
When we talk about systems focused on privacy actually few exist in Linux And on second thought, most of them take Debian as a base, is it a coincidence? Although from a practical point of view Debian has positioned itself as one of the most robust distributions with a large number of applications.
Although from a personal point of view for this I would prefer Fedora or Arch Linux, but that is something else. This time we are going to talk about a Linux distribution that is focused on privacy.
About Septor Linux
Septor is a Linux distribution that provides users with a preconfigured computing environment to browse the Internet anonymously.
It is based on the Debian "Testing" branch and uses Privoxy, a proxy to improve privacy, along with the Tor anonymity network to modify web page data and HTTP headers before the page is processed by the browser.
The Septor distribution uses KDE Plasma as the preferred desktop environment and also includes a launcher to download the latest Tor browser as well as OnionShare for anonymous file sharing and Ricochet for anonymous instant messages.
In this case Debian (Buster) was the one used as the basis for the operating system in its version still under development, with a graphical KDE environment.
The distribution can be used via live mode, with the help of a USB stick or it can be classically installed on a hard disk.

It would be very difficult to buy Septor with Tails, Kodachi Linux or some other distribution with the same approach. Since each of these contributes its own idea.
Top Septor Linux Packages
Currently the The system is mainly made up of the packages that make up Debian Buster and at the heart of the system we find the Linux Kernel 4.19 as well as the KDE Plasma desktop environment in its version 5.14.3.
According to the project task, for the pre-installed software, the applications that were considered suitable for the distribution of this type were selected. A couple of apps got a replacement, so now the full list of programs looks like this:
- Dolphin and KFind to manage and search files.
- Synaptic and Gdebi to manage and install the software.
- Graphics / Multimedia: GIMP, Gwenview. VLC, K3b, Guvcview
- Office: LibreOffice, Kontact, KOrganizer, Okular, Kwrite, Kate
- Internet: Tor Viewer, Thunderbird, Ricochet IM, HexChat, QuiteRSS, OnionShare
- Tools: Gufw, Konsole, Ark, Sweeper, KGpg, Cleopatra, MAT, KWallet, VeraCrypt, Bootis
For access to the files in the root folder, there is an icon available in the menu. In the first launch, the Ricochet instant messaging client will ask if the user wants to connect through the Tor network.
HexChat and QuiteRSS are configured by default on the Tor network, and users can modify this by configuring these applications on the Network.
Download Septor Linux
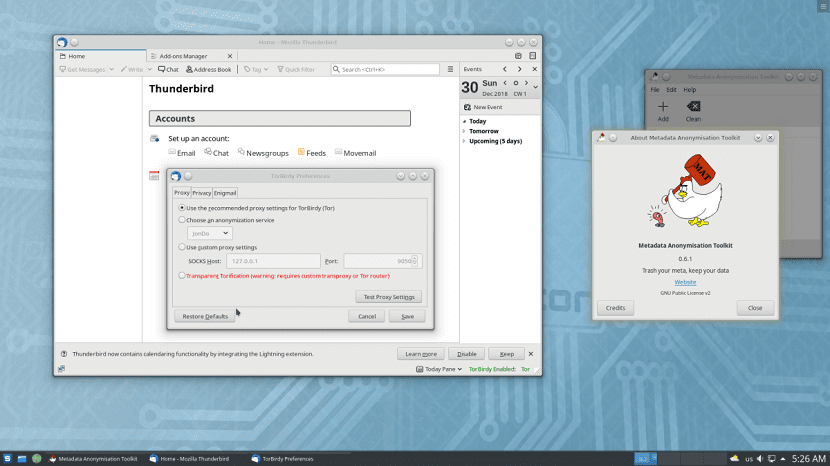
Finally, if you still do not have Septor Linux installed on your computer and you want to download and install this Linux distribution focused on user privacy on your computer or you want to test it under a virtual machine.
You just have to go to the official website of the distribution and in its download section you can get the image of the system. The link is this.
You can save the downloaded image to a USB device with the help of the Etcher application.
Septor Linux is currently distributed as a single Live DVD ISO image It contains packages optimized only for 64-bit hardware architectures (x86_64) and can be burned to a 2GB or larger USB flash drive as well as a DVD.
If you are newcomers to Linux and are encouraged to go through the installation process, I can tell you that this is simple and takes about 10 minutes.
The graphical interface of the installation process defaults to English, which can already be changed in the first step.