Those who are aware of the news on the internet, news linked to Anonymous, their actions, they will know that websites such as the FBI, CIA, US Department of Justice, and many other important sites (Interpol, Vatican, etc) have been offline for several hours ... so as not to make the story too long 🙂
Just a few days ago the news came out that the administrators of the popular website Taringa are accused and will face "justice" in a trial. And actions by Anonymous They did not wait, because they quickly went offline (through DDoS attacks) various government sites from Argentina.
But… What is a DDoS attack?
I'll explain it as simple as possible 🙂
Attack DDoS means attack of Denial of Service. And in short, it is about accessing thousands of thousands of times to a website. In other words, if you or I now enter X site, this generates a certain load (it puts the server where the site is to work) ... 100 or 1000 people accessing the same site will generate a load greater than 10, that is logical. Well, DDoS attacks are the equivalent of hundreds of thousands (millions) of users accessing the same website PER SECOND. That is, 100.000 supposed users access, but after 1 second more are added ... and more and more per second. consequences? ... simple, there will come a time when the workload of the server (where the website is) will be so much, but SO MUCH, that it simply runs out of RAM, and can not do anything else ... and this my friends, will make the website goes offline.
I tried to explain it as simple as possible hahaha. That is why perhaps the most knowledgeable I know that they will find some other error or detail that has been excluded, my apologies for this 😉
Now, here I will teach you how to do those attacks DDoS, using a tool developed by the same Anonymous: LOIQ.
Yes ... exists LOIC, Meaning Low Orbit Ion Cannon, and can be used on Windows, Mac or Linux. The problem is that to use it in Linux, you need to install Wine and in this (in Wine) the Windows Net.Frameworks. That is, to make it work in Windows you need to emulate the LOIC (.exe) in our distro. Another way (which I haven't tried) is using Mono libraries.
I personally don't like either of these two alternatives. I don't really like using Wine, and I really hate Mono ¬_¬… so what to do in this case?
Fortunately, there is a version of LOIC call LOIQ (change from C to Q) written in C ++ ... and uses Qt libraries 😀
Simply put ...
We just go down a .tar.gz, we unzip it, and we just run the loiq file and BINGO !! we have LOIQ (which is the same as LOIC) open in our distro, and ready to use 😉… or !! … They can simply install a .deb and voila 😀
Here are the download links:
LOIQ (Low Orbit Ion Cannon in C ++ and Qt) -" Archive .DEB
LOIQ (Low Orbit Ion Cannon in C ++ and Qt) -" Archive .TAR.BZ2
I directly use the .tar.bz2, because this way I save having to install another package as such on my system.
That is, for me to execute it, I download the .tar.bz2, unzip it, and execute.
I will leave you a command that will do the following:
- Download the .tar.bz2 package
- Unzip it.
- And it will allow you simply by typing in a terminal «loik»(Without the quotes) have the application run for them.
cd $HOME && wget http://ftp.desdelinux.net/loiq-0.3.1a.tar.bz2 && bzip2 -dc loiq-0.3.1a.tar.bz2 | tar -xv && mv loiq-0.3.1a .loiq-0.3.1a && sudo ln -s $HOME/.loiq-0.3.1a/loiq /usr/local/bin/
They will be asked for their password, they write it down and press [enter], and that's it, nothing more 😀
Open another terminal and type «loik»(Without the quotes) and press [enter], the following should appear:
And that is LOIQ ... which is neither more nor less than LOIC but for Linux, using Qt libraries.
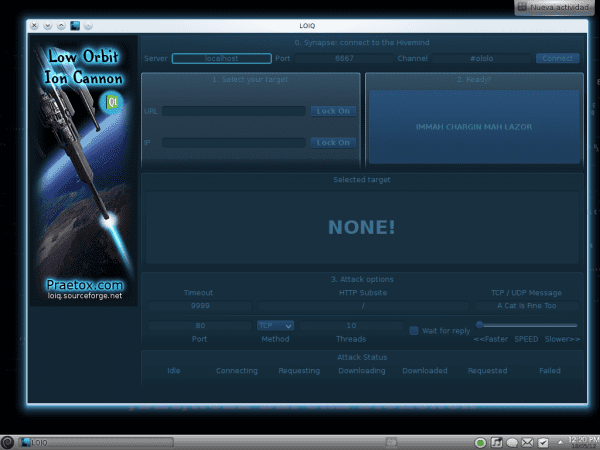
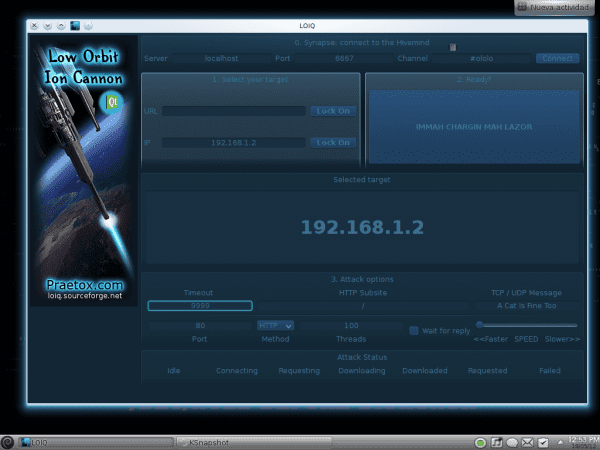
To do an attack (I will do a test with an internal server of my work), in the 1st field where it says URL we put the domain (for example, server.domain.com), or if we know the IP we can put this in the field below, the one that says IP. Once the data has been written in one of these two fields, we press the button to the right of the field that says «lock on«. Next, below and in the center it says 10 and below «Threads«, Increase this to any number, I will put 100. This number will be the number of packages / requests that will be made, and right next to (above where it says Method) we select HTTP in the drop-down list. They have many more options, timeout, directory they want to attack, etc. etc.
Since we are doing a test only, let's just leave that at that. I leave the screenshot of how it turned out for me:
And then, once the data is in ... they just press the largest button, the one with a lot of weird letters hahaha (says: IMMAH CHARGIN MAH LAZOR)… And the attack begins 😀
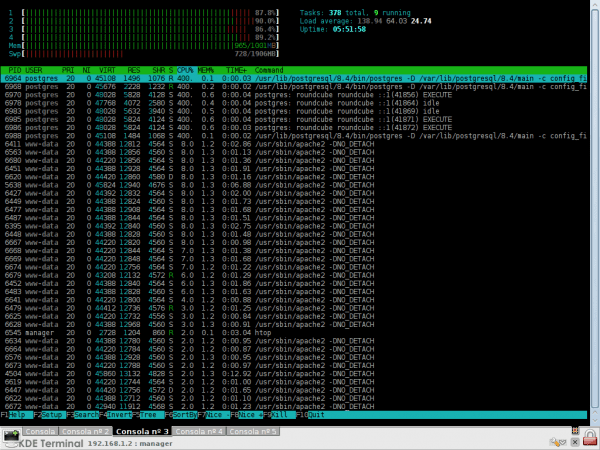
I'll do it here, and in less than 5 seconds the server I'm attacking (I remember, a server from here at work) will have almost 100% of the RAM occupied, and the CPUs at maximum… see:
As you can see ... 4CPUs (physical, not virtual), and 2GB of RAM went to the ground, offline server, no website of those that were there opened, POP3 service, IMAP service, everything was put offline, because the server had no more resources to respond to requests that were made.
And remember, this was only done by 1 person (I, a single LOIQ / LOIC) and with only 100 requests ... Can you imagine more than 3000 people doing DDoS attacks on the same server? (real figure ...)… I said, even the CIA and FBI have succumbed 😉
I clarify, that this tutorial is with EDUCATIONAL PURPOSES!!
The objective of putting this tutorial is that just a few hours after being published, we will put another tutorial on iptables and how to gain protection against DDoS. Just for that we put this tutorial 😉
Other information to take into account ...
If you are going to do DDoS (which I don't tell you to do hahaha), I recommend that you first read the Anonymous security guide, there they explain about VPN and others.
Anyway. I hope you are good and do not use this for harmful purposes ... do not let the dark side absorb you 😀
regards
Not long ago both the pirate bay and wikileaks suffered ddos attacks for a few hours and now you come with this.
I know ... believe me I'm not oblivious to any information of this kind, at all.
I do not agree (not even one bit) with what happened to PirateBay and WikiLeaks, and I am aware that Anonymous did not officially participate or support it (official accounts of them spoke out against the attack, and the culprit will be discovered ...).
If I put this tutorial, it is simply to give continuity to the series of guides / tutorials on iptables that we have been putting, because the next tutorial will be to gain protection against DDoS.
That is the only reason why I put this tutorial.
I hope this is not misunderstood ...
🙁… fuck buddy, you make it sound like I had participated in the DDoS against PirateBay O_O…
The road to hell is full of good intentions …….
By the way, you know who he is, he was a "renegade" who confessed on twitter.
Yes, just like the internet is full of tutorials on DDoS, SQLi, hping3, flood, XSS, exploits, etc.
Yes, here, we put a DDoS tutorial, and its intention was NOT what you think ... but also, we put a tutorial on how to gain protection against this type of attack.
By the way, those iptables rules from the tutorial the author tested (and uses) in his work, effective against hping3 and LOIC / LOIQ.
Greetings friend
+1 I am not in favor of this type of article, but hey. At the end Anonymous trying to do justice, he is committing a crime.
Hands have not answered the request to the fair in the UCI .. What happens ELAV do not want to come ...
We are in a thousand two things. In passing, I need you to answer me about the email that I sent you, because time is running out and I need to move with that ...
Many will not bear the urge to use it for "educational" purposes 🙂
Yes, they clarified for educational purposes to throw away the server of my university as I told you on IRC LOL
Don't do it, be better than them and don't give them the pleasure 🙂
Very good info, I have been interested in the subject for a long time but I had not done much research on it. The guide is very clear, thank you very much.
0000 OO
hahaha very good the tuto ... I had both versions the HIOC and the LOIC but for Windows .... and @ KZKG ^ Gaara experienced a test from my servers to their servers jeej ... very good clarification, it will only be used for educational purposes, although as KZKG ^ Gaara says with the proper configuration of Iptables it is for pleasure that they carry out DdoS attacks
Try it so you can see hahaha ... that I go there in person and beat you to hell haha.
In a while I will publish the iptables anti-DDoS tutorial hehe
Did you even notice loic's cf? This program uses your real IP to carry out the attack, and all accesses and IPs are registered on the server, which means that you can go straight to jail for wanting to play juanker.
To what extent anonymous use VPNs, zombie machines or cyber cafes to carry out attacks without being so easily detected.
Read the last paragraphs please ...
There I clarify, that first they should NOT do DDoS, and also if they do use VPN before, I even put a link to an Anonymous security manual.
Uffff, great, this is really cool hehe: P .. Thank you very much my friend.
PS: waiting for the next anti-DDoS tutorial
Regards!
Soon, we just need to take a photo to put it in the post, that the iptables / firewall that we have we have used a lot already 😉
Come on, everyone to do ddos attacks on desdelinux to test the server
Hahaha
regards
: )
You would be able? ... man, you would have to have very bad feelings, or we would have done something very bad to you 🙁
it was just an ironic comment with no intention of offending
: )
See. It would be good if they gave us our own medicine, let's see if KZKG ^ Gaara will ever listen to me ^^
Master if wisdom is eternal hahahahaha
I agree with Elav, I do not think that placing this type of tutorials is the most successful in a public space like this, in addition to encouraging someone to do something silly, it could attract unnecessary attention (to a good understanding ...)
Well, I have to disagree.
After all, a Linux tutorial is still a tutorial, and this article is nothing more than interesting information for every Linux user (whether it is useful or not depends on each one). Loic in Qt bookstores? I, at least, did not know him and now I do.
Indeed. I, like all (or at least many) network administrators, have to always be innovating, learning about new types of attacks and so on. Once I read and found LOIC, I realized that getting it to work on Linux was quite a problem, then (months later) I found LOIQ, and I thought it was interesting to share this.
In addition, the main objective of this post is none other than to give space to the one we put next to this one, that of anti-DDoS security.
Greetings friend 😀
hehe that curious precisely in the university I am seeing this issue the DDoS attacks if they had published this before I would have added this as part of an example of my research XD, excellent information, greetings.
Very good entry with very good, well-explained information for all Linux users. From my point of view, I have always thought that this type of work or pentest should be done. desde Linux or some Unix since Windows does not convince me because of so many viruses and other issues, in Unix we can do a netstat or a tcpdump and we can see clearly what we are doing and where we are doing it.
Another interesting program or better said tool is this script written in perl
Slowloris
http://ha.ckers.org/slowloris/
Very interesting for
Apache 1.x
Apache 2.x
dhttpd
GoAhead WebServer
On the subject, it is good to know how the attacks work to understand how the defense works since this will only learn us more, and also this we would only do to our sites for testing since another matter is the ip.
regards
hi, i followed the tutorial:
cd $ HOME && wget http://ftp.desdelinux.net/loiq-0.3.1a.tar.bz2 && bzip2 -dc loiq-0.3.1a.tar.bz2 | tar -xv && mv loiq-0.3.1a .loiq-0.3.1a && sudo ln -s $ HOME / .loiq-0.3.1a / loiq / usr / local / bin /
but when trying to run the application:
root @ ubuntu: / usr / local / bin # ls
loik
root @ ubuntu: / usr / local / bin # loiq
it throws me the following error:
root @ ubuntu: / usr / local / bin # loiq
loiq: error while loading shared libraries: libQtGui.so. 4: cannot open shared object file: No such file or directory
which may be wrong from what I understand you can't open the shared file object
The error is not found in the installation procedure, the detail is that the Qt libraries necessary to run the application are not installed on your system. As my partner Gaara use KDE, it does not have this problem, without instead, as you use Gnome (GTK), you get that "error". Unfortunately at the moment I don't use Ubuntu / Debian on any of my computers so I couldn't tell you what packages are necessary to run the app correctly :(.
@Gaara you use Debian, it would not be bad if you expanded the article to overcome this problem ...
Greetings 😉
My mistake, sorry ... I should have specified this a little more hehe.
It happens that LOIQ as I said in the post, is written with Qt libraries, that is ... from KDE, so if you use Gnome (Unity, Cinnamon), Xfce or another environment that is NOT KDE, this will happen to you.
In order not to mess up a lot, try the .deb 😉
Greetings and any problem here we are to help.
«And remember, this was only done by 1 person (me, a single LOIQ / LOIC) and with only 100 requests ... Can you imagine more than 3000 people doing DDoS attacks on the same server? (real figure ...) ... what was said, even the CIA and FBI have succumbed »
What will an attack carried out on your local network have to do with an attack carried out over the Internet? Anyway ... talking without having a clue ... a great blog huh 🙂
Hello and welcome 😉
Of course nothing, they are two completely different media. I said what you quote in your comment, so that the less expert user could get an idea of what can be achieved, see (and read in a few words) what was talked about at the beginning of the post, because I did not intend that this was only one more post of just theory.
😉… right, I have no idea 😀
Could you if you are so kind, explain to me what or where I went wrong or said something wrong? You know, we newbies are prone to mistakes 🙂
Thank you in either case casos
Thank you for your visit and comment, I await your response (I.e.
@perseo, @ garaa… .grax for the info I try it and tell you how it went ……
Excuse me friend and to uninstall it from the terminal which command do I use? '
If you installed it using the .DEB you just have to search for the package using Synaptic, or using:
apt-cache search loiq
Then assuming the package is called: loiq
This would be enough to delete it:
sudo apt-get purge loiq
regards
Hello, hello..interesting your article… but as a second part it would be good to know how to obfuscate the ip so as not to end up in front of a court. Waiting for your lessons, teacher and may the force be with you.
I freak out…. looking for an anti attack tutorial I find this…. I do not fall from my amazement, bravo boy ...
Uy yes Uy yes… We are legion, we are anonymous ..
Hi bro, what is the name of the program where you view the HTTP requests and the traffic generated by LOIQ?
Hello teachers, sorry for the inconvenience but the link is down, could someone be kind enough to re-upload it?
i'm new to linux, but i try hard.
PS: Does anyone know exactly what to know what to know to work in computer security?
because I would like to get into this beautiful area,
also what languages are more suitable for this world?
Atte: Thank you very much.