Hello friends!. We are going to make a network with several desktop computers, but this time with the Debian 7 "Wheezy" Operating System. As a server he clearOS. As a data, let us observe that the project Debian-Edu use Debian on your servers and workstations. And that project teaches us and makes it easier to set up a complete school.
It is essential to read before:
- Introduction to a Network with Free Software (I): Presentation of ClearOS
We will see:
- Example network
- We configure the LDAP client
- Configuration files created and / or modified
- The /etc/ldap/ldap.conf file
Example network
- Domain Controller, DNS, DHCP, OpenLDAP, NTP: ClearOS Enterprise 5.2sp1.
- Controller Name: centos
- Domain Name: friends.cu
- Controller IP: 10.10.10.60
- ---------------
- Debian version: wheezy.
- Name of the team: debian7
- IP adress: Using DHCP
We configure the LDAP client
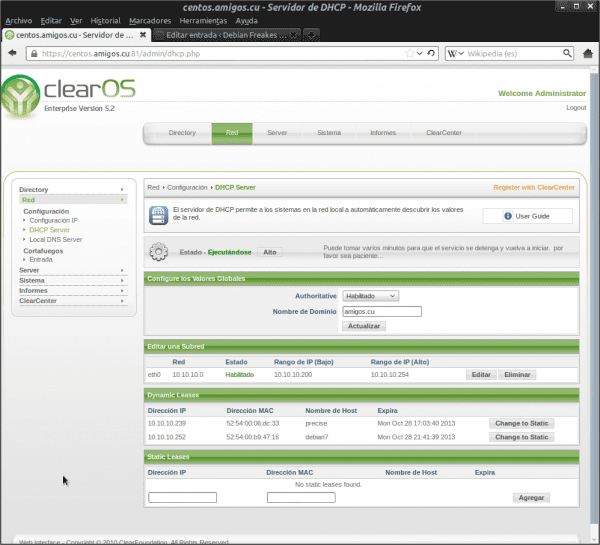
We must have the OpenLDAP server data on hand, which we obtain from the ClearOS administration web interface in «Directory »->« Domain and LDAP«:
LDAP Base DN: dc = friends, dc = cu LDAP Bind DN: cn = manager, cn = internal, dc = friends, dc = cu LDAP Bind Password: kLGD + Mj + ZTWzkD8W
We install necessary packages. As the user root we execute:
aptitude install libnss-ldap nscd finger
Notice that the output of the previous command also includes the package libpam-ldap. During the installation process they will ask us several questions, which we must answer correctly. The answers would be in the case of this example:
LDAP server URI: ldap: //10.10.10.60 The distinguished name (DN) of the search base: dc = friends, dc = cu LDAP version to use: 3 LDAP account for root: cn = manager, cn = internal, dc = friends, dc = cu Password for the root LDAP account: kLGD + Mj + ZTWzkD8W Now he announces that the file /etc/nsswitch.conf it is not managed automatically, and that we must modify it manually. Do you want to allow the LDAP administrator account to behave as the local administrator ?: Si Is a user required to access the LDAP database ?: No LDAP administrator account: cn = manager, cn = internal, dc = friends, dc = cu Password for the root LDAP account: kLGD + Mj + ZTWzkD8W
If we are wrong in the previous answers, we execute as the user root:
dpkg-reconfigure libnss-ldap dpkg-reconfigure libpam-ldap
And we adequately answer the same questions asked before, with the only addition of the question:
Local encryption algorithm to use for passwords: md5
Eye when replying because the default value offered to us is Crypt, and we must declare that it is md5. It also shows us a screen in console mode with the output of the command pam-auth-update executed as root, which we must accept.
We modify the file /etc/nsswitch.conf, and we leave it with the following content:
# /etc/nsswitch.conf # # Example configuration of GNU Name Service Switch functionality. # If you have the `glibc-doc-reference 'and` info' packages installed, try: # `info libc" Name Service Switch "'for information about this file. passwd: compat ldap group: compat ldap shadow: compat ldap hosts: files mdns4_minimal [NOTFOUND = return] dns mdns4 networks: files protocols: db files services: db files ethers: db files rpc: db files netgroup: nis
We modify the file /etc/pam.d/common-session to automatically create user folders when logging in in case they don't exist:
[----] session required pam_mkhomedir.so skel = / etc / skel / umask = 0022 ### The above line must be included BEFORE # here are the per-package modules (the "Primary" block) [----]
We execute in a console as the user root, Just to Check, pam-auth-update:
We restart the service nscd, and we do checks:
: ~ # service nscd restart [ok] Restarting Name Service Cache Daemon: nscd. : ~ # finger strides Login: strides Name: Strides El Rey Directory: / home / strides Shell: / bin / bash Never logged in. No mail. No Plan. : ~ # getent passwd strides Strides: x: 1006: 63000: Strides El Rey: / home / strides: / bin / bash: ~ # getent passwd legolas legolas: x: 1004: 63000: Legolas The Elf: / home / legolas: / bin / bash
We modify the re-connection policy with the OpenLDAP server.
We edit as the user root and very carefully, the file /etc/libnss-ldap.conf. We look for the word «hard«. We remove the comment from the line #bind_policy hard and we leave it like this: bind_policy soft.
The same change mentioned before, we make it in the file /etc/pam_ldap.conf.
The above modifications eliminate a number of LDAP-related messages during boot and at the same time streamline it (the boot process).
We restart our Wheezy because the changes made are essential:
: ~ # reboot
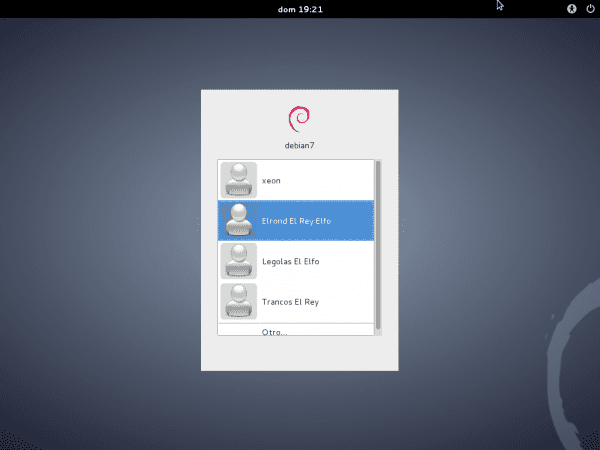
After rebooting, we can log in with any user registered in ClearOS OpenLDAP.
We recommend that then the following is done:
- Make external users a member of the same groups as the local user created during the installation of our Debian.
- Using the command visudo, executed as root, give the necessary execution permissions to external users.
- Create a bookmark with the address https://centos.amigos.cu:81/?user en Iceweasel, to have access to the personal page in ClearOS, where we can change our personal password.
- Install the OpenSSH-Server -if it is not selected when installing the system- to be able to access our Debian from another computer.
Configuration files created and / or modified
The LDAP topic requires a lot of study, patience and experience. The last one I don't have. We highly recommend that packages libnss-ldap y libpam-ldap, in the case of a manual modification that causes the authentication to stop working, be reconfigured correctly using the command dpkg-reconfigure, that is generated by DEBCONF.
The related configuration files are:
- /etc/libnss-ldap.conf
- /etc/libnss-ldap.secret
- /etc/pam_ldap.conf
- /etc/pam_ldap.secret
- /etc/nsswitch.conf
- /etc/pam.d/common-sessions
The /etc/ldap/ldap.conf file
We haven't touched this file yet. However, the authentication works correctly due to the configuration of the files listed above and the PAM configuration generated by pam-auth-update. However, we must also configure it properly. It makes it easy to use commands like ldapsearch, provided by the package ldap-utils. The minimum configuration would be:
BASE dc = friends, dc = cu URI ldap: //10.10.10.60 SIZELIMIT 12 TIMELIMIT 15 DEREF never
We can check if the OpenLDAP server of ClearOS works correctly, if we execute in a console:
ldapsearch -d 5 -L "(objectclass = *)"
The command output is copious. 🙂
I love Debian! And the activity is over for today, Friends !!!

Excellent article, direct to my tips drawer
Thanks for commenting Elav… more fuel 🙂 and wait for the next one that tries to authenticate using sssd against an OpenLDAP.
Thank you very much for sharing, looking forward to the other delivery 😀
Thanks for comment !!!. It seems that the mental inertia of authenticating against a Microsoft domain is strong. Hence the few comments. That is why I write about the true free alternatives. If you look at it carefully, they are easier to implement. A bit conceptual at first. But nothing.