Good day. Today I bring you some small tips, we are going to see the open ports that we have. To do this we will use NMap so we proceed to install it.
En Debian / Ubuntu:
# apt-get install nmap
then to see the open ports on your pc. (In local)
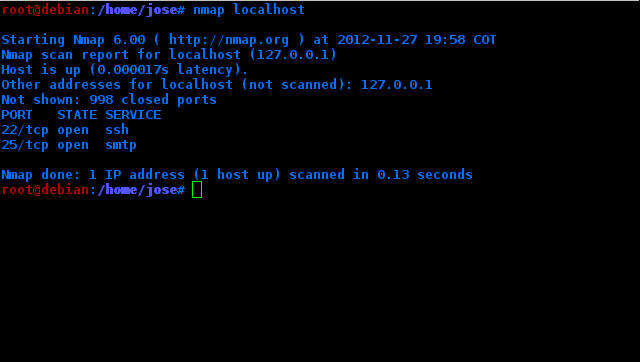
#nmap localhost
These are the ports that are open locally, that is, they do not necessarily go to the internet. In my case, 22 is open for ssh and 25 for smtp.
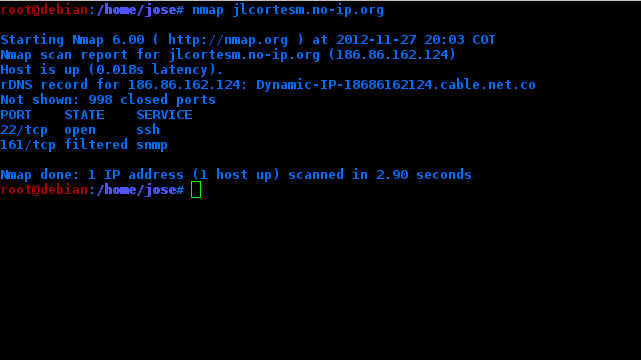
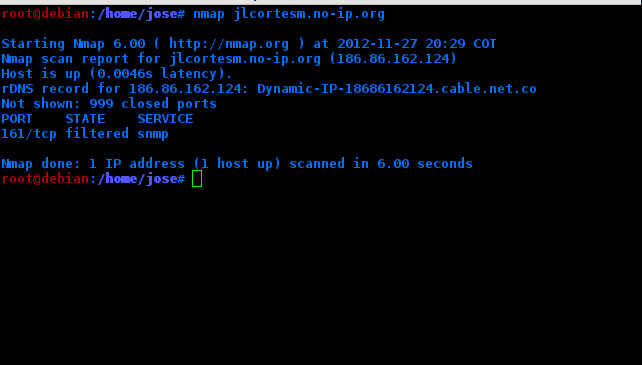
To see the open ports on my pc but on the internet I do the same nmap but with my ip address
In my case it appears that the host is on but it does not see any open ports (it only scans 1000). This is because even though the port is open on my pc, the Router is filtering it.
But if I open the respective port on the router ...
The fact that they can see which ports are open on my pc poses some risk on my machine. So I'm going to secure my ssh server a bit. For this I am going to change the default port (22) for any other ...
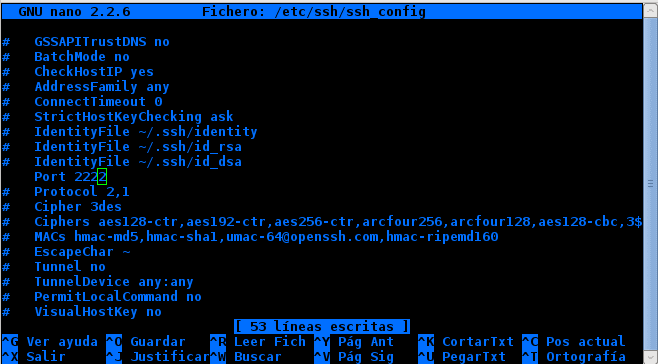
I go as root to the file / etc / ssh_config:
# nano /etc/ssh/ssh_config
let's go where it says # port 22 .. we delete the # and change the port for the one we want ..
In my case I will use 2222
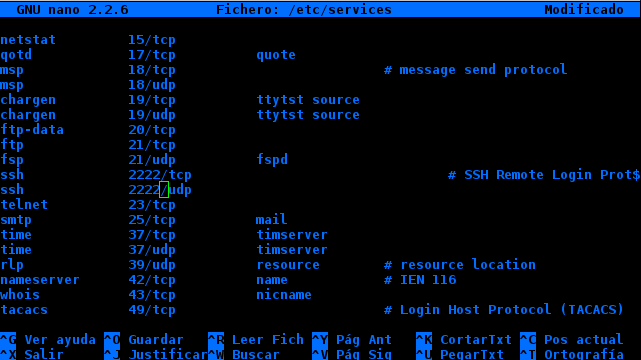
We do the same looking for the word "port" in the file / Etc / ssh / sshd_config changing it to the same port that we are going to use. Now we edit / etc / services
We seek ssh and we change the two ports for the one we changed before.
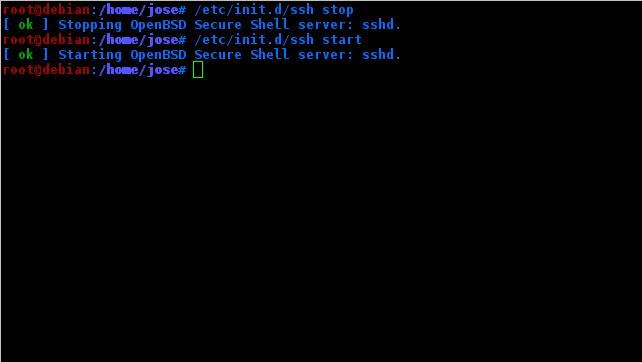
Now we reset the service.
And we do Nmap again.
As you can see. Nothing about our port and / or ssh service comes out.
But does the ssh work?
OF COURSE.
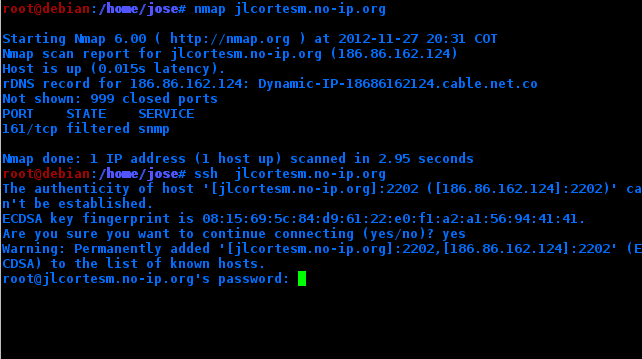
Important is that if you are going to enter from another computer, you obviously have to indicate the port you are using.
ssh -p 2222 IP (For example)
So you can change the ports of any other service.
Regards.!

Thanks for the tip, interesting.
And in Spanish? ha ha ha ha ha ha
This is a science, I tried it and it no longer connected to the internet, haha, a friend helped me solve it after reading the article on his lap, he liked it a lot and he is installing ubuntu on his laptop, when before he told me that it was not for him.
regards
haha I don't know what you have moved wrong .. But I put it as explicit as possible. But if you want I can make a video for you. 🙂
Naaaaah, I am denied for networks and English, I have wanted to learn for a long time and I have not really found an instructor who has patience for me, imagine.
Teach a 40-year-old man like he's 10, hahahaha
haha It's nothing .. With a hangout or something like that .. Sure you understand me.
Welcome to that hangout !!
^^
Compatriot, excellent contribution.
I dare to launch this challenge to see if port 2222 oO does not appear
Run: sudo nmap -v -sS -A -p 1-65535 localhost
PS: the scan will be slow ... I add the option «-v» so that you don't get bored watching the terminal do anything.
Obvious if .. But I'm talking about normal scan. The nmap has many options and features, knowing how to use it. no port escapes him.
Besides that there is always a way .. Especially in linux, nothing is totally safe .. It is only a small tip: p
My intention was not to belittle the cloaking tactic but the nmap command that I leave for when one does not remember the port that was chosen as the default replacement is good (it is difficult to remember ips and ports ...). In my case I have had to connect remotely via VNC to PCs where their port is not the typical 5900 or 5901; a normal scan would tell me there is no listening port for vnc so what is the solution? Answer: Use nmap and force it to query all ports. 😉
Of course, I was not offended far from it, We know that everything is not totally safe. There are only security levels. And there is always something beyond ... there is always something that violates security. It is a good contribution, you could do a little tutorial on nmap. 🙂 Greetings.
A perfect complement to the previous post. I don't know if you did it on purpose, but it turned out great. 🙂
This is only security for obscurity, unfortunately with the option -v of the nmap you identify that the port you put corresponds to the nmap. To try to protect yourself from nmap, you have to use iptables rules, which cannot completely protect a scan either. But hey, it works against hacking novices ...
Hi, a question, I do not understand why nmap does not remove the port after having changed it, does it bring a port range to scan by default?
Yes, nmap by default scans 1000 ports. If we know how to handle it, this is not enough to protect ssh or any other service from the clutches of nmap. The best would be a fail2ban and a psad.
@Jlcmux
Allow me to make some corrections on what you posted, I am correcting in parts:
1.
"These are the ports that are open locally, that is, they don't necessarily go to the internet. In my case, the 22nd is open for ssh and 25th for smtp."
This is not so. Those are the ports that are open on the host that you will scan within the range of the first 1024 ports, which is the range that NMAP scans by default.
"These are the ports that are open locally, that is, they do not necessarily go to the internet .."
You should clarify that the only way that they do not "go out" to the net is by being your machine on a swimming network (NAT by definition is itself a primitive firewall) and as long as the ports are not open on the device that make NAT (usually the router) and redirect (FORWARDING) those ports open to your machine.
Of course if the machine is directly connected to the modem then it IS exposed to the net.
To the command published by @taregon, which is the correct one to scan and tap all the ports of a machine, you can add, among other options, -sV so that nmap tries to discover which service runs on each port: sudo nmap -v -sS -sV -A -p 1-65535 localhost
Example:
Starting Nmap 6.25 ( http://nmap.org ) at 2012-12-06 13:39 ART
Nmap scan report for localhost.localdomain (127.0.0.1)
Host is up (latency 0.00021s).
Not shown: 999 closed ports
PORT STATE SERVICE VERSION
631 / tcp open ipp CUPS 1.6
2222 / tcp open ssh OpenSSH 6.1 (protocol 2.0)
2.
«The fact that they can see which ports are open on my pc poses some risk on my machine. So I'm going to secure my ssh server a bit. For this I am going to change the default port (22) for any other ...
I go as root to the / etc / ssh_config file:
# nano / etc / ssh / ssh_config
we go where it says # port 22 .. we erase the # and we change the port for the one we want .. »
NO! One thing has nothing to do with the other!
/ etc / ssh / ssh_config handles only client options so the port you set there will be the one the ssh client uses by default to connect to ssh servers instead of port 22.
You only do the change of listening port you are looking for by changing the option mentioned in the / etc / ssh / sshd_config file.
Finally, with this web tool we can test which ports are or are not open on our machine, which ones are hidden, check that the ping echo is disabled and some other things: https://www.grc.com/x/ne.dll?bh0bkyd2
Greetings.
Very good review. i liked thanks 😀
Great tutorial of Nmap
🙂 Greetings !!!
colleagues, does anyone know how I can do to know the open ports of another person ??? from my computer ???
Use the command: nmap XXXX
Where the x's are the ip of the computer to scan
Hello, first of all thanks for sharing.
I have a problem, hopefully you can help me: When doing an nmap with my ip from the same machine it tells me that port 3306 is open and with netstat I see that the port is listening; However, when doing a scan with nmap from another pc, it does not indicate the open port 3306.
Also I already changed the bin-address to 0.0.0.0
I am trying to connect a java application with a DB on a LAMP server and the application works because I have already made queries on another pc where I set up a wamp server for testing and everything is ok.
Any ideas? I do not know what else to do