Hello friends!. We are starting a new series of articles that we hope will be helpful. We have decided to write them for those who like to know what they work with, and make their own implementations without depending on totally proprietary software, or those that are half free and half commercial.
Required reading is the OpenLDAP Software 2.4 Administrator's Guide. Yes, in English, because we are using software designed and written in the language of Shakespeare. 🙂 We also strongly recommend reading the Ubuntu Server Guide 12.04., which we give for download.
The existing documentation is in English. I have not found Spanish translations of either of the two previously recommended.
Everything written in this introduction is taken from Wikipedia or freely translated into Spanish from the documents mentioned above.
We will see:
- Summary definition
- LDAP Key Features from the User's Perspective
- When should we use LDAP?
- When should we not use LDAP?
- What services and software do we plan to install and configure?
Summary definition
From Wikipedia:
LDAP is the acronym for Lightweight Directory Access Protocol, which refers to a protocol at the application level that allows access to an ordered and distributed directory service to search for different information in a network environment. . LDAP is also considered a database (although its storage system may be different) that can be queried.
A directory is a set of objects with attributes organized in a logical and hierarchical way. The most common example is the telephone directory, which consists of a series of names (persons or organizations) that are arranged alphabetically, with each name having an address and a telephone number attached to it. To understand better, it is a book or folder, in which people's names, telephone numbers and addresses are written, and it is arranged alphabetically.
An LDAP directory tree sometimes reflects various political, geographic, or organizational boundaries, depending on the model chosen. Current deployments of LDAP tend to use Domain Name System (DNS) names to structure the higher levels of the hierarchy. As you move down the directory, entries may appear that represent people, organizational units, printers, documents, groups of people, or anything that represents a given entry in the tree (or multiple entries).
Usually, it stores authentication information (user and password) and is used to authenticate, although it is possible to store other information (user contact data, location of various network resources, permissions, certificates, etc.). In summary, LDAP is a unified access protocol to a set of information on a network.
The current version is LDAPv3, and it is defined in RFCs RFC 2251 and RFC 2256 (LDAP base document), RFC 2829 (authentication method for LDAP), RFC 2830 (extension for TLS), and RFC 3377 (technical specification) .
Some LDAP implementations:
Active Directory: is the name used by Microsoft (since Windows 2000) as a centralized information store for one of its management domains. A Directory Service is a structured repository of information on the various objects contained in the Active Directory, in this case they could be printers, users, computers ... It uses different protocols (mainly, LDAP, DNS, DHCP, Kerberos...).
Under this name there is actually a schema (definition of the fields that can be consulted) LDAP version 3, which allows integrating other systems that support the protocol. This LDAP stores information on users, network resources, security policies, configuration, assignment of permissions, etc.
Novell Directory ServicesAlso known as eDirectory is the Novell implementation used to manage access to resources on different servers and computers on a network. It is basically composed of a hierarchical and object-oriented database, which represents each server, computer, printer, service, people, etc. Between which permissions for access control are created, through inheritance. The advantage of this implementation is that it runs on multiple platforms, so it can be easily adapted to environments that use more than one operating system.
It is the forerunner in terms of Directory structures, having been introduced in 1990 with Novell Netware version 4.0. Although Microsoft's AD has grown in popularity, it still cannot match the reliability and quality of eDirectory and its Cross-Platform capabilities.
OpenLDAP: It is a free implementation of the protocol that supports multiple schemes so it can be used to connect to any other LDAP. It has its own license, the OpenLDAP Public License. Being a platform independent protocol, several GNU / Linux and BSD distributions include it, as do AIX, HP-UX, Mac OS X, Solaris, Windows (2000 / XP), and z / OS.
OpenLDAP has four main components:
- slapd - standalone LDAP daemon.
- slurpd - standalone LDAP update replication daemon.
- LDAP protocol support library routines
- Utilities, tools and clients.
LDAP Key Features from the User's Perspective
What kind of information can we store in a Directory?. The information model in an LDAP directory is based on entries. An entry is a collection of attributes that has a unique Distinguished Name or "Distinguished Name (DN)". The DN is used to refer to the entry uniquely.
Each attribute of an entry has a type and one or more values. The types are typically mnemonic strings like cn o "Common Name" for common names, or mail for email addresses. The syntax of the values depends on the type of attribute.
For example, an attribute cn can contain the value of Frodo bagins. An attribute mail can have the courage frodobagins@amigos.cu. An attribute jpgePhoto can contain a photo in binary format JPEG.
How is the information organized?. In LDAP, directory entries are organized in a hierarchical structure in the form of an inverted tree. Traditionally, this structure reflects geographic and / or organizational boundaries or limits.
Entries representing countries appear at the top of the tree. Below them will be entries representing states and national organizations.
Then there may be entries that represent organizational units, people, printers, documents, or whatever else we are able to think of.
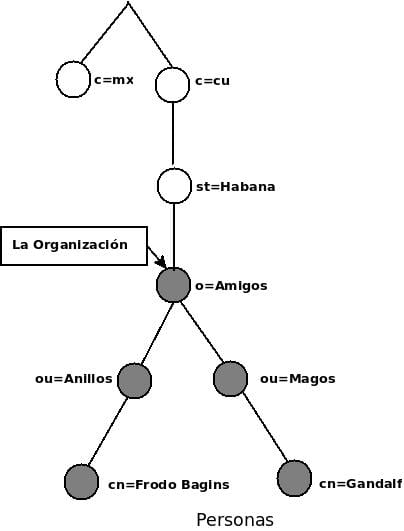
The figure below is an example of an LDAP directory tree in which traditional names are used.
LDAP allows control of which attributes we need for an entry by using a special attribute called objectClass. The value of the attribute objectClass determines the Scheme Rules o Schema Rules that the input must obey.
How do we reference the information?. We refer to an entry by its Distinguished Name or Distinguished Name, which is constructed from the name of the entry itself (called Distinguished Relative Name or Relative Distinguished Name o RDN), concatenated with the name of the entries of its ancestors or ancestors.
For example, in the figure above the entry Frodo Bagins has a RDN cn = Frodo Bagins and DN complete is cn = Frodo Bagins, ou = Rings, o = Friends, st = Havana, c = cu.
How do we access the information?. LDAP has defined the operations necessary to interrogate and update the directory. These include the operations of adding and deleting an entry, modifying an existing entry, and renaming an entry.
However, most of the time LDAP is used to search for information stored in the directory. Search operations allow a portion of the directory to be searched for entries that meet some criteria specified in the search filter. That way we can search each entry that met the search criteria.
How do we protect information from unauthorized access?. Some directory services are unprotected and allow anyone to view your information.
LDAP provides a mechanism for clients to authenticate, or confirm their identity to a directory service, in order to guarantee access control to protect the information that the server contains.
LDAP also supports data security services, both with respect to integrity and confidentiality.
When should we use LDAP?
This is a very good question. In general, we must use the Directory Service when we need information to be centrally stored and managed, and to be accessible through standards-based methods.
Some examples of the type of information that we find in the business and industrial environment:
- Machine Authentication
- User Authentication
- System Users and Groups
- Address book
- Organizational Representations
- Resource Tracking
- Telephone Information Warehouse
- User Resource Management
- Email Address Search
- Application Settings Store
- PBX Telephone Plant Configurations Warehouse
- etc…
There are several Distributed Schema Files -Distributed Schema Files- standards-based. However, we can always create our own Schema Specification ... when we are LDAP Experts. 🙂
When should we not use LDAP?
When we realize that we are twisting or by forcing our LDAP to do what we need. In that case, it may need to be redesigned. Or if we need a single application to use and manipulate our data.
What services and software do we plan to install and configure?
- Directory Service or Directory Services based OpenLDAP
- Services NTP, DNS y DHCP independent
- To integrate Samba to LDAP
- Possibly we will develop the integration of LDAP y Kerberos
- Manage the Directory with the web application Ldap Account Manager.
And this is it for today, friends!
Sources:
- https://wiki.debian.org/LDAP
- OpenLDAP Software 2.4 Administrator's Guide
- Ubuntu 12.04 server guide
I think FreeIPA is a comprehensive project (LDAP, Kerberos, DNS, etc) interesting to study, based on the LDAP 389 server.
To begin with the liks of the Pfs do not work. I am very interested in educating myself in ldap. Thanks for sharing.
Links corrected.
Interesting.
You went over the phone, one more time!
Great contribution.
Hug! Paul.
Thank you all for commenting !!! I could not connect before with my modem at 28000 baud / second. What kind of speed. 🙂
Greetings to all
Thank you very much everyone for comment !!!. Ozkar, FreeIPA is much more than an LDAP. It integrates Red Hat Active Directory 389 with a whole series of related services. It is a Fedora project animal. Too huge for my modest knowledge.
Excellent article, it suits me like a glove since I was planning to internalize myself in these issues, I look forward to new articles.
Thank you very much for sharing, with that and the ClearOS I have for a while 🙂
Excellent tutorial, I also downloaded the Ubunto book, thanks!
Ubuntu jejjeej I'm still asleep ...
Although disrespecting your work, I have read it above and if I understood everything very badly or less well, it can be understood in this joke:
"But if I become the capo capo of open-ldap I develop my web browser and google shakes!"
Thanks for the effort and it hurts that there is no material in Spanish. mmm ...
Fico, see if this guide in Spanish serves to add it to the material ...
http://www.google.com.ar/url?sa=t&rct=j&q=&esrc=s&source=web&cd=4&ved=0CEwQFjAD&url=http%3A%2F%2Felpuig.xeill.net%2Fdepartaments%2Finformatica%2Ffitxers%2Fsistemes-operatius%2Fcurso-de-ldap-en-gnu-linux%2Fat_download%2Ffile&ei=NwXgUrIOxLaRB4LHgYgG&usg=AFQjCNGj7BjNtzfdlu1gsl3YSWK1U1ELpw&sig2=aKABXgHookIGYhYXevUQew&bvm=bv.59568121,d.eW0
Now moving forward a bit I keep reading the posts on the page https://blog.desdelinux.net/ldap-introduccion/ I would like you to clarify for me a little what refers to Machine Authentication this point is not clear to me and I am very enthusiastic about this OpenLdap I have already spent several hours reading this blog but I want to be able to master the topics and concepts for that reason my intervention in your activities in advance thank you very much Mr. Fico we continue in contact greetings