Notice: next we will talk about various tools compatible with most of the GNU / Linux distributions; We will talk about how to use them, how they work and their basic configuration. At the end we will talk about several tips so that your browsing experience is appropriate.
GNU / Linux systems are known for their relative security, superior to commercial systems like Microsoft Windows; Even so, they are not spared from attacks, scam techniques, rootkits, pishing, which have more to do with the user's browsing habits on the Internet and their indiscriminate use of repositories and applications that do not come from official sources, even installing official software is vulnerable: as an example installing Google Chrome, which sends all your browsing habits to Google servers, invites you to run malicious plug-ins like Flash or run proprietary JS. Many computer security gurus have told me that it is better, in an application dedicated to privacy, that it is free, so that experts from all over the world can test its effectiveness, even suggest errors and report bugs.
There are hundreds of applications and tools, these are only some of the most used and tested, I recommend them.
Applications:
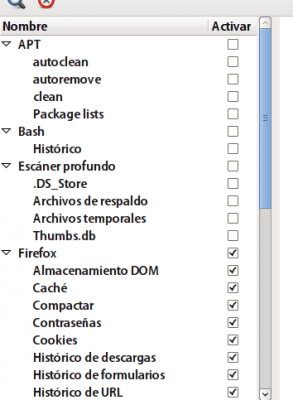
- bleachbit. This application that is available in the official Debian repositories serves to clean your system superficially and also deeply. Eliminating for example broken logs, terminal command history, image thumbnails, etc. In the image we see the list of options that can be "cleaned" with this tool. EFF in your guide (https://ssd.eff.org/en/module/how-delete-your-data-securely-linux) Self Defense for Surveillance shows how to use this tool. installation: sudo apt-get bleachbit.
- Steghide. Consider this as a second layer of security to hide information using stenography. Hide for example a compromising image or sensitive private information inside another normal-looking image, you can hide documents and several other things. Here is a little tutorial http://steghide.sourceforge.net/documentation/manpage_es.php, you can also consult the manual from the terminal. Installation: sudo apt-get install steghide
- GPG. In a previous post I have spoken and here on the blog you can find information about the use, installation and configuration of this great encryption tool. Its good use guarantees security against the possible interception of your email and online communications. The great thing about this is that it comes pre-installed on most distros.
- icedove. The Debian version of Thunderbird has been discussed about this tool together with the Enigmail extension in a previous post. In addition to managing your emails, it works wonderfully protecting them.
- Iceweasel (uBlock, about config). Not only is it a free and open source browser, it also includes several privacy settings by default: it does not include the telemetry that Firefox has by default. Although it has problems running videos on YouTube, it is a great browser that with the indicated add-ons, would be a great ally of yours when you explore the web safely. Let's talk about uBlock, the extension that not only blocks ads, you can prevent the execution of scripts, make whitelist, blacklist, social buttons, etc. Testing Iceweasel security with this plugin, the web https://panopticlick.eff.org/ The EFF gives us a result that indicates that the browser has strong protection against tracking and surveillance. Even so, the identifier of the browser is being disclosed, as well as our operating system. The following preferences can be modified in the about: config of your browser, use this project on Github: https://github.com/xombra/iceweasel/blob/master/prefs.js
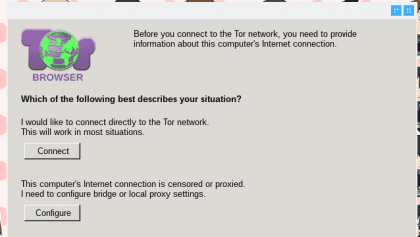
- Tor Browser (Tor Button, NoScript, HTTPS Everywhere). Not only is using the anonymous browser, it is especially important to note that it includes powerful extensions that, together with the default encryption of the onion network, make a fantastic experience in terms of protecting your privacy. The NoScript plugin is useful to block malicious code possibly running on multiple sites, it is also possible to avoid running JavaScript with dangerous elements. While HTTPS Everywhere helps us by forcing all possible connections through the secure hypertext protocol. All these extensions are installed by default in the Tor browser, other features and tips can be found on the project page: https://www.torproject.org/docs/documentation.html.en
- TrueCrypt. Encrypt your disks, partitions and external drives. Keeps your files safe by preventing someone from opening them without the correct password. It works like an electronic safe, where you can store your files under lock and key, safely. This tutorial for Linux can vary some commands on Debian based systems. https://wiki.archlinux.org/index.php/TrueCrypt
- chkrootkit Here installation details: http://www.chkrootkit.org/faq/. Easy to use and powerful tool that reviews binaries, system files, makes comparisons and returns the result, which can be possible changes, infections and damages. These changes can do: execute remote commands, open ports, perform DoS attacks, install hidden web servers, use bandwidth for file transfers, monitor with keylogers, etc.
- TAILS. The safe operating system. If you have ever read the novel Little Brother (by Cory Doctorow, activist and writer), there is always a mention of a secure operating system, which encrypts all communications over the network; Well, that's what TAILS does, in addition to integrating great tools for analysis, protection and privacy improvement. Even its execution as a live operating system, it does not leave traces of its execution on the machine. The official download of the ISO image is in the following link (link) and the complete documentation: https://tails.boum.org/doc/index.en.html.
- Tor Messenger, Jabber. A previous post has mentioned the creation of messaging services using XMPP and others, there is complete information about these tools. You can also check: https://ossa.noblogs.org/xmpp-vs-whatssap/
Tips:
Thanks to friends of the https://ossa.noblogs.org/ and various activist protection sites, the following mountain of tips has been compiled to help you navigate safely while protecting your privacy.
From OSSA: https://ossa.noblogs.org/tor-buenas-practicas/
From Whonix: https://www.whonix.org/wiki/DoNot
From Hacktivists: http://wiki.hacktivistas.net/index.php?title=Tools/
Take into account that privacy is a right, act, encrypt, use Tor, do not benefit proprietary software, question, be curious.


For the issue of volume encryption, I would change TrueCrypt (since the project was abandoned a long time ago) for VeraCrypt, which is a fork that works the same and they have already incorporated performance and security improvements, and those that remain to come. In fact, from what I have seen it is a little known project so far that is taking a lot of life.
Regards!
Bleachbit I don't think I will use it again. Suddenly last week my laptop stopped working (or started) and it was just less than a week since I had installed Bleachbit. I can not assure that it is because of this program but maybe ...
It is also true that I installed the most updated version (from the official website) because the one that came in the Linux Mint repositories was out of date, it is the bad thing about this distribution.
Chkrootkit I tried it but then you get positives that you are looking for and it turns out that they are false positives.
I think that if you use Linux mint, what affected you was the intrusion that the Linux Mint servers had. It seems that they managed to sneak malware and rootkit into the updates and they did not notice!: P
I forgot, when I did a cleaning with Bleachbit it erased almost 1GB every time, it seems that it is doing an incredible cleaning but in reality what it takes up most of what it deletes are the files of web browsers and the. "By hand" very easily, removing that in each cleaning erased about 100MB.
What do you recommend to do ccleaner-style maintenance? I have been installing Debian for a week and the applications that I use the most, but after installing so much I think there is a lot to delete. I stay tuned thanks.
I'm not really an expert, I used Bleachbit for maintenance because I think it's the closest thing to Ccleaner but I don't trust it anymore.
What I am going to do from now on is from time to time:
sudo apt-get clean
sudo apt-get autoclean
sudo apt-get autoremove
And delete some folders from .cache and you're done. I also didn't notice any improvement when I first used Bleachbit.
TrueCrypt was a good project but it is already dead, although the last analysis of its source code says that it is safe, new vulnerabilities arise every day, the 0-day being the most dangerous, for that reason it is essential that an encryption program like TrueCrypt counts with an active community, to solve possible vulnerabilities.
On the other hand, the Apache 2.0 license for VeraCrypt (© 2006-2016 Microsoft) does not give me much confidence, I prefer a GPL or BSD instead.
I recommend:
As Browser extensions (Iceweasel and Firefox only) use:
Finally I would like to say that I really liked your posts, I hope they will be published more with thematic of security, privacy and a bit of hardenig XD and finally I want to say that I loved Steghide, I did not know him.
Excellent post, how do I find you in GNU social?
I just created an account
It was necessary to analyze an antivirus such as ClamAV (which does not hurt) or an antimalware ... (It is not far from the issue of privacy)
Regarding communication Telegram is very popular and more and more. We also have Tox and the recent RIng (mentioned in another post).
Thanks for all your contributions, I didn't know that Bleachbir failed this badly; it has always worked well for a long time on my computers. Regarding GNU social, I don't know if it's the place to post it, but I have a post planned on free and uncensored alternatives to Twitter and Facebook.
Regards!