General index of the series: Computer Networks for SMEs: Introduction
This article is the continuation and last of the miniseries:
- Squid + PAM Authentication on CentOS 7.
- Local user and group management
- Authoritative DNS Server NSD + Shorewall
- Prosody IM and local users
Hello friends and friends!
The Enthusiasts they want to have their own mail server. They do not want to use servers where "Privacy" is between question marks. The person in charge of implementing the service on your small server is not a specialist in the subject and will initially try to install the core of a future and complete mail server. Is that the "equations" to make a Full Mailserver are a bit difficult to understand and apply. 😉
Margin annotations
- It is necessary to be clear about which functions each program involved in a Mailserver performs. As an initial guide we give a series of useful links with the stated purpose of visiting them.
- Implementing a Complete Mail Service manually and from scratch is a tiring process, unless you are one of the "Chosen" who perform this type of task daily. A Mail Server is formed -in a general way- by various programs that separately handle SMTP, POP / IMAP, Local Storage of Messages, tasks related to the treatment of the SPAM, Antivirus, etc. ALL of these programs must communicate with each other correctly.
- There is no one-size-fits-all or "best practice" on how to manage users; where and how to store messages, or how to make all the components work as a single whole.
- The assembly and tuning of a Mailserver tends to be obnoxious in matters such as permissions and file owners, choosing which user will be in charge of a certain process, and in small errors made in some esoteric configuration file.
- Unless you know very well what you are doing, the end result will be an insecure or slightly non-functional Mail Server. That at the end of the implementation It does not work, it will be possibly the lesser of the evils.
- We can find on the Internet a good amount of recipes on how to make a Mail Server. One of the most complete -in my very personal opinion- is the one offered by the author ivar abrahamsen in its thirteenth edition of January 2017 «How to set up a mail server on a GNU / Linux system«.
- We also recommend reading the article «A Mailserver on Ubuntu 14.04: Postfix, Dovecot, MySQL«, or «A Mailserver on Ubuntu 16.04: Postfix, Dovecot, MySQL«.
- True. The best documentation in this regard can be found in English.
- Although we never make a Mailserver faithfully guided by the How to ... mentioned in the previous paragraph, the mere fact of following it step by step will give us a very good idea of what we will be facing.
- If you want to have a complete Mailserver in just a few steps, you can download the image iRedOS-0.6.0-CentOS-5.5-i386.iso, or look for a more modern one, be it iRedOS or iRedMail. It is the way that I personally recommend.
We are going to install and configure:
- Postfix as a server Mail Ttransport Agent (SMTP).
- Dovecot as POP - IMAP server.
- Certificates for connections through TLS.
- Squirrelmail as a web interface for users.
- DNS record relative to «Sender Policy Framework»Or SPF.
- Module generation Diffie Hellman Group to increase the security of SSL certificates.
It remains to be done:
At least the following services would remain to be implemented:
- postgrey: Postfix server policies for Gray Lists and reject Junk Mail.
- amavisd-new: script that creates an interface between the MTA, and virus scanners and content filters.
- Clamav Antivirus: antivirus suite
- SpamAssassin: extract Junk Mail
- Razor (pyzor): SPAM capture through a distributed and collaborative network. The Vipul Razor network maintains an updated catalog of the propagation of junk mail or SPAM.
- DNS record "DomainKeys Identified Mail" or DKIM.
The packages postgrey, amavisd-new, clamav, spamassassin, razor y pyzor They are found in the program repositories. We will also find the program openkim.
- The correct declaration of the DNS records "SPF" and "DKIM" is essential if we do not want our mail server just put into operation, to be declared undesirable or a producer of SPAM or Junk Mail, by other mail services such as gmail, Yahoo, Hotmail, etc.
Initial checks
Remember that this article is a continuation of others that begin in Squid + PAM Authentication on CentOS 7.
Ens32 LAN interface connected to the Internal Network
[root @ linuxbox ~] # nano / etc / sysconfig / network-scripts / ifcfg-ens32
DEVICE=ens32
ONBOOT=yes
BOOTPROTO=static
HWADDR=00:0c:29:da:a3:e7
NM_CONTROLLED=no
IPADDR=192.168.10.5
NETMASK=255.255.255.0
GATEWAY=192.168.10.1
DOMAIN=desdelinux.fan DNS1=127.0.0.1
ZONE = public
[root @ linuxbox ~] # ifdown ens32 && ifup ens32
Ens34 WAN interface connected to the Internet
[root @ linuxbox ~] # nano / etc / sysconfig / network-scripts / ifcfg-ens34
DEVICE=ens34 ONBOOT=yes BOOTPROTO=static HWADDR=00:0c:29:da:a3:e7 NM_CONTROLLED=no IPADDR=172.16.10.10 NETMASK=255.255.255.0 # The ADSL Router is connected to # this interface with # the following address IP GATEWAY=172.16.10.1 DOMAIN=desdelinux.fan DNS1=127.0.0.1
ZONE = external
DNS resolution from the LAN
[root@linuxbox ~]# cat /etc/resolv.conf search desdelinux.fan nameserver 127.0.0.1 nameserver 172.16.10.30 [root@linuxbox ~]# host mail .desdelinux.fan is an alias for linuxbox.desdelinux.fan. linuxbox.desdelinux.fan has address 192.168.10.5 linuxbox.desdelinux.fan mail is handled by 1 mail.desdelinux.fan. [root@linuxbox ~]# hostmail.desdelinux.fan .desdelinux.fan is an alias for linuxbox.desdelinux.fan. linuxbox.desdelinux.fan has address 192.168.10.5 linuxbox.desdelinux.fan mail is handled by 1 mail.desdelinux.fan.
DNS resolution from the Internet
buzz@sysadmin:~$hostmail.desdelinux.fan 172.16.10.30 Using domain server: Name: 172.16.10.30 Address: 172.16.10.30#53 Aliases: mail.desdelinux.fan is an alias for desdelinux.fan. desdelinux.fan has address 172.16.10.10 desdelinux.fan mail is handled by 10 mail.desdelinux.fan.
Problems resolving hostname locally «desdelinux.fan"
If you have problems resolving the hostname «desdelinux.fan" from the LAN, try commenting out the file line /etc/dnsmasq.conf where it is declared local=/desdelinux.fan/. Afterwards, restart the Dnsmasq.
[root @ linuxbox ~] # nano /etc/dnsmasq.conf # Comment the line below: # local=/desdelinux.fan/ [root @ linuxbox ~] # service dnsmasq restart Redirecting to / bin / systemctl restart dnsmasq.service [root @ linuxbox ~] # service dnsmasq status [root@linuxbox ~]# host desdelinux.fan desdelinux.fan has address 172.16.10.10 desdelinux.fan mail is handled by 10 mail.desdelinux.fan.
Postfix and Dovecot
The very extensive documentation of the Postfix and Dovecot can be found at:
[root @ linuxbox ~] # ls /usr/share/doc/postfix-2.10.1/ bounce.cf.default LICENSE README-Postfix-SASL-RedHat.txt COMPATIBILITY main.cf.default TLS_ACKNOWLEDGEMENTS examples README_FILES TLS_LICENSE [root @ linuxbox ~] # ls /usr/share/doc/dovecot-2.2.10/ AUTHORS COPYING.MIT dovecot-openssl.cnf NEWS wiki COPYING ChangeLog example-config README COPYING.LGPL documentation.txt mkcert.sh solr-schema.xml
In CentOS 7, the Postfix MTA is installed by default when we choose the Infrastructure Server option. We must check that the SELinux context allows writing to Potfix in the local message queue:
[root @ linuxbox ~] # getsebool -a | grep postfix
postfix_local_write_mail_spool -> on
Modifications in the FirewallD
Using the graphical interface to configure the FirewallD, we must ensure that the following services and ports are enabled for each Zone:
# ------------------------------------------------- ----- # Fixes in FirewallD # ------------------------------------------------- ----- # firewall # Public zone: http, https, imap, pop3, smtp services # Public zone: ports 80, 443, 143, 110, 25 # External zone: http, https, imap, pop3s, smtp services # External zone: ports 80, 443, 143, 995, 25
We install Dovecot and necessary programs
[root @ linuxbox ~] # yum install dovecot mod_ssl procmail telnet
Minimum Dovecot configuration
[root @ linuxbox ~] # nano /etc/dovecot/dovecot.conf protocols =imap pop3 lmtp listen =*, :: login_greeting = Dovecot is ready!
We explicitly disable Dovecot's plaintext authentication:
[root @ linuxbox ~] # nano /etc/dovecot/conf.d/10-auth.conf
disable_plaintext_auth = yes
We declare the Group with the necessary privileges to interact with the Dovecot, and the location of the messages:
[root @ linuxbox ~] # nano /etc/dovecot/conf.d/10-mail.conf mail_location = mbox: ~ / mail: INBOX = / var / mail /% u mail_privileged_group = mail mail_access_groups = mail
Certificates for the Dovecot
Dovecot automatically generates your test certificates based on the data in the file /etc/pki/dovecot/dovecot-openssl.cnf. To have new certificates generated according to our requirements, we must perform the following steps:
[root @ linuxbox ~] # cd / etc / pki / dovecot / [root @ linuxbox dovecot] # nano dovecot-openssl.cnf [ req ] default_bits = 1024 encrypt_key = yes distinguished_name = req_dn x509_extensions = cert_type prompt = no [ req_dn ] # country (2 letter code) C=CU # State or Province Name (full name) ST=Cuba # Locality Name (eg. city ) L=Havana # Organization (eg. company) O=DesdeLinux.Fan # Organizational Unit Name (eg. section) OU=Enthusiasts # Common Name (*.example.com is also possible) CN=*.desdelinux.fan # Email contact emailAddress=buzz@desdelinux.fan [ cert_type ] nsCertType = server
We eliminate test certificates
[root @ linuxbox dovecot] # rm certs / dovecot.pem rm: delete the regular file "certs / dovecot.pem"? (y / n) y [root @ linuxbox dovecot] # rm private / dovecot.pem rm: delete the regular file "private / dovecot.pem"? (y / n) y
We copy and execute the script mkcert.sh from the documentation directory
[root @ linuxbox dovecot] # cp /usr/share/doc/dovecot-2.2.10/mkcert.sh. [root @ linuxbox dovecot] # bash mkcert.sh Generating a 1024 bit RSA private key ......++++++ ................++++++ writing new private key to '/etc/ pki/dovecot/private/dovecot.pem' ----- subject= /C=CU/ST=Cuba/L=Havana/O=DesdeLinux.Fan/OU=Enthusiasts/CN=*.desdelinux.fan/emailAddress=buzz@desdelinux.fan SHA1 Fingerprint=5F:4A:0C:44:EC:EC:EF:95:73:3E:1E:37:D5:05:F8:23:7E:E1:A4:5A [root @ linuxbox dovecot] # ls -l certs / total 4 -rw -------. 1 root root 1029 May 22 16:08 dovecot.pem [root @ linuxbox dovecot] # ls -l private / total 4 -rw -------. 1 root root 916 May 22 16:08 dovecot.pem [root @ linuxbox dovecot] # service dovecot restart [root @ linuxbox dovecot] # service dovecot status
Certificates for Postfix
[root@linuxbox ~]# cd /etc/pki/tls/ [root@linuxbox tls]# openssl req -sha256 -x509 -nodes -newkey rsa:4096 -days 1825 \ -out certs/desdelinux.fan.crt -keyout private/desdelinux.fan.key Generating a 4096 bit RSA private key .........++ ..++ writing new private key to 'private/domain.tld.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CU State or Province Name (full name) []:Cuba Locality Name (eg, city) [Default City]:Havana Organization Name (eg, company) [ Default Company Ltd]:DesdeLinux.Fan Organizational Unit Name (eg, section) []:Enthusiasts Common Name (eg, your name or your server's hostname) []:desdelinux.fan Email Address []:buzz@desdelinux.fan
Minimal Postfix configuration
We add to the end of the file / etc / aliases following:
root: buzz
For the changes to take effect we execute the following command:
[root @ linuxbox ~] # newaliases
The Postifx configuration can be done by directly editing the file /etc/postfix/main.cf or by command postconf -e taking care that all the parameter we want to modify or add is reflected in a single line of the console:
- Each one must declare the options they understand and need!.
[root@linuxbox ~]# postconf -e 'myhostname = desdelinux.fan' [root@linuxbox ~]# postconf -e 'mydomain = desdelinux.fan' [root @ linuxbox ~] # postconf -e 'myorigin = $ mydomain' [root @ linuxbox ~] # postconf -e 'inet_interfaces = all' [root @ linuxbox ~] # postconf -e 'mydestination = $ myhostname, localhost. $ mydomain, localhost, $ mydomain, mail. $ mydomain, www. $ mydomain, ftp. $ mydomain' [root @ linuxbox ~] # postconf -e 'mynetworks = 192.168.10.0/24, 172.16.10.0/24, 127.0.0.0/8' [root @ linuxbox ~] # postconf -e 'mailbox_command = / usr / bin / procmail -a "$ EXTENSION"' [root @ linuxbox ~] # postconf -e 'smtpd_banner = $ myhostname ESMTP $ mail_name ($ mail_version)'
We add to the end of the file /etc/postfix/main.cf the options given below. To know the meaning of each of them, we recommend reading the accompanying documentation.
bif = no
append_dot_mydomain = no
delay_warning_time = 4h
readme_directory = no
smtpd_tls_cert_file=/etc/pki/certs/desdelinux.fan.crt
smtpd_tls_key_file=/etc/pki/private/desdelinux.fan.key
smtpd_use_tls = yes
smtpd_tls_session_cache_database = btree: $ {data_directory} / smtpd_scache
smtp_tls_session_cache_database = btree: $ {data_directory} / smtp_scache
smtpd_relay_restrictions = permit_mynetworks permit_sasl_authenticated defer_unauth_destination
# Maximum mailbox size 1024 megabytes = 1 g and g
mailbox_size_limit = 1073741824
recipient_delimiter=+
maximal_queue_lifetime = 7d
header_checks = regexp: / etc / postfix / header_checks
body_checks = regexp: / etc / postfix / body_checks
# Accounts that send a copy of incoming mail to another account
recipient_bcc_maps = hash: / etc / postfix / accounts_ forwarding_copy
The following lines are important to determine who can send mail and relay to other servers, so that we do not accidentally configure an "open relay" that allows unauthenticated users to send mail. We must consult the Postfix help pages to understand what each option means.
- Each one must declare the options they understand and need!.
smtpd_helo_restrictions = permit_mynetworks,
warn_if_reject reject_non_fqdn_hostname,
reject_invalid_hostname,
allow
smtpd_sender_restrictions = permit_sasl_authenticated,
permit_mynetworks,
warn_if_reject reject_non_fqdn_sender,
reject_unknown_sender_domain,
reject_unauth_pipelining,
allow
smtpd_client_restrictions = reject_rbl_client sbl.spamhaus.org,
reject_rbl_client blackholes.easynet.nl
# NOTE: The option "check_policy_service inet: 127.0.0.1: 10023"
# enables the Postgrey program, and we should not include it
# otherwise we are going to use Postgrey
smtpd_recipient_restrictions = reject_unauth_pipelining,
permit_mynetworks,
permit_sasl_authenticated,
reject_non_fqdn_recipient,
reject_unknown_recipient_domain,
reject_unauth_destination,
check_policy_service inet: 127.0.0.1: 10023,
allow
smtpd_data_restrictions = reject_unauth_pipelining
smtpd_relay_restrictions = reject_unauth_pipelining,
permit_mynetworks,
permit_sasl_authenticated,
reject_non_fqdn_recipient,
reject_unknown_recipient_domain,
reject_unauth_destination,
check_policy_service inet: 127.0.0.1: 10023,
allow
smtpd_helo_required = yes
smtpd_delay_reject = yes
disable_vrfy_command = yes
We create the files / etc / postfix / body_checks y / etc / postfix / accounts_forwarding_copy, and we modify the file / etc / postfix / header_checks.
- Each one must declare the options they understand and need!.
[root @ linuxbox ~] # nano / etc / postfix / body_checks
# If this file is modified, it is not necessary # to run postmap # To test the rules, run as root: # postmap -q 'super new v1agra' regexp: / etc / postfix / body_checks
# Should return: # REJECT Rule # 2 Anti Spam Message Body
/ viagra / REJECT Rule # 1 Anti Spam of the message body
/ super new v [i1] agra / REJECT Rule # 2 Anti Spam of the message body
[root @ linuxbox ~] # nano / etc / postfix / accounts_forwarding_copy
# After modifying, you must execute: # postmap / etc / postfix / accounts_ forwarding_copy
# and the file is created or measured: # /etc/postfix/accounts_forwarding_copy.db
# ------------------------------------------ # ONE account to forward one BCC copy # BCC = Black Carbon Copy # Example: # webadmin@desdelinux.fan buzz@desdelinux.fan
[root @ linuxbox ~] # postmap / etc / postfix / accounts_ forwarding_copy
[root @ linuxbox ~] # nano / etc / postfix / header_checks
# Add at the end of the file # DOES NOT REQUIRE Postmap as they are Regular Expressions
/ ^ Subject: =? Big5? / REJECT Chinese encoding not accepted by this server
/ ^ Subject: =? EUC-KR? / REJECT Korean encoding not allowed by this server
/ ^ Subject: ADV: / REJECT Advertisements not accepted by this server
/^From:.*\@.*\.cn/ REJECT Sorry, Chinese mail not allowed here
/^From:.*\@.*\.kr/ REJECT Sorry, Korean mail not allowed here
/^From:.*\@.*\.tr/ REJECT Sorry, Turkish mail not allowed here
/^From:.*\@.*\.ro/ REJECT Sorry, Romanian mail not allowed here
/^(Received|Message-Id|X-(Mailer|Sender)):.*\b(AutoMail|E-Broadcaster|Emailer Platinum | Thunder Server | eMarksman | Extractor | e-Merge | from stealth [^.] | Global Messenger | GroupMaster | Mailcast | MailKing | Match10 | MassE-Mail | massmail \ .pl | News Breaker | Powermailer | Quick Shot | Ready Aim Fire | WindoZ | WorldMerge | Yourdora | Lite) \ b / REJECT No mass mailers allowed.
/ ^ From: "spammer / REJECT
/ ^ From: "spam / REJECT
/^Subject:.*viagra/ DISCARD
# Dangerous extensions
/name=[^> Iluminación*\.(bat|cmd|exe|com|pif|reg|scr|vb|vbe|vbs)/ REJECT REJECT We do not accept attachments with these extensions
We check the syntax, restart Apache and Postifx, and enable and start Dovecot
[root @ linuxbox ~] # postfix check [root @ linuxbox ~] # [root @ linuxbox ~] # systemctl restart httpd [root @ linuxbox ~] # systemctl status httpd [root @ linuxbox ~] # systemctl restart postfix [root @ linuxbox ~] # systemctl status postfix [root @ linuxbox ~] # systemctl status dovecot ● dovecot.service - Dovecot IMAP / POP3 email server Loaded: loaded (/usr/lib/systemd/system/dovecot.service; disabled; vendor preset: disabled) Active: inactive (dead) [root @ linuxbox ~] # systemctl enable dovecot [root @ linuxbox ~] # systemctl start dovecot [root @ linuxbox ~] # systemctl restart dovecot [root @ linuxbox ~] # systemctl status dovecot
Console-level checks
- It is very important before continuing with the installation and configuration of other programs, to make the minimum necessary checks of the SMTP and POP services.
Local from the server itself
We send an email to the local user Legolas.
[root @ linuxbox ~] # echo "Hello. This is a test message" | mail -s "Test" legolas
We check the mailbox of Legolas.
[root @ linuxbox ~] # openssl s_client -crlf -connect 127.0.0.1:110 -starttls pop3
After the message Dovecot is Ready! we proceed:
--- + OK Dovecot is Ready! USER legolas +OK PASS legolas +OK Logged in. STAT +OK 1 559 LIST +OK 1 messages: 1 559 . RETR 1 +OK 559 octets Return-Path:desdelinux.fan> X-Original-To: legolas Delivered-To: legolas@desdelinux.fan Received: by desdelinux.fan (Postfix, from userid 0) id 7EA22C11FC57; Mon, 22 May 2017 10:47:10 -0400 (EDT) Date: Mon, 22 May 2017 10:47:10 -0400 To: legolas@desdelinux.fan Subject: Test User-Agent: Heirloom mailx 12.5 7/5/10 MIME-Version: 1.0 Content-Type: text/plain; charset=us-ascii Content-Transfer-Encoding: 7bit Message-Id: <20170522144710.7EA22C11FC57@desdelinux.fan> From: root@desdelinux.fan (root) Hello. This is a test message . QUIT DONE [root @ linuxbox ~] #
Remotes from a computer on the LAN
Let's send another message to Legolas from another computer on the LAN. Note that TLS security is NOT strictly necessary within the SME Network.
buzz @ sysadmin: ~ $ sendemail -f buzz@deslinux.fan \ -t legolas@desdelinux.fan\ -u "Hello" \ -m "Greetings Legolas from your friend Buzz" \ -s email.desdelinux.fan -o tls=no May 22 10:53:08 sysadmin sendemail [5866]: Email was sent successfully!
If we try to connect through telnet From a host on the LAN - or from the Internet, of course - to the Dovecot, the following will happen because we disable plaintext authentication:
buzz@sysadmin:~$ telnet mail.desdelinux.fan 110Trying 192.168.10.5...
Connected to linuxbox.desdelinux.fan. Escape character is '^]'. +OK Dovecot is Ready! user legolas
-ERR [AUTH] Plaintext authentication disallowed on non-secure (SSL / TLS) connections.
quit + OK Logging out Connection closed by foreign host.
buzz @ sysadmin: ~ $
We must do it through openssl. The complete output of the command would be:
buzz@sysadmin:~$ openssl s_client -crlf -connect mail.desdelinux.fan:110 -starttls pop3 CONNECTED (00000003) depth=0 C = CU, ST = Cuba, L = Havana, O = DesdeLinux.Fan, OU = Enthusiasts, CN = *.desdelinux.fan, emailAddress = buzz@desdelinux.fan verify error: num = 18: self signed certificate verify return: 1 depth=0 C = CU, ST = Cuba, L = Havana, O = DesdeLinux.Fan, OU = Enthusiasts, CN = *.desdelinux.fan, emailAddress = buzz@desdelinux.fan verify return:1 --- Certificate chain 0 s:/C=CU/ST=Cuba/L=Havana/O=DesdeLinux.Fan/OU=Enthusiasts/CN=*.desdelinux.fan/emailAddress=buzz@desdelinux.fan i:/C=CU/ST=Cuba/L=Havana/O=DesdeLinux.Fan/OU=Enthusiasts/CN=*.desdelinux.fan/emailAddress=buzz@desdelinux.fan --- Server certificate -----BEGIN CERTIFICATE----- MIICyzCCAjSgAwIBAgIJAKUHI/2ZD+MeMA0GCSqGSIb3DQEBBQUAMIGbMQswCQYD VQQGEwJDVTENMAsGA1UECBMEQ3ViYTEPMA0GA1UEBxMGSGFiYW5hMRcwFQYDVQQK Ew5EZXNkZUxpbnV4LkZhbjEUMBIGA1UECxMLRW50dXNpYXN0YXMxGTAXBgNVBAMU ECouZGVzZGVsaW51eC5mYW4xIjAgBgkqhkiG9w0BCQEWE2J1enpAZGVzZGVsaW51 eC5mYW4wHhcNMTcwNTIyMjAwODEwWhcNMTgwNTIyMjAwODEwWjCBmzELMAkGA1UE BhMCQ1UxDTALBgNVBAgTBEN1YmExDzANBgNVBAcTBkhhYmFuYTEXMBUGA1UEChMO RGVzZGVMaW51eC5GYW4xFDASBgNVBAsTC0VudHVzaWFzdGFzMRkwFwYDVQQDFBAq LmRlc2RlbGludXguZmFuMSIwIAYJKoZIhvcNAQkBFhNidXp6QGRlc2RlbGludXgu ZmFuMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC7wckAiNNfYSz5hdePzKuZ m2MMuhGDvwrDSPDEcVutznbZSgJ9bvTo445TR+Bnk+OZ80lujS2hP+nBmqxzJbpc XR7E9eWIXxr4fP4HpRrCA8NxlthEsapVMSHW+lnPBqF2b/Bt2eYyR7gJhtlP6gRG V57MmgL8BdYAJLvxqxDIxQIDAQABoxUwEzARBglghkgBhvhCAQEEBAMCBkAwDQYJ KoZIhvcNAQEFBQADgYEAAuYU1nIXTbXtddW+QkLskum7ESryHZonKOCelfn2vnRl 8oAgHg7Hbtg/e6sR/W9m3DObP5DEp3lolKKIKor7ugxtfA4PBtmgizddfDKKMDql LT+MV5/DP1pjQbxTsaLlZfveNxfLRHkQY13asePy4fYJFOIZ4OojDEGQ6/VQBI8= -----END CERTIFICATE----- subject=/C=CU/ST=Cuba/L=Habana/O=DesdeLinux.Fan/OU=Enthusiasts/CN=*.desdelinux.fan/emailAddress=buzz@desdelinux.fan issuer=/C=CU/ST=Cuba/L=Havana/O=DesdeLinux.Fan/OU=Enthusiasts/CN=*.desdelinux.fan/emailAddress=buzz@desdelinux.fan --- No client certificate CA names sent Server Temp Key: ECDH, secp384r1, 384 bits --- SSL handshake has read 1342 bytes and written 411 bytes --- New, TLSv1/SSLv3, Cipher is ECDHE-RSA-AES256 -GCM-SHA384 Server public key is 1024 bit Secure Renegotiation IS supported Compression: NONE Expansion: NONE SSL-Session: Protocol: TLSv1.2 Cipher: ECDHE-RSA-AES256-GCM-SHA384 Session-ID: C745B4A0236204E16234CB15DC9CDBC3D084125FF5989F5DB 6C5295BF4E2D73A Session-ID-ctx : Master-Key: 1904D204C564B76361CEA50373F8879AF793AF7D7506C04473777F6F3503A9FD919CD1F837BC67BFF29E309F352526F5 Key-Arg: None Krb5 Principal: None PSK identity: None PSK identity hint: None TLS session ticket lifetime hint: 300 (seconds) TLS session ticket: 0000 - 4e 3a f8 29 7a 4f 63 72-ee f7 a6 4f fc ec 7e 1c N:.)zOcr...O..~. 0010 - 2c d4 be a8 be 92 2e ae-98 7e 87 6d 45 c5 17 a8 ,.....~.mE... 0020 - db 3a 86 80 df 8b dc 8d-f8 1f 68 6e db a7 e3 86 .:.......hn.... 0030 - 08 35 e5 eb 98 b8 a4 98-68 b1 ea f7 72 f7 c1 79 .5......h...r ..y 0040 - 89 4a 28 e3 85 a4 8b da-e9 7a 29 c7 77 bf 22 0d .J(......z).w.". 0050 - bd 5c f6 61 8c a1 14 bd-cb 31 27 66 7a dc 51 28 .\.a.....1'fz.Q( 0060 - b7 of 35 bd 2b 0f d4 ec-d3 e0 14 c8 65 03 b1 35 ..5.+.... ...e..5 0070 - 38 34 f8 de 48 da ae 31-90 bd f6 b0 e6 9c cf 19 84..H..1........ 0080 - f5 42 56 13 88 b0 8c db-aa ee 5a d7 1b 2c dd 71 .BV.......Z..,.q 0090 - 7a f1 03 70 90 94 c9 0a-62 e5 0f 9c bf dc 3c a0 z..p.. ..b.....<. Start Time: 1495484262 Timeout: 300 (sec) Verify return code: 18 (self signed certificate) --- + OK Dovecot is Ready! USER legolas + OK PASS legolas + OK Logged in. LIST + OK 1 messages: 1 1021. BACK 1 +OK 1021 octets Return-Path: X-Original-To: legolas@desdelinux.fan Delivered-To: legolas@desdelinux.fan Received: from sysadmin.desdelinux.fan (gateway [172.16.10.1]) by desdelinux.fan (Postfix) with ESMTP id 51886C11E8C0 fordesdelinux.fan>; Mon, 22 May 2017 15:09:11 -0400 (EDT) Message-ID: <919362.931369932-sendEmail@sysadmin> From: "buzz@deslinux.fan" To: "legolas@desdelinux.fan"desdelinux.fan> Subject: Hello Date: Mon, 22 May 2017 19:09:11 +0000 X-Mailer: sendEmail-1.56 MIME-Version: 1.0 Content-Type: multipart/related; boundary="----MIME delimiter for sendEmail-365707.724894495" This is a multi-part message in MIME format. To properly display this message you need a MIME-Version 1.0 compliant Email program. ------MIME delimiter for sendEmail-365707.724894495 Content-Type: text/plain; charset="iso-8859-1" Content-Transfer-Encoding: 7bit Greetings Legolas from your friend Buzz ------MIME delimiter for sendEmail-365707.724894495-- . QUIT + OK Logging out. closed buzz @ sysadmin: ~ $
Squirrelmail
Squirrelmail is a web client written entirely in PHP. It includes native PHP support for the IMAP and SMTP protocols, and provides maximum compatibility with the different browsers in use. It runs correctly on any IMAP server. It has all the functionality that you need from an email client including MIME support, address book and folder management.
[root @ linuxbox ~] # yum install squirrelmail
[root @ linuxbox ~] # service httpd restart
[root @ linuxbox ~] # nano /etc/squirrelmail/config.php
$domain = 'desdelinux.fan';
$imapServerAddress = 'mail.desdelinux.fan';
$ imapPort = 143;
$smtpServerAddress = 'desdelinux.fan';
[root @ linuxbox ~] # service httpd reload
DNS Send Policy Framenwork or SPF record
In the article Authoritative DNS Server NSD + Shorewall We saw that the Zone «desdelinux.fan» was configured as follows:
root@ns:~# nano /etc/nsd/desdelinux.fan.zone $ORIGIN desdelinux.fan. $TTL 3H @ IN SOA nos.desdelinux.fan. root.desdelinux.fan. ( 1 ; serial 1D ; refresh 1H ; retry 1W ; expire 3H ) ; minimum or ; Negative caching time to live ; @ IN NS ns.desdelinux.fan. @ IN MX 10 email.desdelinux.fan. @ IN TXT "v=spf1 a:mail.desdelinux.fan -all" ; ; Registration to resolve dig queries desdelinux.fan @ IN A 172.16.10.10 ; ns IN A 172.16.10.30 mail IN CNAME desdelinux.fan. chat IN CNAME desdelinux.fan. www IN CNAME desdelinux.fan. ; ; SRV records related to XMPP _xmpp-server._tcp IN SRV 0 0 5269 desdelinux.fan. _xmpp-client._tcp IN SRV 0 0 5222 desdelinux.fan. _jabber._tcp IN SRV 0 0 5269 desdelinux.fan.
In it the registry is declared:
@ IN TXT "v=spf1 a:mail.desdelinux.fan -all"
To have the same parameter configured for the SME Network or LAN, we must modify the Dnsmasq configuration file as follows:
# TXT records. We can also declare an SPF record txt-record=desdelinux.fan,"v=spf1 a:mail.desdelinux.fan -all"
Then we restart the service:
[root @ linuxbox ~] # service dnsmasq restart [root@linuxbox ~]# service dnsmasq status [root@linuxbox ~]# host -t TXT mail.desdelinux.fan mail.desdelinux.fan is an alias for desdelinux.fan. desdelinux.fan descriptive text "v=spf1 a:mail.desdelinux.fan -all"
Self Signed Certificates and Apache or httpd
Even if your browser tells you that «The owner of .desdelinux.fan You have configured your website incorrectly. To prevent your information from being stolen, Firefox has not connected to this website ”, the previously generated certificate IT IS VALID, and will allow the credentials between the client and the server to travel encrypted, after we accept the certificate.
If you wish, and as a way to unify the certificates, you can declare for Apache the same certificates that you declared for Postfix, which is correct.
[root @ linuxbox ~] # nano /etc/httpd/conf.d/ssl.conf
SSLCertificateFile /etc/pki/tls/certs/desdelinux.fan.crt
SSLCertificateKeyFile /etc/pki/tls/private/desdelinux.fan.key
[root @ linuxbox ~] # service httpd restart
[root @ linuxbox ~] # service httpd status
Diffie-Hellman Group
The issue of Security becomes more difficult every day on the Internet. One of the most common attacks on connections SSL, is the Logjam and to defend against it it is necessary to add non-standard parameters to the SSL configuration. For this there is the RFC-3526 «More Modular Exponential (MODP) Diffie-Hellman groups for Internet Key Exchange (IKE)«.
[root @ linuxbox ~] # cd / etc / pki / tls /
[root @ linuxbox tls] # openssl dhparam -out private / dhparams.pem 2048
[root @ linuxbox tls] # chmod 600 private / dhparams.pem
According to the version of Apache that we have installed, we will use the Diffie-Helman Group from the file /etc/pki/tls/dhparams.pem. If it is a version 2.4.8 or later, then we will have to add to the file /etc/httpd/conf.d/ssl.conf the following line:
SSLOpenSSLConfCmd DHParameters "/etc/pki/tls/private/dhparams.pem"
The version of Apache that we are using is:
[root @ linuxbox tls] # yum info httpd
Loaded plugins: fastestmirror, langpacks Loading mirror speeds from cached hostfile Installed packages Name: httpd Architecture: x86_64
Version: 2.4.6
Release: 45.el7.centos Size: 9.4 M Repository: installed From repository: Base-Repo Summary: Apache HTTP Server URL: http://httpd.apache.org/ License: ASL 2.0 Description: The Apache HTTP Server is a powerful, efficient, and extensible: web server.
As we have a version prior to 2.4.8, we add at the end of the previously generated CRT certificate, the content of the Diffie-Helman Group:
[root @ linuxbox tls] # cat private / dhparams.pem >> certs/desdelinux.fan.crt
If you want to check that the DH parameters were correctly added to the CRT certificate, execute the following commands:
[root @ linuxbox tls] # cat private / dhparams.pem ----- BEGIN DH PARAMETERS ----- MIIBCAKCAQEAnwfWSlirEuMwJft0hgAdB0km9d3qGGiErRXPfeZU+Tqp/ZFOCdzP /O6NeXuHI4vnsTDWEAjXmpRzq/z1ZEWQa6j+l1PgTgk2XqaMViD/gN+sFPnx2EmV keVcMDqG03gnmCgO9R4aLYT8uts5T6kBRhvxUcrk9Q7hIpGCzGtdgwaVf1cbvgOe 8kfpc5COh9IxAYahmNt+5pBta0SDlmoDz4Rk/4AFXk2mjpDYoizaYMPeIInGUzOv /LE6Y7VVRY/BJG9EZ5pVYJPCruPCUHkhvm+r9Tt56slk+HE2d52uFRSDd2FxK3n3 cN1vJ5ogsvmHayWUjVUA18LLfGSxEFsc4wIBAg== ----- END DH PARAMETERS ----- [root@linuxbox tls]# cat certs/desdelinux.fan.crt -----BEGIN CERTIFICATE----- MIIGBzCCA++gAwIBAgIJANd9FLCkDBfzMA0GCSqGSIb3DQEBCwUAMIGZMQswCQYD VQQGEwJDVTENMAsGA1UECAwEQ3ViYTEPMA0GA1UEBwwGSGFiYW5hMRcwFQYDVQQK DA5EZXNkZUxpbnV4LkZhbjEUMBIGA1UECwwLRW50dXNpYXN0YXMxFzAVBgNVBAMM DmRlc2RlbGludXguZmFuMSIwIAYJKoZIhvcNAQkBFhNidXp6QGRlc2RlbGludXgu ZmFuMB4XDTE3MDUyMjE0MDQ1MloXDTIyMDUyMTE0MDQ1MlowgZkxCzAJBgNVBAYT AkNVMQ0wCwYDVQQIDARDdWJhMQ8wDQYDVQQHDAZIYWJhbmExFzAVBgNVBAoMDkRl c2RlTGludXguRmFuMRQwEgYDVQQLDAtFbnR1c2lhc3RhczEXMBUGA1UEAwwOZGVz ZGVsaW51eC5mYW4xIjAgBgkqhkiG9w0BCQEWE2J1enpAZGVzZGVsaW51eC5mYW4w ggIiMA0GCSqGSIb3DQEBAQUAA4ICDwAwggIKAoICAQCn5MkKRdeFYiN+xgGdsRn8 sYik9X75YnJcbeZrD90igfPadZ75ehtfYIxxOS+2U+omnFgr/tCKYUVJ50seq/lB idcLP4mt7wMrMZUDpy1rlWPOZGKkG8AdStCYI8iolvJ4rQtLcsU6jhRzEXsZxfOb O3sqc71yMIj5qko55mlsEVB3lJq3FTDQAY2PhXopJ8BThW1T9iyl1HlYpxj7OItr /BqiFhxbP17Fpd3QLyNiEl+exVJURYZkvuZQqVPkFAlyNDh5I2fYfrI9yBVPBrZF uOdRmT6jv6jFxsBy9gggcy+/u1nhlKssLBEhyaKfaQoItFGCAmevkyzdl1LTYDPY ULi79NljQ1dSwWgraZ3i3ACZIVO/kHcOPljsNxE8omI6qNFWqFd1qdPH5S4c4IR1 5URRuwyVNffEHKaCJi9vF9Wn8LVKnN/+5zZGRJA8hI18HH9kF0A1sCNj1KKiB/xe /02wTzR/Gbj8pkyO8fjVBvd/XWI8EMQyMc1gvtIAvZ00SAB8c1NEOCs5pt0Us6pm 1lOkgD6nl90Dx9p805mTKD+ZcvRaShOvTyO3HcrxCxOodFfZQCuHYuQb0dcwoK2B yOwL77NmxNH1QVJL832lRARn8gpKoRAUrzdTSTRKmkVrOGcfvrCKhEBsJ67Gq1+T YDLhUiGVbPXXR9rhAyyX2QIDAQABo1AwTjAdBgNVHQ4EFgQURGCMiLVLPkjIyGZK UrZgMkO0X8QwHwYDVR0jBBgwFoAURGCMiLVLPkjIyGZKUrZgMkO0X8QwDAYDVR0T BAUwAwEB/zANBgkqhkiG9w0BAQsFAAOCAgEAdy1tH1DwfCW47BNJE1DW8Xlyp+sZ uYTMOKfNdnAdeSag1WshR6US6aCtU6FkzU/rtV/cXDKetAUIzR50aCYGTlfMCnDf KKMZEPjIlX/arRwBkvIiRTU1o3HTniGp9d3jsRWD/AvB3rSus4wfuXeCoy7Tqc9U FaXqnvxhF8/ptFeeCeZgWu16zyiGBqMj4ZaQ7RxEwcoHSd+OByg8E9IE2cYrWP2V 6P7hdCXmw8voMxCtS2s++VRd1fGqgGxXjXT8psxmY2MrseuTM2GyWzs+18A3VVFz UXLD2lzeYs638DCMXj5/BMZtVL2a4OhMSYY4frEbggB3ZgXhDDktUb7YhnBTViM3 2sgJJOSTltOgAnyOPE0CDcyktXVCtu3PNUc+/AB3UemI9XCw4ypmTOMaIZ2Gl6Uo pmTk41fpFuf8pqW3ntyu43lC5pKRBqhit6MoFGNOCvFYFBWcltpqnjsWfY2gG/b5 8D5HsedueqkAsVblKPBFpv1BB9X0HhBUYsrz8jNGZGbkgR4XQoIoLbQZHEB35APU 4yT1Lzc3jk34yZF5ntmFt3wETSWwJZ+0cYPw7n4E6vbs1C7iKAMQRVy+lI5f8XYS YKfrieiPPdmQ22Zm2Tbkqi4zjJBWmstrw6ezzAQNaaAkiOiJIwvXU81KYsN37THh Nf0/JsEjPklCugE= -----END CERTIFICATE----- -----BEGIN DH PARAMETERS----- MIIBCAKCAQEAnwfWSlirEuMwJft0hgAdB0km9d3qGGiErRXPfeZU+Tqp/ZFOCdzP /O6NeXuHI4vnsTDWEAjXmpRzq/z1ZEWQa6j+l1PgTgk2XqaMViD/gN+sFPnx2EmV keVcMDqG03gnmCgO9R4aLYT8uts5T6kBRhvxUcrk9Q7hIpGCzGtdgwaVf1cbvgOe 8kfpc5COh9IxAYahmNt+5pBta0SDlmoDz4Rk/4AFXk2mjpDYoizaYMPeIInGUzOv /LE6Y7VVRY/BJG9EZ5pVYJPCruPCUHkhvm+r9Tt56slk+HE2d52uFRSDd2FxK3n3 cN1vJ5ogsvmHayWUjVUA18LLfGSxEFsc4wIBAg== ----- END DH PARAMETERS -----
After these changes, we must restart the Postfix and httpd services:
[root @ linuxbox tls] # service postfix restart [root @ linuxbox tls] # service postfix status [root @ linuxbox tls] # service httpd restart [root @ linuxbox tls] # service httpd status
The inclusion of the Diffie-Helman Group in our TLS certificates may make connecting over HTTPS a little slower, but the addition of security is well worth it.
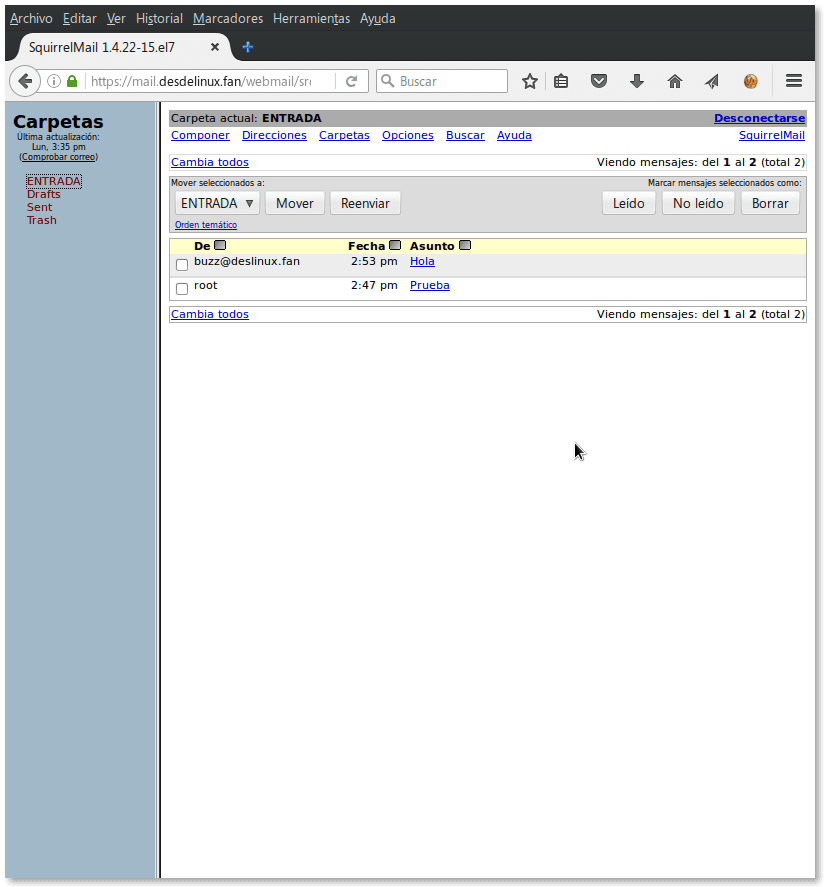
Checking Squirrelmail
AFTER that the certificates are correctly generated and that we verify their correct operation as we did through the console commands, point your preferred browser to the URL http://mail.desdelinux.fan/webmail and it will connect to the web client after accepting the corresponding certificate. Note that, even though you specify the HTTP protocol, it will be redirected to HTTPS, and this is due to the default settings that CentOS offers for Squirrelmail. See the file /etc/httpd/conf.d/squirrelmail.conf.
About user mailboxes
Dovecot creates the IMAP mailboxes in the folder home of each user:
[root @ linuxbox ~] # ls -la /home/legolas/mail/.imap/ total 12 drwxrwx ---. 5 legolas mail 4096 May 22 12:39. drwx ------. 3 legolas legolas 75 May 22 11:34 .. -rw -------. 1 legolas legolas 72 May 22 11:34 dovecot.mailbox.log -rw -------. 1 legolas legolas 8 May 22 12:39 dovecot-uidvalidity -r - r - r--. 1 legolas legolas 0 May 22 10:12 dovecot-uidvalidity.5922f1d1 drwxrwx ---. 2 legolas mail 56 May 22 10:23 INBOX drwx ------. 2 legolas legolas 56 May 22 12:39 Sent drwx ------. 2 legolas legolas 30 May 22 11:34 Trash
They are also stored in / var / mail /
[root @ linuxbox ~] # less / var / mail / legolas From MAILER_DAEMON Mon May 22 10:28:00 2017 Date: Mon, 22 May 2017 10:28:00 -0400 From: Mail System Internal Data Subject: DON'T DELETE THIS MESSAGE -- FOLDER INTERNAL DATA Message-ID: <1495463280@linuxbox> . It is created automatically by the mail system software. If deleted, important folder data will be lost, and it will be re-created with the data reset to initial values. From root@desdelinux.fan Mon May 22 10:47:10 2017 Return-Path:desdelinux.fan> X-Original-To: legolas Delivered-To: legolas@desdelinux.fan Received: by desdelinux.fan (Postfix, from userid 0) id 7EA22C11FC57; Mon, 22 May 2017 10:47:10 -0400 (EDT) Date: Mon, 22 May 2017 10:47:10 -0400 To: legolas@desdelinux.fan Subject: Test User-Agent: Heirloom mailx 12.5 7/5/10 MIME-Version: 1.0 Content-Type: text/plain; charset=us-ascii Content-Transfer-Encoding: 7bit Message-Id: <20170522144710.7EA22C11FC57@desdelinux.fan> From: root@desdelinux.fan (root) X-UID: 7 Status: RO Hello. This is a test message From buzz@deslinux.fan Mon May 22 10:53:08 2017 Return-Path: X-Original-To: legolas@desdelinux.fan Delivered-To: legolas@desdelinux.fan Received: from sysadmin.desdelinux.fan (gateway [172.16.10.1]) by desdelinux.fan (Postfix) with ESMTP id C184DC11FC57 fordesdelinux.fan>; Mon, 22 May 2017 10:53:08 -0400 (EDT) Message-ID: <739874.219379516-sendEmail@sysadmin> From: "buzz@deslinux.fan" To: "legolas@desdelinux.fan"desdelinux.fan> Subject: Hello Date: Mon, 22 May 2017 14:53:08 +0000 X-Mailer: sendEmail-1.56 MIME-Version: 1.0 Content-Type: multipart/related; boundary="----MIME delimiter for sendEmail-794889.899510057 / var / mail / legolas
PAM miniseries summary
We have looked at the core of a Mailserver and put a little emphasis on security. We hope that the article serves as an Entry Point to a topic as complicated and susceptible to making mistakes as it is the implementation of a Mail Server manually.
We use local user authentication because if we read the file correctly /etc/dovecot/conf.d/10-auth.conf, we will see that in the end it is included -default- the authentication file of the system users ! include auth-system.conf.ext. Precisely this file tells us in its header that:
[root @ linuxbox ~] # less /etc/dovecot/conf.d/auth-system.conf.ext
# Authentication for system users. Included from 10-auth.conf. # # # # PAM authentication. Preferred nowadays by most systems.
# PAM is typically used with either userdb passwd or userdb static. # REMEMBER: You'll need /etc/pam.d/dovecot file created for PAM # authentication to actually work. passdb {driver = pam # [session = yes] [setcred = yes] [failure_show_msg = yes] [max_requests = ] # [cache_key = ] [ ] #args = dovecot}
And the other file exists /etc/pam.d/dovecot:
[root @ linuxbox ~] # cat /etc/pam.d/dovecot #% PAM-1.0 auth required pam_nologin.so auth include password-auth account include password-auth session include password-auth
What are we trying to convey about PAM authentication?
- CentOS, Debian, Ubuntu, and many other Linux distributions install Postifx and Dovecot with local authentication enabled by default.
- Many articles on the Internet use MySQL - and more recently MariaDB - to store users and other data concerning a Mailserver. BUT these are servers for THOUSANDS OF USERS, and not for a classic SME Network with - perhaps - hundreds of users.
- Authentication through PAM is necessary and sufficient to provide network services as long as they run on a single server as we have seen in this miniseries.
- Users stored in an LDAP database can be mapped as if they were local users, and PAM authentication can be used to provide network services from different Linux servers acting as LDAP clients for the central authentication server. In this way, we would work with the credentials of the users stored in the central LDAP server database, and it would NOT be essential to maintain a database with local users.
Until the next adventure!
Believe me that in practice this is a process that gives more than one sysadmin severe headaches, I am convinced that in the future it will be a reference guide for anyone who wants to manage their emails themselves, a practical case that becomes in an abc when integrating postfix, dovecot, squirrelmail ..
Thank you very much for your praiseworthy contribution,
Why not use Mailpile, when it comes to security, with PGP? Also Roundcube has a much more intuitive interface and can also integrate PGP.
3 days ago I read the post, I know how to thank you. I do not plan to install a mail server but it is always helpful to see the creation of certificates, useful for other applications and these tutorials hardly expire (even more when you use centOS).
Manuel Cillero: Thanks for linking to and from your blog this article which is the minimum core of a mail server based on Postfix and Dovecot.
Lizard: As always, your evaluation is very well received. Thank you.
Darko: In almost all my articles I say more or less that "Everyone implements the services with the programs that they like the most." Thanks for comment.
Martin: Thanks to you also for reading the article and I hope it will help you in your work.
Tremendous article friend Federico. Thank you very much for such a good tuto.
excellent although I would use "virtual users" to avoid having to create a system user every time I add an email, thanks I learned a lot of new things and this is the type of post I was waiting for
Good afternoon,
They would be encouraged to make the same one with fedora directory server + postifx + dovecot + thunderbird or outlook.
I have a part but I'm stuck, I would gladly share the document to the community @desdelinux
I did not imagine that it would reach more than 3000 visits !!!
Greetings Lizard!
Excellent tutorial colleague.
Could you do it for Debian 10 with users of an Active Directory mounted on Samba4 ???
I imagine it would be almost the same but changing the authentication type.
The section that you dedicate to the creation of self-signed certificates is very interesting.