This post tries to clarify a little about how networks work and how to turn our Linux equipment into a Router that ensures a little more our network, whether at home or even business. So let's get down to business:
Routing and filtering
To talk and understand about routing we can first define what is the function of the router? For this we can say that a router, in addition to creating a network and allowing connection with other equipment (knowing that we can do this with an AP, Switch, Hub or others) has the ability to connect two different networks to each other.
As we can see in the image, there is a local network "10.0.1.0" that is created by the router, and reaches one of its two interfaces. Then the router on its other interface, has another network, with its public IP with which it can connect to the Internet. The routing function is basically to serve as an intermediary between these two networks so that they can communicate.
Linux as a router.
Naturally, the Linux Kernel already has the ability to do "forwarding", but by default it is disabled, so if we want our Linux to do this work we must go to the file.
/proc/sys/net/ipv4/ip_forward
There we will find that it is a file that only contains a zero "0", what we must do is change it to a one "1" to activate this behavior. This unfortunately is deleted when we restart the computer, to leave it activated by default we must use the command:
sysctl net.ipv4.ip_forward=1
Or edit it directly in the file /etc/sysctl.conf. Depending on the distribution this configuration can also be in a file in /etc/sysctl.d/.
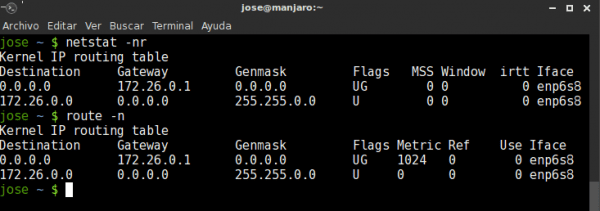
By default our Linux must have a routing table, which is generally the configuration of our lan network and connection to the router. If we want to see this routing we can use two commands:
route -n
o
netstat -nr
Both commands should return the same.
In general, this configuration is enough for your Linux to serve as a Gateway and other computers can navigate through our computer. Now, if we want our Linux to connect two or more networks, whether local or not, for example, we can make use of static routes.
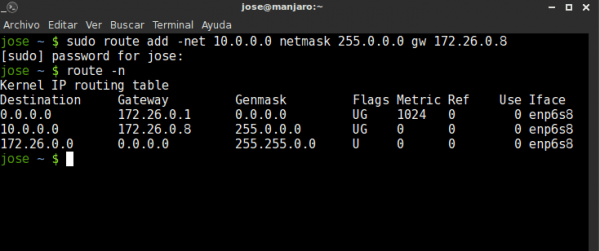
Suppose my Linux has two network interfaces, the first one has an Internet connection whose network is 172.26.0.0 and the second one (10.0.0.0) has some computers from another local network. If we want to route packets to that other network we can use:
route add -net 10.0.0.0 netmask 255.0.0.0 gw 172.26.0.8
In general it is:
route add -net REDDESTINO netmask MASCARA gw IPDELLINUX
if we give route regardless of whether this network exists or not, this routing will be fixed in our table.
If we want to eliminate said routing we can use
route del -net 10.0.0.0 netmask 255.0.0.0
iptables.
Basically iptables is used for filtering packets, outgoing, incoming or others, this makes it a great tool for managing our network traffic. Well, iptables, just as it allows us to filter the traffic from the same computer, it also allows us to filter the traffic that passes through it. (Forwarding). Iptables can be divided into tables, chains, and actions.
- Boards: basically there can be two tables, filters, to filter packets and nat to translate addresses, that is, to move from one network to another.
- Cadenas: The chain refers to the type of traffic that we want to filter or swim, that is, to which traffic are we going to apply the tables? and they can be: INPUT: Incoming traffic, OUTPUT: outbound traffic or FORWARD: Traffic that passes through it, but it is not a proper connection.
- It may also appear POST-ROUTING, which is used to treat the packet in a certain way after it has been routed.
- Actions: Actions are basically the action to be performed with the chain. This action can be Dropp that just destroys that traffic or ACCEPT. that allows traffic to do that action.
IPTABLES rules are saved and executed in the order that they were created, and if a rule deletes a previous rule, the last rule in the order is always applied.
Firewall Policies.
In general, firewalls naturally work in two ways:
- Allow all traffic except, or
- Do not allow any traffic except ...
To apply policies use IPTABLES - P ACTION CHAIN
Where the string represents the type of traffic (INPUT, OUTPUT, FORWARD, POSTROUTING ...) and the action is DROP OR ACCEPT.
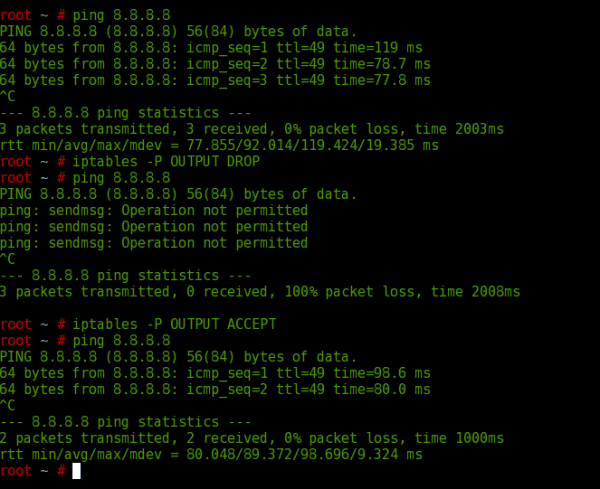
Let's look at an example.
Here we see that at first I was able to ping, then I told IPTABLES that all OUTPUT traffic was DROP or not allowed. Then I told IPTABLES to accept it.
If we are going to build a firewall from scratch we must always apply the rules of (Do not allow any traffic except ... For this then we apply the rules
iptables -P INPUT DROP iptables -P OUTPUT DROP iptables -P FORWARD DROP
To return we write the same and replace DROP with ACCEPT.
At this point, since all traffic is denied, we begin to tell our IPTABLES what traffic it can have.
The syntax is:
iptables -A cadena -s ip_orgigen -d ip_destino -p protocolo --dport puerto -j acción
Where:
String = INPUT, OUTPUT or FORWARD
origin_ip = Origin of the packets, this can be a single IP or a network and in this case we must specify the mask).
destination_ip = where the packets are going. this can be a single IP or a network and in this case we must specify the mask).
protocol = indicates the protocol used by the packets (icmp, tcp, udp ...)
port = destination port of the traffic.
action = DROP or ACCEPT.
Example:
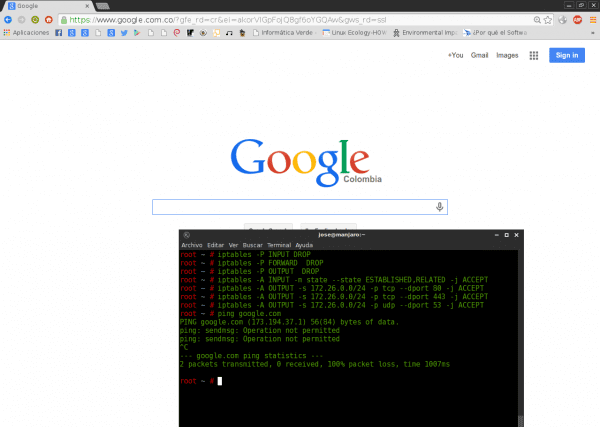
ALL restricted policies apply.
Then we add the rules to be able to have traffic through port 80 HTTP and 443 HTTPS, with the TCP protocol. Then port 53 It is applied for the DNS client to resolve the domains, otherwise you will not navigate. This works with udp protocol.
The line:
iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT
It is because of the following: When you make an HTTP request for example, you connect to port 80 of the server, but the server to return the information needs to connect to you through any port. (Generally greater than 1024).
As all our ports are closed this will not be achieved unless we open all ports higher than 1024 (Bad idea). What this says is that all incoming traffic that comes from a connection that I established myself is accepted. I mean, a connection that in principle I started.
I hope you liked this information. In the next one I will talk about NAT, Proxy and scripts for Firewal.


This is the basis that many entrepreneurs take to manufacture their own firewalls, that is why there are so many brands of firewalls with embedded linux on the market, some good and others not so much.
Excellent article. I look forward to the second part.
Very good explanation, it helped me to understand the proxy of my work. Thank you
Hello Jlcmux,
Excellent, I really liked it, when will the other party be available?
Greetings and thanks for sharing
Thanks for the comment.
I sent the other part yesterday, in the course of the day I think they will be publishing it.
Greetings.
Very good article friend @ Jlcmux, I really learned with him since he clarified some doubts that I had for some time, by the way you would not mind sharing the book of the source of the article, that of Sébastien BOBILLIER, well slau2s and now to see the 2nd part, salu2s.
Hello Thanks for commenting Israel.
It turns out that I have the book in physical form. But I found this link on Google Books. http://books.google.com.co/books?id=zxASM3ii4GYC&pg=PA356&lpg=PA356&dq=S%C3%A9bastien+BOBILLIER+Linux+%E2%80%93+Administraci%C3%B3n+del+sistema+y+explotaci%C3%B3n+de+los+servicios+de+red#v=onepage&q=
I think it's complete.
Very good article, I add a query: What would be the advantage of using linux as a router, if there is any, with respect to hardware dedicated to it? Or is it just for exercise? I know there are dedicated distros but I don't know if they are to salvage old PCs or provide more flexibility in configuration.
Well, I think the advantages and disadvantages depend on the scenario where you are going to implement this. Why surely you are not going to buy a UTM or something like that for your house? And maybe for a small business that can't afford it either. It is also good as an exercise, as it helps you understand all the logic of this and you can better configure a dedicated FWall. In addition to that almost all these devices really what they have is Embedded Linux.
Greetings.
Hello, a question, can you generate an "artificial" interface in linux for similar routing between networks? (packet tracer style) to work with virtual machines? eg if I have eth0 (because I have a single card of course) can I create eth1 to make another network? Very good tutor!
In Linux you can create virtual interfaces, of course. If you have eth0, you can have eth0: 0, eth0: 1, eth0: 2 ... etc
So good, thanks for sharing