Linux Audit Framework: All About the Auditd Command
A few days ago, starting in February, we boarded a special post a great one collection of essential commands (basic and intermediate) available on most free and open operating systems based on GNU/Linux. Consequently, some were very simple, and with which folders and files could be manipulated, and information displayed on them. While others were more complex, and with which configurations and parameters could be managed.
But, this collection only covered a modest 60 linux commands. And given that, on average, there are hundreds of commands available in most GNU/Linux Distributions, it is time, little by little, to address other similar or more important, advanced or specialized ones. Such as, the Linux Auditd Command o "Linux Audit Framework", which we will address today in this post.
Linux commands: The most essential to master in the year 2023
But, before starting this interesting post about the Linux Auditd Command o "Linux Audit Framework", we recommend the previous publication, for later reading:


Linux Audit Framework: Powerful Linux auditing environment
What is the Auditd Command (Linux Audit Framework)?
Briefly, we could describe said audit command as, a software tool (framework) auditing for Linux, which provides a CAPP compliant audit system (Controlled Access Protection Profile, in English, or Controlled Access Protection Profile, in Spanish). So it is able to collect information reliably about any event relevant (or not) for security in a Linux operating system.
Consequently, it is ideal to support us when making monitoring of the actions carried out in an OS. In this way, the Auditd command or the Linux Audit Framework (Linux Audit Framework or LAF) is able to help us maintain our most secure OS, thanks to providing us with the necessary means to analyze what happens in it with a great level of detail.
However, and as is to be understood, does not provide additional self-confidence, that is, it does not protect our OS against code malfunction or any type of exploitation by malicious software or intrusive attacks. But, It is useful for tracking down potential problems for further analysis and correction., in such a way, to take additional security measures to mitigate them and even avoid them. Finally, The LAF it works by listening for events reported by the kernel and logging them to a log file for later analysis and reporting back to the user.
It is a user space tools for security auditing. The audit package contains the userland utilities for storing and searching the audit logs generated by the Linux kernel audit subsystem, from version 2.6 onwards. auditd package (on Debian)

How do you install and use the Auditd command?
Like most commands, via Terminal (CLI), it can be easily and routinely installed. using the default or preferred package manager of your GNU/Linux Distro.
Eg Debian GNU / Linux and derivatives would be:
sudo apt install auditdMeanwhile in Fedora GNU/Linux and Red Hat, and its similar would be:
sudo dnf install auditdsudo yum install auditAnd for its basic and default use, it is only necessary to execute the following command orders:
- Check execution status
sudo systemctl status audit- Enable background service
sudo systemctl enable auditd- View currently configured rules
sudo auditctl -l- Creation of display rules (watch) or control (syscall)
sudo auditctl -w /carpeta/archivo -p permisos-otorgadossudo auditctl -a action,filter -S syscall -F field=value -k keyword- Manage all created rules
sudo vim /etc/audit/audit.rules- List all the events that have to do with a specific process according to its PID, associated keyword, path or file or system calls.
sudo ausearch -p PIDsudo ausearch -k keywordsudo ausearch -f rutasudo ausearch -sc syscall- Generate audit reports
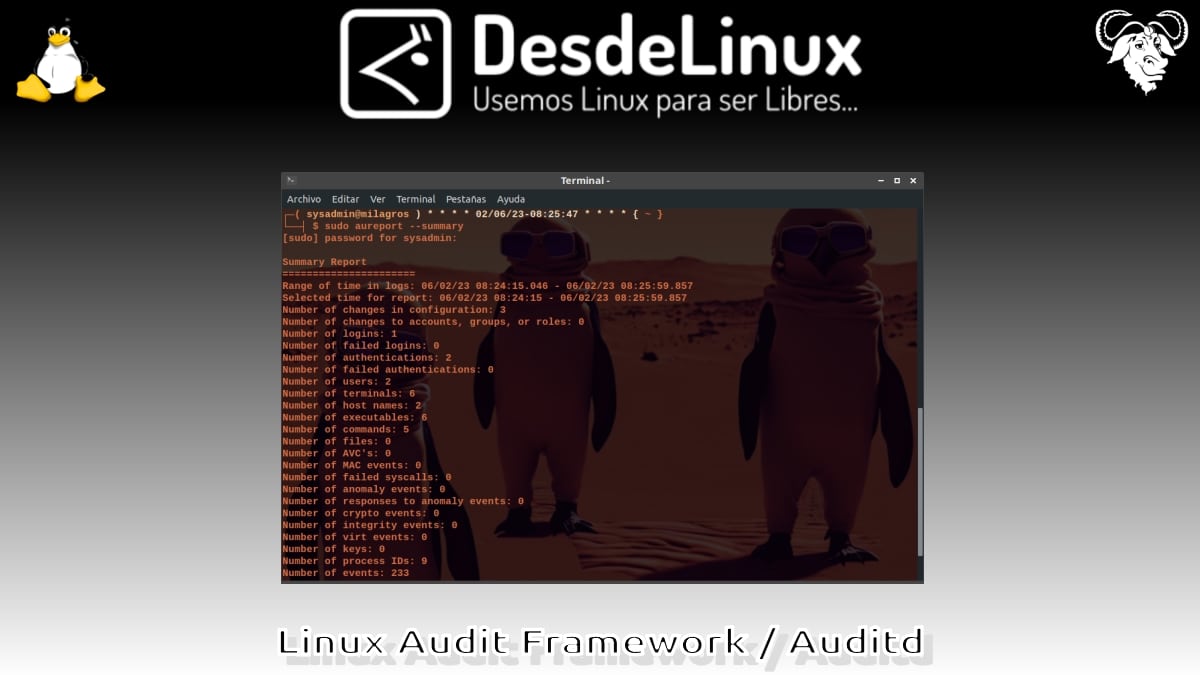
sudo aureport -nsudo aureport --summarysudo aureport -f --summarysudo aureport -l --summarysudo aureport --failed- Trace the execution of a process
sudo autracet /ruta/comandoHowever, to learn more about it We recommend exploring the following links:
- Debian Manpages: Auditd
- Official Web site
- Official section on GitHub
- ArchLinux Wiki: Auditd
- Red Hat Linux Security Guide: Auditing the System Chapter
- SUSE Security Guide: Chapter The Linux Audit Framework
- OpenSUSE Security and Hardening Guide: Chapter The Linux Framework Audit
Summary
In summary, we hope that this publication related to the powerful auditing environment integrated in GNU/Linux known as "Linux Audit Framework", which is provided through the Linux Auditd Command, allow many, the power audit (examine and evaluate) all the activity of its free and open operating systems based on GNU/Linux. And thus, they can easily detect and correct any anomalous, inappropriate or harmful configuration or activity promptly.
Finally, do not forget to contribute your opinion on today's topic, via comments. And if you liked this post, do not stop sharing it with others. Also, remember visit our home page en «DesdeLinux» to explore more news, and join our official channel of Telegram from DesdeLinux, West group for more information on today's topic.