
|
At this point in the game, you probably already have your smartphone, which surely comes with Bluetooth. Thanks to him and a little program called BlueProximity (that you have to install on your computer), you will be able lock / unlock your computer al zoom in or out. |
In the interconnected world we live in, if there is one gadget that we never detach from, it is the mobile phone. For that reason, thanks to BlueProximity we will be able to block our PC when we move away, until we return with the mobile, it is still blocked. Of course we can unlock it manually, just by entering the password.
Installing it is very simple since it is found in almost all repositories Officials of the most popular distros.
sudo apt-get install blueproximity
Configuration
Phone Settings
First, you have to link your computer and mobile phone. Once the mobile is linked, it will not ask for a password when we want to reconnect the computer and the phone. There is still the possibility that your mobile phone will ask you to accept the connection which is an additional layer of security, apart from the pairing mechanism. The phone should have an option to disable this question for everyone, or even a special device. Disabling this question does not disable BlueProximity although it is quite useless since you always have to do something on your phone when you return to your computer.
Phone connection
After setting up the phone you can go ahead and set up BlueProximity. After the exit the first thing you should see is the configuration window.
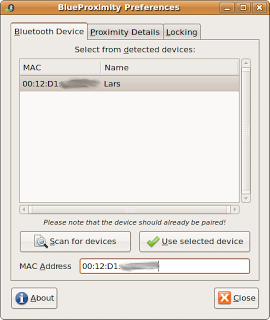
In the first tab we can configure our phone in BlueProximity, for this we will do an analysis and once the phone address is found we will select.
To find out the address, you have to set your phone to Bluetooth visible mode. It may be the standard configuration, but you never know… Now click the Scan for Devices button. The scanner will take about 10 seconds. You should find the device after those seconds in the list, perhaps among the other bluetooth devices that it detects around you.
Setup distance detection
Now BlueProximity should start working, but there might be more tuning parameters required. This way you can change the detection parameters and test them. You will notice how the icon changes if you play with the values.
In the second tab select distance and lock / unlock duration.
Once these requirements are met, the corresponding action (lock or unlock) will be activated.
Action lock settings
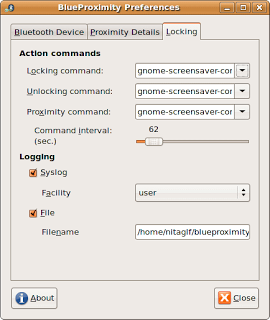
Go to the third tab called locking to see the following screen:
The upper section refers to the commands that BlueProximity will execute for each configured event. The default is the command to lock and unlock the screen using the GNOME desktop screen saver. If you are a KDE user you have to click on the down arrow and select the entry xscreensaver. Note that this will only work with the built-in KDE version of xscreensaver. The original xscreensaver does not include an unlock command.
The proximity command is a command that is executed every certain interval and is performed while the user is in range (the screen is unlocked). That way you can, for example, prevent the screensaver from activating while you are nearby. This is the standard configuration.
The lower section deals with state changes. The syslog entry allows you to generate a syslog message on each state change coming from the logfacility that you have configured and the log level prior warning. You can also configure it exclusively for recording in a certain file.
You can also turn off the monitor at the time of blocking and thus you will save electricity when you are away from your computer; of course it will light up when you come back. The following commands can be used to turn the monitor off and on.
Lock command + shutdown:
gnome-screensaver-command -l && xset dpms force off
Unlock + power command:
xset dpms force on && gnome-screensaver-command -d
Source: subinet.es
not counting what the battery sucks to have the bluetooth on always
Very good. Cheers,
You have to be lazy to get away and not press a combination of keys, and if you run out of battery and get used to your computer crashing when you walk away? and the funny thing that grabs your cell phone when you are distracted and makes your computer crash ... obviously there is always the option to unlock it with the password, but there would be several geeks having fun out there: p, not cool, not cool
That's right ... it has its downsides, that's undeniable.
However, it is one more alternative ...
Cheers! Paul.
Maybe you're lucky and nobody notices ...