
Masu bincike daga Jami'ar Masaryk sun bayyana bayanai importante game da rauni a iri-iri iAiwatar da ECDSA / EdDSA sa hannu na zamani na algorithm, hakan yana ba da damar dawo da ƙimar maɓallin keɓaɓɓe bisa laákari da bayanan kwararar bayanai kan raunin mutum wanda ya bayyana yayin amfani da hanyoyin nazari ta hanyoyin mutum na uku. An laƙantar da yanayin larurar Minerva.
Ayyukan da suka fi shahara abin ya shafa hanyar kai harin kai tsaye sune BuɗeJDK, OracleJDK (CVE-2019-2894) da ɗakin karatu Labaran (CVE-2019-13627) ana amfani dashi a cikin GnuPG. Matsalolin sune kuma mai saukin kai ga dakunan karatu MatrixSSL, Crypto ++, wolfCrypt, elliptical, jsrsasign, Python-ECDSA, ruby_ecdsa, fastecdsa da kuma wasu katunan wayoyi Athena IDProtect, TecSec Armored Card, SafeNet eToken 4300, Inganci S / A IDflex V.
Baya ga raunin da aka ambata a wannan lokacin bai shafe su ba OpenSSL, Botan, mbedTLS, da BoringSSL. Mozilla NSS, LibreSSL, Nettle, BearSSL, cryptlib, OpenSSL a cikin yanayin FIPS. Microsoft .NET crypto, Linux kernel libkcapi, Sodium, da GnuTLS har yanzu ba a gwada su ba.
Mun sami aiwatarwar da ta rasa ɗan tsayin sikelin yayin yaduwar sikelin a cikin ECC. Wannan zubin na iya zama kamar ƙarami ne tunda ɗan tsayin yana da ƙananan bayanai kaɗan da ke cikin sikelin. Koyaya, a game da sa hannun ECDSA / EdDSA ƙarni, tace bazuwar tsakaitaccen tsayi ya wadatar don dawo da maɓallin keɓaɓɓen da aka yi amfani da shi bayan lura da sa hannun fewan ɗari zuwa fewan dubu cikin saƙonnin da aka sani, saboda aikace-aikacen wasu dabaru .
Mun yi imanin cewa duk katunan da ke sama suna da tasiri saboda suna raba wani abu na ECDSA (FIPS 214 module), wanda aka bayyana a matsayin Athena OS2 ECDSA755 Component a Inside Secure AT90SC A1.0 (Firmware). Mun gwada raunin kawai akan katin IDProtect na Athena tare da bayanan CPLC da ATR
Matsalar ta samo asali ne ta hanyar ikon tantance ƙimar bitar mutum yayin rubanyawa ta hanyar sikeli yayin kasuwancin ECC. Hanyoyin kai tsaye, kamar kimanta jinkiri wajen yin lissafi, ana amfani dasu don cire bayanai daga ragowa.
Hare-hare yana buƙatar damar shiga mara gida ba tare da gata ba wanda aka sanya sa hannu na dijital (ba a cire harin nesa ba, amma yana da matukar rikitarwa kuma yana buƙatar adadi mai yawa don bincike, sabili da haka ana iya ɗaukar sawura).
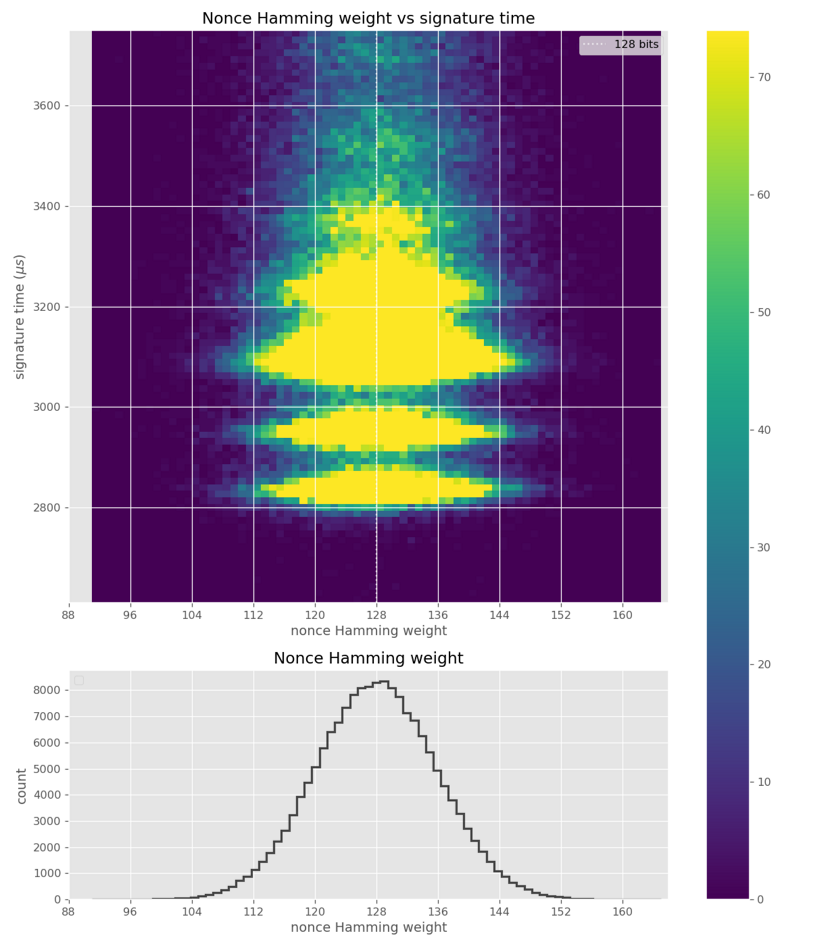
Duk da karancin zubewar, ga ECDSA ma'anar wasu 'yan ragowa tare da bayani game da farawa (ba a samu ba) ya isa aiwatar da hari don sake dawo da cikakken mabuɗin masu zaman kansa.
A cewar marubutan hanyar, don samun nasarar maɓallin kewayawa, nazarin ɗari-ɗari zuwa dubun-dubatar sa hannu na dijital ya isa ga sakonnin da maharin ya sani. Misali, don tantance maɓallin keɓaɓɓe da aka yi amfani da shi a cikin Attana IDProtect smart card bisa layin Inside Secure AT90SC, ta amfani da lanƙwasa mai lanƙwasa secp256r1, an bincika sa hannun dubu 11 na dijital. Jimlar lokacin kai harin mintina 30 ne.
Lambar mu ta kai hari da hujja game da ra'ayi shine hanyar Brumley & Tuveri.
An riga an gyara matsalar a cikin libgcrypt 1.8.5 da wolfCrypt 4.1.0, sauran ayyukan ba su samar da sabuntawa ba tukuna. Haka kuma yana yiwuwa a gano alamar yanayin rauni a cikin kunshin libgcrypt a cikin rarrabawa akan waɗannan shafukan: Debian, Ubuntu, RHEL, Fedora, budeSUSE / SUSE, FreeBSD, Kibiya.
Masu binciken sun kuma gwada wasu katunan da dakunan karatu, wanda wadannan ba su da rauni:
- BuɗeSSL 1.1.1d
- Bouncy Castle 1.58
- BoringSSL 974f4dddf
- libtom ya ɓoye 1.18.2
- Tafiya 2.11.0
- Microsoft CNG
- mbTLS 2.16.0
- Intel IPP-Crypto
Cards
- Bayani: ACS ACOSJ 40K
- Farashin A22CR
- G&D SmartCafe 6.0
- G&D SmartCafe 7.0
- Infineon CJTOP 80K INF SLJ 52GLA080AL M8.4
- Infineon SLE78 Universal JCard
- NXP JCOP31 v2.4.1
- Bayanin NXP JCOP CJ2A081
- NXP JCOP v2.4.2 R2
- NXP JCOP v2.4.2 R3
- SIMOME TaiSYS Vault
Idan kana son karin bayani game da harin da aka yi amfani da shi da kuma gano abubuwan da ke faruwa, za ka iya yin hakan a cikin bin hanyar haɗi. Kayan aikin da aka yi amfani da su don maimaita harin suna nan don saukarwa.