Lilu It is a new ransomware that is also known by the name of Lilocked and that aims to infect Linux-based servers, something that he has achieved successfully. The ransomware began infecting servers in mid-July, but attacks have become more frequent in the last two weeks. Much more frequent.
The first known case of the Lilocked ransomware came to light when a user uploaded a note to ID Ransomware, a website created to identify the name of this type of malicious software. Your target is servers and get root access in them. The mechanism it uses to get that access is still unknown. And the bad news is that now, less than two months later, Lilu has been known to have infected thousands of Linux-based servers.
Lilu attacks Linux servers to get root access
What Lilocked does, something we can guess from its name, is block. To be more specific, once the server has been successfully attacked, the files are locked with a .lilocked extension. In other words, the malicious software modifies the files, changes the extension to .lilocked, and they become totally unusable… unless you pay to restore them.
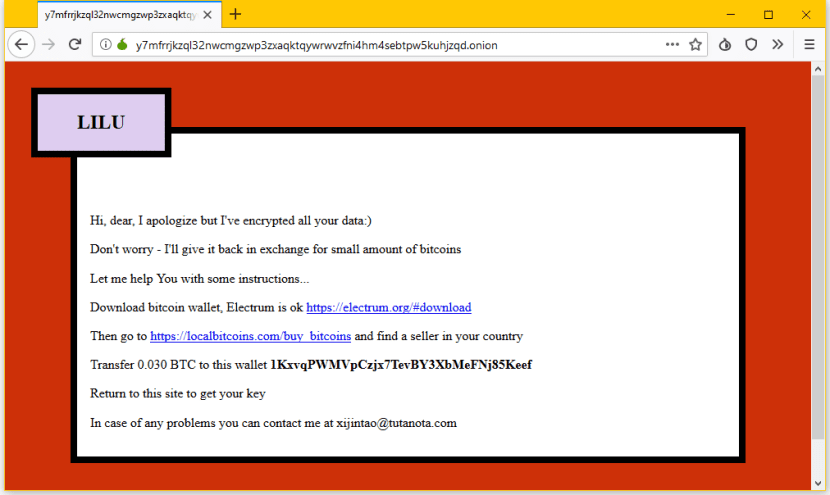
In addition to changing the file extension, a note also appears that says (in English):
«I have encrypted all your sensitive data !!! It's strong encryption, so don't be naive trying to restore it;) »
Once the link of the note is clicked, it is redirected to a page on the dark web that asks to enter the key that is in the note. When such a key is added, 0.03 bitcoins (€ 294.52) are requested to be entered in the Electrum wallet so that the encryption of the files is removed.
Does not affect system files
Lilu does not affect system files, but others such as HTML, SHTML, JS, CSS, PHP, INI and other image formats can be blocked. This means that the system will work normallyIt's just that the locked files won't be accessible. The "hijacking" is somewhat reminiscent of the "Police virus", with the difference that it did prevent the use of the operating system.
Security researcher Benkow says that Lilock has affected about 6.700 servers,Most of them are cached in Google search results, but there could be more affected ones that are not indexed by the famous search engine. At the time of writing this article and as we have explained, the mechanism that Lilu uses to work is unknown, so there is no patch to apply. It is recommended that we use strong passwords and that we always keep the software well updated.
Hello! It would be helpful to publicize the precautions to take to avoid infection. I read in a 2015 article that the infection mechanism was unclear but that it was probably a brute force attack. However, I consider, given the number of infected servers (6700), that it is unlikely that so many administrators will be so careless as to put short, easy-to-break passwords. Regards.
It is really doubtful that it can be said that linux is infected with a virus and, in passing, in java, for this virus to enter the server they must first cross the router's firewall and then that of the linux server, then as ose "auto-executes" so that it asks root access?
even assuming it achieves the miracle of running, what do you do to gain root access? because even installing in non-root mode it is very difficult since it would have to be written in crontab in root mode, that is, you must know the root key that to obtain it you would need an application such as a "keyloger" that "captures" the keystrokes, but there is still the question how would that application be installed?
Forget to mention that an application cannot be installed "within another application" unless it comes from a ready-made download website, however by the time it reaches a pc it will have been updated several times, which would make the vulnerability for which was written is no longer effective.
In the case of windows, it is very different since an html file with java scrypt or with php can create an unusual .bat file of the same scrypt type and install it on the machine since it is not required to be root for this type of objective