The other day I was working on the maintenance of some virtual machines (VM, Virtual Machine) and it happened to me that I did not remember the Password de Root nor from any other user. Oh! Poor me, what a mess I got! !What did I do!? At what point did I change the password that I don't remember? Then some thoughts followed that I can't reproduce but you can imagine ...
Searching the blog I found an old friend's post elav for Change root password on Debian / LMDE. Unfortunately it didn't work for me, so here is another method.
Well, the fact is that he did not remember the password and also the one he had stored in the KeePassX it didn't work, for any user. So after giving up on trying the thousand and one keys that crossed my mind I simply deigned to do a reset to the Password de Root from GRUB for my dear Debian.
Editing GRUB options
The process is relatively simple and all we need is to have GRUB installed (not to mention that we have to have access to see the machine boot, right?). In my case, I connected with the virt-manager (I have the VMs with KVM) and rebooted the machine, but this also works for a real machine.
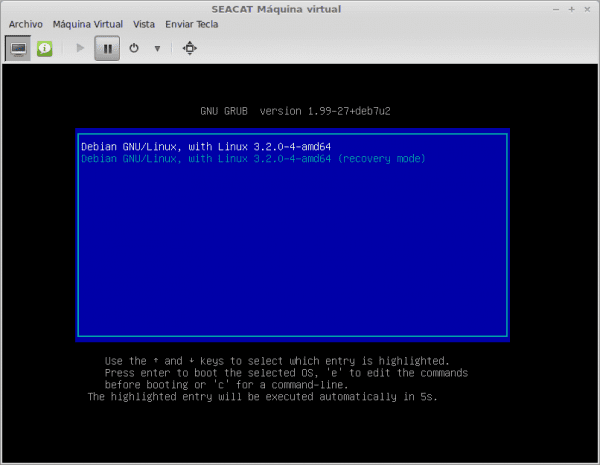
When the GRUB start we have to edit the boot options by pressing the key e.
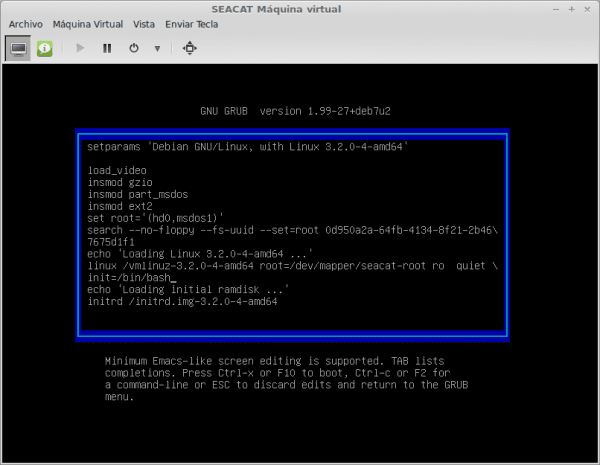
Now we must edit the options with which the system starts. We move to the line that loads the operating system kernel. It's the line that starts with linux:
echo 'Loading Linux 3.2.0-4-amd64 ...' linux /vmlinuz-3.2.0-4-amd64 root = / dev / mapper / seacat-root ro quiet
And we add:
init=/bin/bash
After the word quiet. The line should be:
linux /vmlinuz-3.2.0-4-amd64 root=/dev/mapper/seacat-root ro quiet init=/bin/bash
Once this has been edited, we just have to start the machine. As it says in the image, with Ctrl+x o F10 we start the system with these options.
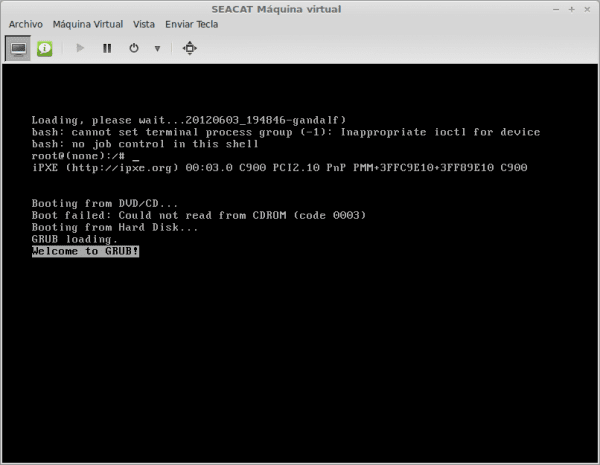
This will return a shell and we can edit the file / Etc / shadow.
Removing the Root password
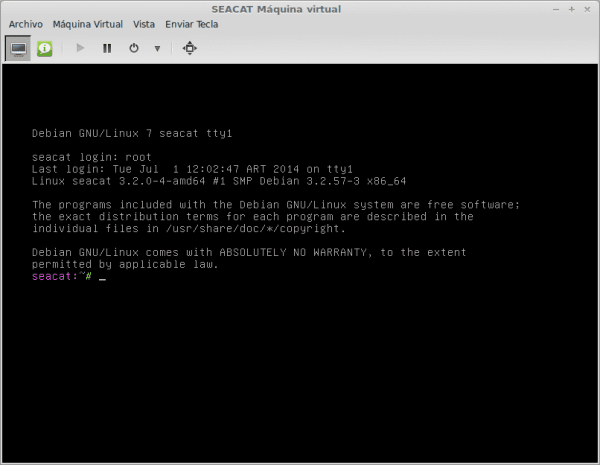
In the fourth line of the image, the prompt appears as follows:
root@(none):/#
The first thing we have to do is go back file system so that it has write permissions. For that we execute:
root@(none):/# mount -o remount rw /
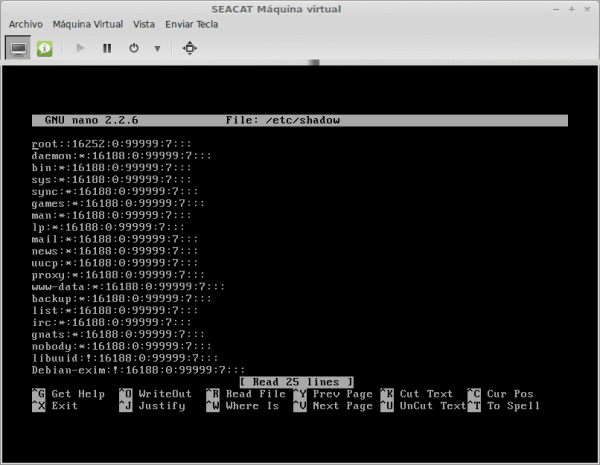
Now yes, we can proceed to edit with dwarf the file / Etc / shadow.
The file / Etc / shadow in the first line you have the information of root. For each line we have a set of fields and these are separated by two points (:).
The first field corresponds to the username, the second field is the hash corresponding to the Password. What we have to do is delete all the characters so that it remains without Password de root. As seen in the image:
We save the file with Ctrl+o and we left nano with Ctrl+x. Now we only have to restart the machine. When the system asks us to login we can enter as root without having to enter any Password.
Once the system starts, we enter as root and now we can run Passwd and we set a new one Password de root:
# passwd
I hope it has served!
This is one of those items that you have to have on hand, for when a catastrophe occurs. That sooner or later they happen!
I solved it in a very similar way, but without having to touch the shadows. In my blog I tell you how I did it.
http://unbrutocondebian.blogspot.com.es/2014/03/restablecer-la-contrasena-de-root.html
HELLO LITOS, I'M MEGAFAN FROM YOUR BLOG !!!!
Very good tuto. I liked how you went about resetting the root password.
THIS IS A TERRIBLE SECURITY BREACH !!!… .if it does work.
How to do to avoid it? Does anyone have any ideas?
It is not a security failure, it is a way to recover the system from a serious problem such as forgetting the administrator password.
For this reason, the CPDs have restricted access, to prevent you from fiddling with grub. But if you foresee that this is not enough or access cannot be limited, then you must protect grub
https://blog.desdelinux.net/como-proteger-grub-con-una-contrasena-linux/
Relax, in life nothing is certain! You just have to be aware of everything, be updating, monitoring! 🙂
I agree with the partner, this allows anyone to access our pc, serious, right?
Security flaw? It's as if you said that the option reset password your email was dangerous.
following the classic partitioning, and encrypting some partitions / folders with personal information, separating / root / home / usr / var / boot and so many mount points that they are now on one partition.
Greetings colleagues, very good blog and very good guide, I wanted to clarify that this step root @ (none): / # mount -o remount rw / is not necessary in systems based on debian and many systems based on Red Hat, and only a few Distros based on Gentoo are the ones that require this step, simply run passwd after performing the steps they describe to enter the system without a root password
Very good tutorial, as they say above, in the event of a disaster, it bails out, but this is almost always avoided with good change control.
Thanks for sharing.
Greetings.
to favorites or bookmarks = D
So basically if someone wants to access my pc, they just have to restart it, access grub, fiddle and voila.
Yes, unless you password protect Grub, which can be done safely.
Do not be scared, if the bad guy has physical access to the computer and knows something, it is inevitable that he will achieve his goals.
This grub method makes it a bit easier to do what you could always chroot from a live-cd / dvd.
But if the user who owns the pc changes the root password, he will realize why he will no longer be able to enter.
The screwed up thing would be for someone to chroot from a live-cd / dvd and make a copy of the / etc / shadow file on a pendrive to have fun with john-the-rupper on their own computer, it would be screwed because you wouldn't know if you your root and user passwords have been cracked.
Compa thank you very much it helped me a lot
Hello, from what I can see, you suppose that everyone who reads your tutorial must be an expert at least advanced in the handling of Linux, but what if he is not !!!!! So I wonder what that nano is, and how do I open it, with what command and where do I place that command? The / etc / shadow file, where is that file and how do I get to that folder to be able to do what this tutorial says. "EYE" I do not criticize the tutorial, on the contrary, it is very good, excellent, but you must also think about those who do not know (I include myself) much about command handling in Linux. I explain, I assumed that writing nano would open the editor and it did, but then I did not know how to get to / etc / shadow while in nano. And excuse the rest of users, but not all of us are experts, many of us are just enthusiastic learners…. more detail ... Thank you ...
great today something similar happened to me and I knew that through grub it is done and believe me several times I did it but much more complicated
In this tutorial he explains it very simply, I will apply it if possible this week
thank you for your contribution a thousand congratulations
BUE - NÍ - YES - MO.
It has saved me from reformatting Debian.
This is also true for Debian 8, which is what I have tested it with.
Thank you.
It did not work for me, I still have the same problem, I do not know if I have to see the fact that I install debian in graphic mode in virtualbox, I would like you to help me: /,
Great! I had formatted a note with debian 8 and it hit me when I forgot the pass. I agree that it is not a "failure", in any case I think that the security systems they propose are very strong. Regarding the user who has doubts, well, rather than saying "you suppose that we are all experts", I could simply place the doubts, without prejudice ;-D.
Thank you very much for sharing!
ps: I did have to carry out the mount step, I had edited the pass from my puppy linux, hehe, but still I had to enter the grub options to apply the passwd (no way!)
Hello, first, thank you very much for the contribution, it is just what I needed to not reinstall Debian 8, but I have a more serious problem, and that when I do the whole process and start in bash mode the OS does not work the keyboard ... nor does it detect it, nor does the keyboard lights work or anything at all, so I can't change anything from bash root mode.
PS: for what it's worth I had a similar problem when I installed debian, installed the grub boot loader on another independent partition and debian on another partition, I have experienced this before with other systems and it always worked for me, in this case with debian not , and esque when debian started just installed to the graphical interface neither the keyboard nor the mouse worked, just when you have to put the password to start session.
THANK YOU IN ADVANCE FOR HELPING OTHERS, GREETINGS.
Thank you very much for the contribution. Quick and effective solution 😉
Thank you! You saved me! ; D
hello everyone I need help I did the whole process to where I had to write r mount -o remount rw / but one of the things went wrong, and then I tried but it only goes as far as I write init = / bin / bash I give it ctrl + x, and from there some letters come out, they pass quickly but it does not reach the screen of r mount -o remount rw / what do I have to do?
Thank you very much for this tutorial, it was really very useful to me, in debian 9 it did not let me enter as root user and with this it was solved, once again thanks.
Perfect the Tuto very good you are a capo!
Hey.
I have tried applying this method but it has not worked for me.
The problem is that, although we can edit the "shadow" file, we cannot save it. Editing it without having privileges opens it in read-only mode.
Greetings.
[quote] The first thing we must do is remount the filesystem so that it has write permissions. For that we execute:
root @ (none): / # mount -o remount rw / [quote]
I think that's why you have to go back the fs.
I think I remember that for W there was also a way to access users and modify or remove password, through a livecd.
Step to leave my thanks, as appropriate. You got me out of a big trouble. I checked other blogs and this solution was the most complete and best explained.