!Hello friends! Today I bring you an alternative to using an FTP Server for secure file transfer. Already the colleague KZKG ^ Gaara posted one based on the package jailkit. The one we will develop is based on the packages that we have more at hand in our repository.
We will see:
- Enter required
- How do we configure the Openssh-server?
- How do we create users?
- How do we modify home directories to make the cage work?
Enter required
We often need files to be copied from remote computers to our machine. Many have asked me about it. Do I install an FTP? How do I install a SAMBA? Well, let's go from the simple to the complex. From the outset, why complicate ourselves if we have the OpenSSH Server installed ?. And if we don't have it, with the simple command:
aptitude install openssh-server
Now we have it !, and then we will be able to transfer files safely via the SFTP (Secure File Transfer Protocol) protocol, which uses SSH (Secure Shell) for encryption.
By default, users with permission to start a remote session via ssh user @ my team, they will be able to see almost all the files stored on our system, which may not be to our liking, or that for security reasons we should not allow it.
This article will help us configure the OpenSSH Server so that the users that we want are restricted to their personal directory / home / user. We clarify that, With this method, declared users will not be able to start a remote session through an ssh console or through PuTTy. They will only be able to transfer files to or from their personal directory on our computer or server.
The method described here is valid for Debian versions 5 (Lenny) or higher, and for Ubuntu versions 9.04 or higher. The SSH package version of Hardy or Ubuntu 8.04 is very late and does not support the configuration that we will describe below.
How do we configure the Openssh-server?
As the user root we edit the file / Etc / ssh / sshd_config with any simple text editor. We recommend the use of dwarf in console mode.
nano / etc / ssh / sshd_config
We want the following line to be present:
Subsystem sftp
In Lenny and Squeeze there are:
Subsystem sftp / usr / lib / openssh / sftp-server
In case it does not exist, we add at the end of the file:
Subsystem sftp internal-sftp
We continue with the editing of the file sshd_config and we add at the end:
Match group group-sftp ChrootDirectory% h X11Forwarding no AllowTcpForwarding no ForceCommand internal-sftp
We save the changes and restart the service:
/etc/init.d/ssh restart
How do we create users?
First we create the «group»That we declare in the sshd_config. Be careful with the name that we chose previously, it will not be that it already exists and is a group belonging to the System. If we do not want to restrict existing users on our system, we must create new users so that they can transfer files. For the cage to work, we also have to make them, members of the group in question.
addgroup group-sftp adduser user1 adduser user2 [----] usermod -G group-sftp user1 usermod -G group-sftp user2
To check the creation of the group and users, we can do:
less / etc / password less / etc / group ls -l / home
And the users should appear usuario1 y usuario2as well as the groups group-sftp and those corresponding to the created users. Also, when listing the directory / Home, the home directories of each user created will appear.
How do we modify home directories to make the cage work effectively?
We must increase the security of the personal folders of each user created so that they cannot create additional folders under their personal directory, and with write permissions where we want (not where they want) 🙂:
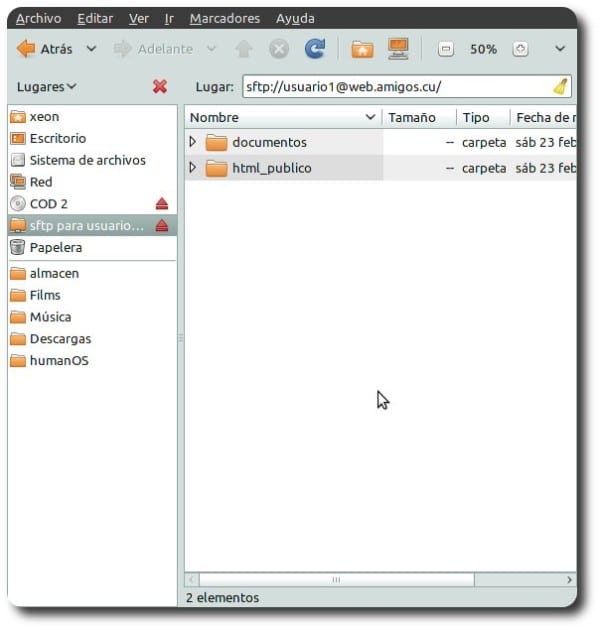
chown root: root / home / user1 / home / user2 chmod 755 / home / user1 / home / user2 cd / home / user1 mkdir documents html_public chown user1: user1 * cd / home / user2 mkdir documents html_public chown user2: user2 *
Users belonging to the group group-sftp, from now on they will be able to log in with their names and passwords via SFTP only, and they will be able to transfer files to and from the directories located below their personal folder and that were created by us, but they will not be able to see the rest of our file system.
For the transfer of files and folders, we can use Nautilus, Konqueror, WinSCP, FileZilla, and others that support the SFTP protocol. In the case of Konqueror, we must use fish: // user @ remotecomputer.
We hope this article will be of practical use to us!
Until the next adventure, friends!
Good article. A very secure way to share files. Thanks so much for the explanation. 🙂
Excellent
And isn't it more comfortable to use sshfs?
For our team the remote folder would appear as one more folder with the same characteristics.
Hello Federico, as always excellent article. I am very happy to be able to read your posts from the Internet now.
A hug,
Jako
How about Jacobo, no Federico does not agree directly. Hey when you come back no more ubuntu you paint human green and full opensuse. A hug. 😉
You're making excellent contributions, keep it up 😀
Thanks a thousand KZKG ^ Gaara, and Thanks to EVERYONE for your feedback
Can a user be caged in a folder other than / home / user /… ..?
What I want to do is cage a user in the / media / hdd / folder ...
I need to do it this way since the server is a Raspberry Pi with Raspbian, and it has the / home /… / folder on a sd card, which would fill up in no time
I have tried it in several ways and the result in client is always «Broken pipe», and the result in fatal server: bad ownership or modes for chroot directory component «/ media / HDD /»
Thank you very much to all
I think you're going to have to tell the system that that user's home folder is / home / HDD, as long as that partition has a native linux format, that is, ext4; ext3; etc. Example, if the user is jae -for short- you must execute something like this:
: ~ # usermod –move-home –home / home / HDD jae
Also see the man usermod. Cheers
I have a problem, or I have a service in amazon with a public friend and I have to enter through sftp to place or remove files.
I've done it before and everything is fine but today he did something to me that hadn't happened
Inside the ami there are a series of folders and one of them is a captive internet portal (page for my users) it turns out that there I do promotions and publicity for my users and I constantly make modifications and upload them through sftp (with winscp) root permissions and the root pass
I have given chmod 777 for write permissions and everything had gone well
but today when updating the web and uploading the index.html and its other files it gave me the names but it has left me with no bytes that is to say zero (blank) now you don't see anything on my web
I have closed the session and entered again, gave permissions again, change user, update, try to put other files, generate new ones and it always does the same
it gives me the files but they have no data
Can somebody help me ???
I would very much appreciate your answers
first of all, Thanks
atte
Mr. Irving Hernandez
Hello how to use filezilla, I have already seen several modes and I still cannot connect.
It's wrong.
Good afternoon,
Perform the procedure and the caged works perfectly, however when trying to write on the folder «documents» or «html_publico» it gives me access denied. It has the permissions mentioned and nothing that allows it.
drwxr-xr-x. 2 user1 user1 4096 Mar 11 13:16 docs
drwxr-xr-x. 2 user2 user2 4096 Mar 11 13:16 html_publico
The result is access denied when trying to write to any folder. However, performing a get does allow it.
I hope you can help me as soon as possible.
Greetings.