If you want to create a VPN server, let me tell you that there is an excellent option from which you can support yourself in order to achieve your mission and that is that the project Firezone is developing a VPN server pTo organize access to hosts on an internal network isolated from user devices located on external networks.
The project aims to achieve a high level of security and simplify the VPN implementation process.
About Firezone
The project is being developed by a Cisco Security Automation Engineer, who tried to create a solution that automates work with host configuration and eliminates the hassle they had to face when organizing secure access to VPCs in the cloud.
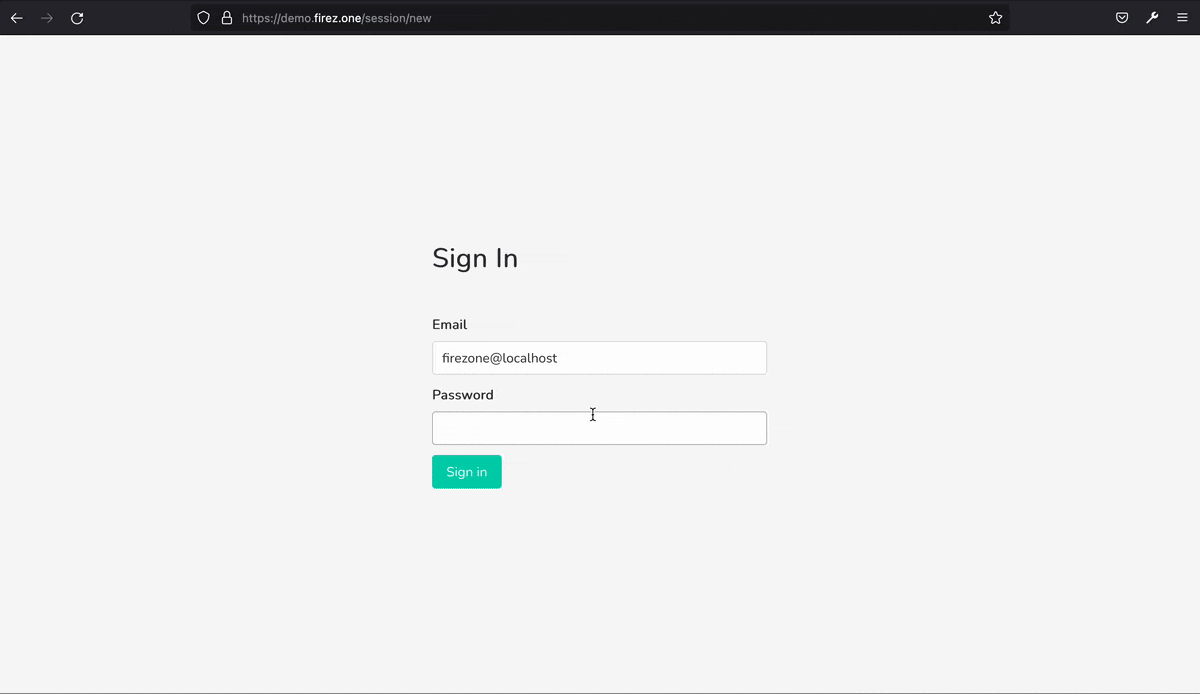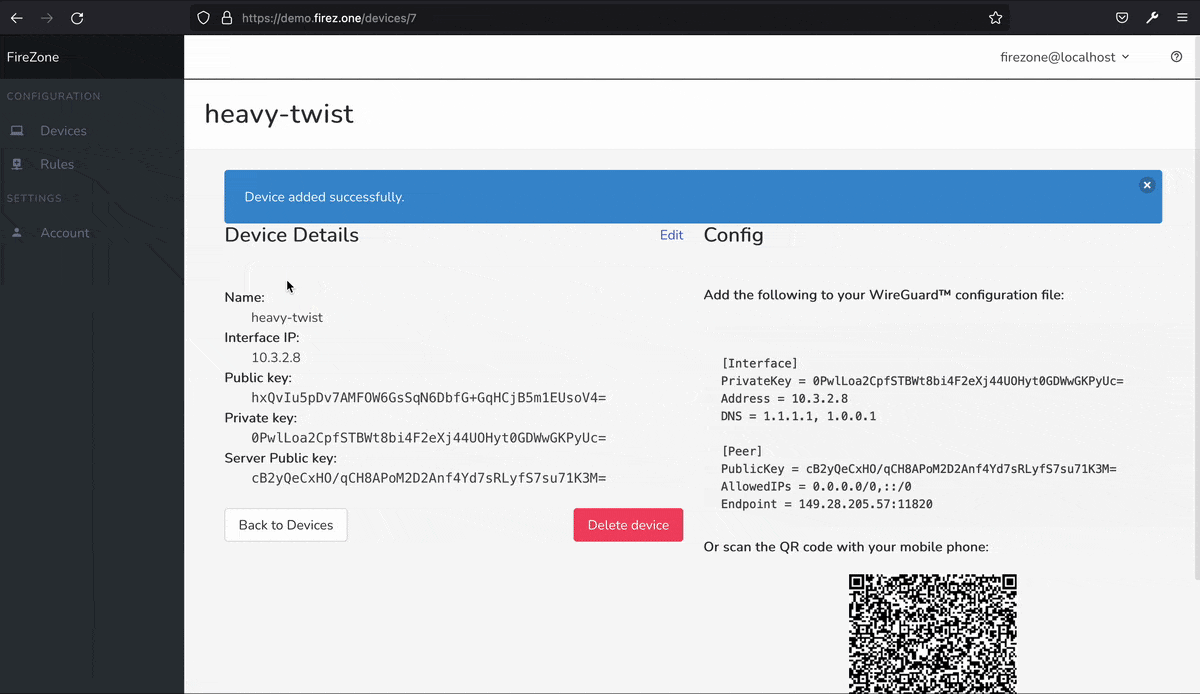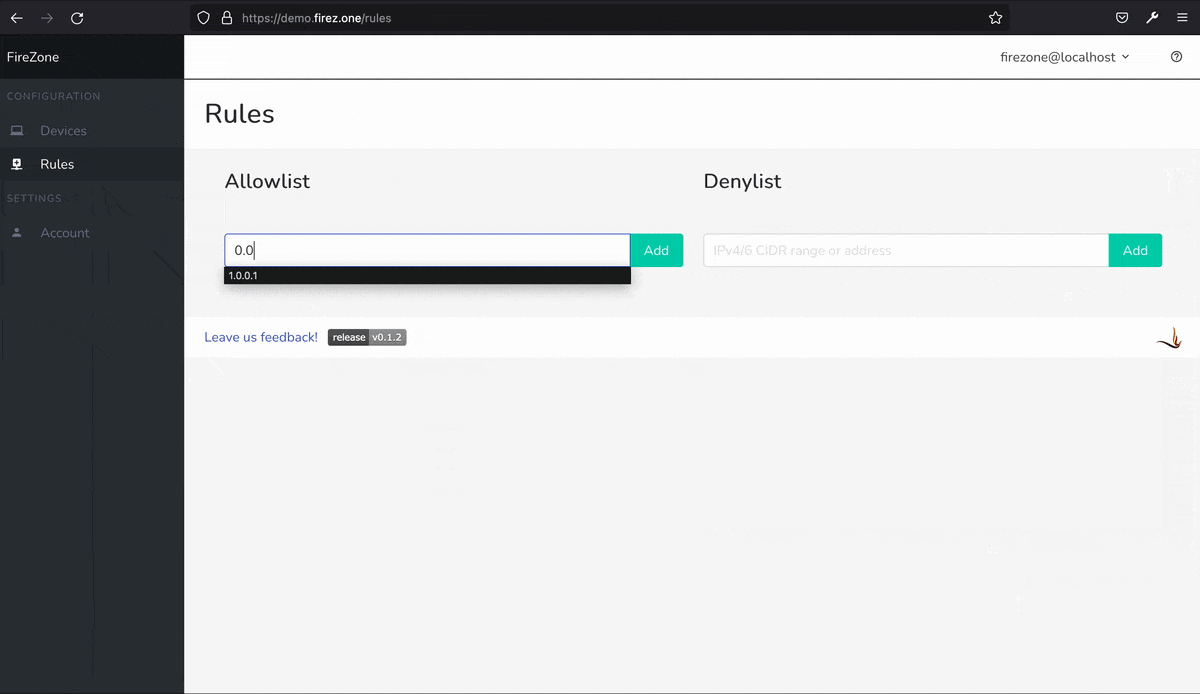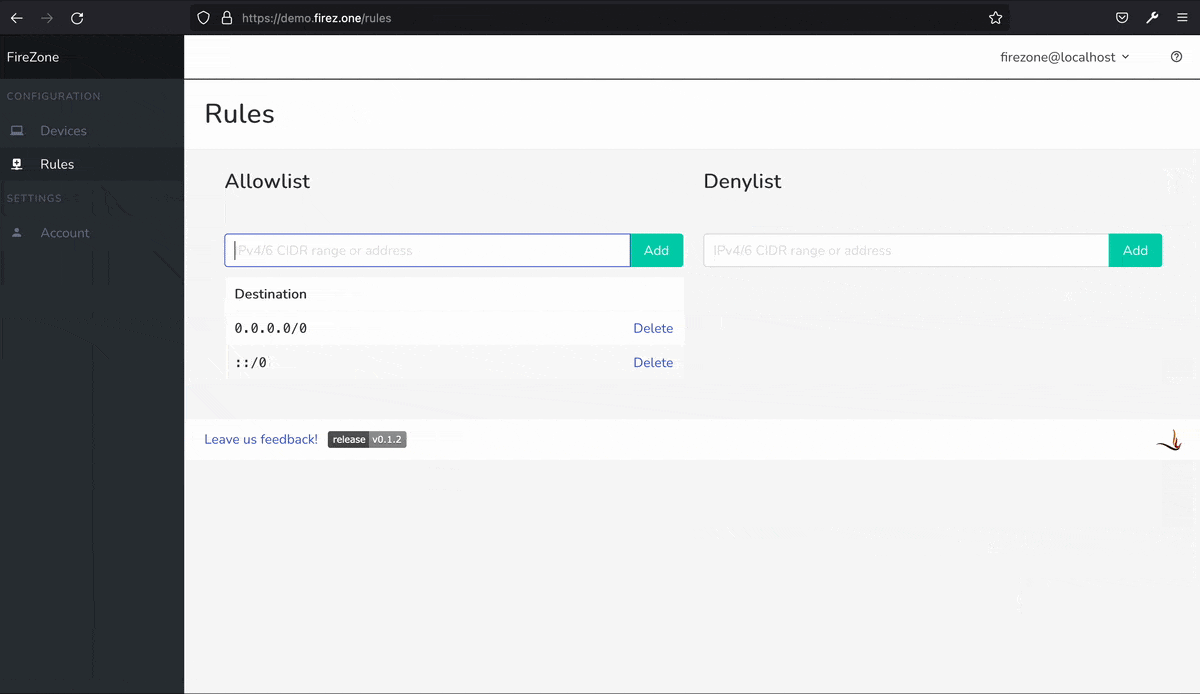
Fire zone acts as an interface to both the WireGuard kernel module as for the netfilter kernel subsystem. Create a WireGuard interface (called wg-firezone by default) and a netfilter table and add the appropriate routes to the routing table. Other programs that modify the Linux routing table or the netfilter firewall can interfere with the operation of Firezone.
You can think of Firezone as an open source counterpart to OpenVPN Access Server, built on top of WireGuard instead of OpenVPN.
WireGuard is used to organize communication channels in Firezone. Firezone also has a built-in firewall functionality that uses nftables.
In its current form, the firewall is limited by blocking outbound traffic to specific hosts or subnets In internal or external networks, this is due to the fact that Firezone is a beta software, so for the moment its use is only recommended by limiting the access of the network to the web user interface to avoid exposing it to the public Internet.
Firezone requires a valid SSL certificate and a matching DNS record to run in production, which can be generated and managed by the Let's Encrypt tool to generate a free SSL certificate.
On the part of administration, it is mentioned that this is done through the web interface or in command line mode using the firezone-ctl utility. The web interface is built on the basis of Admin One Bulma.
Currently, all Firezone components run on the same server, But the project is initially developed with an eye on modularity, and in the future it is planned to add the ability to distribute components for the web interface, VPN and firewall on different hosts.
The plans also mention the integration of a DNS-based ad blocker, support for host and subnet block lists, the ability to authenticate via LDAP / SSO, and additional user management capabilities.
Of the mentioned features of Firezone:
- Fast: use WireGuard to be 3-4 times faster than OpenVPN.
- No dependencies: all dependencies are grouped thanks to Chef Omnibus.
- Simple: takes a few minutes to set up. Manage through a simple CLI API.
- Safe: works without privileges. HTTPS applied.
- Encrypted cookies.
- Firewall included - Uses Linux nftables to block unwanted outbound traffic.
For installation, rpm and deb packages are offered for different versions of CentOS, Fedora, Ubuntu and Debian, the installation of which does not require external dependencies, since all the necessary dependencies are already included using the Chef Omnibus toolkit.
To work, you only need a Linux distribution that has a Linux kernel no earlier than 4.19 and a kernel module compiled with WireGuard VPN. According to the author, starting and configuring a VPN server can be done in just a few minutes. The components of the web interface run under a non-privileged user and access is only possible over HTTPS.
Firezone consists of a single distributable Linux package that you can install and manage. The project code is written in Elixir and Ruby, and is distributed under the Apache 2.0 license.
Finally if you are interested in knowing more about it or you want to follow the installation instructions, you can do it from the following link.