Learning SSH: Good practices to do in an SSH Server
In this present, sixth and last post, from our series of posts on Learning SSH we will address in a practical way, the configuration and use of the options specified in the OpenSSH configuration file that are handled on the side of the ssh-server, that is, the file "SSHD Config" (sshd_config). Which, we addressed in the previous installment.
In such a way that we can know in a brief, simple and direct way, some of the best good practices (recommendations and tips) when set up an SSH Serverboth at home and in an office.

Learning SSH: SSHD Config File Options and Parameters
And, before starting today's topic, about the best “good practices to apply in the configurations of an SSH Server”, we will leave some links to related publications, for later reading:


Good practices in an SSH Server
What good practices apply when configuring an SSH Server?
Next, and based on the options and parameters del SSHD Config file (sshd_config), previously seen in the previous post, these would be some of the best good practices to perform regarding the configuration of said file, to ensure our best remote connections, incoming and outgoing, on a given SSH Server:
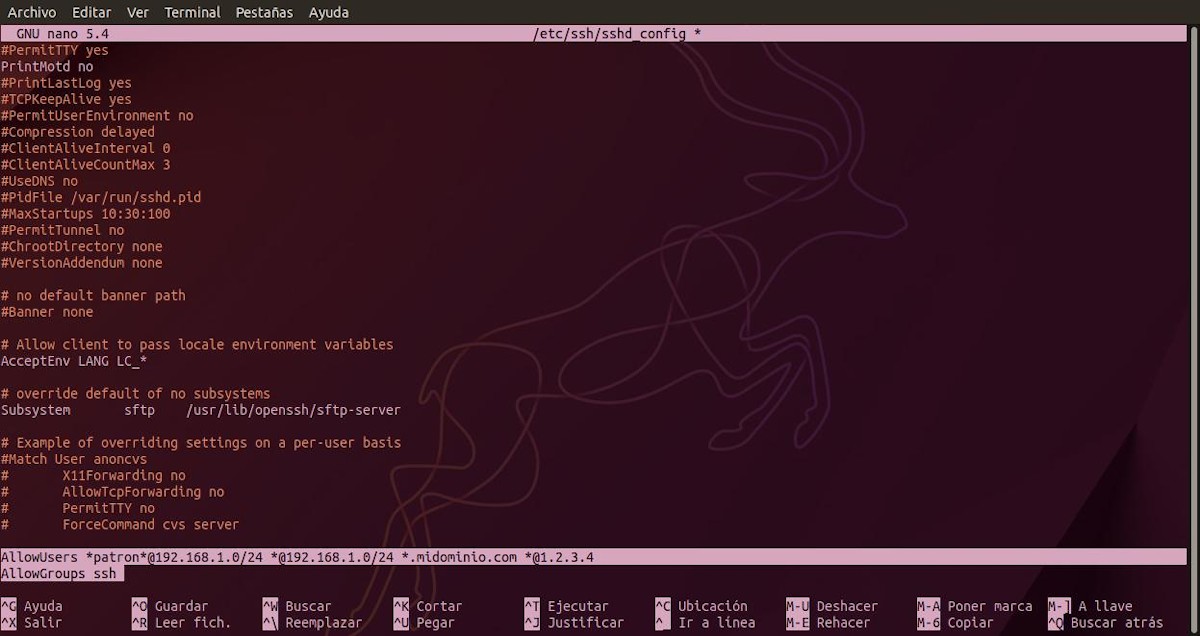
Specify the users who can log in SSH with the option AllowUsers
Since this option or parameter is usually not included by default in said file, it can be inserted at the end of it. Making use of a list of username patterns, separated by spaces. So that, if specified, the login, then only the same will be allowed for username and hostname matches that match one of the configured patterns.
For example, as seen below:
AllowUsers *patron*@192.168.1.0/24 *@192.168.1.0/24 *.midominio.com *@1.2.3.4
AllowGroups ssh
Tell SSH which local network interface to listen on with the ListenAddress option
To do this, you must enable (uncomment) the opción ListenAddress, which comes frome default with the value "0.0.0.0", but it actually works on ALL mode, that is, listen on all available network interfaces. Therefore, then said value must be established in such a way that it is specified which one or local IP addresses they will be used by the sshd program to listen for connection requests.
For example, as seen below:
ListenAddress 129.168.2.1 192.168.1.*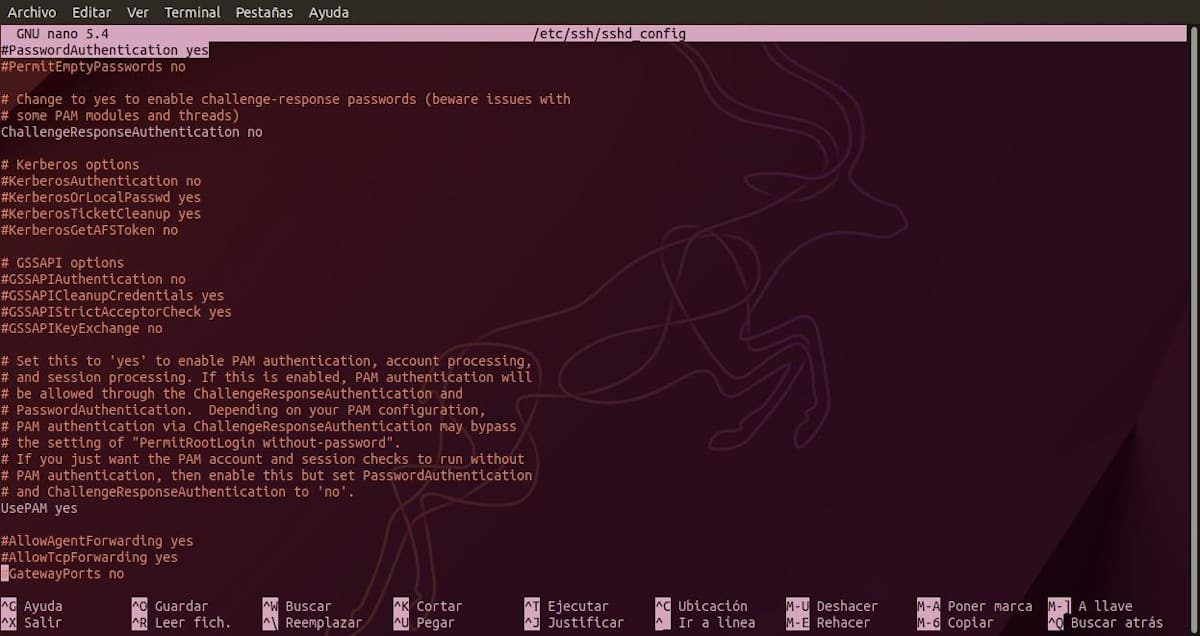
Set SSH login via keys with the option Password Authentication
To do this, you must enable (uncomment) the opción Password Authentication, which comes frome default with the yes value. And then, set that value as "No", in order to require the use of public and private keys to achieve access authorization to a specific machine. Achieving that only remote users can enter, from the computer or computers, that are previously authorized. For example, as seen below:
PasswordAuthentication no
ChallengeResponseAuthentication no
UsePAM no
PubkeyAuthentication yes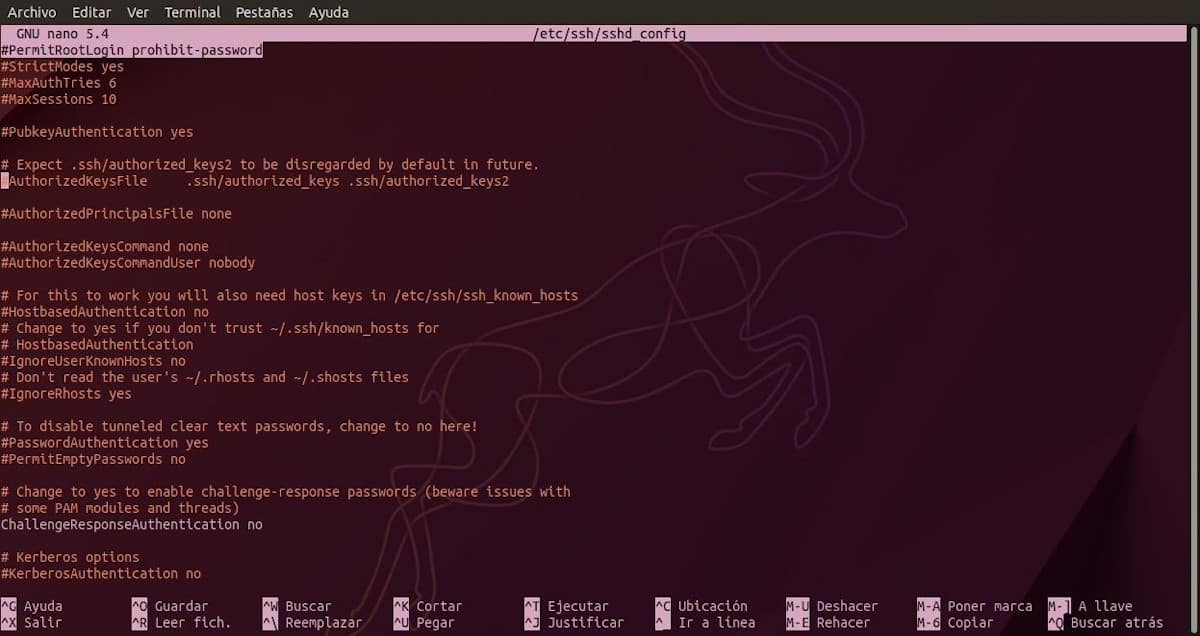
Disable root login via SSH with the option PermitRootLogin
To do this, you must enable (uncomment) the PermitRootLogin option, which comes frome default with the "prohibit-password" value. However, if it is desired that in full, root user is not allowed to start an SSH session, the appropriate value to set is "No". For example, as seen below:
PermitRootLogin no
Change the default SSH port with the Port option
To do this, you must enable (uncomment) the port option, which comes by default with the value "22". Nevertheless, it is vital to change said port to any other available one, in order to mitigate and avoid the number of attacks, manual or brute force, that can be made through said well-known port. It is important to make sure that this new port is available and can be used by the other applications that are going to connect to our server. For example, as seen below:
Port 4568
Other useful options to set
Lastly, and since the SSH program is too extensive, and in the previous installment we already addressed each of the options in more detail, below we will only show some more options, with some values that could be appropriate in multiple and varied use cases.
And these are the following:
- Banner /etc/issue
- ClientAlive Interval 300
- ClientAliveCountMax 0
- LoginGraceTime 30
- LogLevel INFO
- MaxAuthTries 3
- MaxSessions 0
- Max Startups 3
- AllowEmptyPasswords No
- PrintMotd yes
- PrintLastLog yes
- StrictModes Yes
- SyslogFacility AUTH
- X11 Forwarding yes
- X11DisplayOffset 5
NoteNote: Please note that, depending on the level of experience and expertise of the SysAdmins and the security requirements of each technology platform, many of these options can quite rightly and logically vary in very different ways. In addition, other much more advanced or complex options can be enabled, as they are useful or necessary in different operating environments.
Other good practices
Among other good practices to implement in an SSH Server We can mention the following:
- Set up a warning email notification for all or specific SSH connections.
- Protect SSH access to our servers against brute force attacks using the Fail2ban tool.
- Periodically check with the Nmap tool on SSH servers and others, in search of possible unauthorized or required open ports.
- Strengthen the security of the IT platform by installing an IDS (Intrusion Detection System) and an IPS (Intrusion Prevention System).


Summary
In short, with this latest installment on "Learning SSH" we finished the explanatory content on everything related to OpenSSH. Surely, in a short time, we will be sharing a little more essential knowledge about the SSH protocol, and regarding your use by console through Shell scripting. So we hope you are “good practices in an SSH Server”, have added a lot of value, both personally and professionally, when using GNU/Linux.
If you liked this post, be sure to comment on it and share it with others. And remember, visit our «homepage» to explore more news, as well as join our official channel of Telegram from DesdeLinux, West group for more information on today's topic.
I look forward to the second part of this article where you expand more on the last point:
Strengthen the security of the IT platform by installing an IDS (Intrusion Detection System) and an IPS (Intrusion Prevention System).
Thank you!!
Regards, Lhoqvso. I will be waiting for its realization. Thank you for visiting us, reading our content and commenting.