
|
The encryption or encryption of files, texts, etc. It is a tool that all Linux users should know about and that, unfortunately, few know and use on a daily basis. This is especially striking when you consider Linux's reputation as a "secure operating system"; This is one more tool that Linux puts at your fingertips to improve your security. Why don't you use it? Out of ignorance? Well, this post comes to fill that "gap"The easiest method to encrypt information is by using GNU Privacy Guard (GPG). This mini how-to describes its installation and handling in Ubuntu from head to toe. It took me almost 2 days to write it, so I hope you find it useful. |
How GPG works
GPG uses a hybrid system that combines symmetric and asymmetric encryption.
Asymmetric encryption always works with a key pair. One of them will be you "public" key and the other you "private" key. As its name indicates, the public key can be given to those to whom you want to send encrypted messages and there is no danger if someone else sees it, in fact, they are usually published on public servers to facilitate their access; The private key, on the other hand, must be secret and you do not have to share it with anyone. The most beautiful thing about all this is that, as we will see below, both keys are created directly by GPG based on your personal data. The last step is to "seal" these two keys through a "passphrase". So, in the end, the only password you will have to remember is your "passphrase".
Passing on clean, thanks to the asymmetric encryption, If the sender uses the recipient's public key to encrypt the message, once encrypted, only the recipient's private key will be able to decrypt this message, since they are the only one who knows it. Therefore, the confidentiality of the sending of the message is achieved: nobody except the recipient can decrypt it. If the owner of the key pair uses their private key to encrypt the message, anyone can decrypt it using their public key. In this case, the identification and authentication of the sender is therefore achieved., since it is known that only he could have used his private key (unless someone could have stolen it).
One last comment that I find interesting to mention is that asymmetric ciphers were invented in order to completely avoid the problem of key exchange of symmetric ciphers. With public keys, it is not necessary for the sender and the recipient to agree on the key to use. All that is required is for the sender to obtain a copy of the recipient's public key before initiating the secret communication. What's more, that same public key can be used by anyone who wants to communicate with its owner.
How safe is GPG?
El algorithm used by GPG is DSA / ElGamal, since it is "free" and no "proprietary" patents fall on it.
Regarding the key length, depends on user requirements. It is necessary to balance between safety and process optimization. The larger a key, the lower the risk that the message will be decoded if it is intercepted, but the time it will take to calculate the processes will also increase. The minimum size that GnuPG requires is 768 bits, although many people think it should be 2048 (which is the maximum with GnuPG at the moment). When security is a higher priority than time, the option is to choose the largest key size that is allowed.
Installing GPG on Ubuntu
Ubuntu comes "out of the box" with GPG and a graphical interface for GPG called Seahorse. To access Seahorse we just have to go to Applications> Accessories> Passwords and encryption keys.
Before that, I recommend opening a terminal and typing:
sudo aptitude install seahorse-plugins sudo killall nautilus
What this does is allow us integrate GPG to Nautilus. From now on, if we right-click on a file, we will see two more options appear: "Encrypt" and "Sign". We will see how to use these new tools below.
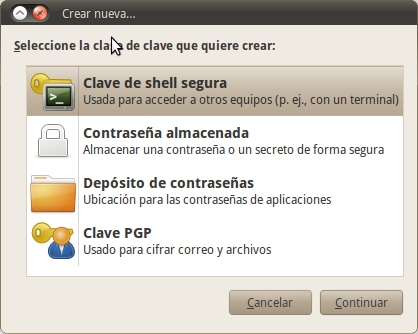
Create the keys
Before starting to encrypt messages and files, as we saw, it is necessary to first create our asymmetric keys and our "passphrase". To do this we go to Applications> Accessories> Passwords and encryption keys. Once there we go to File> New> PGP Key.
The system will then ask us to enter our name, email address and a comment. The latter is optional, while the first two are mandatory. The email address chosen should be a valid one, as it will be used to sign the user identifier. If this address is modified in any way, the signature will not correspond. The keys will be generated based on this data.
In section Advanced key, you can select a different type of encryption. The recommended one is "DSA Elgamal 768 bits" but I recommend that you change it to "DSA Elgamal 2048 bits" as it is considered sufficiently secure and flexible. The expiration date is the date the key is no longer useful for encryption or signing operations. 6 months is a reasonable time for this. You will have to change the expiration date or generate a new key or subkey after this period of time has passed.
The last step is to enter a password. Note the difference between the Anglo-Saxon terms for the word "password": the term "Password»Indicates a« password », while the term«passphrase»Indicates a«phrase on the way". Therefore this password must be made up of more than one word. For a password to be effective (secure), you must:
be long;
combine uppercase, lowercase and numbers;
contain special characters (not alphanumeric);
be hard to guess. Therefore, other than names, significant dates, telephone numbers, document numbers, ...
In general, to create a strong password It is advisable to intercalate capital letters with minusCulas, numbers, other non-alphanumeric characters, etc.. When choosing words and phrases we must avoid those too obvious words, or significant dates, and never use quotes from books or famous phrases. That said, we must ensure that the password we choose is difficult enough that it cannot be breached by a "brute force attack" or even a "dictionary attack", but easy enough for us to remember it. If we forgot a password, our key would be totally useless, and the cryptograms with it encrypted, indecipherable. Given this possibility, it is recommended to always create revocation certificates together with the keys.
Once all the required data has been entered, the key generation process begins, which takes considerable time depending on the size of the keys and the speed of your computer. During this process the program collects random data that it will use to generate the keys. Once finished, Seahorse will close.
Public key servers
Publish my public keys
Public key servers are used to precisely distribute public keys. In this way, it is very easy to search for someone (by name or email) in the database and find their public keys to send them encrypted messages (that only he / she can decrypt).
To "upload" your public keys to these servers, you only have to open Seahorse, select your key and go to Remote> Synchronize and publish keys. An alert will appear advising us that this will cause the publication of the selected public keys.
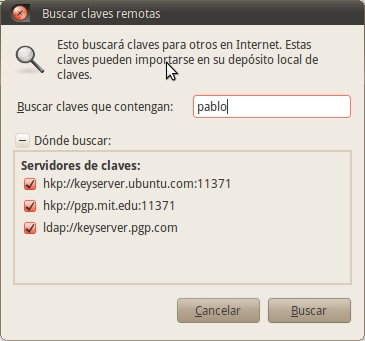
Get the public keys of my friends
Open Seahorse and go to the menu Remote> Find remote keys. Enter the name or email of the person you are looking for. Then select the corresponding key. When you finish you will see that the new key has been added to the "Other keys" tab.
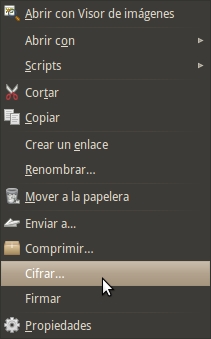
(De) Encrypting files and folders
Once the key pair has been generated, encrypting and decrypting files is quite simple. You just have to select a file, right click and select "Encrypt".
In the dialog that appears, select the key you created earlier, and click OK.
If you selected a folder to encrypt, it will ask you if you want to encrypt each file within the folder separately or if you prefer that a ZIP file be created that will later be encrypted. The second option is the best in most cases.
If you are encrypting a file, once the encryption is complete, you should create a file of the same name but with the extension .pgp. Once the process is finished, you can delete the old file. If you encrypted a folder, you should find two new files: the encrypted version with the extension .pgp and a .zip file with the original version of the folder. Both the ZIP and the original folder can be deleted after encryption.
For security reasons, unencrypted versions of files should be permanently deleted, rather than simply being sent to the recycle bin. But first make sure to try decrypting the encrypted file, to see that everything is fine.
To do this, you just have to double click on the .pgp file and enter the password when it asks for it. The original file will then reappear. In case it is a folder, the .zip file will appear, and you must then extract its content.
Decrypting files on my other computer
This is not a system designed to create portable encrypted files (as TrueCrypt). To decrypt your own files on another computer, you have to export your key and then import it in the second compu. This represents a security risk. However, sometimes it may be necessary to perform this task (for example, if you have a PC and a notebook and want to have a single GPG key pair and not one for each computer as if they were different "identities"). So, here are the steps to follow in that case:
On the computer where you created the keys, launch Seahorse (Applications> Accessories> Passwords and Encryption Keys), and right-click on your personal key and select "Properties."
In the dialog box that appears, click on the "Details" tab, then on the "Export" button next to "Export full key". Save the file to your desktop. You will find that a new file has been created with the extension .asc. They are your keys in plain text.
Copy the .asc file to a USB stick, and from there to the second computer. Now on that computer start Seahorse and click on the "Import" button. Navigate to where you saved the .asc file, and click "Open." This will import the key. Close Seahorse and double click on any file encrypted with your key to decrypt it. It will ask you for the passphrase, so write it down. After this, the original file will be saved in the same folder where the .pgp file is.
Finally, keep in mind that the time and date of the computers where you create / import / export the keys must be correct. For various technical reasons, Seahorse and the gpg command cannot import a key if the time and date on the PC is less than the date it is created. Of course, this means that if the computer where you created the key has the wrong date, it could give you quite a bit of trouble creating and using the key.
Encrypt text
There is a Gedit plugin to encrypt selected text. To enable it, go to Edit> Preferences> Plugins. I chose "Text Encryption". Once the plug-in is enabled, the options in Edit> Encrypt / Decrypt / Sign will be enabled.
GPG and Firefox
There is a plug-in for Firefox (FireGPG) that provides an integrated graphical interface to apply GPG operations (including (de) encryption, signature, and signature verification) on any text on a web page.
FireGPG it also allows working with webmails (Gmail, etc.), although at the time I tested it the integration with Gmail was "broken". To see a complete list of webmails that FireGPG works with: http://getfiregpg.org/s/webmails
Download FireGPG: http://getfiregpg.org/stable/firegpg.xpi
Speeding up the encryption process a bit ...
To (de) encrypt information using always the same "identity", I recommend that you go to System> Preferences> Encryption and key stores. Then I accessed the tab "Encryption", and where it says "Default key" select the key that you will always use to (de) encrypt information. If you are curious, I recommend that you also take a look at the tab "PGP Passphrase" to tune your GPG to the maximum.
Sign and Verify
Many times, you don't want to send an encrypted email, but you do want the recipient to be certain that it was I who sent it. For that, digital signatures are used. All you need to do is verify the email using GPG and the sender's public key.
To encrypt an email, as we saw, a pair of keys is used. One of them is secret and the other public. In the case of the digital signature, all the people who receive an email signed by me will be able to verify that this email was written by me and that the email was not maliciously altered on the way, using my public key, since I signed it using my private key.
For this reason, one of the great problems of encryption is precisely that the issuer has to be very sure that the key or, in the case of the digital signature, that it really belongs to the person who claims to be the owner of the the signature. After all, I can claim to be "Monica Lewinsky" and put her name in my digital signature. To solve this problem, there is the signing of the public keys. So, when someone signs my public key, they are confirming that that key belongs to me. In other words, they are vouching that this key is mine. The mutual signing of keys forms, according to Robert De Niro, a "web of trust" or "network of trust". For more information on the subject I recommend you visit http://www.rubin.ch/pgp/weboftrust.
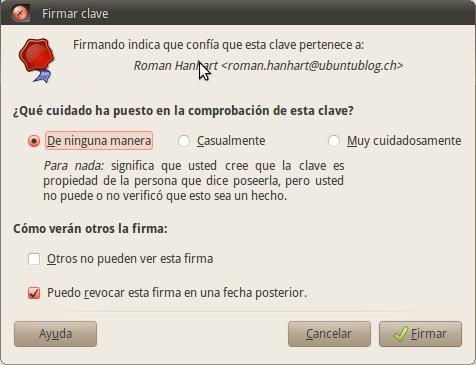
To sign a key in your keystore:
1) Select the key you want to sign from the Trusted keys or Other collected keys tabs,
2) Choose Sign on the toolbar or File> Sign,
3) Select how thoroughly you checked the key,
4) Indicate if the signature should be local to your key deposit and if your signature can be revoked,
5) Click Sign.
GPG and Thunderbird
There is a plug-in for Thunderbird and Seamonkey called Enigmail that allows you to write and receive signed and / or encrypted messages using GPG.
The first time you run this plug-in, a series of forms will appear that you must complete. It also includes guides that explain how to use GPG.
For more information about GPG I recommend reading:
- GNUPG Mini Like: http://www.dewinter.com/gnupg_howto/spanish/index.html
- The help that comes in Ubuntu from the manual of passwords and encryption keys. Open Seahorse> Help> Index.
- http://aplawrence.com/Basics/gpg.html
- http://commons.oreilly.com/wiki/index.php/Ubuntu_Hacks/Security#Encrypt_Your_Email_and_Important_Files
- http://ubuntuforums.org/showthread.php?t=680292



Writing allows me to mastermind my thoughts, planetary and Digital scholarship standards by
share-out their ideas with one another on the classroom Web log situation
blogging with Mrs. Lanphear. gift bags are Component
part of all acknowledge that isn't the way to deal switching to something new.
So visit my page: click here
Good Pablo! I do not know if it is my browser, but the text of this tutorial is cut off, that is, I am missing the end of each line. Thanks for the help!
Your tutorial is very nice !! Good wey, I've been looking for help! So good!!
pD: Those who have doubts read well assholes! that good vibes !!
DALE CHIDO MAN !!! VERY GOOD TUTO THAT ONDAAAAA
Chee !! yenoo my cheleee b0las !! papahuevoo !! What ric000 frut000 papitoo !! the conxa of the l0ra pendej00s !!
In Firefox it looks good ...
good article! very interesting. tonight I reread it with more time
Grateful friend .. Greetings from Venezuela.
Dear User,
I am very grateful for your excellent work and, also, for sharing the compilation of the procedure to generate this tutorial.
Best regards,
D.
Buenos Aires.
Wow! Very good tutorial!
I only have one doubt ... When I export my key to the .asc file, does it export both public and private keys? I have that fear of losing the private one, because the public one is already online, but the private one is somewhere in the system that I don't know about; I want to make a copy of it and have the two keys in a secret USB. Also, I would like to have that "synchronization" of identities between 2 machines.
If you are so kind to clarify my doubt, or declare where my private key is (I already looked in ~ / .gnupg but I don't know what it is) I will be very grateful 🙂 if you can email, better, you will find it in my Disqus profile .
Regards!
HaD!
I think I already got the hang of it; I'll test about it later ...
So, now it remains to know how to rescue my private and public key by terminal, because I believe that now I sent both to the server in Launchpad !! D: (I say it because I sent him the text that he gives me for "exporting" my key -which apparently are the two keys-)
Thanks for your answer!
HaD!
Hello:
GnuPG uses patent-free algorithms, but I would like to know if SMIME uses algorithms that are not free software.
Thank you
Look, from what I understand, s / mime is an "open standard" and GNUPG (since version 2) has support for s / mime. In short, I think that if the people at GNUPG incorporated it, it is because their algorithms are free and the standard is open, so you can use it without problems.
The truth is I do not know. Anyway, don't you think it's time to update? Cheers! Paul.
On 06/12/2012 18:06, «Disqus» wrote:
… It still has support (LTS)… 😉… thanks anyway.
salu2.
Do you know if there is a seahorse bug on 10.04?… In another version it is perfect but in 10.04 it gives an error when generating the key.
PIECE OF TUTORIAL! Here is my final practice of Hardware Fundamentals xD
Thanks Piter! I am happy that is was useful for you. It was the idea ... 🙂
A hug! Paul.
I don't like it at all it's disgusting !!!!!!!!!!!!!!!!!!!
They can also use the FNIB service, encrypted mail through the use of Swiftcoins.
http://www.youtube.com/watch?v=U3_pMGXlOMM
Hello
very good post
but I have some doubts ...
I was currently on maivelope but it's giving me problems
I can't decrypt the emails they send me using PGP
It turns out that I have a contact who has sent me a message using PGP but I can't decrypt it, I get this: Error! No private key found for this message. Required private key identities: 187C3E990A964C30 or BDA0CFE6BF5E5C1C I already tried to send a message with the private key and even so I get that ... what am I doing wrong?
and I have switched to Portable PGP but I don't know what the passphrase is ...
I don't remember that in maivelope he asked me or I did something to make it appear ...
Great tutorial!
Whoever says it's disgusting doesn't know what's going on
Hey.
I can't get it to appear after clicking the file or folder to encrypt the drop-down (by clicking the right button) so that it appears encrypt, but it doesn't. It happens to me on both lubuntu 16.04 and xubuntu 16.04
Hi, I can't use the first code "sudo aptitude install seahorse-plugins" tells me: "sudo: aptitude: command not found".
Hello, in Ubuntu 19.10 the first command does not accept me, it tells me that this package is not available but that it is referred to another package. It also says that the seahorse-plugins package is missing, obsolete, or available from another source.
regards