Two researchers (Mathy Vanhoef and Eyal Ronen) unveiled on a new attack method which is already cataloged in the CVE-2019-13377 which this failure affects wireless networks using WPA3 security technology allows you to obtain information about the characteristics of the password that can be used to select it in an offline mode The problem is manifested in the current version of Hostapd.
These same researchers similarly identified six vulnerabilities in WPA3 a few months agoespecially in terms of the SAE authentication mechanism, also known as Dragonfly. These attacks look like dictionary attacks and allow an opponent to retrieve the password by abusing side or secondary channel leaks.
In addition, carried out a large number of attacks on the various mechanisms that make up the WPA3 protocol, such as a dictionary attack against WPA3 when operating in transition mode, a side attack in microarchitecture based on a cache against SAE Handshake and they took the opportunity to show how the retrieved time and information from the cache can be used to carry out a "Password partition attacks" offline.
This allows an attacker to recover the password used by the victim.
However, the analysis showed that the use of Brainpool leads to the appearance of a new class of leaks on third-party channels in the Dragonfly connection matching algorithm used in WPA3, which provides protection against password guessing in offline mode.
The problem identified shows that create Dragonfly and WPA3 implementations, removed from data leaks through third-party channels, it is an extremely difficult task It also shows the inconsistency of the closed-door standards development model without conducting a public discussion of the proposed methods and community auditing.
When ECC Brainpool is used when encoding a password, the Dragonfly algorithm performs several preliminary iterations with a password related to quickly computing a short hash before applying the elliptical curve. Until a short hash is found, the operations performed are directly dependent on the client's MAC address and password.
About new vulnerabilities
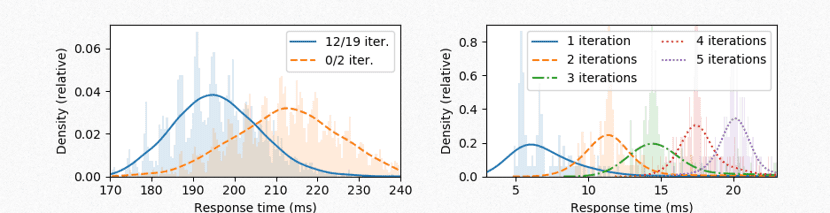
In the runtime it is correlated to the number of iterations and delays between operations during preliminary iterations can be measured and used to determine password characteristics, which can be used offline to clarify the correct choice of password parts during their selection.
To carry out an attack, you must have access to the user's system connecting to the wireless network.
In addition, the researchers identified a second vulnerability (CVE-2019-13456) associated with information leakage in the implementation of the EAP-pwd protocol using the Dragonfly algorithm.
The problem is specific to the FreeRADIUS RADIUS server and based on information leakage through third-party channels, as well as the first vulnerability, it can significantly simplify the password selection.
In combination with an improved method of noise detection during delay measurement, to determine the number of iterations, it is sufficient to carry out 75 measurements for one MAC address.
The resulting attacks are efficient and inexpensive. For example, degradation attacks can be exploited using existing WPA2 cracking tools and hardware. Side channel vulnerabilities can, for example, be abused to carry out a brute force attack using the largest known dictionaries for as little as $ 1 on Amazon EC2 instances.
Methods to improve protocol security to block identified issues have already been included in previews of future Wi-Fi standards (WPA 3.1) and EAP-pwd.
Fortunately, as a result of research, both the Wi-Fi standard and EAP-pwd are being updated with a more secure protocol. Although this update is not backward-compatible with current WPA3 implementations, it prevents most of our attacks.
Source: https://wpa3.mathyvanhoef.com