Pentmenu: A Bash Script for Reconnaissance and DOS Attacks
From time to time, we take the opportunity to explore a free, open and free tool in the field of computer security, especially in the world of hacking and pentesting. For this reason, today we take the opportunity to introduce you to another interesting and useful tool of this type called «Pentmenu».
And what is Pentmenu? Well, briefly it is, un small Linux script made in Bash Shell which has been created by the user reconnaissance attacks and DOS. And of course, all this in an easy way, through aA cool selection menu for quick and easy network reconnaissance and thus successful execution of necessary attacks.

Hacking Tools 2023: Ideal for use on GNU/Linux
But, before starting this present post about this interesting hacking and pentesting tool called «Pentmenu», we recommend that you explore the previous related post:

Pentmenu: Hacking and pentesting tool
Exploring Pentmenu on GNU/Linux
For download, explore and get to know the Pentmenu tool as usual we will use our usual Respin MilagrOS. And the procedure to carry this out is the one that appears on your official website on GitHub. And it is the following:
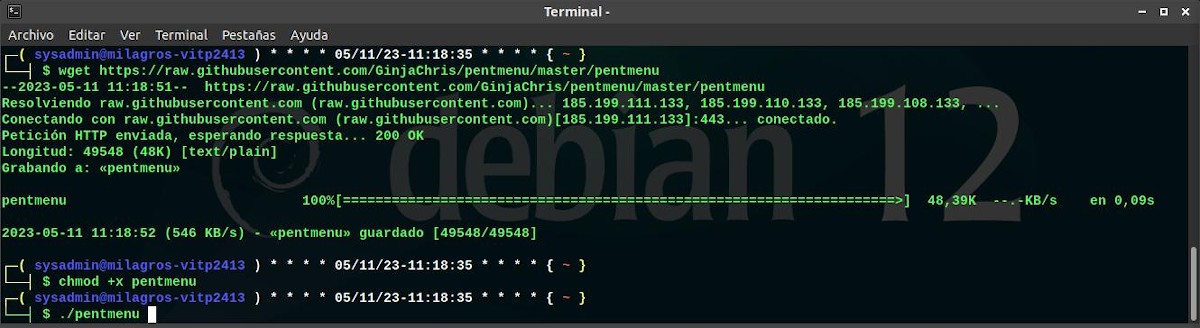
Download
wget https://raw.githubusercontent.com/GinjaChris/pentmenu/master/pentmenugranting of permissions
chmod +x pentmenuExecution
./pentmenu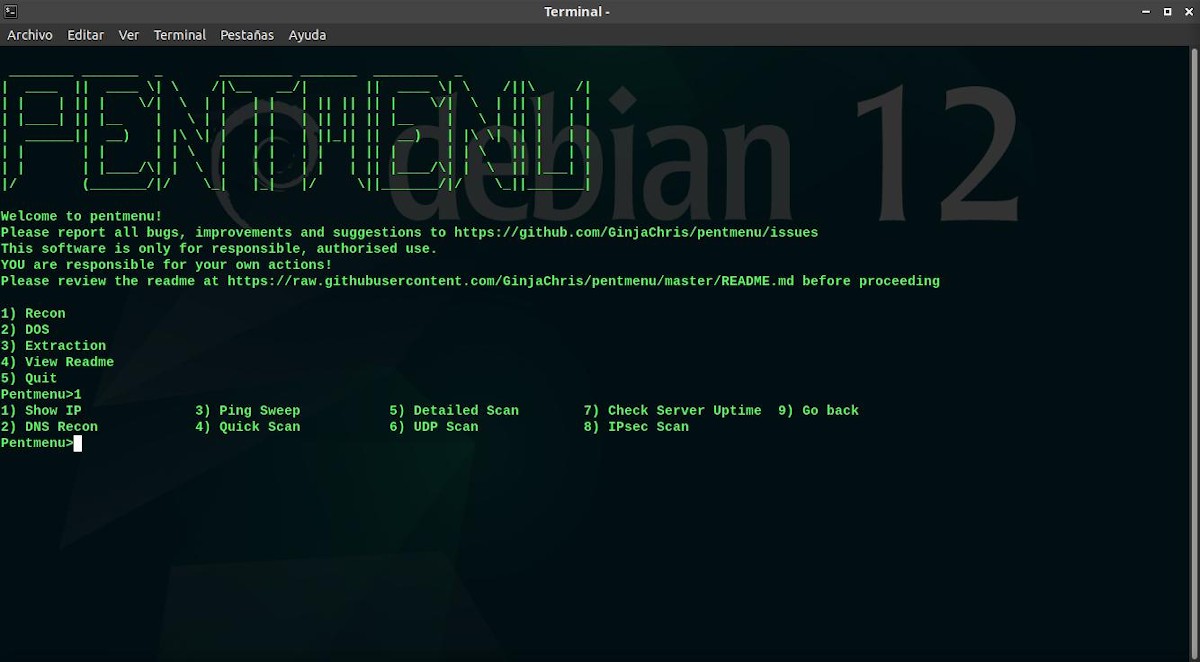
Menu 1: Recon (Recognition Modules)
This menu or module offers the following functionalities:
- Show IP: This option uses the curl command to search for the external IP of our computer.
- DNS Recognition: This option targets passive recognition, and consequently performs a DNS lookup and a whois lookup of the target.
- Ping sweep: This option uses the nmap command to perform an ICMP echo (ping) against the destination host or network.
- Quick Scan: This option works as a TCP port scanner, by using the nmap command to look for open ports using the TCP SYN scan.
- detailed scan: This option uses the nmap command to identify active hosts, open ports, attempts to identify the operating system, write banners, and more.
- UDP Scan: This option uses the nmap command to search for open UDP ports. In consecuense, scans all UDP ports of the destination host.
- Check Server Uptime: This option calculates the uptime of the target host by querying an open TCP port with hping3. Accuracy of results may vary or may not work from machine to machine.
- IPsec Scan: This option is intended to try to identify the presence of an IPsec VPN server using ike-scan and various Phase 1 proposals.
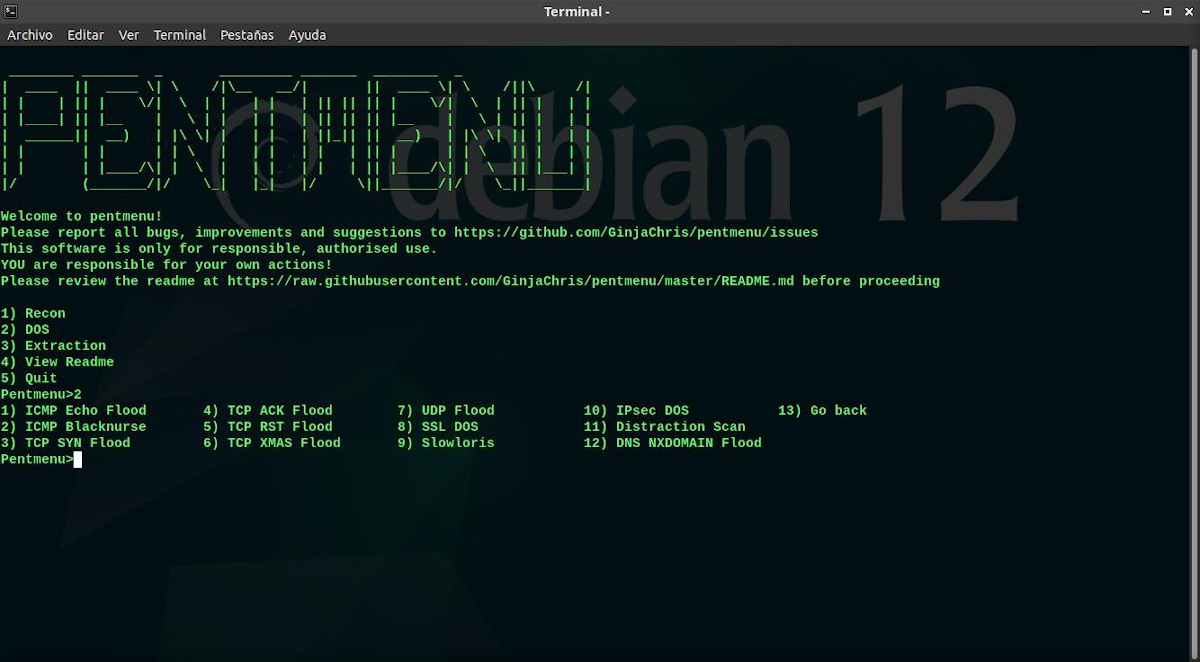
Menu 2: DOS (DOS attack modules)
- ICMP Echo Flood: This option uses the hping3 CLI application to launch a traditional ICMP echo flood against a target host.
- ICMP Blacknurse Flood: This option uses the hping3 CLI application to launch a traditional ICMP Blacknurse flood against a target host.
- TCP SYN Flood: This option sends a flood of TCP SYN packets using hping3. But, yeahIf it doesn't find hping3, try using the nmap-nping utility instead.
- TCP ACK Flood: This option offers the same options as the SYN Flood, but sets the TCP ACK (Acknowledgment) flag instead.
- TCP RST Flood: This option offers the same options as SYN Flood, but sets the TCP RST (Reset) flag instead.
- TCP XMAS Flood: This option offers the same options as SYN Flood and ACK Flood, but it sends packets with all TCP flags set (CWR, ECN, URG, ACK, PSH, RST, SYN, FIN).
- UDP Flood: This option offers the same options as the SYN Flood, but instead sends UDP packets to the specified host:port.
- SSL TWO: This option uses OpenSSL to attempt a DOS attack against a destination host:port. It does this by opening many connections and making the server perform expensive handshake calculations.
- Slowloris: This option uses the netcat program to slowly send HTTP headers to the destination host:port with the intent of starving it of resources.
- IPsec DOS: This option uses the ike-scan program to try to flood the specified IP with main mode and aggressive mode phase 1 packets from random source IPs.
- DistractionScan: This option it doesn't actually trigger a DOS attack, but simply launches multiple TCP SYN scans, using hping3, from a spoofed IP of our choosing.
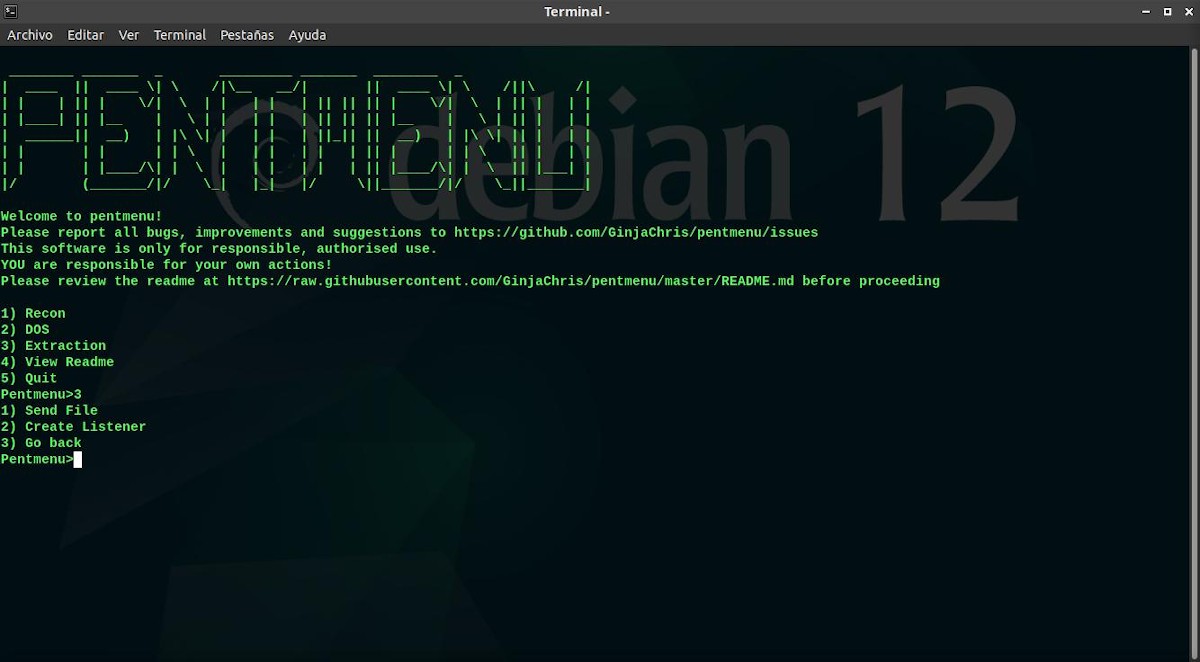
Menu 3: Extraction
- Send File: This module uses the netcat program to send data with TCP or UDP. which is usually extremely useful for extracting data from target hosts.
- Create Listener: This module uses netcat to open a listener on a configurable TCP or UDP port. Which is usually extremely useful for testing syslog connectivity, receiving files, or checking active scanning on the network.
Finally, the menu 4 (View Readme) It allows us to see locally and in more detail, everything described above, which in turn, is what is found on GitHub. And menu 5 (Quit), basically is to exit and close the program.
Summary
In summary, «Pentmenu» is one of many hacking and pentesting tools, free, open and free, available to learn and practice activities in the field of computer security. However, and as with many others that we have addressed here or not, this utility must be used keeping in mind the responsible and authorized use of what it will be applied to, therefore, everything that is done with it is at your discretion. responsibility of the user. And in case someone tries it or has tried it before, we invite you to tell us about your experience with it, via comments.
Lastly, remember visit our «homepage» and join our official channel of Telegram to explore more news, guides and tutorials. And also, has this group to talk and learn more about any IT topic covered here.