General index of the series: Computer Networks for SMEs: Introduction
federicotoujague@gmail.com
https://blog.desdelinux.net/author/fico
Hello friends and friends!
This article is a continuation of Squid + PAM Authentication in CentOS 7- SMB Networks.
UNIX / Linux operating systems offer a REAL multi-user environment, in which many users can work simultaneously on the same system and share resources such as processors, hard drives, memory, network interfaces, devices inserted in the system, and so on.
For this reason, System Administrators are obliged to continuously manage the users and groups of the system and to formulate and implement a good administration strategy.
Next we will see very concisely the general aspects of this important activity in Linux Systems Administration.
Sometimes it is better to offer Utility and then Need.
This is a typical example of that order. First we show how to implement an Internet Proxy service with Squid and local users. Now we must ask ourselves:
- ¿how can I implement network services on a UNIX / Linux LAN from local users and with a acceptable security?.
It does not matter that, in addition, Windows clients are connected to this network. It only matters the need for which services the SME Network needs and what is the simplest and cheapest way to implement them.
- ¿Perhaps the authentication mechanism at the birth of the ARPANET, Internet and other networks Wide Aarea Network o Local Aarea Network initials was based on LDAP, Directory Services, In the Microsoft LSASS, In the Active Directory, or by Kerberos?, just to mention a few.
A good question that everyone should seek their answers. I invite you to search for the term «authentication»On Wikipedia in English, which is by far the most complete and coherent as far as original content -in English- is concerned.
According to History already roughly, first was the Authentication y Content local, after NIS Network Information System developed by Sun Microsystem and also known as Yellow Pages o yp, and then LDAP Lightweight Directory Access Protocol.
What about «Acceptable Security»Comes up because many times we worry about the security of our local network, while we access Facebook, Gmail, Yahoo, etc. -to mention just a few- and we give Our Privacy in them. And look at the large number of articles and documentaries that regarding the No Privacy on the Internet exist.
Note on CentOS and Debian
CentOS / Red Hat and Debian have their own philosophy on how to implement security, which is not fundamentally different. However we affirm that both are very stable, safe and reliable. For example, in CentOS the SELinux context is enabled by default. In Debian we must install the package selinux-basics, which indicates that we can also use SELinux.
In CentOS, FreeBSD, and other operating systems, the -system- group is created wheel to allow access as root only to system users belonging to that group. Read /usr/share/doc/pam-1.1.8/html/Linux-PAM_SAG.html, and /usr/share/doc/pam-1.1.8/html/Linux-PAM_SAG.html. Debian does not incorporate a group wheel.
Main files and commands
Archives
The main files related to managing local users in a Linux operating system are:
CentOS and Debian
- / Etc / passwd: user account information.
- / Etc / shadow- User account security information.
- / Etc / group: group account information.
- / etc / gshadow- Security information for group accounts.
- / etc / default / useradd: default values for account creation.
- / etc / skel /: directory that contains the default files that will be included in the HOME directory of the new user.
- /etc/login.defs- Password security configuration suite.
Debian
- /etc/adduser.conf: default values for account creation.
Commands on CentOS and Debian
[root @ linuxbox ~] # chpasswd -h # Update passwords in batch mode Usage mode: chpasswd [options] Options: -c, --crypt-method METHOD the crypt method (one of NONE DES MD5 SHA256 SHA512) -e, --encrypted the provided passwords are encrypted -h, --help shows this help prompt and terminate -m, --md5 encrypts password in clear using MD5 algorithm -R, --root CHROOT_DIR directory to chroot into -s, --sha-rounds number of SHA rounds for SHA encryption algorithms * # batch- Execute commands when system load allows. In other words # when the average load falls below 0.8 or the value specified by invoking # the atd command. More information man-batch. [root @ linuxbox ~] # gpasswd -h # Declare Administrators in / etc / group and / etc / gshadow How to use: gpasswd [options] GROUP Options: -a, --add USER adds USER to GROUP -d, --delete USER removes USER from GROUP -h, --help shows this help message and ends -Q, - -root CHROOT_DIR directory to chroot into -r, --delete-password remove the GROUP's password -R, --restrict restricts access to GROUP to its members -M, --members USER, ... sets the list of members of GROUP -A, --administrators ADMIN, ... sets the list of GROUP administrators Except for the -A and -M options, the options cannot be combined. [root @ linuxbox ~] # groupadd -h # Create a new group How to use: groupadd [options] GROUP Options: -f, --force terminate if group already exists, and cancel -g if GID is already in use -g, --gid GID use GID for new group - h, --help displays this help message and ends -K, --key KEY = VALUE overwrites the default values of "/etc/login.defs" -o, --non-unique allows you to create groups with GIDs (not unique ) duplicates -p, --password PASSWORD use this encrypted password for the new group -r, --system create a system account -R, --root CHROOT_DIR directory to chroot into [root @ linuxbox ~] # group del -h # Delete an existing group How to use: groupdel [options] GROUP Options: -h, --help show this help message and terminate -R, --root CHROOT_DIR directory to chroot into [root @ linuxbox ~] # groupmems -h # Declare Administrators in a user's primary group How to use: groupmems [options] [action] Options: -g, --group GROUP change the name of the group instead of the user's group (can only be done by the administrator) -R, --root CHROOT_DIR directory to chroot into Actions: -a, --add USER adds USER to group members -d, --delete USER removes USER from group members list -h, --help displays this help message and ends -p, - purge purge all group members -l, --list lists group members [root @ linuxbox ~] # group mod -h # Modify the definition of a group How to use: groupmod [options] GROUP Options: -g, --gid GID changes the group identifier to GID -h, --help shows this help message and ends -n, --new-name NEW_Group changes the name a NEW_GROUP -o, --non-unique allows to use a duplicate GID (not unique) -p, --password PASSWORD changes the password to PASSWORD (encrypted) -R, --root CHROOT_DIR directory to chroot into [root @ linuxbox ~] # grpck -h # Check the integrity of a group file How to use: grpck [options] [group [gshadow]] Options: -h, --help show this help message and exit -r, --read-only display errors and warnings but do not change files -R, - -root CHROOT_DIR directory to chroot into -s, --sort sort entries by UID [root @ linuxbox ~] # grpconv # Associated commands: pwconv, pwunconv, grpconv, grpunconv # Used to convert to and from shadow passwords and groups # The four commands operate on files / etc / passwd, / etc / group, / etc / shadow, # and / etc / gshadow. For more information man grpconv. [root @ linuxbox ~] # sg -h # Execute a command with a different group ID or GID How to use: sg group [[-c] order] [root @ linuxbox ~] # newgrp -h # Change the current GID during a login How to use: newgrp [-] [group] [root @ linuxbox ~] # new users -h # Update and create new users in batch mode Usage mode: newusers [options] Options: -c, --crypt-method METHOD the crypt method (one of NONE DES MD5 SHA256 SHA512) -h, --help show this help message and exit -r, --system create system accounts -R, --root CHROOT_DIR directory to chroot into -s, --sha-rounds number of SHA rounds for SHA encryption algorithms * [root @ linuxbox ~] # pwck -h # Check the integrity of password files How to use: pwck [options] [passwd [shadow]] Options: -h, --help show this help message and exit -q, --quiet report errors only -r, --read-only display errors and warnings but do not change files -R, --root CHROOT_DIR directory to chroot into -s, --sort sort entries by UID [root @ linuxbox ~] # useradd -h # Create a new user or update the default # information of the new user How to use: useradd [options] USER useradd -D useradd -D [options] Options: -b, --base-dir BAS_DIR base directory for the home directory of the new account -c, --comment COMMENT GECOS field of the new account -d, --home-dir PERSONAL_DIR new account's home directory -D, --defaults print or change the default setting of useradd -e, --expiredate EXPIRY_DATE expiration date of new account -f, - inactive INACTIVE period of inactivity of the password of the new account delgroup -g, --gid GROUP name or identifier of the primary group of the new account -G, --groups GROUPS list of supplementary groups of the new account -h, --help shows this help message and ends -k, - skel DIR_SKEL uses this alternate "skeleton" directory -K, --key KEY = VALUE overwrites the default values of "/etc/login.defs" -l, --no-log-init does not add the user to the databases from lastlog and faillog -m, --create-home creates the home directory of user -M, --no-create-home does not create the home directory of user -N, --no-user-group does not create a group with the same name as the user -o, --non-unique allows creating users with duplicate (non-unique) identifiers (UIDs) -p, --password PASSWORD encrypted password of the new account -r, --system creates an account of the system -R, --root CHROOT_DIR directory to chroot into -s, --shell CONSOLE console access of the new account -u, --uid UID user identifier of the new account -U, --user-group createa group with the same name as user -Z, --selinux-user USER_SE uses the specified user for the SELinux user [root @ linuxbox ~] # userdel -h # Delete a user's account and related files Usage mode: userdel [options] USER Options: -f, --force force some actions that would fail otherwise eg removal of user still logged in or files, even if not owned by the user -h, --help displays this message Help and finish -r, --remove remove home directory and mailbox -R, --root CHROOT_DIR directory to chroot into -Z, --selinux-user remove any SELinux user mapping for the user [root @ linuxbox ~] # usermod -h # Modify a user account How to use: usermod [options] USER Options: -c, --comment COMMENT new value of the GECOS field -d, --home PERSONAL_DIR new personal directory of the new user -e, --expiredate EXPIRED_DATE sets the expiration date of the account to EXPIRED_DATE -f, --inactive INACTIVE sets idle time after account expires to INACTIVE -g, --gid GROUP forces use of GROUP for new user account -G, --groups GROUPS list of supplemental groups -a, --append append the user to the supplemental GROUPS mentioned by the -G option without removing him / her from other groups -h, --help display this help message and terminate -l, --login NAME again name for user -L, --lock locks user account -m, --move-home move contents of home directory to new directory (use only in conjunction with -d) -o, --non-unique allows to use Duplicate (non-unique) UIDs -p, --password PASSWORD use encrypted password for new account -R, --root CHR OOT_DIR directory to chroot into -s, --shell CONSOLE new access console for user account -u, --uid UID forces use of UID for new user account -U, --unlock unlocks user account -Z, --selinux-user SEUSER new SELinux user mapping for the user account
Commands in Debian
Debian differentiates between useradd y adduser. Recommends that System Administrators use adduser.
root @ sysadmin: / home / xeon # adduser -h # Add a user to the system root @ sysadmin: / home / xeon # addgroup -h # Add a group to the system adduser [--home DIRECTORY] [--shell SHELL] [--no-create-home] [--uid ID] [--firstuid ID] [--lastuid ID] [--gecos GECOS] [--ingroup GROUP | --gid ID] [--disabled-password] [--disabled-login] USER Add a normal user adduser --system [--home DIRECTORY] [--shell SHELL] [--no-create-home] [ --uid ID] [--gecos GECOS] [--group | --ingroup GROUP | --gid ID] [--disabled-password] [--disabled-login] USER Add a user from the system adduser --group [--gid ID] GROUP addgroup [--gid ID] GROUP Add a user group addgroup --system [--gid ID] GROUP Add a group from the system adduser USER GROUP Add an existing user to an existing group general options: --quiet | -q do not display process information on standard output --force-badname allow user names that do not match the configuration variable NAME_REGEX --help | -h usage message --version | -v version number and copyright --conf | -c FILE use FILE as configuration file root @ sysadmin: / home / xeon # delusional -h # Remove a normal user from the system root @ sysadmin: / home / xeon # delgroup -h # Remove a normal group from the system deluser USER removes a normal user from the system example: deluser miguel --remove-home removes the user's home directory and the mail queue. --remove-all-files removes all files owned by the user. --backup backs up files before deleting. --backup-to destination directory for backups. The current directory is used by default. --system only remove if you are a system user. delgroup GROUP deluser --group GROUP removes a group from the system example: deluser --group students --system only remove if it is a group from the system. --only-if-empty only remove if they have no more members. deluser USER GROUP removes the user from the group example: deluser miguel students general options: --quiet | -q don't give process info on stdout --help | -h usage message --version | -v version number and copyright --conf | -c FILE use FILE as configuration file
Policies
There are two types of policies that we must consider when creating user accounts:
- User Account Policies
- Password aging policies
User Account Policies
In practice, the fundamental components that identify a user account are:
- User account name - user LOGIN, not the name and surnames.
- User id - UID.
- Main group to which it belongs - GID.
- Password - Password.
- Access permits - access permissions.
The main factors to consider when creating a user account are:
- The length of time that the user will have access to the file system and resources.
- The amount of time in which the user must change their password - periodically - for security reasons.
- The amount of time that the login -login- will remain active.
Furthermore, when assigning a user his UID y Password, we must take into account that:
- The integer value UID it must be unique and not negative.
- El Password it must be of adequate length and complexity, so that it is difficult to decipher.
Password aging policies
On a Linux system, the Password of a user is not assigned a default expiration time. If we use password aging policies, we can change the default behavior and when creating users, the defined policies will be taken into account.
In practice, there are two factors to consider when setting the age of a password:
- Security.
- User convenience.
A password is more secure the shorter its expiration period. There is less risk of it being leaked to other users.
To set the password aging policies, we can use the command change:
[root @ linuxbox ~] # chage Usage mode: chage [options] USER Options: -d, --lastday LAST_DAY sets the day of the last password change to LAST_DAY -E, --expiredate CAD_DATE sets the expiration date to CAD_DATE -h, --help displays this help message and ends -I, --inactive INACTIVE disables the account after INACTIVE days from the expiration date -l, --list shows the account's age information -m, --mindays MINDAYS sets the number minimum days before changing password to MIN_DAYS -M, --maxdays MAX_DAYS sets the maximum number of days before changing password to MAX_DAYS -R, --root CHROOT_DIR directory to chroot into -W, --warndays WARNING_DAYS sets the days of expiration notice to DAYS_NOTICE
In the previous article we created several users as an example. If we want to know the age values of the user's account with LOGIN Galadriel:
[root @ linuxbox ~] # chage --list galadriel Last password change: Apr 21, 2017 Password expires: never Inactive password: never Account expires: never Minimum number of days between password change: 0 Maximum number of days between password change: 99999 Number of days of notice before password expires: 7
Those were the default values that the system had when we created the user account using the graphical administration utility "Users and groups":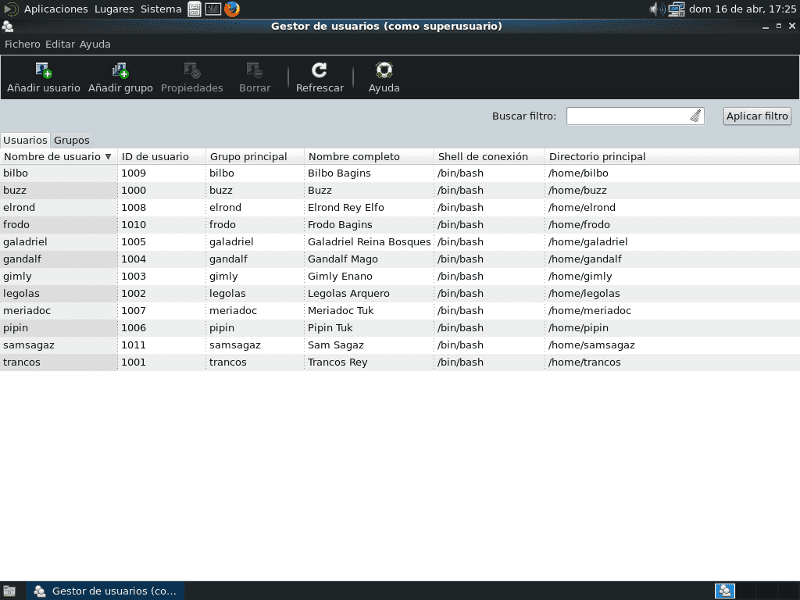
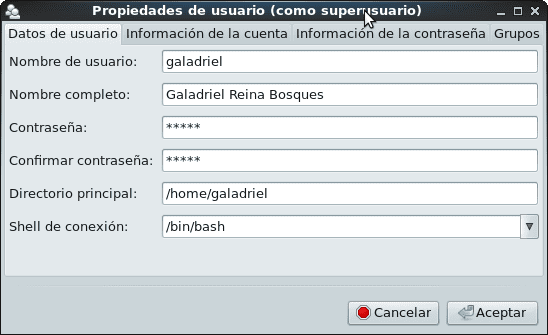

To change password aging defaults, it is recommended to edit the file /etc/login.defs y modify the minimum amount of values we need. In that file we will only change the following values:
# Password aging controls: # # PASS_MAX_DAYS Maximum number of days a password may be used. # PASS_MIN_DAYS Minimum number of days allowed between password changes. # PASS_MIN_LEN Minimum acceptable password length. # PASS_WARN_AGE Number of days warning given before a password expires. # PASS_MAX_DAYS 99999 #! More than 273 years! PASS_MIN_DAYS 0 PASS_MIN_LEN 5 PASS_WARN_AGE 7
for the values that we chose according to our criteria and needs:
PASS_MAX_DAYS 42 # 42 continuous days that you can use the Password PASS_MIN_DAYS 0 # password can be changed at any time PASS_MIN_LEN 8 # minimum password length PASS_WARN_AGE 7 # Number of days the system warns you to # change the password before it expires.
We leave the rest of the file as it was and we recommend not changing other parameters until we know well what we are doing.
The new values will be taken into account when we create new users. If we change the password of an already created user, the value of the minimum password length will be respected. If we use the command Passwd instead of the graphical utility and we write that the password will be «legolas17«, The system complains like the graphic tool« Users and groups »and it replies that«Somehow the password reads the username»Although in the end I accept that weak password.
[root @ linuxbox ~] # passwd legolas Changing the password of the legolas user. New Password: goalkeeper # is less than 7 characters INCORRECT PASSWORD: Password is less than 8 characters Retype new password: legolas17 Passwords do not match. # Logical right? New Password: legolas17 INCORRECT PASSWORD: Somehow the password reads the user's name Retype the new password: legolas17 passwd: all authentication tokens were updated successfully.
We incur "the weakness" of declaring a password that includes the LOGIN user. That is a non-recommended practice. The correct way would be:
[root @ linuxbox ~] # passwd legolas Changing the password of the legolas user. New Password: highmountains01 Retype the new password: highmountains01 passwd: all authentication tokens were updated successfully.
To change the expiration values of the Password de Galadriel, we use the chage command, and we only have to change the value of PASS_MAX_DAYS from 99999 to 42:
[root @ linuxbox ~] # chage -M 42 galadriel
[root @ linuxbox ~] # chage -l galadriel
Last password change: Apr 21, 2017 Password expires: Jun 02, 2017 Inactive password: never Account expires: never Minimum number of days between password change: 0 Maximum number of days between password change: 42
Number of days of notice before password expires: 7
And so on, we can change the passwords of the users already created and their expiration values manually, using the graphical tool «Users and groups», or using a script - script that automates some of the non-interactive work.
- In this way, if we create local users of the system in a way that is not recommended by the most common practices regarding security, we can change that behavior before continuing to implement more PAM-based services..
If we create the user anduin with LOGIN «anduin»And password«ThePassword»We will obtain the following result:
[root @ linuxbox ~] # useradd anduin [root @ linuxbox ~] # passwd anduin Changing the password of the user anduin. New Password: ThePassword INCORRECT PASSWORD: Password does not pass dictionary verification - It is based on a word in the dictionary. Retype the new password: ThePassword passwd - All authentication tokens were updated successfully.
In other words, the system is creative enough to indicate the weaknesses of a password.
[root @ linuxbox ~] # passwd anduin Changing the password of the user anduin. New Password: highmountains02 Retype the new password: highmountains02 passwd - All authentication tokens were updated successfully.
Policy Summary
- It is clear that the password complexity policy, as well as the minimum length of 5 characters, is enabled by default in CentOS. On Debian, the complexity check works for normal users when they try to change their password by invoking the command Passwd. For the user root, there are no default limitations.
- It is important to know the different options that we can declare in the file /etc/login.defs using the command man login.defs.
- Also, check the content of the files / etc / default / useradd, and also in Debian /etc/adduser.conf.
System Users and Groups
In the process of installing the operating system, a whole series of users and groups are created which, one literature calls Standard Users and another System Users. We prefer to call them System Users and Groups.
As a rule, system users have a UID <1000 and your accounts are used by different applications of the operating system. For example, the user account «squid»Is used by the Squid program, while the« lp »account is used for the printing process from word or text editors.
If we want to list those users and groups, we can do it using the commands:
[root @ linuxbox ~] # cat / etc / passwd [root @ linuxbox ~] # cat / etc / group
It is not recommended at all to modify the users and groups of the system. 😉
Due to its importance, we repeat that in CentOS, FreeBSD, and other operating systems, the -system- group is created wheel to allow access as root only to system users belonging to that group. Read /usr/share/doc/pam-1.1.8/html/Linux-PAM_SAG.html, and /usr/share/doc/pam-1.1.8/html/Linux-PAM_SAG.html. Debian does not incorporate a group wheel.
Managing user and group accounts
The best way to learn how to manage user and group accounts is:
- Practicing the use of the commands listed above, preferably in a virtual machine and before of using graphical tools.
- Consulting the manuals or man pages of each command before searching for any other information on the Internet.
Practice is the best criterion of truth.
Summary
By far, a single article dedicated to Local User and Group Management is not enough. The degree of knowledge that each Administrator acquires will depend on the personal interest in learning and deepening about this and other related topics. It is the same as with all the aspects that we have developed in the series of articles SME Networks. In the same way you can enjoy this version in pdf here.
Next delivery
We will continue to implement services with authentication against local users. We will then install an instant messaging service based on the program Prosody.
See you soon!
Hello, great article, I ask you where I work, printers are shared a lot, the problem is in cups, sometimes it hangs and they cannot print as I can give them permission to restart it (because most of the time we are working in other areas) without giving the password root since the only way I found is to change it so that a specific user can restart it.
From already thank you very much.
Greetings HO2GI !. For example, let's say that the user Legolas you want to give it permission to only restart the CUPS service, using of course the command sudo, which must be installed:
[root @ linuxbox ~] # visudo
Cnd alias specification
Cmnd_Alias RESTARTCUPS = /etc/init.d/cups restart
User privilege specification
root ALL = (ALL: ALL) ALL
legolas ALL = RESTARTCUPS
Save the changes made to the file sweats. Login as the user Legolas:
legolas @ linuxbox: ~ $ sudo /etc/init.d/squid reload
[sudo] password for legolas:
Sorry, user legolas is not allowed to execute '/etc/init.d/postfix reload' as root on linuxbox.desdelinux.fan.
legolas @ linuxbox: ~ $ sudo /etc/init.d/cups restart
[sudo] password for legolas:
[ok] Restarting Common Unix Printing System: cupsd.
Forgive me if the prompt differs on CentOS, because I was guided by what I just did on Debian Wheezy. ;-). Where I am right now, I don't have any CentOS on hand.
On the other hand, if you want to add other System Users as full CUPS Administrators -they can configure it wrong- you make them members of the group lpadmin, which is created when you install CUPS.
https://www.cups.org/doc/man-lpadmin.html
http://www.computerhope.com/unix/ulpadmin.htm
Great thanks a thousand Fico I will try it right now.
HO2GI, in CentOS / Red -Hat it would be:
[root @ linuxbox ~] # visudo
Services
Cmnd_Alias RESTARTCUPS = / usr / bin / systemctl restart cups, / usr / bin / systemctl status cups
Allow root to run any commands anywhere
root ALL = (ALL) ALL
legolas ALL = RESTARTCUPS
Save changes
[root @ linuxbox ~] # exit
buzz @ sysadmin: ~ $ ssh legolas @ linuxbox
legolas @ linuxbox's password:
[legolas @ linuxbox ~] $ sudo systemctl restart cups
We trust You have received the usual lecture from the Local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for legolas:
[legolas @ linuxbox ~] $ sudo systemctl status cups
● cups.service - CUPS Printing Service
Loaded: loaded (/usr/lib/systemd/system/cups.service; enabled; vendor preset: enabled)
Active: active (running) since Mar 2017-04-25 22:23:10 EDT; 6s ago
Main PID: 1594 (cupsd)
CGroup: /system.slice/cups.service
└─1594 / usr / sbin / cupsd -f
[legolas @ linuxbox ~] $ sudo systemctl restart squid.service
Sorry, user legolas is not allowed to execute '/ bin / systemctl restart squid.service' as root on linuxbox.
[legolas @ linuxbox ~] $ exit