Less than a month ago we asked your opinion regarding HTTPS in DesdeLinux. Through peterczech For more than a week the blog has HTTPS enabled, that is, they can access https://blog.desdelinux.net and the server will respond.
The reasons for thinking about HTTPS we talked about before, basically are:
- Google will consider HTTPS sites for SEO in the future.
- HTTPS is information encryption, which translates into greater security for your information and ours.
As you can see, it is a point in our favor in every way to properly implement HTTPS on our sites.
Regarding SEO and GoogleAlthough it is true that Google will NOT immediately associate your PageRank with HTTPS, it will be something that in the future will have a direct relationship, come on, that will influence our SEO. Right now we can use tools to check our SEO, I'm even testing some SEO positioning applications available that may have a version for Android, well, in the future the implementation or not of HTTPS will be one of the parameters to be measured.
Regarding information security, it is evident that the logins (user and password) circulating in plain text on the network is not the most advisable, anyone with two fingers of forehead could capture a password and well ... do what your imagination allows 🙂
HTTPS on DesdeLinux
As I said before, if they agree to https://blog.desdelinux.net Our server will respond to them, their browser will show them that the site is not trustworthy and such… because we have not paid for a company to sign our certificate as "valid". They just have to click on Download / Get Certificate and then on Approve it, that will be enough for them to access the site.
Thanks to peterczech We have a certificate generated by ourselves, because whoever writes them knows about servers and others but… hehe, I had never had to work with SSL, so I recommend that you download and import our CA in your browser.
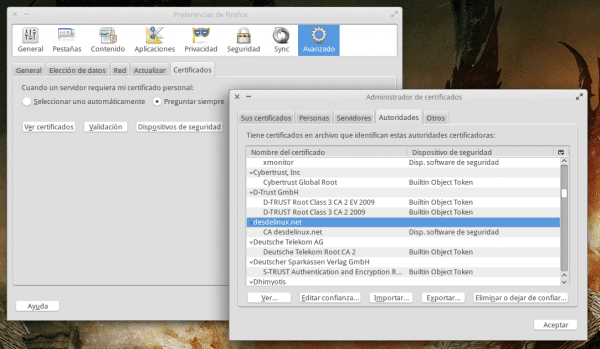
To add it here the steps:
- Open Firefox
- Ir a Preferences o Configuration
- Let's go to the section Advanced, specifically the tab Certificates
- We click on the button Import and we look for the file that we just downloaded, and that's it.
Here is a screenshot:
Once the certificate is added to the browser, we will be able to access the blog by HTTPS without the warning sign appearing 😉
And now, what's next?
For now we are testing HTTPS, that the blog is displayed well there and checking that everything is fine. So, any error ... please report it 😉
Then something we plan to do is that the WP-Admin will be mandatory to use it through HTTPS, because the first thing that we must protect is the user & password of all of us, for this it is enough to add a line in the wp-config.php of WordPress.
This will (possibly) be the next step.
Well nothing, I'll leave it there for the moment. I await feedback from you to see if everything works as it is supposed to funcione
PD: The blog continues to work over HTTP and HTTPS, don't worry 😉

Testing implementation, meanwhile best of luck so that nothing falls.
1) to do it in chrome, go to settings, show advanced options, manage certificates, issuing authorities tab, import, select the certificate and that's it.
2) I think he reminds me of the wordpress login is failing because after logging in (and entering the panel), I enter the blog and log out.
the login is done. do not worry.
In my case, I am using chromium, is it asking me for the password that was used to encrypt the certificate ??? something very strange that asks me that.
In the case of firefox, it was imported successfully.
Some help??
Hi NauTiluS, I just tested it on Chromium 36 and the latest Chrome 37 and there is no problem.
It is in the issuing authorities tab, not in the one of your certificates
I have the 37 and this is where it gave me that problem
I forgot, I give you a video that I made with the steps I take and the commented failure.
I'll give you the video here, with the steps taken.
https://vimeo.com/105256304
ps: please a moderator to delete the previous comment, since the enter key was pressed by mistake.
The certificate must be imported in the tab with the name Authorities and not in your certificates as you do in your video .. Click on the tab with the name Authorities :).
Ready petercheco.
It is the first time that I do it in chromium:!
HTTPS in a blog is absurd, most people only access blogs to read them and for a login access, there is nothing of value other than a username, a password and the email. On the other hand, doing it because Google stipulates it makes me quite scared, since then we already give the reason that Google is the government of the Internet and whoever does not go through its hoop is left behind. Likewise, the change in Google's algorithm is being misinterpreted since it does not say that all websites must be HTTPS but if they will give priority to content that requires to be encrypted against content that is not (For example, markets or websites where data is handled sensitive such as credit cards or personal information). This as a security system is very good and I agree that Google does that, but now we do not have to spend $ 30 a year per certificate and domain for a simple public information website.
Now, I hope you keep in mind that a website with a self-signed certificate IS penalized by Google, since there will be alerts that the website is dangerous and not everyone will bother to add the certificate in their browser.
A greeting.
Interesting comment. I personally do not support https, and you have given me good reason to reaffirm my position.
…. why does Google stipulate it?, ... little by little the google monopoly is trapping GNU / Linux in its mercantilist trap, and its users will be left at the mercy of its dark marketing interests. They do not realize that this monopoly Google wants to put in the privacy of people who even ask for a telephone number for what purpose? … To track and know everything you do. Now you will no longer be able to comment freely in these forums… .if you are not registered on this page? … .And everything why?… Because that's the way google sends.
I think we are exaggerating too much ...
that it will not be possible to comment freely on DesdeLinux? …that you cannot comment if you are not registered? …this has nothing, I repeat, NOTHING to do with Google or any other company, they would be measures that, if applied (although I see no reason to do so), would be our decision, not others'.
HTTPS is not owned by Google far from it, it is simply HTTP but the information travels encrypted (protected) through the network, nothing more.
It is not putting HTTPS to put it, I still think that the login data travels in plain text is a BAD, VERY BAD idea.
That a hacker through an MITM attack knows that I am reading a blog that he can access himself using the same address from which I access is what worries me the least, that is why I reaffirm that not all websites must have HTTPS necessarily and I believe that Google's position is to prioritize encrypted content whose sensitive data traffic is higher than public visibility traffic.
I do not see it well now having to pay an X a year for a certificate and for those who manage a domain pass, but those of us who have more than 3 registered domains is an expense that we cannot afford in any way.
This is not entirely true, especially in cases where users are "innocent" enough to use the same password in their e-mail. 🙂
Hug! Paul.
I share your point of view @usemoslinux, many "innocent" users have the bad habit of using the same username and password for almost everything they do on the Internet without understanding the risk that this implies for their privacy.
And speaking about the privacy issue, https is not only implemented for security, but also to give the user the ability to have higher levels of privacy and that is a positive from any point of view, without having the need to enter into other rants for that issue.
I agree with both :).
Using HTTPS is always positive but it is not to waste money either. Only implement it where it is really needed. For users to use the same password on all sites is like making 50 copies of your house key and throwing them out on the street, until someone knows where you live, a misfortune occurs and you have to change your bowler hat, but I don't have a locksmith who knows I do that and gives me a copy. If people are not careful with their sensitive data, why should we help them if they are not taking seriously something that should be treated with common sense. The latter sounds very cruel but at least I have learned through misfortunes and even with a lot of information about how we should treat our data, most of them do not take seriously how they should treat the data.
Spending, in my case, 30 euros more a year to protect people from something that they should not do out of common sense, is not profitable for me.
The certificate is incorrectly installed ...
http://www.sslshopper.com/ssl-checker.html#hostname=blog.desdelinux.net
Yes, you are right, something is wrong ..
The certificate is not installed incorrectly .. Everything is correct. What this page informs is that it is not a certificate signed by any of the main certification authorities.
DESDELINUX.NET has its own CA :).
It also states that it is the correct server with its correct ip:
blog.desdelinux.net = 69.61.93.35
Which gives security to users that it is the server. desdelinux.net as it appears in the domain's DNS configuration.
And even Firefox / Iceweasel makes it easy for me to understand.
https://filippo.io/Heartbleed/#blog.desdelinux.net
Hello Franco
I tell you the same as @Mstaaravin .. What this page informs is that it is not a certificate signed by any of the main certification authorities ..
In no case is he affected with Heartbleed.
A small fix on the server and it no longer shows me the vulnerability, thanks for the information.
Hey, why don't you sign it with CAcert? so all of us who have imported CAcert certificates would not have to make an exception to your certificate, and it would automatically enter the blog 😉
How strange, when you try to register in CAcert, you get the page that it is not a valid certificate hahahaha
There you nailed it Elav hahahaha
I apologize .. instead of nailed .. nailed ..
do you already have points in CAcert? if nobody has endorsed you, I think they won't let you upload your certificate = /
It doesn't come by default in browsers, but CAcert is a globally recognized entity, and people like me trust it and import CAcert certificates. Thus, if the blog desdelinux It is certified by CAcert, with all the more reason I trust that its SSL certificate is valid, and I don't have to go around importing independent certificates 😉
I don't know if you have ever been certified by CAcert, but the process is that at least 5 people (approximately) have to certify you, and they check about 3 identifications each. I trust CAcert a lot.. regarding the certificate of desdelinux, I also trust it, but I will give you an example, how do I know that the certificate was not changed an hour ago by some cracker, and I am accepting the fake certificate from the start? I don't think this happened, I'm simply saying that CAcert boosts your confidence a little.
Exactly that is the problem, we cannot upload our certificate 😀
Can someone give us a hand?
There is no point in generating a certificate signed by CAcert, since this authority is not included by default in web browsers.
It is the same as the CA itself desdelinux.net
For those who do not believe me: http://es.wikipedia.org/wiki/CAcert.org
It's funny what you say @biker.. Do you trust CAcert, but you don't trust the certificate and its own CA issued by Desde Linux?
Also @biker, keep in mind that the google website also uses a certificate issued by them (google Inc) .. Do you trust it? Because it is the same .. The difference is that they have contacted the developers of the main web browsers and they have included their CA certificate by default in their browsers ..
You can do the same desdelinux.net..
Let's see @biker,
On the one hand, I understand what you are saying. On the other hand, precisely to prevent a hacker from changing the website of desdelinux.net to another location with a different certificate, you are given the CA to download desdelinux.net to which you import and with which all the certificates located on the server are signed. desdelinux..If someone unsubscribes the actual server desdelinux.net and imposes yours with a different certificate than the one that will have been generated, this will not be signed by the real authority of desdelinux.net and in the browser you will get a message saying that the server certificate does not correspond to the certificates signed by the original CA.
It is impossible for something to happen .. That is why I created both the server certificate and the CA that signs them and I did not directly use a self-signed certificate since this would be dangerous :).
Hi. Very good news. With self-signed certificates it's quite a matter. I work with openvpn and it uses ssl for the certificates and there are no problems. But for the webs, if they do not have the same ones formed by a company in the field, it is worse than not using ssl. And this issue of the ccertificates is crap since they charge you locutas for them.
If you enter the web using HTTPS, when entering any article it does not maintain the protocol but the request to the entrance is using HTTP. Come on, some links do not maintain the protocol (in the web header menu it does)
Yes indeed, this is still missing because you have to modify the loop or something in the WordPress core, or at least this is the first solution I find 🙂
Congratulations KZKG ^ Gaara for the work you have done and I hope everything goes well and that you have few reports. I have browsed the blog using https and I did not see anything that I have to report: D.
Regarding the certificate of desdelinux.net.. The certificate desdelinux.net is not self-signed but is signed by a security authority (CA). desdelinux.net..
That is why this blog offers to download this authority ..
It's like the CAcert authority @biker talks about .. I think there is no problem in importing a certificate in the browser that boys and girls have ..: D.
For my part it is good to protect the communication between the client and the server by encrypting it.
Thanks to you for the help.
Let's hope to solve the details that still remain 🙂
You're welcome KZKG ^ Gaara. Glad I can help a bit :).
Testing and it goes smoothly.
Reporting from the Underworld: Well, when I accessed through https, I got that certificate security, then I gave Download the CA created by petercheco, I got a label where I was wondering if it allowed to install that certificate to access the site, to receive messages from him, etc., I accepted everything and entered the blog perfectly through https. Results: The only bad thing for me is, as I expected, that the loading of the pages slows down a bit, but hey, that's not like cutting your wrists, if I'm in a hurry then I access through http, period. All security efforts are appreciated.
It's already loading me faster, it was just a broadband speed problem from here ... from the underworld.
It works perfect but when accessing the articles and moving between pages it uses http by default, is there a way to always use https?
I agree, the same thing happens to me.
It gives me an error, and it is not because it is not from a recognized certifying authority
Technical details:
blog.desdelinux.net uses an invalid security certificate. The certificate is not trusted because no issuer chain was provided. (Error code: sec_error_unknown_issuer)
I wonder: if the certificate is not signed by a recognized security entity, it would not be easier (at least in firefox) to simply enter the site through https and when the warning appears, permanently save the certificate, as is normally done with any self signed certificate?
Well in Firefox you can make a permanent exception, but in IE I think not .. It is better that each one import the authority in their browser and that's it.
It turned out like this for me.
Hello, I know it is not the place, for my problem but I have a problem, maybe you can help me. I'm experimenting with Elementary Os, I just installed the proprietary Nvidia driver which says (Recommended). Since I did this, the system starts me directly as if it were in the terminal, that is, it does not load the graphical aspect. When I enter with the second option (recovery mode) and I choose the option to continue the normal bounce, there if it lifts the graphic part. From now on sorry for posting this here and I hope you can help me. Cheers
Someone to guide me:
I have managed to install the certificate in both Firefox and Qupzilla. But now that I have reinstalled Maxthon I have not figured out how to get the certificate installed. Someone who has made it?
Thank you
I just tried, but apparently although it is based on Chrome it does not have such options.
Curious tip ... So they don't have the wordpress admin with https? Hmmm It looks like a hacker's restaurant… I recommend «Security for dummies» 😛
Willians, as there is trust and we have known each other for years I will tell you clearly, you can get non-constructive criticism… you know where.
To fuck and bother for another part ¬_¬
Without pretending to fall into a dictionary offense competition that you should believe me when I tell you that you have everything to lose, I would like to suggest that you go beyond the mockery of my words - or the tip of your nose.
There is an idea in them that, appealing to your intellect (I was definitely wrong, sorry for overestimating you), I assumed that you would be able to assimilate in a sufficiently constructive way and not with the perretic / catharsis of a 9 year old child with which you have assumed it .
Support for social misunderstanding aside, and in case you are still reading these lines (it may be the case that I have overestimated you again and right now you are biting a towel in Anger Management mode), I tell you, as a summary of my idea, I find it curious that someone who has written so many posts that have to do with security in systems, whether web or any other type, maintains - after several years since he has desdelinux- the blog administration interface using plain http.
I never asked and the truth is that I was not interested in finding out, but I always assumed that the admin of desdelinux It ran -as a primary security measure- over https (and not as an option, but not as THE OPTION).
Nothing, it will pass. At the moment he assumes all this as one more contribution, alone. Save the "non-constructive criticism" tooth for whoever really deserves it.
Your partner still willians
Very interesting, I have enjoyed reading. After so many comments, it is not easy to add something, but I have a question.
From the moment users visit, comment, etc. On other websites, your security is still exposed. For that reason I do not see the usefulness, unless they are limited only to DesdeLinux.
Greetings.
StartSSL gives valid certificates like paid companies but totally free 🙂
So far it seems to be working fine. It's a good start.
They have not tried with https://www.startssl.com/ offers free certificates, another good option is https://www.cacert.org/, days ago I read this post https://www.sslshopper.com/article-free-ssl-certificates-from-a-free-certificate-authority.html