Briar is an excellent messaging app that syncs messages across the Tor network, protecting users and their relationships from surveillance.
Instant messaging applications exist many, but there are few that actually offer the user "decent" data protection as far as it is concerned. Given this demand by a large number of users, various applications have become popular, apart from the commercial ones, which still leaves a lot to think about whether the user's information is actually protected.
It is because of that Today we are going to talk here on the blog about, Briar, a messaging app designed for activists, journalists and anyone who needs a way secure, easy and robust to communicate.
Country/region specific messaging apps are working fine. Line is the most popular messaging platform in Japan, KakaoTalk in South Korea and WeChat in China, although the latter is also due to the ban on Facebook and WhatsApp in China. In Eastern Europe and Africa, Viber competes with WhatsApp for the most downloads and usage.
Messaging apps that offer end-to-end encryption (E2EE) can claim to protect their users by claiming that they threw away the key, metaphorically and literally, and that they cannot undo what was encrypted during transmission. However, both BRIAR and Telegram claim to protect all users.
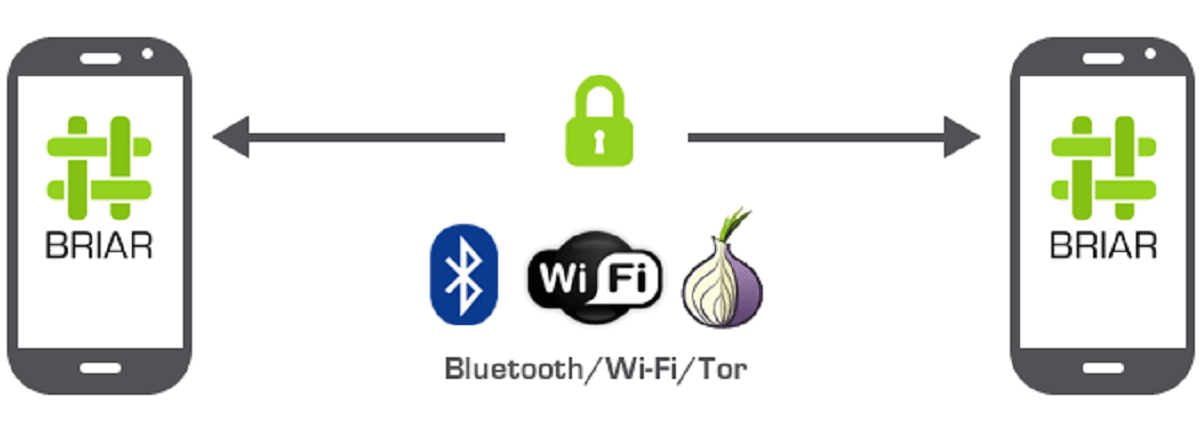
Unlike traditional messaging apps, Briar does not depend on a central server: messages are synced directly between users' devices. In the event of an internet outage, Briar can sync via Bluetooth or Wi-Fi, keeping information flowing in a crisis. If the Internet is active, Briar can sync across the Tor network, protecting users and their relationships from surveillance.
Both Telegram and Signal were founded on strong pro-encryption ideals and regularly attack Facebook for its messaging business model. Briar uses direct and encrypted connections between users to avoid surveillance and censorship. Traditional messaging software is based on central servers and exposes messages and relationships to surveillance.
briar can share data over Wi-Fi, Bluetooth, and the Internet, in addition to providing private messages, public forums and blogs that are protected against the following surveillance and censorship threats:
Of the Briar's standout features:
- Metadata monitoring: Briar uses the Tor network to prevent listeners from knowing which users are talking to each other. Each user's contact list is encrypted and stored on their own device;
- Content Monitoring: all communications between devices are end-to-end encrypted, protecting the content from eavesdropping or tampering;
- Content filtering: Briar's end-to-end encryption prevents keyword filtering, and due to its decentralized design, there are no servers to block;
- Removal Orders: each user who subscribes to a forum saves a copy of its content, so there is no single point where a post can be deleted;
- Denial of service attacks: Briar forums do not have a central server to attack, and all subscribers have access to the content even if they are offline;
- Internet interruptions: Briar can work over Bluetooth and Wi-Fi to keep information transferring during interruptions.
The Briar development team intends to use its data synchronization capabilities to support secure distributed applications, including collaborative document editing.
“Our goal is to empower people in any country to create safe spaces where they can discuss any issue, plan events, and organize social movements,” he says.
Finally, it is worth mentioning that the main disadvantage of Briar is that it requires a constant connection to Tor and uses a persistent notification to get the job done. Unsurprisingly, this is not good for battery life. So unless you need the tightest security, you're probably better off using Signal or a similar app.
You can download the application at the following link.