How many of us have had the need to “limit access” to the files contained in a certain directory / folder or we simply need to prevent some people from viewing, deleting or modifying the content of a certain file? More than one, right? Can we achieve it in our beloved penguin? The answer is: Of course yes : D.
Introduction
Many of us who come from Windows, were used to dealing with this "problem" in a very different way, to achieve this objective we had to resort to unorthodox "techniques", such as hiding the file through its attributes, moving our information to the most remote place of our team (within 20,000 folders) to try to dissuade our "enemy" XD, changing or eliminating the file extension, or the most "common" of practices, download a program that allows us to " close ”our directory behind a nice dialog box that asks us for a password to access it. We had a much better alternative? No.

I am very sorry for my "Windoleros" friends (I say it with great affection so that nobody is offended, ok?;)), But today I have to teach myself a little bit with Windows: P, since I will explain why this OS does not allow native this functionality.
How many of you have noticed that when we sit behind a “Windows” computer (even if it is not ours) we automatically become owners of everything that the computer contains (images, documents, programs, etc.)? What do I mean? Well, simply by taking "control of Windows", we can copy, move, delete, create, open or modify folders and files left and right, regardless of whether we are the "owners" of this information or not. This reflects a major security flaw in the operating system, right? Well, this is all because Microsoft's operating systems were not designed from the ground up to be multi-user. When the versions of MS-DOS and some versions of Windows were released, they fully trusted that the end user would be responsible for "guarding" their respective computer so that no other user had access to the information stored in it ... go naive ¬ ¬. Now WinUsers friends, you know why there is this "mystery": D.
On the other hand, GNU / Linux, being a system designed fundamentally for networking, the security of the information that we store on our computers (not to mention on the servers) is essential, since many users will have or may have access to part of the software resources (both applications and information) and hardware that are managed on these computers.
Now we can see why the need for a permit system? Let's dive into the topic;).

In GNU / Linux, the permissions or rights that users can have over certain files contained in it are established in three clearly differentiated levels. These three levels are as follows:
<° Owner's Permits.
<° Group permissions.
<° Permissions of the rest of the users (or also called "the others").
To be clear about these concepts, in network systems (such as the penguin) there is always the figure of the administrator, superuser or root. This administrator is in charge of creating and removing users, as well as establishing the privileges that each of them will have in the system. These privileges are established both for each user's HOME directory and for the directories and files that the administrator decides that the user can access.
Owner permissions
The owner is the user who generates or creates a file / folder within their working directory (HOME), or in some other directory over which they have rights. Each user has the power to create, by default, the files they want within their working directory. In principle, he and only he will be the one who has access to the information contained in the files and directories in your HOME directory.
Group permissions
The most normal thing is that each user belongs to a work group. In this way, when a group is managed, all the users that belong to it are managed. In other words, it is easier to integrate several users into a group who are granted certain privileges in the system, than to assign the privileges independently to each user.
Permissions of the rest of users
Finally, the privileges of the files contained in any directory may also be held by other users who do not belong to the workgroup in which the file in question is integrated. That is, users who do not belong to the workgroup in which the file is, but who do belong to other workgroups, are called other system users.
Very nice, but how can I identify all this? Simple, open a terminal and do the following:
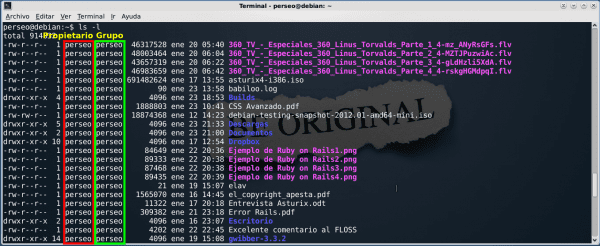
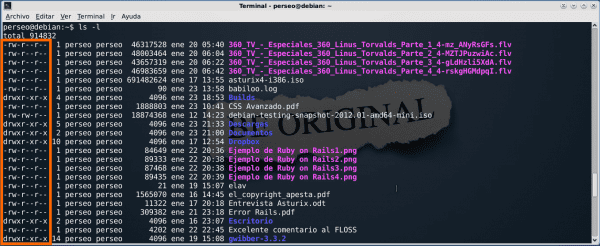
$ ls -l
Note: they are lowercase letters "L" 😉
It will appear something like the following:
As you can see, this command displays or "lists" the content of my HOME, what we are dealing with are the red and green lines. The red box shows us who is the owner and the green box indicates to which group each of the files and folders listed above belongs. In this case, both the owner and the group are called "Perseus", but they may well have encountered a different group such as "sales". For the rest, do not worry for now, we will see later: D.
Types of permissions in GNU / Linux
Before learning how to set permissions in GNU / Linux, we must know how the different types of files that the system can have can be differentiated.
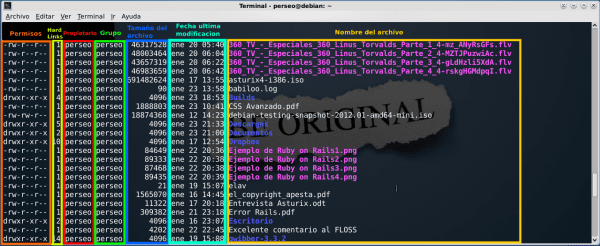
Each file in GNU / Linux is identified by 10 characters which are called mask. Of these 10 characters, the first (from left to right) refers to the file type. The following 9, from left to right and in blocks of 3, refer to the permissions granted, respectively, to the owner, the group and the rest or others. A screenshot to demonstrate all this stuff:
The first character of the files can be the following:
| Excuse me | It identifies <strong>financial incentives</strong>, grants and loans from local, regional and European institutions. |
| - | Archive |
| d | Directory |
| b | Special Block File (Device Special Files) |
| c | Special characters file (tty device, printer ...) |
| l | Link file or link (soft / symbolic link) |
| p | Channel special file (pipe or pipe) |
The next nine characters are the permissions granted to system users. Every three characters, the owner, group, and other user permissions are referenced.
The characters that define these permissions are the following:
| Excuse me | It identifies <strong>financial incentives</strong>, grants and loans from local, regional and European institutions. |
| - | Without permission |
| r | Read permission |
| w | Write permission |
| x | Execution permission |
File permissions
<° Reading: basically allows you to view the content of the file.
<° Write: allows you to modify the content of the file.
<° Execution: allows the file to be executed as if it were an executable program.
Directory permissions
<° Read: Allows you to know what files and directories the directory that has this permission contains.
<° Write: allows you to create files in the directory, either ordinary files or new directories. You can delete directories, copy files in the directory, move, rename, etc.
<° Execution: allows you to go over the directory to be able to examine its contents, copy files from or to it. If you also have read and write permissions, you can perform all possible operations on files and directories.
Note: If you do not have the execution permission, we will not be able to access that directory (even if we use the "cd" command), since this action will be denied. It also allows to delimit the use of a directory as part of a path (as when we pass the path of a file that is in that directory as a reference. Suppose we want to copy the file "X.ogg" which is in the folder " / home / perseo / Z "-for which the folder" Z "does not have execution permission-, we would do the following:
$ cp /home/perseo/Z/X.ogg /home/perseo/Y/
obtaining with this an error message telling us that we do not have sufficient permissions to access the file: D). If the execution permission of a directory is deactivated, you will be able to see its content (if you have read permission), but you will not be able to access any of the objects contained in it, because for this this directory is part of the necessary path to figure out the location of your objects.
Permission management in GNU / Linux
So far, we have seen what permissions are for in GNU / Linux, below we will see how to assign or subtract permissions or rights.
Before starting, we must bear in mind that when we register or create a user in the system, we automatically grant them privileges. These privileges, of course, will not be total, that is, users will not normally have the same permissions and rights of the superuser. When the user is created, the system generates by default the user privileges for file management and directory management. Obviously, these can be modified by the administrator, but the system generates more or less valid privileges for most of the operations that each user will carry out on their directory, their files, and on the directories and files of other users. These are generally the following permissions:
<° For files: - rw-r-- r--
<° For directories: - rwx rwx rwx
Note: they are not the same permissions for all GNU / Linux distributions.
These privileges allow us to create, copy and delete files, create new directories, etc. Let's see all this in practice: D:
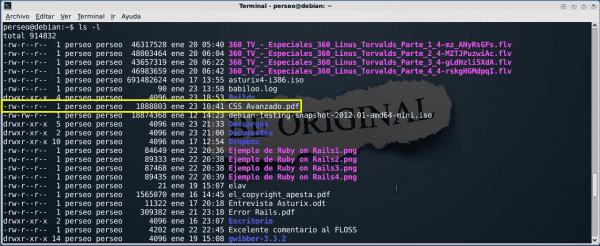
Let's take the "Advanced CSS.pdf" file as an example. Let's observe that it appears as follows: -rw-r--r-- … Advanced CSS.pdf. Let's take a closer look.
| Type | User | Group | Rest of users (others) | file name |
| - | rw - | r-- | r-- | Advanced CSS.pdf |
This means that:
<° Type: Archive
<° The user can: Read (view content) and write (modify) the file.
<° The group to which the user belongs can: Read (only) the file.
<° Other users can: Read (only) the file.
For those curious who are wondering at the moment what the other fields of the list obtained by ls -l refer to, here is the answer:
If you want to know more about the hard and soft / symbolic links, here the explanation and their differences.
Well friends, we come to the most interesting and heavy part of the subject in question ...
Permission assignment
The command chmod ("Change mode") allows modifying the mask so that more or less operations can be performed on files or directories, in other words, with chmod you can remove or remove rights for each type of user. If the type of user to whom we want to remove, put or assign privileges is not specified, what will happen when performing the operation is to affect all users simultaneously.
The basic thing to remember is that we give or remove permissions at these levels:
| Parameter | Level | Description |
| u | owner | owner of the file or directory |
| g | group | group to which the file belongs |
| o | others | all other users who are not the owner or group |
Permission types:
| Excuse me | It identifies <strong>financial incentives</strong>, grants and loans from local, regional and European institutions. |
| r | Read permission |
| w | Write permission |
| x | Execution permission |
Give the owner permission to execute:
$ chmod u+x komodo.sh
Remove execute permission from all users:
$ chmod -x komodo.sh
Give read and write permission to other users:
$ chmod o+r+w komodo.sh
Leave only read permission to the group to which the file belongs:
$ chmod g+r-w-x komodo.sh
Permissions in octal numeric format
There is another way of using the chmod command that, for many users, is “more comfortable”, although a priori it is somewhat more complex to understand ¬¬.
The combination of values of each group of users forms an octal number, the "x" bit is 20 that is 1, the w bit is 21 that is 2, the r bit is 22 that is 4, we have then:
<° r = 4
<° w = 2
<° x = 1
The combination of bits on or off in each group gives eight possible combinations of values, that is, the sum of the bits on:
| Excuse me | Octal Value | Description |
| - - - | 0 | you don't have any permission |
| - - x | 1 | execute permission only |
| - w - | 2 | write permission only |
| - wx | 3 | write and execute permissions |
| r - - | 4 | read permission only |
| r - x | 5 | read and execute permissions |
| rw - | 6 | read and write permissions |
| rwx | 7 | all permissions set, read, write and execute |
When you combine user, group, and other permissions, you get a three-digit number that makes up the file or directory permissions. Examples:
| Excuse me | Market | Description |
| rw- --- -— | 600 | The owner has read and write permissions |
| rwx --x --x | 711 | The owner read, write and execute, the group and others only execute |
| rwx rx rx | 755 | The read, write and execute owner, group and others can read and execute the file |
| rwx rwx rwx | 777 | The file can be read, written and executed by anyone |
| r-- --- -— | 400 | Only the owner can read the file, but neither can he modify or execute it and of course neither the group nor others can do anything in it. |
| rw-r-- --- | 640 | Owner user can read and write, group can read file, and others can't do anything |
Special permissions
There are still other types of permits to consider. These are the SUID (Set User ID) permission bit, the SGID (Set Group ID) permission bit and the sticky bit (persistence permission bit).
Setu
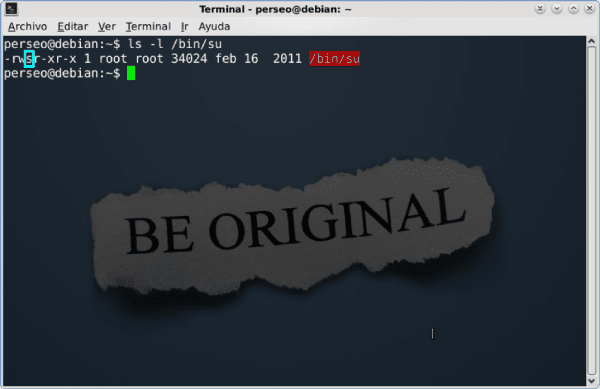
The setuid bit is assignable to executable files, and allows that when a user executes said file, the process acquires the permissions of the owner of the executed file. The clearest example of an executable file with the setuid bit is:
$ su
We can see that the bit is assigned as "s" in the following capture:
To assign this bit to a file it would be:
$ chmod u+s /bin/su
And to remove it:
$ chmod u-s /bin/su
Note: We must use this bit with extreme care as it can cause an escalation of privileges in our system ¬¬.
setgid
The setid bit allows acquiring the privileges of the group assigned to the file, it is also assignable to directories. This will be very useful when several users of the same group need to work with resources within the same directory.
To assign this bit we do the following:
$ chmod g+s /carpeta_compartida
And to remove it:
$ chmod g-s /carpeta_compartida
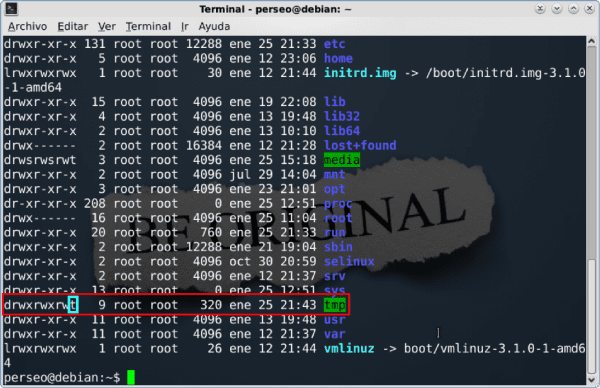
sticky
This bit is usually assigned in directories to which all users have access, and it allows to prevent a user from deleting files / directories of another user within that directory, since all have write permission.
We can see that the bit is assigned as "t" in the following capture:
To assign this bit we do the following:
$ chmod o+t /tmp
And to remove it:
$ chmod o-t /tmp
Well friends, now you know how to better protect your information, with this I hope you stop looking for alternatives to folder Lock o Folder Guard that in GNU / Linux we don't need them at all XD.
P.S: This particular article was requested by the neighbor of a friend's cousin XD, I hope I have solved your doubts ...…

Excellent article, very well explained.
Thanks friend 😀
Excellent Perseus, I had no idea about permissions in octal numeric format (which is a very interesting little stuff) or special permissions (setuid / setgid / sticky).
I was dying of sleep but this got me up a bit, I already want to grab the console 😀 +1000
Good thing that it was useful to you, Greetings 😉
Excellent, the explanations are very clear, thank you very much.
setgid
The bit Setu allows you to acquire the privileges
in that part there is a small error.
Thanks for observing and commenting, sometimes my fingers get "tangled" XD ...
Greetings 😉
I am already corrected 😀
Very good article, Perseus. In any case, I would like to make some observations so that the information is more complete:
Be careful when applying permissions recursively (chmod -R) because we may end up giving files too many permissions. One way around this is by using the find command to distinguish between files or folders. For example:
find /var/www -type d -print0 | xargs -0 chmod 755find /var/www -type f -print0 | xargs -0 chmod 644
Another thing: establishing privileges on directories or files is not an infallible method to protect information, since with a LiveCD or putting the hard disk in another PC it is not difficult to access the folders. To protect sensitive information it is necessary to use encryption tools. For example, TrueCrypt is very good and it is also cross-platform.
And finally: just because most users don't change file system privileges in Windows doesn't mean it's impossible to do so. At least the NTFS file system can be secured as much as an EXT, I know because in my work I have complete partitions without execution or writing permissions, etc. This can be achieved through the security tab (which is usually hidden). The main problem with Windows is that its default configuration allows everything.
Thank you very much for expanding the topic;). As to:
[...] establecer privilegios sobre directorios o archivos no es un método infalible para proteger la información, ya que con un LiveCD o poniendo el disco duro en otra PC no es difícil acceder a las carpetas [...]You are absolutely right, even with Win the same thing happens, possibly later we will talk about the various tools that help us to encrypt our information.
regards
Hugo friend how are you 😀
The problem with TrueCrypt ... is the license something "strange" that it has, can you tell us more about it? 🙂
Greetings compa
The TrueCrypt license will be a little weird, but at least version 3.0 of the license (which is current) allows personal and commercial use on unlimited workstations, and also allows copying, reviewing the source code, making modifications and distributing it. derivative works (as long as it's renamed), so if it's not 100% free, frankly it's pretty close.
The old Perseus leaves the rest of the team bad with his articles for being that complete.
Nobody here is better than nobody huh? And much less better than me JAJAJAJAJAJAJA
hahahaha, be careful friend, remember we are in the same boat 😀
Thanks for the comment 😉
Permits, it is something that is learned from day to day, not from one day to the next, so let's study lol
Excellent article Perseus.
A tip: it is not necessary to write the sign to each symbol, it is enough to indicate it only once. Example:
$ chmod o + r + w komodo.sh
It can look like
$ chmod o + rw komodo.sh
same with
$ chmod g + rwx komodo.sh
it can also look like
$ chmod g + r-wx komodo.sh
following that format you can do this
$ a-rwx, u + rw, g + w + or example.txt
note: a = all.
Greetings.
Wow friend, I didn't know that one, thanks for sharing 😀
Very good article, everything is very well explained.
It is more comfortable for me to change the permissions of the files octally, more clearly. I find it enough to understand the other way but this has been a long time ago hahaha
Hello people, perseus; I really liked the page. I would like to be able to collaborate with it. Is it possible? By clicking on my nick you have references !! haha.
I usually make sporadic publications, and I am more and more activist of the SL, something that I will not abandon in my life as long as I am available and have a couple of fingers. Well, I guess they have my email. a hug and strength with the project that seems to me «bloggers united!», ACA ES LA TRENDENCIA !! This is how the web of the future is created.
Hahahahaha, it would be a pleasure for you to join us, let elav or gaara see your request 😉
Take care and I hope to see you here soon 😀
I'm writing you an email now (to the address you put in the comment) 🙂
I have a doubt. How you can apply permissions to directories and that these do not change their attributes, regardless of the user who modifies them, including root.
Greetings.
Maybe this article clarify a little ..
Well written this article, thanks for sharing knowledge
How well it has been useful, we hope to see you here again. Greetings 😉
Very good article.
I am very happy that it has been useful to you, greetings 😉
The truth I do not agree in linux moving a file to a folder System is a headache. you have to provide permission for everything and enter your password. in windows moving files is easy, even in the same windows folder. a whole procedure to move a file to a folder in linux when in windows it is easier to copy and paste. I use both operating systems. mint 2 Maya cinnamon and windows 13
I've been using Linux for a few years now, and honestly I haven't had these problems for quite some time.
I can move files / folders without any problem, and I have my HDD partitioned in 2. Obviously, to access the other partition the 1st time I have to put my password, but then never again.
If you have a strange problem, tell us, we will gladly help you 😉
Correct article as far as the Linux part is concerned. In your comments on managing permissions in Windows: You don't know at all how permissions are set. The control of these of a much higher power (except in 16 bit versions, Windows 95, 98, Me and mobile) to how they are managed in the penguin system and of a sublime granularity, and for the record that I deal with both operating systems no manias against either of us.
My advice: do a little digging and you will realize, no external programs are required at all. For the all very good. 😉
Very good article. The subject of permissions is an interesting thing to learn. It has happened to me once not to be able to access a file in a long path, because I did not have execute permissions in one of the directories. It is also good to know at least the existence of the special permissions like the Sticky bit.
PS: I've been following the blog for a while but I hadn't registered. They have very interesting articles but what caught my attention the most is the treatment between users. Beyond the fact that there may be differences, in general, everyone tries to help each other by contributing their experiences. That's something remarkable, unlike other sites full of trolls and flamewars 😉
Very interesting, but I learned it differently about the permissions, instead of in Octal, in Binary, so that if, for example, "7" is 111, it meant that it had all the permissions, so if you put 777 it will you give all the permissions to all users, groups ...
A greeting.
Impressive, concise, clear and on topic.
What a good article, congratulations and thanks for all the clarifications… ..
salu2.
Woow if I learn a lot with your tutorials, I feel like a little grasshopper in this immense field that is Linux, but limiting what Hugo once said here, in this row of comments if we put a live cd and if our files are not encrypted not really much left to protect, additionally in Windows I think there was not much problem creating an administrator user and a limited account within the win operating system and thus protect your administrator account data…. But really thank you very much for this article I am more knowledgeable in the matter thanks to you ...…
The truth is that I wanted to run an executable xD and it told me permission denied when opening and writing x files but I read a little here and learned something and it served to see the permissions that that folder that contained the files and the executable had the last thing I remember that I did was that I wanted to access a folder and as the name was long I changed it and between easy xD, then I looked at the permissions and looked at something that said about adm I went to the file I put properties and selected something that said adm then without removing properties Enter the folder and then run the executable and it could start without problems now what I don't know is what I did xD the truth is, I don't know it was because I changed the name of the folder but I don't know and thanks I was able to execute it No problem.
Hello I have some questions,
I have a web system that must write an image to the linux server,
the details is that it does not allow to register it, try changing the permissions but it could not be,
I am new to this, because I would like you to guide me, thank you.
Go that this has helped me, thank you very much for the contribution.
Personally, the documentation helped me to learn, which was put into practice in an activity in my work.
The relevant practices I did were on Debian. Congratulations and greetings.
Excellent tutorial on permissions in GNU / Linux. My experience as a Linux user and as an administrator of servers based on some GNU / Linux distribution is that many of the technical problems that may arise are based on the management of permissions for groups and users. This is something that must be taken into account. I congratulate Perseus for his blog and I am also interested in joining GNU forces on this blog. Greetings from Mexico, comrades!
Hello, first of all I congratulate you very good the article and I consult you I have this case: 4 ———- 1 root root 2363 Feb 19 11:08 / etc / shadow with a 4 forward how these permissions would read.
Thank you
Windows: We select folder, right button, properties> Security tab, there you can add or delete users or groups, and each one put the permissions you want (read, write, full control, etc.). I don't know what the hell you mean
By the way, I use linux daily, I use elementary, based on ubuntu.
Go well
wonderfully it is the best explained article
Thank you
Friend:
Very good contribution, it helped me a lot.
Thank you.
Son of a bitch doesn't even work.
How many of you have noticed that when we sit behind a "Windows" computer That part is totally a lie, because since Windows NT, even before Windows 98 and that problem that you have no security is totally false.
Security in Windows is something Microsoft has taken very seriously for a reason it is the most widely used desktop operating system today.
The article is well explained about the permissions of GNU / Linux but you have swung as always happens in these articles that the one who writes it either does not use Windows or does not know how to use it because they do not like it and only get a negative review.
What must be emphasized is that Windows is very safe in its file system with ACL (Access Control List) characteristic that it carries in Windows from all Windows NT that makes the file system very secure. In GNU / Linux they have also implemented it.
Since Windows Vista the (User Account Control) UAC feature implemented and making it comfortable to use Windows without having to be an administrator to use it comfortably.
For me, a good feature that they implemented because using Windows XP as a user without administration permissions could be done, but at home, who used it like that? almost nobody because of how uncomfortable it was for not having something like UAC.
What if it has been clear to me that whoever wrote the article has done knowing what he is writing even though he has not explained the GNU / Linux ACL.
Hello friend, good information, just wanted to ask
Is there a way to do this, being in the metasploit, inside the victim machine?
Could it be done with these permissions to make that file ineligible, or is it impossible, I mean being inside the metasploit?
Thank you very much for this blog, very good information.