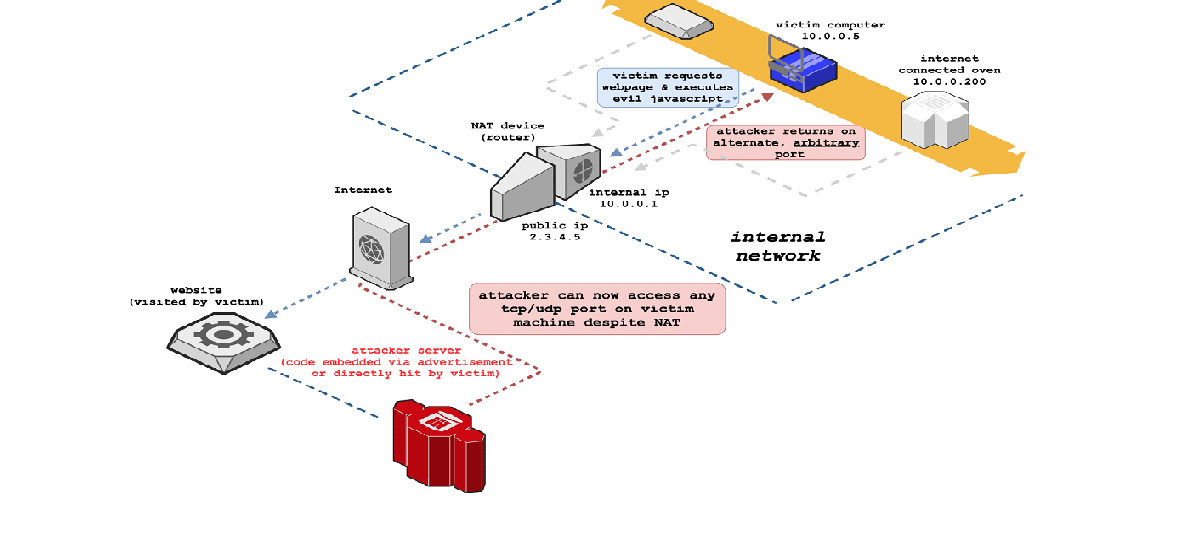
Samy kamkar (a famous security researcher known for creating various sophisticated attack devices, such as a keylogger on a USB phone charger) has introduced a new attack technique called "NAT slipstreaming".
El ataque allows, when opening a page in a browser, to establish a connection from the attacker's server to any UDP or TCP port on the user's system located behind the address translator. The Attack Toolkit is published on GitHub.
The method relies on fooling the ALG connection tracking mechanism (Application Level Gateways) in address translators or firewalls, which is used to organize the NAT forwarding of protocols that use multiple network ports (one for data and one for control), such as SIP. H323, IRC DCC and FTP.
The attack is applicable to users who connect to the network using internal addresses from the intranet range (192.168.xx, 10.xxx) and allows any data to be sent to any port (no HTTP headers).
To carry out an attack, it is sufficient for the victim to execute the JavaScript code prepared by the attackerFor example, by opening a page on the attacker's website or viewing a malicious advertisement on a legitimate website.
In a first stage, the attacker obtains information about the user's internal address, which can be determined by WebRTC or, if WebRTC is disabled, by brute force attacks with response time measurement when requesting a hidden image (for existing hosts, an attempt to request an image is faster than for non-existent timeout before returning a TCP RST response).
In the second stage, the JavaScript code executed in the victim's browser generates a large HTTP POST request (which does not fit in a packet) to the attacker's server using a non-standard network port number to initiate tuning of the TCP fragmentation parameters and MTU size on the victim's TCP stack.
In response, the attacker's server returns a TCP packet with the MSS option (Maximum segment size), which determines the maximum size of the received packet. In the case of UDP, the manipulation is similar, but relies on sending a large WebRTC TURN request to trigger IP-level fragmentation.
«NAT Slipstreaming exploits the user's browser in conjunction with the Application Level Gateway (ALG) connection tracking mechanism built into NAT, routers, and firewalls by chaining internal IP extraction through a time attack or WebRTC, fragmentation discovery of automated remote IP and MTU, TCP packet size massaging, misuse of TURN authentication, precise control of packet limits and protocol confusion from browser abuse, "said Kamkar in an analysis.
The main idea is that, knowing the fragmentation parameters, can send a large HTTP request, the queue of which will fall on the second packet. At the same time, the queue that goes into the second packet is selected so that it does not contain HTTP headers and is cut off on data that completely corresponds to another protocol for which NAT traversal is supported.
In the third stage, using the above manipulation, the JavaScript code generates and sends a specially selected HTTP request (or TURN for UDP) to the TCP port 5060 of the attacker's server, which, after fragmentation, will be split into two packets: a packet with HTTP headers and part of the data and a valid SIP packet with the internal IP of the victim.
The system for tracking connections on the network stack will consider this packet to be the beginning of a SIP session and it will allow packet forwarding for any port selected by the attacker, assuming this port is used for data transmission.
The attack can be carried out regardless of the browser used. To solve the problem, Mozilla developers suggested blocking the ability to send HTTP requests to network ports 5060 and 5061 associated with the SIP protocol.
The developers of the Chromium, Blink and WebKit engines also plan to implement a similar protection measure.
Source: https://samy.pl