only three are the ones that stood out the most from the announcement. Among them, a of which I draw attention of the users is the notification blocking system in the browser.
With this new implementation in Firefox, you can completely stop seeing pop-up notification requests. Because when the user visits a new site that sends similar requests, a small icon will appear in the address bar, swaying from side to side and indicating that Firefox has blocked the next notification.
With that if the user does not want to receive notifications of the site you are viewing, then the icon that appears should simply be ignored. If you need notifications, simply click on the icon and the button to allow notifications is clicked.
Making mention of this new feature in Firefox, Google unveiled little agoor plans to implement the anti-intrusive notification tools from Chrome, similar to those that were offered to users in Firefox 72 some days ago.
Google agreed that most credential-related notifications are displayed on sites in an intrusive manner.
As mentions that instead of showing such notifications when there is a real need of them, sites generally abuse this feature and request confirmation of authority after the first opening of the site, without being linked to the context of the operations carried out.
Such activity, for example, leads to authorization by the user to receive spam requests for push notifications, thereby interrupting the user's work and distracting attention to actions in confirmation dialogs.
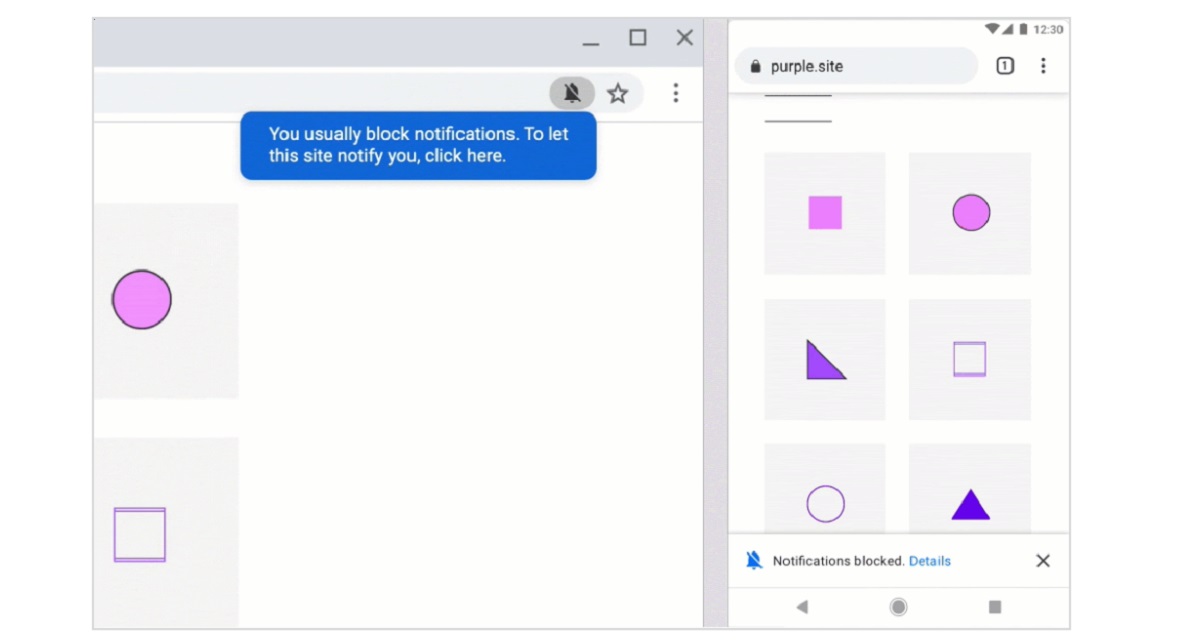
It is because of that Google announced that from the launch of Chrome 80 (scheduled for February 4) it will be possible to display information about authorization requests in a discreet way that requires no action.
Instead of a separate dialogue, a notice will be displayed with a warning about the request being blocked authorization in the address bar, which will then collapse into an indicator with the image of the bell crossed out. By clicking on the indicator, you can activate or reject the requested permission at any convenient time.
In Chrome 80, both in desktop edition and mobile version, the new mode will be applied only under certain conditions, but in the settings there will be an item for your app for all permission requests
Today feature is gradually rolling out on Canary, Dev and Beta channels and can be forcibly enabled in Chrome 80 and later versions. To enable the function simply go to chrome: // flags / # quiet-notification-promptpts.
Automatically, the new mode will be selectively enabled for users that have previously blocked such requests, as well as for sites where a large percentage of rejected requests are recorded.
In the future too it is planned to implement stricter measures to protect against using the interface notifications output by the sites for malicious or fraudulent activities.
It is also not recommended that sites use pop-ups or advertising dialogs that distract with a proposal to subscribe to notifications, which are usually displayed before requesting authorization.
It is recommended that the request be made only after actions initiated by the user, for example when the user clicks a special subscription indicator in the menu or on a separate page.
Also in the ad, Google recommends that developers follow best practices to request permission to notify users. Websites that ask users to sign up for web notifications when they first arrive often have very low acceptance rates.
Source: https://blog.chromium.org