
Learning SSH: SSH Config File Options and Parameters
In our latest installment on Learning SSH We deal with virtually all SSH command options and parameters of the OpenSSH program, which are available when you run the ssh command at the terminal. One of them was "-o option", which we explain allows use options specified in the OpenSSH configuration file, that is, the file "SSHConfig" (ssh_config).
For this reason, today we will briefly explain some of these specified options in the OpenSSH configuration file, to give us a small and useful idea of what we can do when executing a command order of the type “ssh -o option…”, or simply configure our local SSH server (client).

Learning SSH: Options and Configuration Parameters
And as usual, before diving into today's topic about the options and parameters available in the file OpenSSH "SSH Config" (ssh_config), we will leave for those interested the following links to some previous related posts:



SSH Config File Options and Parameters (ssh_config)
What is the SSH Config (ssh_config) file for OpenSSH?
OpenSSH has 2 configuration files. one called ssh_config for the configuration of client package and another call sshd_config for server package, both located in the following path or directory: /etc/ssh.

Therefore, when working on the configuration file "SSH Config" (ssh_config) We assume that we will be working on a computer that will function as a client-type workstation, that is, that it will carry out SSH connections to one or more teams Servers with SSH.
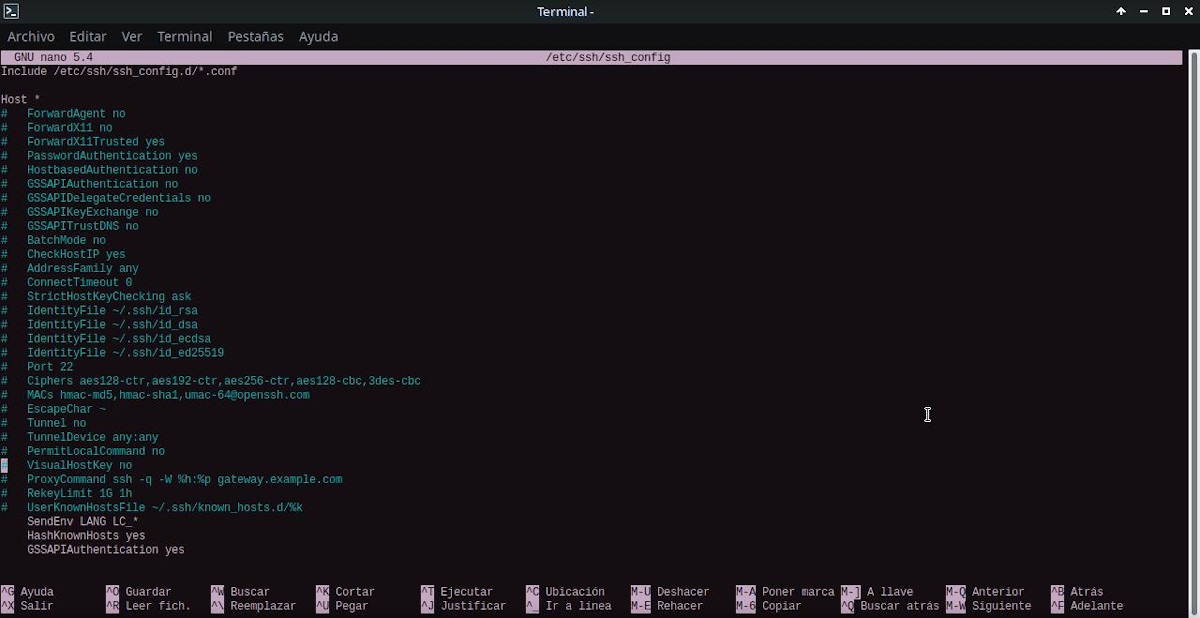
List of existing options and parameters
Below are some of the options or parameters that exist within the configuration file "SSH Config" (ssh_config), many of which can be used within a command like “ssh -o option…”.
host/match
This option or parameter indicates within the SSH client configuration file (ssh_config) that the following declarations (up to the next Host or Match option or parameter) are restricted indicated), so that they are only for those hosts that match one of the patterns given after the keyword.
That is to say, that this option acts as a section divider within the file, just like the Match option. Therefore, both can be repeated multiple times in the file. setting. And its values, can be a list of patterns, which determine what are the subsequent options to apply to connections made to the hosts in question.
The value * means "all hosts”, while in Match the value “all” does the same. And, if more than one pattern is provided, they must be separated by whitespace. A pattern input can be negated by prefixing it with an exclamation mark ('!'), so that negated matches are useful in providing exceptions for wildcard matches.
AddressFamily
Allows you to specify which type (family) of addresses to use when connecting. Valid arguments are: any (default), inet (use only IPv4), or inet6 (use only IPv6).
BatchMode
Allows you to disable password prompts and host key confirmation prompts on user interaction, if you set the "yes" argument or value. This option is useful in scripts and other batch jobs where no user is present to interact with SSH. The argument must be "yes" or "no", where "no" is the default value.
This parameter allows you to specify whether SSH should terminate the connection, if it cannot configure all requested dynamic, tunnel, local, and remote port forwarding.
ForwardAgent
This parameter allows you to specify whether the connection to the authentication agent (if any) will be forwarded to the remote machine. The argument can be "yes", since "no" is the default, and agent forwarding should be enabled with caution. Since, users with the ability to bypass file permissions on the remote host can access the local agent through the forwarded connection.
ForwardX11
Here it is specified whether X11 connections will be automatically redirected through the secure channel and the DISPLAY set. The argument can be "yes", since "no" is the default value.
ForwardX11Trusted
Here you set to yes which remote X11 clients will have full access to the original X11 display. Namely, If this option is set to "yes", remote X11 clients will have full access to the original X11 screen. While, yesi is set to no (default), remote X11 clients will be considered untrusted and will be prevented from stealing or tampering with data belonging to trusted X11 clients.
HashKnownHosts
Used to tell SSH to hash host names and addresses when they are added to ~/.ssh/known_hosts. So that these encrypted names can be used normally by ssh and sshd, but without revealing identifying information, in case the contents of the file are disclosed.
GSSAPIAuthentication
Used to specify within SSH, whether GSSAPI-based user authentication is allowed. GSSAPI is typically used for Kerberos authentication, for example with Active Directory.
SendEnv
It is used to specify which local environment variables should be sent to the server. To make this work correctly, the server must also support it, as well as be configured to accept these environment variables. Variables are specified by name, which can contain wildcard characters. Also, several of the environment variables can be separated by whitespace or spread over several directives of this type (SendEnv).
More information
And in this fourth installment, to expand this information and study each and every one of the options and parameters available within the configuration file "SSH Config" (ssh_config)We recommend exploring the following links: SSH configuration file for the OpenSSH client y Official OpenSSH Manuals, in English. And just as in the previous three installments, explore the following official content and trustworthy online about SSH and OpenSSH:
- Debian Wiki
- Debian Administrator's Manual: Remote Login / SSH
- Debian Security Handbook: Chapter 5. Securing services running on your system


Summary
In short, this new installment on "Learning SSH" very surely the explanatory content will be a great complement to the previous publications related to OpenSSH. In such a way, to perform better and more complex remote connections. and run more secure and reliable settings, using said remote and secure connection protocol.
If you liked this post, be sure to comment on it and share it with others. And remember, visit our «homepage» to explore more news, as well as join our official channel of Telegram from DesdeLinux, West group for more information on today's topic.