Not long ago I explained how to know which IPs have been connected by SSH, but ... what if the username or password was incorrect and they didn't connect?
In other words, if there is someone trying to guess how to access our computer or server by SSH, we really need to know, or not?
For that we will do the same procedure as in the previous post, we will filter the authentication log but this time, with a different filter:
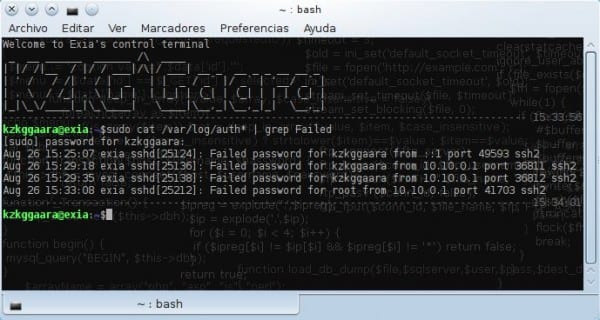
cat /var/log/auth* | grep Failed
I leave a screenshot of how it looks:
As you can see, it shows me the month, day and time of each failed attempt, as well as the user with which they tried to enter and the IP from which they tried to access.
But this can be arranged a bit more, we will use awk to improve the result a bit:
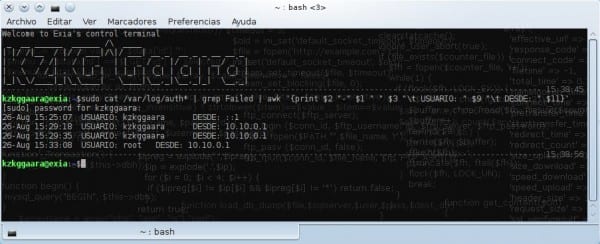
cat /var/log/auth* | grep Failed | awk '{print $2 "-" $1 " " $3 "\t USUARIO: " $9 "\t DESDE: " $11}'
Here we see how it would look:
This line that I just showed you should not be memorized all by heart, you can create a alias for her, the result is the same as with the first line anyway, just a little more organized.
This I know will not be useful to many, but for those of us who manage servers I know that it will show us some interesting data hehe.
regards
Very good use of pipes
regards
Thank you
Excellent the 2 post
I always used the first one, because I don't know awk, but I'm going to have to learn it
cat / var / log / auth * | grep Failed
Here where I work, at the Faculty of Mathematics-Computing at the Univ de Oriente in Cuba, we have a factory of "little hackers" who are constantly inventing things that they shouldn't and I have to be with 8 eyes. The ssh theme is one of them. Thanks for the tip dude.
One doubt: if one has a server facing the internet but in iptables one opens the ssh port only for certain internal MAC addresses (let's say from an office), access attempts from the rest of the internal addresses would reach the authentication log and / or external? Because I have my doubts.
In the log what is saved is only the requests allowed by the firewall, but denied or approved by the system as such (I mean the login).
If the firewall does not allow SSH requests to pass, nothing will reach the log.
This I have not tried, but come on ... I think it must be like this 😀
grep -i failed /var/log/auth.log | awk '{print $ 2 «-» $ 1 »» $ 3 «\ t USER:» $ 9 «\ t FROM:» $ 11}'
rgrep -i failed / var / log / (logrotates folders) | awk '{print $ 2 «-» $ 1 »» $ 3 «\ t USER:» $ 9 «\ t FROM:» $ 11}'
in centos-redhat… ..etc ……
/ var / log / secure