Kwesinye isikhathi sidinga ukwazi ukuthi ngabe i-X port ivulekile yini kukhompyutha ekude (noma kuseva), ngaleso sikhathi sinezinketho eziningi noma amathuluzi esizowasebenzisa:
nmap
Isixazululo sokuqala abaningi bethu abacabanga ukuthi: nmap , bheka i-athikili ebizwa ngokuthi: Bona amachweba avulekile nge-NMap nezinyathelo zokuzivikela
Uma ungafuni ukwenza ukuskena okuphelele, kepha umane ufuna ukwazi ukuthi ngabe itheku elithile livulekile ku-X computer / server, kungaba kanjena:
nmap {IP_O_DOMINIO} -p {PUERTO} | grep -i tcp
Isibonelo:
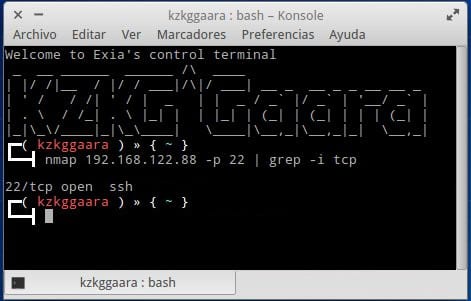
nmap localhost -p 22 | grep -i tcp
Kulungile:
nmap 127.0.0.1 -p 22 | grep -i tcp
Lokhu okwenziwa kulula, kubuza i-IP noma i-Host ukuthi ngabe itheku elinikeziwe livulekile noma cha, bese kuhlunga i-grep futhi kukhombisa kuphela umugqa abafuna ukuwufunda, lowo obatshela ukuthi uvulekile (uvulekile) noma uvaliwe (uvaliwe) lelo chweba:
Yebo ... yebo, i-nmap (ithuluzi lokuhlola inethiwekhi nethuluzi lokuhlola itheku) liyasisebenzela, kepha kusenokunye okuhlukile lapho kufanele uthayiphe okuncane 🙂
nc
nc noma i-netcat, kuyindlela elula kakhulu ukwazi ukuthi itheku livulekile noma cha:
nc -zv {IP_O_DOMINIO} {PUERTO}
Leyo:
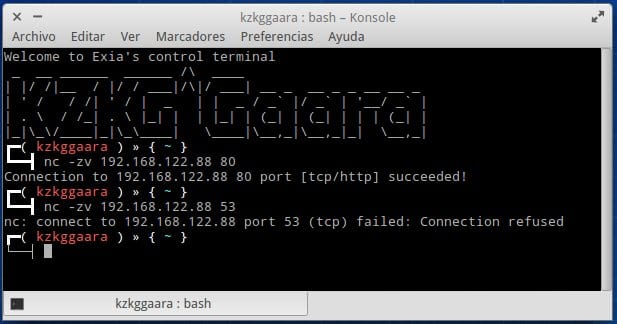
nc -zv 192.168.122.88 80
Nasi isithombe-skrini senza isivivinyo ethekwini esivulekile (80) nesinye kwesinye itheku esingelona (53):
El -zv okwenzayo kulula, ifayela le- v kusivumela ukuthi sibone ukuthi itheku livulekile noma cha, ngenkathi z ivala ukuxhumana ngokushesha lapho itheku lihlolwe, uma singafaki z lapho-ke kuzofanele senze i- Ctrl + C ukuvala i-nc.
Telnet
Lokhu ngukuhluka engikusebenzise isikhashana (ngenxa yokungazi lokhu esesikhulume ngakho), i-telnet yona isisiza kakhulu kunokukwazi nje ukuthi itheku livulekile noma cha.
telnet {IP_O_HOST} {PUERTO}
Nasi isibonelo:
telnet 192.168.122.88 80
Inkinga nge-telnet ukuvala ukuxhumeka. Ngamanye amagama, ngezikhathi ezithile ngeke sikwazi ukuvala isicelo senethiwekhi futhi sizophoqeleka ukuyivala leyo terminal, noma kwenye itheminali yenza i-telnet killall noma into efanayo. Kungakho ngigwema ukusebenzisa i-telnet ngaphandle kwalapho ngidinga ngempela.
Isiphetho!
Noma kunjalo, ngithemba ukuthi lokhu bekukuthakazelisa, uma kukhona owaziyo enye indlela yokwazi ukuthi itheku livulekile noma cha kwenye ikhompyutha, yishiye kumazwana abekiwe.
Phendula ngokucaphuna
Le miyalo izongisiza uma ngixhuma nge-SSH!
Gracias!
Ingabe kukhona uhlelo lokusebenza lokuqhafaza lokwenza okufanayo?
Kahle ungahlala ufake i-zenmap esebenzisa i-nmap ngemuva :)
Uma nge-nmapfe, isikhombimsebenzisi sokuqhafaza esiza nmap.
Nge-netcat ingitshela ukuthi z inketho engavumelekile, ngaphandle kwayo isebenza kahle, futhi ku- $ man nc, nayo ayiveli. Kwavelaphi?
https://blog.desdelinux.net/wp-content/uploads/2013/12/Captura-de-pantalla-de-2013-12-29-011908.png
-zIcacisa ukuthi i-nc kufanele ivele iskene amademoni okulalela, ngaphandle kokuthumela idatha kuwo. Kuyiphutha ukusebenzisa le nketho ngokuhlangana ne-- l inketho.
Nge nc yebo ngiyabona O_O
Futhi ngixhuma kanjani ku-VPS nge-SSL?
Engihlala ngikwenza ukusebenzisa i-nmapfe host-ip ukuze inginike wonke amachweba we-tcp, manje ukubona amachweba we-udp avulekile okufanele uwasebenzise:
nmap -sU umphathi-ip
Ngisebenzise futhi i-telnet ngaphezu kwanoma yini enye emafasiteleni uma ngingenayo i-nmap efakiwe, okuhlukile kwe-netcat akungikhangi ...
Phendula ngokucaphuna
Ngingathanda ukwazi okwengeziwe ngalokhu, ngithemba ukuthi ungangisekela nginolwazi oluyisisekelo kakhulu futhi ngithanda ukwazi kabanzi ukusebenzisa lolu hlobo lolwazi emsebenzini wami.
Ngisanda kuthola ukuthi anginawo amachweba engifuna ukuthi avulwe, manje kuzofanele ngicwaninge ukuthi ngiwavula kanjani ukuze ngenze engikudingayo. Ngiyabonga ngomnikelo, ungisize kakhulu.
I-athikili ethakazelisa kakhulu! Ngaphandle kwe-netcat, iyasebenza nakwi-vmware ESXi:
http://www.sysadmit.com/2015/09/prueba-de-conexion-un-puerto-desde-VMWare-Windows-Linux.html
Sudo uthole ukufaka nmap
nam 192.168.0.19 -p 21 | grep -i tcp
ikhaya lomsebenzisi wendawo srv / ftp
qala kabusha ngensizakalo yesudo vsftpd qala kabusha
write_enable = YEBO ukuze abasebenzisi bendawo bakwazi ukulayisha amafayela.
Ukubopha umuntu ongaziwa ekhaya lakhe
chroot_local_user = yebo
chroot_list_enable = yebo
allow_writreable_chroot = yebo
no_annon_password = cha ukuze umuntu ongaziwa akwazi ukudlulisa inhlonipho
deni_email_enable = yebo
banile_email_file = / njll / vsftpd.banned_emails Ukuphika umuntu ongaziwa nge-imeyili.
____—————————————————————–
umsebenzisi wamakheji ngaphansi kwalabo abasohlwini
chroot_local_user = yebo
chroot_lits_enable = yebo
chroot_list_file = / njll / vsftpd.chroot_list.
Ukufaka abasebenzisi igama le-sudo adduser
khubaza indawo locale_enable = cha
zivalele ngokwenu
engaziwa ku-srv / ftp
emagcekeni ekhaya lakho
Kuhle kakhulu! Uma singenayo i-nmap, i-telnet noma i-netcat, singasebenzisa ikati kanye nesiqondisi se-proc:
ikati </ dev / tcp / HOST / PORT
Isibonelo: http://www.sysadmit.com/2016/03/linux-cat-y-proc-prueba-de-conexion.html
Ngiyabonga, incazelo enhle kakhulu