
WordPress: 10 best practices in terms of security
WordPress (WP) is known as the most popular CMS, among many things, having been designed with an emphasis on accessibility, performance, and ease of use, being in continuous development (current version 5.2), have a huge community of users in many languages and have a huge customization capacity through the use of own or third party themes and add-ons.
Also for being very safe, but for that, as in any application or system, good practices must be followed to achieve a secure long-term implementation. And in this post we want to provide some basic recommendations in this regard.

Introduction
WP being the most popular CMS for building websites, it is also usually a frequent target of computer attacks, so apart from its constant updating, requires frequent maintenance, updating, and security procedures for thus avoid weaknesses due to vulnerabilities in add-ons, weak passwords, outdated software, among many other reasons, that is, make greatly reduce your vulnerability to any intended or unforeseen attack.
In addition, WP like any other Content Management Systems (CMS) allows you to quickly and efficiently build a website and then put it online. Its highly capacity for work and growth, via modules, complementary themes, makes it easier than ever to achieve this task but without the need for the long years of learning that are usually required for this.
However, a side effect nothing pleasant that can arise from this, it may be that some managers of said tool, usually bypass, the measures necessary to ensure that the website created or maintained is secure. For this reason, it is important to keep in mind some general and specific measures (good practices), about WP or any other CMS and website to keep it safe.
Good practices
1.- Strengthen your security in general
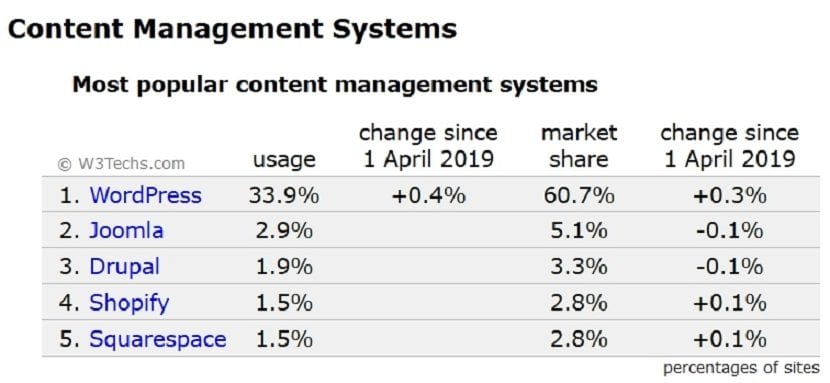
WP surely easily exceeds 30% of the base of active websites on the Internet today, which makes it a favorite target for invaders and / or attackers (hackers / crackers) with good or bad intentions. Therefore, a known and already successfully exploited vulnerability on a similar site with WP will be tried on other similar sites with WP.
So if you manage and / or use one or more website (s) with WP make sure you are more careful, thorough and aware of their online security. Keep in mind that most of the security violations analyzed and reported on websites with WP had little or nothing to do with the core of the application itself, but a lot to do with everything related to its implementation, configuration and general maintenance, carried out incorrectly by developers or administrators. '

2.- Know your vulnerabilities
WordPress has about 4.000 known security vulnerabilities, distributed as follows: WP Core (37%), Plugins (52%) and Themes (11%), according to a recent report from the WPScans website, which is now called WPSec (since 01-05-2019). Investigate the security vulnerabilities facing your website and find a solution to resolve these issues. Avoid running insecure versions of WP Core, or its plugins and themes.
Focus on the following security topics on your WP or website, that is, on The different types of Attacks from:
- Brute force: Reinforcing security on your login page.
- File inclusion: Strengthening the security of your wp-config.php configuration file.
- SQL injection: Strengthening the security of your MySQL database associated with WP.
- Cross Site Scripting: Strengthening the security of used WP plugins.
- Malware infection: Reinforcing the general security of your website to prevent unauthorized access, the insertion of malware and the subsequent collection of confidential data by these malicious codes. The most frequent Malware or attacks are usually of the type: Backdoor, Spam SEO, HackTool, Mailer, Defacement and Phishing. Look to protect your site against each of these types of malware or attack.
Remember that once any website is compromised, its SEO ranking can suffer. Because search engines tend to quickly log compromised websites so that browsers will either give visitors warning signs or completely block the ability to navigate those sites.

3.- Know the infrastructure of your Hosting provider
If your website uses external hosting, that is, hired outside of your infrastructure, don't skimp on costs to ensure quality of service from your hosting provider. Above all, if he hosts his site under the "shared hosting" scheme.
As poor quality 'shared hosting' can make your site more vulnerable when one of several websites stored on the same server is compromised. That is, if a website is hacked on a server with "shared hosting", attackers can also gain access to other websites and their data.

4.- Know the eweb technical specifications from your Hosting provider
When it comes to evaluating a hosting provider, its infrastructure is not everything. The technical web specifications used by your hosting provider to achieve better security of the hosted websites is also important. Make sure that it follows the following recommended security guidelines for hosting your website:
- Easy installation of SSL certificates
- Active management of web server software versions.
- Firewall protection
- Record of accesses to the website
- Routine security audits
- Malicious activity detection
- Support for SFTP (not just FTP), TLS 1.2 and 1.3, and for PHP 5.6, at a minimum, although 7.0 onwards is recommended.
All this is necessary, at a minimum, to increase the security of your website with or without WP as a used CMS.

5.- Beware of Themes and Complements used
The plugins and themes that are installed matter a lot at the security level. Aim to use only official WP or Community certified themes and plugins, well known commercial repositories or directly from reputable developers. Since many of them (not certified) can contain malicious code.
It doesn't matter how much you protect your website from WP if you install the malware. Do your research before downloading and installing any themes and plugins, or their developer or promoter website, and have your reservations with the free or discounted ones.

6.- Try to update your CMS frequently
Updates to your web platform are very important for your security. Whether it's WP your CMS or not, outdated versions of your Core, Theme, or plugins can lead you to harbor known vulnerabilities on your website. In the case of WP, which is open source, there is a team specifically dedicated to this issue within the Core of the application.
Every security vulnerability discovered in WP is corrected and eliminated immediately in order to solve each new security problem discovered in WP. Because of that update WP and all its themes and plugins to the latest version is a vital component of a successful security strategy.

7.- I found a suitable password
The quality or strength of our passwords on websites is very important. Logging in to our websites is a preferred target for exploiting vulnerabilities, because it provides the easiest access to your website's administration page.
Brute force attacks are the most common method to exploit your login, discovering the username and password combinations to gain access to the website. In the specific case of WP, by default it does not limit the number of failed login attempts that someone can make, therefore, the most recommended is the use of a complex password for the login of your WP administrator.
When choosing a password, take into account these 3 fundamental requirements based on the CLU format (Complex, Long, Unique):
- COMPLEX: Passwords should be as random as possible and least related to the Web Administrator or the Website.
- LONG: Passwords must be 12 or more characters in length. And fortified with restrictions or limitations on the number of failed connection attempts.
- ONLY: Do not reuse passwords. Each password must be unique in time. This simple rule drastically limits the impact of any compromised password.
Recommendation: Use a password manager such as “LastPass” (online) and “KeePass 2” (offline) to generate and store all your passwords in an encrypted format.

8.- Always have your anti-disaster plan prepared
If you use WP remember that it does not have a built-in backup system. Include one as a priority, so you always have an up-to-date backup of your website. Backups are critical and a general security strategy to implement.
Don't forget that you should not only back up your used websites and databasesbut all the settings of the whole server through automated tasks with script or cloned image systems, to facilitate the necessary restorations and re-installations in the shortest possible time.

9.- Increase your security using 2FA
Strengthen your WP admin login or your website using two-factor authentication (2FA) mechanism, which is one of the best ways to secure your website today. Two-factor authentication adds an extra layer of protection to your website login, by requiring that the use of your password require an additional time-sensitive code from another device, such as your smartphone, to successfully login. .
In the case of WP that does not offer this functionality by default embed the same by using a pluginsuch as iThemes Security to add the same.

10.- Use any necessary security accessories
Most CMS like WP make use of plugins to increase the security potential of themselves. In the specific case of WP, the use of the security plugin called iThemes Security is recommended. to add even more protection to your website. This plugin blocks WP, fixes known holes, stops automated attacks, and strengthens user credentials.
It has a free version (iThemes Security) and a paid version (iThemes Security Pro) which obviously provides more security features such as 2FA, scheduled malware scans, user registration, among other things.
Conclusion
Whether it's over WP or another CMS, you can avoid most of your website security problems simply by following these best or good security practices. Your website deserves and must have the necessary security measures in place to guarantee or minimize its inviolability in these times so troubled by the activity of hackers and crackers.
Finally and as an addition, we recommend you read this other article on our blog on the subject to strengthen the security of your website, called: Linux Permissions for System Administrators and Developers.