Goal, the parent company of Facebook and Instagram, does not stop using all weapons that they consider effective to achieve your “privacy” goals and now it has just been singled out again for practices of tracking users on the web by injecting code into the browser embedded in their applications.
This matter was brought to the attention of the general public by Felix krause, a privacy investigator. In reaching this conclusion, Felix Krause designed a tool capable of detecting if JavaScript code is injected on the page that opens in the browser built into the Instagram, Facebook, and Messenger apps when a user clicks a link that takes them to a page outside of the app.
After opening the Telegram app and clicking a link that opens a third-party page, no code injection was detected. However, when repeating the same experience with Instagram, Messenger, Facebook on iOS and Android, the tool allowed inserting several lines of injected JavaScript code after opening the page in the browser built into these applications.
According to the researcher, the external JavaScript file that the Instagram app injects is (connect.facebook.net/en_US/pcm.js), which is code to create a bridge to communicate with the host application.
More details, The investigator discovered the following:
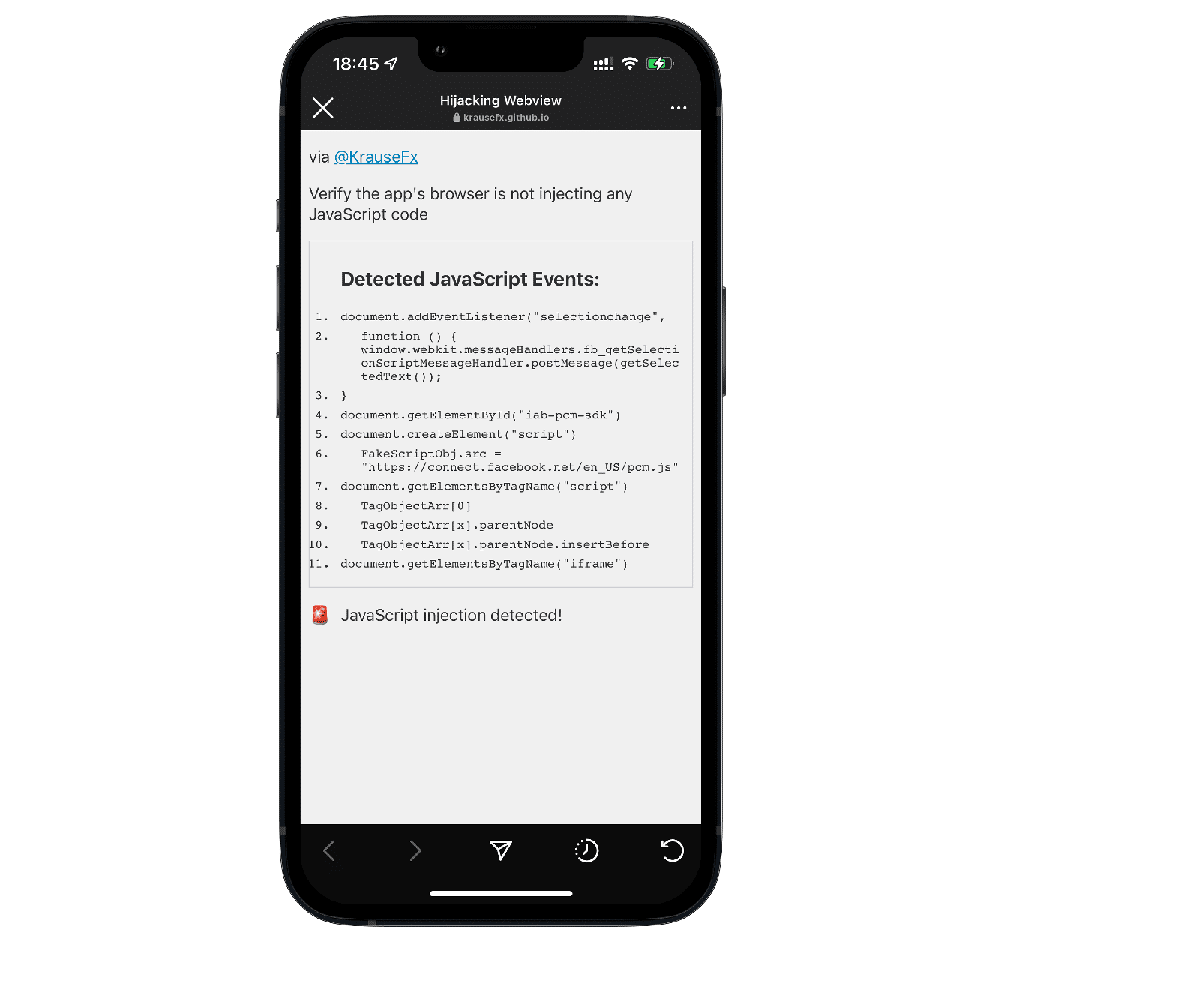
Instagram is adding a new event listener to get details whenever the user selects text on the website. This, combined with listening to screenshots, gives Instagram a complete overview of the specific information that was selected and shared. the Instagram app checks for an item with the id iab-pcm-sdk which is likely referring to “In App Browser”.
If no element with id iab-pcm-sdk is found, Instagram creates a new script element and sets its source to https://connect.facebook.net/en_US/pcm.js
It then finds the first script element on your website to insert the JavaScript pcm file just before
Instagram is also looking for iframes on the website, but no information was found on what it does.
From there, Krause explains that injecting custom scripts into third party websites could, even if there is no evidence to confirm that the company is doing so, allow Meta to monitor all user interactions, such as interactions with each button and link, text selections, screenshots, and all form inputs such as passwords, addresses, and credit card numbers. Also, there is no way to disable the custom browser built into the apps in question.
After the publication of this discovery, Meta would have reacted stating that the injection of this code would help to add events, such as online purchases, before they are used for targeted advertising and measures for the Facebook platform. The company reportedly added that "for purchases made through the app's browser, we ask for user consent to save payment information for autofill purposes."
But for the researcher, there is no legitimate reason to integrate a browser into Meta applications and force users to stay in that browser when they want to browse other sites that have nothing to do with the firm's activities.
In addition, this practice of injecting code into pages of other websites would generate risks on several levels:
- Privacy and analytics: The host app can track literally everything that happens on the website, such as every touch, key press, scrolling behavior, what content is copied and pasted, and data viewed as online purchases.
- Theft of user credentials, physical addresses, API keys, etc.
- Ads and Referrals: The host app can inject ads into the website, or override the ads API key to steal revenue from the host app, or override all URLs to include a referral code.
- Security: Browsers have spent years optimizing the security of the user's web experience, such as displaying HTTPS encryption status, warning the user about unencrypted websites, etc.
- Injecting additional JavaScript code into a third party website can cause issues that can break the website
- Browser extensions and user content blockers are not available.
- Deep linking doesn't work well in most cases.
- It is often not easy to share a link through other platforms (eg email, AirDrop, etc.)
Finally If you are interested in knowing more about it, you can consult the details in the following link.