Un official report de Symantec last November 26, alert of the existence of a new virus, baptized as linux darlioz, which can affect a wide variety of computers, exploiting the vulnerability "php-cgi" (CVE-2012-1823) present in PHP 5.4.3 and 5.3.13.
This vulnerability affects some versions of distributions of GNU / Linux such as Ubuntu, TurboLinux, SuSE, Red Hat, Mandriva, Debian and others, as well as Mac OS X 10.7.1 through 10.7.4, and Mac OS X Server 10.6.8 through 10.7.3.
Although this vulnerability in PHP was detected and corrected since May 2012, many computers are still outdated and use old versions of PHP, resulting in a potential target for a large-scale infection.
The infection procedure, as described in an article de PCWorld, is the following:
Once executed, the worm randomly generates IP addresses, accessing a specific path on the machine with a known ID and password, and sends HTTP POST requests, which exploit the vulnerability. If the vulnerability has not been corrected on the target, the worm is downloaded from a malicious server and starts looking for a new target
According to posted on your blog by Kaoru hayashi, researcher of Symantec, this new worm seems designed to infect, in addition to traditional computers, a wide range of devices connected to the network, such as routers, set-top boxes, security cameras, etc., that work on various variants of GNU / Linux.
Although Symantec evaluates the risk level of this virus as "very low" and the levels of distribution and threat as "low" and considers its containment and removal "easy", in reality the potential risk it represents is multiplied considerably if we take into account the substantial increase that the so-called “internet of things” has been registering in recent times.
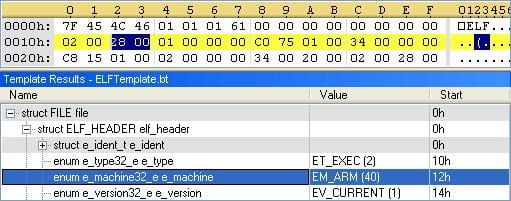
One more time according to Symantec, at the moment the worm's spread only occurs between x86 systems since the downloaded binary is in the ELF (Executable and Linkable Format) for architecture Intel, but the researchers indicate that the servers also host variants for architectures ARM, PPC, MIPS y MIPSEL, which is highly concerning given the high potential of devices with these architectures that are likely to be infected.
It is well known that the firmware embedded in many devices is based on GNU / Linux and usually includes a web server with PHP for the admin interface.
This implies a potential risk much greater than that of computers with any distribution of GNU / Linux, since unlike the latter, they do not regularly receive the security updates necessary to correct the vulnerabilities detected, to which it is added that to carry out the firmware update a certain degree of technical knowledge is required, which a good part of the owners of such devices.
All the recommendations to avoid infection with this worm they are quite simple: keep our systems updated with published security patches and extreme elementary security measures with devices connected to the network, such as change default IP address, username and password y keep firmware updated, either with those released by the manufacturer, or with the free equivalents available from recognized sites.
It is also recommended to block incoming POST requests as well as any other type of HTTPS call, whenever possible.
On the other hand, from now on it is suggested to take into account when evaluating the acquisition of any new equipment, the ease of updating the firmware and the long-term support provided by the manufacturer.
For now, I am updating the firmware of my Netgear router, which for a long time was on the list of pending tasks, lest it be fulfilled that "at the blacksmith's house ..."
Note: The detailed list of distributions of GNU / Linux that originally contain the vulnerability of PHP exploited by this virus is available in the following link.