
Researchers from Masaryk University revealed information very important about vulnerabilities in various iImplementations of the ECDSA / EdDSA digital signature generation algorithm, that allows to recover the value of the private key based on the analysis of information leaks on individual bits that appear when applying analysis methods through third-party channels. The vulnerabilities are codenamed Minerva.
The most famous projects that affect the proposed attack method are OpenJDK, OracleJDK (CVE-2019-2894) and the library libgcrypt (CVE-2019-13627) used in GnuPG. The problems are also susceptible for libraries MatrixSSL, Crypto ++, wolfCrypt, elliptical, jsrsasign, Python-ECDSA, ruby_ecdsa, fastecdsa and also some smart cards Athena IDProtect, TecSec Armored Card, SafeNet eToken 4300, Valid S / A IDflex V.
In addition to the vulnerabilities mentioned at the moment they are not affected OpenSSL, Botan, mbedTLS, and BoringSSL. Mozilla NSS, LibreSSL, Nettle, BearSSL, cryptlib, OpenSSL in FIPS mode. Microsoft .NET crypto, Linux kernel libkcapi, Sodium, and GnuTLS are yet to be tested.
We have found implementations that lose the bit length of the scalar during scalar multiplication in ECC. This leak may seem miniscule since the bit length has a very small amount of information present in the scalar. However, in the case of ECDSA / EdDSA signature generation, filtering the bit length of the random nonce is sufficient for full recovery of the private key used after observing a few hundred to a few thousand signatures in known messages, due to to the application of some techniques.
We believe that all previous cards are affected because they share a common ECDSA component (FIPS 214 module), which is described as Athena OS2 ECDSA755 Component in Inside Secure AT90SC A1.0 (Firmware). We have tested the vulnerability only on the Athena IDProtect card with CPLC and ATR data
The problem is caused by the ability to determine individual bit values during multiplication by a scalar during ECC trading. Indirect methods, such as estimating delay in performing calculations, are used to extract bit information.
An attack requires unprivileged access to the host in which the digital signature is generated (a remote attack is not excluded, but it is very complicated and requires a large amount of data for analysis, therefore it can be considered unlikely).
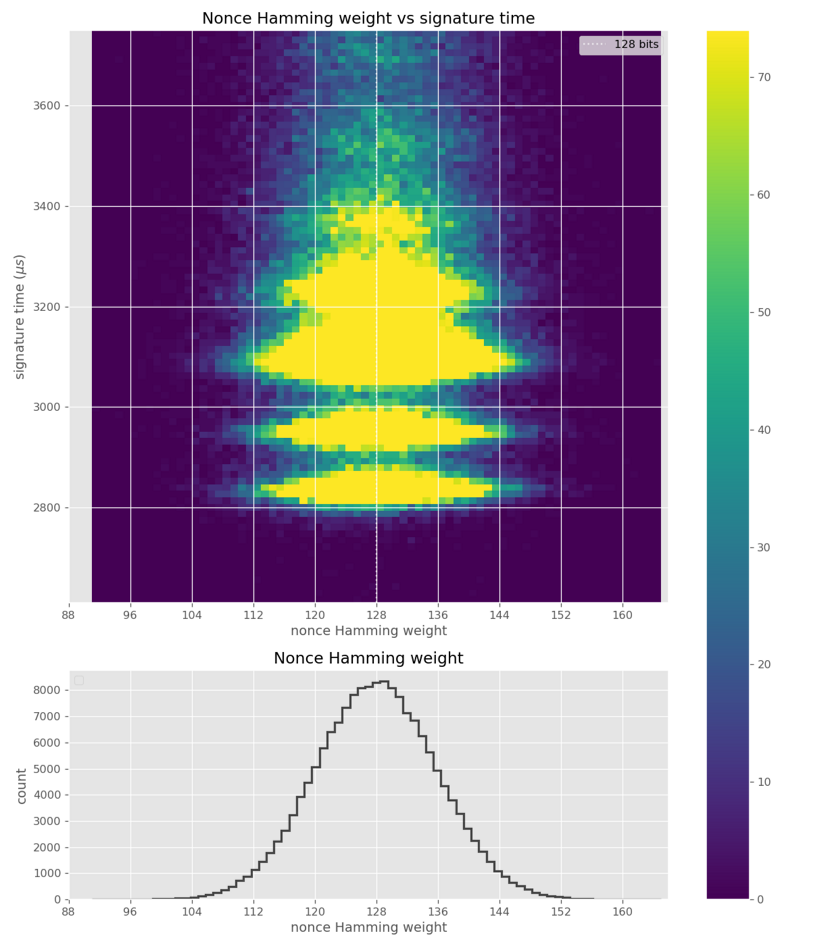
Despite the small size of the leak, for ECDSA the definition of even a few bits with information about the initialization vector (nonce) is sufficient to carry out an attack to sequentially restore the complete private key.
According to the authors of the method, for successful key recovery, analysis of several hundred to several thousand generated digital signatures is sufficient for messages known to the attacker. For example, to determine the private key used in the Athena IDProtect smart card based on the Inside Secure AT90SC chip, using the elliptic curve secp256r1, 11 thousand digital signatures were analyzed. The total attack time was 30 minutes.
Our attack code and proof of concept is inspired by the Brumley & Tuveri method.
The problem has already been fixed in libgcrypt 1.8.5 and wolfCrypt 4.1.0, other projects have not yet generated updates. It is also possible to trace the vulnerability fix in the libgcrypt package in distributions on these pages: Debian, Ubuntu, RHEL, Fedora, openSUSE / SUSE, FreeBSD, Arch.
The researchers also tested other cards and libraries, of which the following are not vulnerable:
- OpenSSL 1.1.1d
- Bouncy Castle 1.58
- BoringSSL 974f4dddf
- libtomcrypt 1.18.2
- Boot 2.11.0
- Microsoft CNG
- mbedTLS 2.16.0
- Intel IPP-Crypto
Cards
- DHW ACOSJ 40K
- Feitian A22CR
- G&D SmartCafe 6.0
- G&D SmartCafe 7.0
- Infineon CJTOP 80K INF SLJ 52GLA080AL M8.4
- Infineon SLE78 Universal JCard
- NXP JCOP31 v2.4.1
- NXP JCOP CJ2A081
- NXP JCOP v2.4.2 R2
- NXP JCOP v2.4.2 R3
- SIMOME TaiSYS Vault
If you want to know more about the attack used and the vulnerabilities detected, you can do so in the following link The tools used to replicate the attack are available for download.