Janar jeri na jerin: Hanyoyin sadarwar Kwamfuta don SMEs: Gabatarwa
Barka dai abokai da abokai!
Tare da wannan labarin munyi niyyar gabatar da Takaitawa zuwa batun Tantance kalmar sirri ta hanyar Pam. Mun saba amfani da Workstation din mu tare da Linux / UNIX tsarin aiki a kullum kuma a wasu lokutan mukan tsaya muyi nazarin yadda tsarin tantancewa ke faruwa duk lokacin da muka fara zama. Shin mun san da wanzuwar rumbun adana bayanai / sauransu / passwdda kuma / sauransu / inuwa hakan shine babban tushen bayanan Shaida na Tantance bayanan masu amfani na gari. Muna fatan cewa bayan karanta wannan sakon zaku sami - aƙalla - bayyananne game da yadda PAM ke aiki.
Gasktawa
Tabbatarwa - don dalilai masu amfani - shine hanyar da ake tabbatar da mai amfani da tsarin. Tsarin tabbatarwa yana buƙatar kasancewar saitin bayanan asali da takaddun shaida - sunan mai amfani da kalmar wucewa - waɗanda aka gwama su da bayanan da aka adana a cikin rumbun adana bayanai. Idan takaddun bayanan da aka gabatar sun yi daidai da na waɗanda aka adana kuma asusun mai amfani ke aiki, an ce mai amfani ya shiga. na kwarai cikin nasara ko nasarar wucewa da gaskatawa.
Da zarar an amintar da mai amfani da shi, ana ba da bayanin ga sabis na kula da hanya don ƙayyade abin da mai amfani zai iya yi a cikin tsarin da waɗanne albarkatun da suke da shi izini don samun damar su.
Bayani don tabbatar da mai amfani ana iya adana shi a cikin rumbunan adana bayanai na cikin gida a kan tsarin, ko kuma tsarin na cikin gida na iya komawa zuwa bayanan da ke akwai a tsarin nesa, kamar su LDAP, Kerberos, bayanan bayanan NIS, da sauransu.
Yawancin tsarin aiki na UNIX® / Linux suna da kayan aikin da ake buƙata don daidaita sabis na tabbatar da abokin ciniki / sabar don mafi yawan nau'ikan bayanan bayanan mai amfani. Wasu daga waɗannan tsarin suna da cikakkun kayan aikin zane kamar Red Hat / CentOS, SUSE / openSUSE, da sauran rarrabawa.
PAM: Module Ingantaccen Module
da Module da aka Shiga don Tantance kalmar sirri Muna amfani dasu kullun idan muka shiga cikin Desktop ɗinmu tare da tsarin aiki bisa Linux / UNIX, da kuma wasu lokutan da yawa idan muka sami dama ga ayyukan gida ko na nesa waɗanda ke da takamaiman tsarin PAM na gida. saka don tabbatarwa kan wannan sabis ɗin.
Za a iya samun dabarun amfani na yadda ake shigar da PAM Module ta hanyar tsarin jihar na Tantance kalmar sirri en ƙungiya tare da Debian kuma en wani tare da CentOS cewa zamu ci gaba.
Debian
Takardun
Idan mun girka kunshin libpam-doc zamu sami ingantattun takardu wadanda suke cikin kundin adireshi / usr / share / doc / libpam-doc / html.
root @ linuxbox: ~ # ƙwarewa shigar libpam-doc tushen @ linuxbox: ~ # ls -l / usr / share / doc / libpam-doc /
Hakanan akwai ƙarin takaddun shaida akan PAM a cikin kundin adireshi:
tushen @ linuxbox: ~ # ls -l / usr / share / doc / | grep pam drwxr-xr-x 2 tushen tushen 4096 Apr 5 21 11 libpam0g drwxr-xr-x 4 tushen tushen 4096 Apr 7 16:31 libpam-doc drwxr-xr-x 2 tushen 4096 Apr 5 21:30 libpam-gnome- keyring drwxr-xr-x 3 tushen tushen 4096 Apr 5 21:11 libpam-modules drwxr-xr-x 2 tushen tushen 4096 Apr 5 21:11 libpam-modules-bin drwxr-xr-x 2 tushen tushen 4096 Apr 5 21: 11 libpam-runtime drwxr-xr-x 2 tushen tushen 4096 Apr 5 21:26 libpam-systemd drwxr-xr-x 3 tushen tushen 4096 Apr 5 21:31 python-pam
Mun yi imanin cewa kafin mu fita neman takardu a Intanet, ya kamata mu sake nazarin wanda aka riga aka girka ko wanda za mu iya girkawa kai tsaye daga rumbunan shirye-shiryen da ake da su don wani abu kuma a lokuta da yawa muna kwafa su zuwa rumbun kwamfutarka. Samfurin wannan shine mai zuwa:
tushen @ linuxbox: ~ # kasa / usr / share / doc / libpam-gnome-keyring / README gnome-keyring shiri ne wanda yake adana kalmar sirri da sauran sirrin masu amfani. Ana gudanar dashi azaman diemon a zaman, kwatankwacin ssh-wakili, da sauran aikace-aikacen suna gano shi ta hanyar canjin yanayi ko D-Bus. Shirye-shiryen na iya sarrafa maballin da yawa, kowannensu yana da kalmar sirri ta kansa, sannan kuma akwai maɓallin kewayawa wanda ba a taɓa adana shi a faifai ba, amma ana manta shi lokacin da zaman ya ƙare. Aikace-aikacen aikace-aikacen libgnome-keyring na laburaren suna amfani dasu don hadewa tare da tsarin maballin GNOME
Wannan fassarar da yardar kaina yana so ya bayyana:
- gnome-keyring shine shirin da ke kula da kiyaye kalmomin shiga da sauran sirrin masu amfani. A kowane zama ana gudanar dashi azaman ne, kamar na ssh-agent, da sauran aikace-aikacen da ake samu ta hanyar sauyin yanayi - yanayi ko ta hanyar D-Bus. Shirin na iya ɗaukar maɓallan maɓalli da yawa, kowannensu yana da kalmar sirri ta kansa. Hakanan akwai wani maɓallin kewayawa wanda ba a taɓa adana shi a kan diski ba kuma ana manta shi lokacin da zaman ya ƙare. Aikace-aikace amfani da libbinome-keyring library don haɗawa tare da tsarin maɓallin GNOME..
Debian tare da Tsarin Aiki na Base
Mun fara daga kwamfutar da muka girka Debian 8 "Jessie" a matsayin Tsarin Gudanar da Ayyuka kuma yayin aikin shigarta muna zaɓar kawai "systema'idodin tsarin yau da kullun", ba tare da sanya wata alama ba don shigar da ayyuka ba - ayyuka ko sanannun fakitoci kamar sabar OpenSSH. Idan bayan mun fara zaman farko zamu aiwatar:
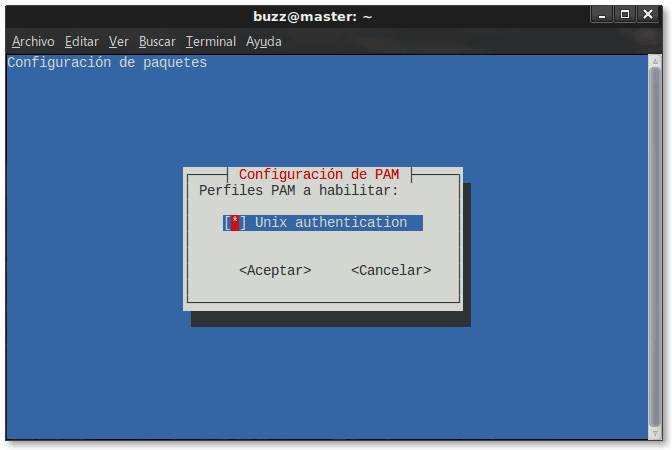
root @ master: ~ # pam-auth-sabuntawa
za mu sami sakamako masu zuwa:
Wanne ya nuna mana cewa Pule Module kawai da ake amfani dashi har zuwa wannan lokacin shine Tantancewar UNIX. Amfani pam-auth-sabuntawa yana ba mu damar daidaita tsarin tabbatar da ainihin tsarin don amfani yayin amfani da Bayanan Bayanai waɗanda aka samar ta Module PAM. Don ƙarin bayani duba mutum pam-auth-sabuntawa.
Kamar yadda bamu riga mun shigar da sabar OpenSSH ba, ba zamu sami tsarin PAM ɗin sa ba a cikin kundin adireshi /da sauransu/pam.d/, wanda zai ƙunshi matakan PAM da bayanan martaba waɗanda aka ɗora har zuwa waɗannan lokacin:
tushen @ maigida: ~ # ls -l /etc/pam.d/ duka 76 -rw-r - r - 1 tushen tushen 235 Sep 30 2014 atd -rw-r - r-- 1 tushen tushen 1208 Apr 6 22:06 na kowa-asusun -rw-r - r-- 1 tushen tushen 1221 Apr 6 22:06 gama-auth -rw-r - r - tushen 1 tushen 1440 Apr 6 22:06 gama-kalmar sirri -rw-r - r - tushen 1 tushen 1156 Apr 6 22:06 gama-zaman -rw-r - r-- tushen 1 tushen 1154 Apr 6 22:06 gama-zaman-ba-hulda ba -rw-r - r- tushen 1 tushen 606 Jun 11 2015 cron -rw-r - r - 1 tushen tushen 384 Nuwamba 19 2014 chfn -rw-r - r-- 1 tushen tushen 92 Nuwamba 19 2014 chpasswd -rw-r - r- tushen 1 tushen 581 Nuwamba 19 2014 chsh -rw-r-- r-- 1 tushen tushen 4756 Nuwamba 19 2014 shiga -rw-r - r-- 1 tushen tushen 92 Nuwamba 19 2014 newusers -rw-r - r - 1 tushen tushen 520 Jan 6 2016 wasu -rw-r- -r-- 1 tushen tushen 92 Nuwamba 19 2014 passwd -rw-r - r-- 1 tushen tushen 143 Mar 29 2015 runuser -rw-r - r - tushen 1 tushen 138 Mar 29 2015 runuser-l -rw -r - r- tushen 1 tushen 2257 Nuwamba 19 2014 su -rw-r - r - tushen 1 tushen 220 Sep 2 2016 systemd-user
Misali, ta amfani da tsarin PAM /etc/pam.d/chfn tsarin yana daidaita sabis ɗin Shadow, yayin ta hanyar /etc/pam.d/kron an saita daemon cron. Don ƙarin koyo kaɗan za mu iya karanta abubuwan da kowane ɗayan waɗannan fayilolin ya ƙunsa wanda yake da darasi sosai. A matsayin samfurin da muke bayarwa ƙasa da abun cikin ƙirar /etc/pam.d/kron:
tushen @ maigida: ~ # less /etc/pam.d/cron # Fayil ɗin sanyi na PAM don cron daemon @ hada da kowa-auth # Sets da loginuid tsari sifa ce da ake bukata pam_loginuid.so # Karanta masu canjin yanayi daga fayilolin tsoho na pam_env, / sauransu / muhalli # da /etc/security/pam_env.conf. zaman da ake buƙata pam_env.so # Bugu da kari, karanta zaman tsarin bayanin yanki da ake bukata pam_env.so envfile = / sauransu / tsoho / wurin zama @ hada da asusu daya @ka hada da zaman gama-gari # Ya saita iyakokin mai amfani, da fatan za a ayyana iyakoki don ayyukan cron # ta hanyar /etc/security/limits.conf da ake bukata pam_limits.so
Tsarin maganganu a cikin kowane fayilolin yana da mahimmanci. Gabaɗaya sharuɗɗa, ba mu ba da shawarar gyara kowane ɗayansu sai dai in mun san abin da muke yi sosai.
Debian tare da tushe OS + OpenSSH
root @ master: ~ # ƙwarewa shigar da aikin-ssh-server
Za a shigar da sabbin kunshin nan: openssh-server {a} budessh-sftp-uwar garken {a} task-ssh-server
Za mu tabbatar da cewa an ƙara modul ɗin PAM kuma an daidaita shi daidai sshd:
tushen @ master: ~ # ls -l /etc/pam.d/sshd -rw-r - r-- 1 tushen asalin 2133 Jul 22 2016 /etc/pam.d/sshd
Idan muna son sanin abubuwan da wannan bayanin ya ƙunsa:
tushen @ maigida: ~ # less /etc/pam.d/sshd
Watau, lokacin da muke kokarin fara zaman nesa daga wata kwamfuta ta amfani ssh, tabbatarwa akan kwamfutar cikin gida ana yin ta ta hanyar PAM module sshd galibi, ba tare da mantawa da sauran izini da bangarorin tsaro waɗanda ke cikin sabis na ssh kamar haka ba.
A wucewa, muna ƙara cewa babban fayil ɗin sanyi na wannan sabis ɗin shine / sauransu / ssh / sshd_config, kuma wannan aƙalla a cikin Debian an shigar dashi ta asali ba tare da barin izinin mai amfani ba tushen. Don ba shi damar, dole ne mu canza fayil ɗin / sauransu / ssh / sshd_config kuma canza layin:
PermitRootLogin ba tare da kalmar wucewa ba
de
PermitRootLogin eh
sannan sake kunnawa da bincika matsayin sabis ta:
root @ master: ~ # systemctl sake farawa ssh tushen @ maigida: ~ # systemctl status ssh
Debian tare da tebur na LXDE
Muna ci gaba da kungiya daya - mun canza suna ko sunan mai masauki by "akwatin Linux»Domin amfani anan gaba - wanda muka gama girka Desktop ɗin LXDE. Mu gudu pam-auth-sabuntawa kuma za mu sami sakamako masu zuwa:
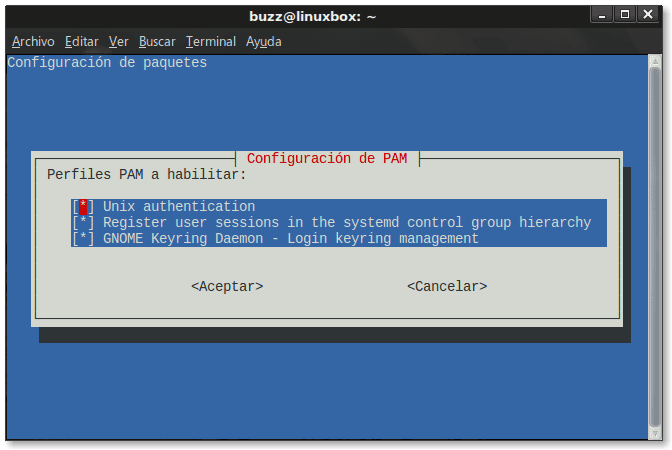
Tsarin ya rigaya ya ba da damar dukkan bayanan martaba -Modules- ya zama dole don ingantaccen inganci yayin girka tebur na LXDE, waɗanda sune masu zuwa:
- UNIX Ingantaccen Module.
- Module da ke rikodin zaman mai amfani a cikin Controlungiyar Kula da Tsarin Mulki na tsarin tsarin.
- GNOME Keyring Daemon Module
- Muna amfani da wannan damar don bayar da shawarar cewa a kowane yanayi, idan aka tambaye mu "bayanan PAM don kunnawa", mun zaɓi zaɓi sai dai in mun san abin da muke yi sosai. Idan muka canza tsarin PAM wanda ake amfani da shi ta atomatik ta Operating System da kansa, zamu iya katse hanyar shiga kwamfutar a sauƙaƙe.
A cikin maganganun da ke sama muna magana ne Tabbatarwa ta Gida ko Tabbatarwa akan kwamfutar gida kamar yadda yake faruwa yayin da muka fara zaman nesa ta hanyar ssh.
Idan muka aiwatar da wata hanya ta Nesa Gaske a cikin ƙungiyar gida Ga masu amfani tare da takardun shaidansu na asali waɗanda aka adana a cikin sabar OpenLDAP ta nesa ko kuma a cikin Littafin Aiki, tsarin zaiyi la'akari da sabon salon tabbatarwa kuma zai ƙara matakan PAM masu mahimmanci.
Babban fayiloli
- / sauransu / passwd: Bayanin Asusun Mai amfani
- / sauransu / inuwa: Amintaccen Bayani na Asusun Mai amfani
- /etc/pam.conf: Fayil wanda yakamata ayi amfani dashi idan kundin adireshi babu /da sauransu/pam.d/
- /da sauransu/pam.d/: Littafin Adireshi inda shirye-shirye da aiyuka suke girka matakan su na PAM
- /etc/pam.d/passwd: Tsarin PAM don passwd.
- /etc/pam.d/rafin-lissafi: Sigogin izini gama gari ga duk sabis
- /etc/pam.d/ba-gari: Sigogin tabbatarwa gama gari ga duk sabis
- /etc/pam.d/kola- wucewa: PAM kayayyaki gama gari ga duk sabis masu alaƙa da kalmomin shiga - kalmomin shiga
- /etc/pam.d/ haduwa-: PAM kayayyaki gama gari ga duk ayyukan da suka shafi zaman mai amfani
- /etc/pam.d/ haduwa-ba tare da aiki ba: PAM kayayyaki gama gari ne ga duk ayyukan da ke da alaƙa da zaman tattaunawa ko kuma waɗanda basa buƙatar sa hannun mai amfani, kamar ayyukan da ake aiwatarwa a farkon da ƙarshen zaman ba tattaunawa.
- / usr / share / doc / passwd /: Littafin bayanai.
Muna bada shawarar karanta shafuka na hannu na passwd y inuwa mediante mutum passwd y inuwar mutum. Hakanan yana da kyau a karanta abubuwan cikin fayilolin asusu na kowa, na kowa-auth, na kowa-passwrod, na gama-gari y zaman-gama-gari.
Akwai matakan PAM
Don samun ra'ayin samfuran PAM da ake dasu a priori A cikin ma'auni na Debian, muna gudana:
buzz @ Linuxbox: ~ $ ƙwarewar binciken libpam
Jerin suna da tsayi kuma kawai zamuyi la'akari da matakan da suka nuna yadda yake da yawa:
libpam-afs-session - PAM module to set up a PAG and obtain AFS tokens libpam-alreadyloggedin - PAM module to skip password authentication for logged users libpam-apparmor - changehat AppArmor library as a PAM module libpam-barada - PAM module to provide two-factor authentication based on HOTP libpam-blue - PAM module for local authenticaction with bluetooth devices libpam-ca - POSIX 1003.1e capabilities (PAM module) libpam-ccreds - Pam module to cache authentication credentials libpam-cgrou - control and monitor control groups (PAM) libpam-chroot - Chroot Pluggable Authentication Module for PAM libpam-ck-connector - ConsoleKit PAM module libpam-cracklib - PAM module to enable cracklib support libpam-dbus - A PAM module which asks the logged in user for confirmation libpam-duo - PAM module for Duo Security two-factor authentication libpam-dynalogin - two-factor HOTP/TOTP authentication - implementation libs libpam-encfs - PAM module to automatically mount encfs filesystems on login libpam-fprintd - PAM module for fingerprint authentication trough fprintd libpam-geo - PAM module checking access of source IPs with a GeoIP database libpam-gnome-keyring - PAM module to unlock the GNOME keyring upon login libpam-google-authenticator - Two-step verification libpam-heimdal - PAM module for Heimdal Kerberos libpam-krb5 - PAM module for MIT Kerberos libpam-krb5-migrate-heimdal - PAM module for migrating to Kerberos libpam-lda - Pluggable Authentication Module for LDA libpam-ldapd - PAM module for using LDAP as an authentication service libpam-mkhomedir - libpam-mklocaluser - Configure PAM to create a local user if it do not exist already libpam-modules - Pluggable Authentication Modules for PAM libpam-modules-bin - Pluggable Authentication Modules for PAM - helper binaries libpam-mount - PAM module that can mount volumes for a user session libpam-mysql - PAM module allowing authentication from a MySQL server libpam-nufw - The authenticating firewall [PAM module] libpam-oath - OATH Toolkit libpam_oath PAM module libpam-ocaml - OCaml bindings for the PAM library (runtime) libpam-openafs-kaserver - AFS distributed filesystem kaserver PAM module libpam-otpw - Use OTPW for PAM authentication libpam-p11 - PAM module for using PKCS#11 smart cards libpam-passwdqc - PAM module for password strength policy enforcement libpam-pgsql - PAM module to authenticate using a PostgreSQL database libpam-pkcs11 - Fully featured PAM module for using PKCS#11 smart cards libpam-pold - PAM module allowing authentication using a OpenPGP smartcard libpam-pwdfile - PAM module allowing authentication via an /etc/passwd-like file libpam-pwquality - PAM module to check password strength libpam-python - Enables PAM modules to be written in Python libpam-python-doc - Documentation for the bindings provided by libpam-python libpam-radius-auth - The PAM RADIUS authentication module libpam-runtime - Runtime support for the PAM library libpam-script - PAM module which allows executing a script libpam-shield - locks out remote attackers trying password guessing libpam-shish - PAM module for Shishi Kerberos v5 libpam-slurm - PAM module to authenticate using the SLURM resource manager libpam-smbpass - pluggable authentication module for Samba libpam-snapper - PAM module for Linux filesystem snapshot management tool libpam-ssh - Authenticate using SSH keys libpam-sshauth - authenticate using an SSH server libpam-sss - Pam module for the System Security Services Daemon libpam-systemd - system and service manager - PAM module libpam-tacplus - PAM module for using TACACS+ as an authentication service libpam-tmpdir - automatic per-user temporary directories libpam-usb - PAM module for authentication with removable USB block devices libpam-winbind - Windows domain authentication integration plugin libpam-yubico - two-factor password and YubiKey OTP PAM module libpam0g - Pluggable Authentication Modules library libpam0g-dev - Development files for PAM libpam4j-java - Java binding for libpam.so libpam4j-java-doc - Documentation for Java binding for libpam.so
Yi naku yanke shawara.
CentOS
Idan yayin aikin shigarwa mun zaɓi zaɓi «Server tare da GUI«, Za mu sami kyakkyawan dandamali don aiwatar da ayyuka daban-daban don Cibiyar Sadarwar SME. Ba kamar Debian ba, CentOS / Red Hat® tana ba da jerin kayan wasan bidiyo da kayan aiki wanda ke sauƙaƙa rayuwa ga Mai Gudanarwa ko Mai Gudanar da Yanar Gizo.
Takardun
Shigar da tsoho, mun same shi a cikin kundin adireshi:
[tushen @ Linuxbox ~] # ls -l /usr/share/doc/pam-1.1.8/ jimlar 256 -rw-r - r--. 1 tushen tushen 2045 Jun 18 2013 Haƙƙin mallaka drwxr-xr-x. 2 tushen tushe 4096 Apr 9 06:28 html -rw-r - r--. 1 tushen tushen 175382 Nuwamba 5 19:13 Linux-PAM_SAG.txt -rw-r - r--. 1 tushen tushe 67948 Jun 18 2013 rfc86.0.txt drwxr-xr-x. 2 tushen tushe 4096 Apr 9 06:28 txts
[tushen @ Linuxbox ~] # ls /usr/share/doc/pam-1.1.8/txts/ README.pam_access README.pam_exec README.pam_lastlog README.pam_namespace README.pam_selinux README.pam_timestamp README.pam_console README.pam_faildelay README.pam_limits README.pam_nologin README.pam_sepermit README.pam_tty_audit README.pam_cracklib README.pam_faillock README.pam_listfile README.pam_permit Fayil. pam_shells README.pam_umask README.pam_chroot README.pam_filter README.pam_localuser README.pam_postgresok README.pam_stress README.pam_unix README.pam_debug README.pam_ftp README.pam_loginuid README.pam_pwhistory README.pam_succeed_if README.pam_userdb README.pam_deny README.pam_group README.pam_mail Fayil .pam_rhosts KA KARANTA
Haka ne, muna kuma kiran ƙungiyar CentOS "linuxbox" kamar yadda yake tare da Debian, wanda zai yi mana sabis don abubuwan nan gaba a kan Cibiyoyin Sadarwar SMB.
CentOS tare da GNOME3 GUI
Lokacin da muka zaɓa yayin shigarwar zaɓi zaɓi «Server tare da GUI«, An shigar da tebur na GNOME3 da sauran abubuwan amfani da shirye-shiryen tushe don haɓaka sabar. A matakin na'ura mai kwakwalwa, don sanin halin tantancewa da muke aiwatarwa:
[tushen @ linuxbox ~] # authconfig-tui
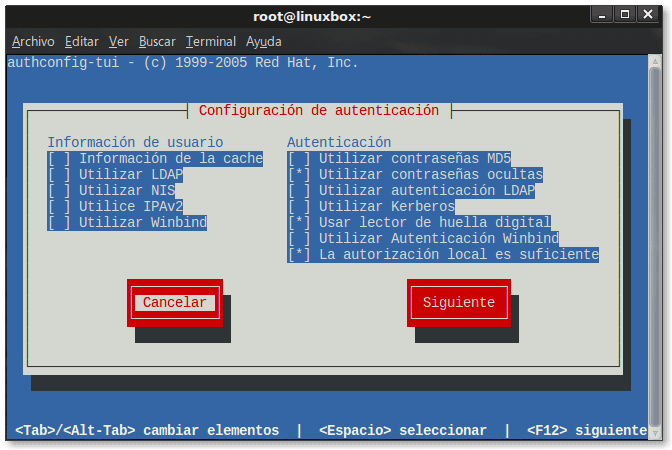
Muna tabbatar da cewa kawai kayan aikin PAM masu mahimmanci don daidaitawar sabar yanzu ana kunna su, har ma da ƙirar don karanta zanan yatsun hannu, tsarin tabbatarwa da muke samu a wasu samfuran Laptops.
CentOS tare da GNOME3 GUI sun shiga cikin Microsoft Active Directory
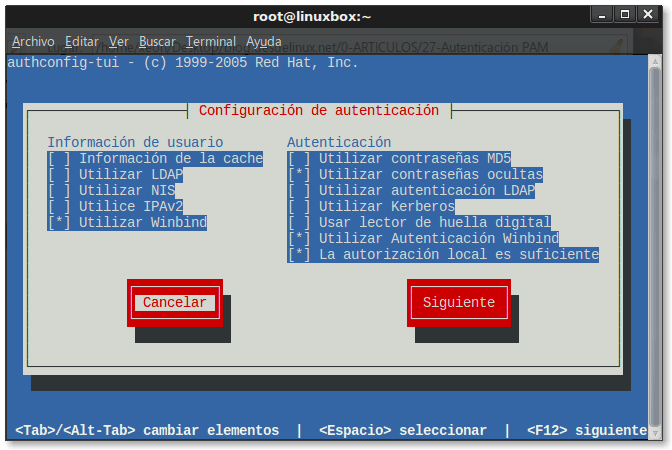
Kamar yadda muke gani, an ƙara wayoyi masu mahimmanci da kunna su -daure- don tabbatarwa kan takaddar aiki, yayin da da gangan muke kashe tsarin don karanta zanan yatsan hannu, saboda ba lallai bane.
A cikin labarin da ke gaba za mu rufe dalla-dalla yadda za a shiga abokin cinikin CentOS 7 zuwa Adireshin Aiki na Microsoft. Muna kawai tsammanin hakan ta hanyar kayan aiki autoconfig-gtk Shigar da kunshin abubuwanda ake bukata, tsarin kirkirar kundayen adireshi na masu amfani da yanki wadanda suke ingantattu a cikin gida, da kuma tsarin hada kanta da abokin huldar zuwa Domain of a Active Directory yana aiki kai tsaye. Wataƙila bayan ƙungiyar, kawai zai zama dole a sake kunna kwamfutar.
Babban fayiloli
Fayilolin da suka danganci Ingantaccen CentOS suna cikin kundin adireshi /da sauransu/pam.d/:
[tushen @ Linuxbox ~] # ls /etc/pam.d/ atd liveinst smartcard-auth-ac authconfig login smtp authconfig-gtk other smtp.postfix authconfig-tui passwd sshd config-util password-auth su crond password-auth-ac sudo kofuna pluto sudo-i chfn polkit-1 su-l chsh postlogin tsarin-auth zanen yatsan-auth postlogin-ac tsarin-auth-ac zanen yatsa-auth-ac ppp system-config-authentication gdm-autologin remote systemd-user gdm-yatsa runuser vlock gdm-ƙaddamar-muhalli runuser-l vmtoolsd gdm-password samba xserver gdm-pin saitin gdm-smartcard smartcard-auth
Akwai matakan PAM
Muna da wuraren ajiya tushe, tsakiya, epel, y updates. A cikinsu zamu sami -among wasu- matakan masu zuwa ta amfani da umarni yum binciken pam-, yum bincike pam_da kuma yum bincika libpam:
nss-pam-ldapd.i686: Nau'in nsswitch ne wanda ke amfani da sabobin adireshin nss-pam-ldapd.x86_64: Nau'in nsswitch ne wanda ke amfani da sabobin adireshin ovirt-wakili-wakili-pam-module.x86_64: PAM module ga oVirt Guest Agent pam -kwallet.x86_64: Tsarin PAM na KWallet pam_afs_session.x86_64: AFS PAG da alamomin AFS akan shiga pam_krb5.i686: A Module Ingantaccen Module don Kerberos 5 pam_krb5.x86_64: A Amincewa da Ingantaccen Module ta hanyar MAPI kan sabar Zarafa pam_oath.x5_86: Tsarin PAM don tabbatar da shigarwa ta shiga don OATH pam_pkcs64.i86: PKCS # 64 / NSS PAM login module pam_pkcs11.x686_11: PKCS # 11 / NSS PAM login modul pam_raus RADIUS Authentication pam_script.x86_64: PAM module don aiwatar da rubutun pam_snapper.i11: PAM module don kiran snapper pam_snapper.x86_64: PAM module don kira snapper pam_ssh.x86_64: PAM module don amfani tare da maɓallan SSH da ssh-agent pam_h 686: Tsarin PAM don tabbatarwa tare da ssh-agent pam_ssh_agent_auth.x86_64: PAM module don tantancewa tare da ssh-agent pam_url.x86_64: PAM module don gaskatawa tare da sabobin HTTP pam_wrapper.x686_86: Kayan aiki ne don gwajin aikace-aikacen PAM da PAM modules pam_yubico. A Module Gasktawa Module ga yubikeys libpamtest-doc.x64_86: The libpamtest API takardun Python-libpamtest.x64_86: A Python wrapper for libpamtest libpamtest.x64_86: Kayan aiki ne don gwajin aikace-aikacen PAM da kuma PAM modules libpamtest-devel.x64_86: A kayan aiki to Aikace-aikacen PAM da kayayyaki PAM
Tsaya
Yana da mahimmanci mu sami mafi ƙarancin sani game da PAM idan muna son fahimtar gaba ɗaya yadda ake aiwatar da Tantancewa duk lokacin da muka shiga kwamfutarmu ta Linux / UNIX. Yana da mahimmanci a san cewa ta hanyar Tantancewar Gida ne kawai za mu iya ba da sabis ga sauran kwamfutoci a cikin ƙaramin hanyar sadarwa ta SME kamar Proxy, Mail, FTP, da sauransu, duk sun mai da hankali ne a kan wata sabar. Duk ayyukan da suka gabata - da ƙari kamar yadda muka gani a baya- suna da tsarin PAM ɗin su.
An nemi majiyar
- Littattafan umarni - shafukan mutane.
- Gasktawa: Shafin Wikipedia a cikin Spanish
- Matakan Inganci
- Red_Hat_Enterprise_Linux-6-ƙaddamarwa_Guide-en-Amurka
Siffar PDF
Zazzage fasalin PDF a nan.
Har sai labarin na gaba!
Mawallafi: Federico A. Valdes Toujague
federicotoujague@gmail.com
https://blog.desdelinux.net/author/fico
Labari dalla dalla kan tabbaci ta amfani da PAM, Na furta ban sani ba dalla-dalla aikin tabbatarwa da adadi mai yawa na amintattu waɗanda zamu iya baku. Wannan babban labarin ne wanda zai baku damar ganin girman Autaddamar da PAM, wanda kuma zai iya samun maƙasudai da yawa a cikin SMEs.
Moreaya daga cikin manyan gudummawar ku, na gode ƙwarai da irin wannan Kyakkyawan Kayan Fico
Na gode da sharhinku, masoyi Luigys. Manufar labarin shine don buɗe zukatan masu karatu game da PAM da matakan sa. Ina tsammanin sakon ya yi nasara.
Ta yadda na sanar da ku cewa maganganun ba sa zuwa wurina ta hanyar wasiƙa.
lol, Na manta rubuta adireshin imel na a cikin sharhin da ya gabata. Wannan shine dalilin da yasa Anonymous ya fito. 😉
Babban labarin, kamar koyaushe.
Mai koyar da Federico sosai, Dole nayi ma'amala da PAM fiye da sau daya kuma ina sha'awar zane, yanada matukar amfani iya saka aiki a cikin ƙugiyoyin da yake bada dama, misali abinda na ƙarshe nayi shine REST API a Python / Flask wanda ya tattara logins da logoff na masu amfani da yankina (salo na babban yaya, don sanin komai), tunda basuyi tunanin inda na sanya kira zuwa curl don sanar da api ba? To haka ne, tare da PAM.
Godiya HO2GI don kimanta gidan.
Mai gudu: Gaishe ku kuma. Kamar koyaushe kuna yin abubuwa masu ban sha'awa. Babu wani abu, wannan sakon yana ɗaya daga cikin waɗanda na sanya kundin adireshi "don buɗe hankali."