El Zed Attack Proxy (ZAP) is a free tool written in Java coming from OWASP project to carry out, in the first instance, penetration tests in web applications, although it can also be used by developers in their daily work. As of today it is in its version 2.1.0 and needs Java 7 to run, although I use it in Debian GNU / Linux with Open JDK 7. For those of us who are starting in the world of web application security, it is an excellent tool to polish our skills.
Among the many features of ZAP, I will comment on the following:
- Interception proxy: Ideal for those of us who are newbies in this field of security, configured in the correct way, it allows to see all the traffic between the browser and the web server of the moment, showing in a simple way the headers and body of the HTTP messages regardless of the method used (HEAD, GET, POST, etc). In addition we can modify the HTTP traffic at will in both directions of communication (between the web server and the browser).
- spiders: It is a feature that helps to discover new URLs on the audited site. One of the ways it does this is by parsing the page's HTML code to discover tags. and follow their attributes href.
- Forced Browsing: Tries to discover non-indexed files and directories on the site such as login pages. To achieve this, it has by default a series of dictionaries that it will use to make requests to the waiting server status code response 200.
- Activate Scan: It automatically generates different web attacks against the site such as CSRF, XSS, SQL injection among others.
- And many others: Actually there are many other features such as: Support for web sockets from version 2.0.0, AJAX Spider, Fuzzer, and many others.
Configuration with Firefox
We can configure the socket through which ZAP will be listening if we are going to Tools -> Options -> Local Proxy. In my case I have it listening on port 8018:
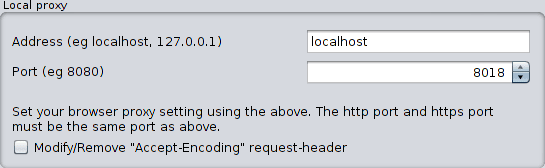
Configuration «Local proxy»
Then we open the Firefox preferences and we will Advanced -> Network -> Configuration -> Manual proxy configuration. We indicate the socket that we previously configured in ZAP:
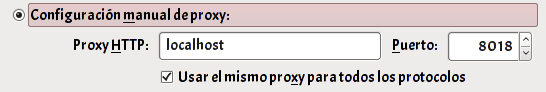
Configure proxy in Firefox
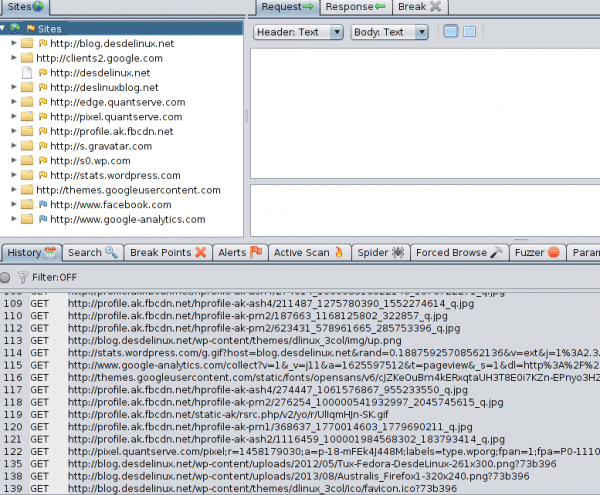
If everything has gone well, we will be sending all our HTTP traffic to ZAP and it will be in charge of redirecting it as any proxy would. As an example, I enter this blog from the browser and see what happens in ZAP:
We can see that more than 100 HTTP messages have been generated (most using the GET method) to fully load the page. As we see in the tab Sites Not only has traffic been generated to this blog, but also to other pages. One of them is Facebook and it is generated by the social plugin at the bottom of the page «Follow us on Facebook". Also did Google Analytics which indicates the presence of said tool for the analysis and visualization of statistics of this blog by the administrators of the site.
We can also observe in detail each of the HTTP messages exchanged, let's see the response that was generated by the web server of this blog when I entered the address http://desdelinux.net choosing its respective HTTP GET request:
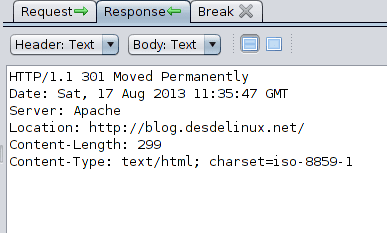
HTTP message detail
We note that a status code 301, which indicates a redirect that is directed towards https://blog.desdelinux.net/.
ZAP becomes an excellent completely free alternative to Burp Suite For those of us who are starting out in this exciting world of web security, we will surely spend hours and hours in front of this tool learning different web hacking techniques, I carry a few🇧🇷 🇧🇷
That is something that I have to do, mostly to prove what I do.
It's quite interesting
This tool looks much more complete than the Microsoft Network Monitor. The contribution is appreciated.
Excellent, thank you very much for the information and explanation.
Greetings.
IMHO, I think these tools should be left for security scopes, and not publish it on a linux blog. There are people who can use it irresponsibly or unconsciously.
The tools are always going to be double-edged tools, as they are used by the good and the bad, unfortunately that cannot be avoided. OWASP ZAP is a tool recognized by the EH community in the field of web security and is used for web audits. Remember, "With great power comes great responsibility."
I published this entry because I am studying self-taught to offer HD services in the future and I thought it would be of interest to other readers. The end is not that they use it illicitly, much less, hence the warning at the beginning of the post.
Regards!
PD1 ->: that'ssuspicious: Troll detected? I have the doubt….
PD2 -> Jhahaha Please do not turn this into a flame war from here down as in other posts.