Wireless Attack Hacking Tools: Wifite and WEF
Ending last month, January 2023, we share one more interesting and useful post to learn about the field of Ethical hacking. Specifically, we address 2 similar free and open tools, coincidentally named the same, i.e. hacking tools, but from different developers. Which, were an ideal replacement for one already quite old and expired called fsociety.
Furthermore, both Hacking Tools applications, were similar in that they offered to facilitate the management and automation of various hacking software tools. But, with the difference that one was for Computers and another for Mobiles. For this reason, today we thought it was ideal to present 2 more free and open tools in this area. But, more specifically, for the field of Wireless Hacking (WiFi). And these 2 apps from the field of “Wireless Attack Hacking Tools” consist of Wifi and WEF.
And, before starting this interesting post about the Wi-Fi and WEF apps belonging to the field of “Wireless Attack Hacking Tools”, we recommend the previous publication, for later reading:

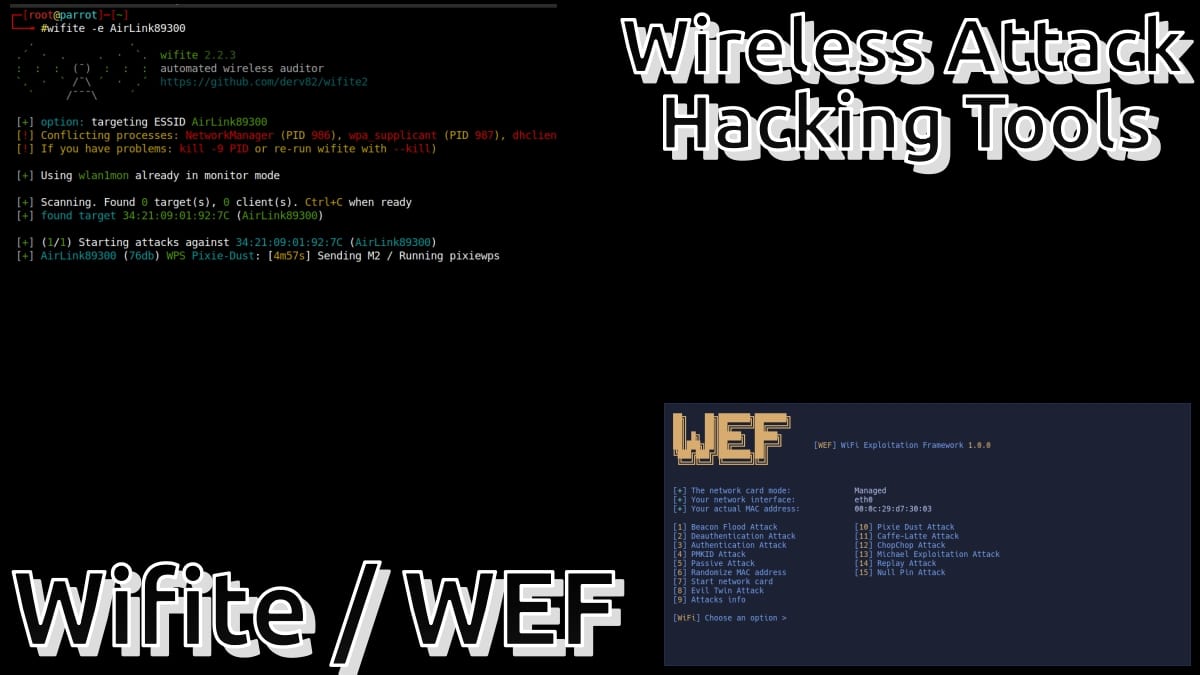
Wifite and WEF: Wireless Attack Hacking Tools apps
What is Wi-Fi?
According to official website on GitHub by Wi-Fi, this tool in the field of “Wireless Attack Hacking Tools” It is briefly described as follows:
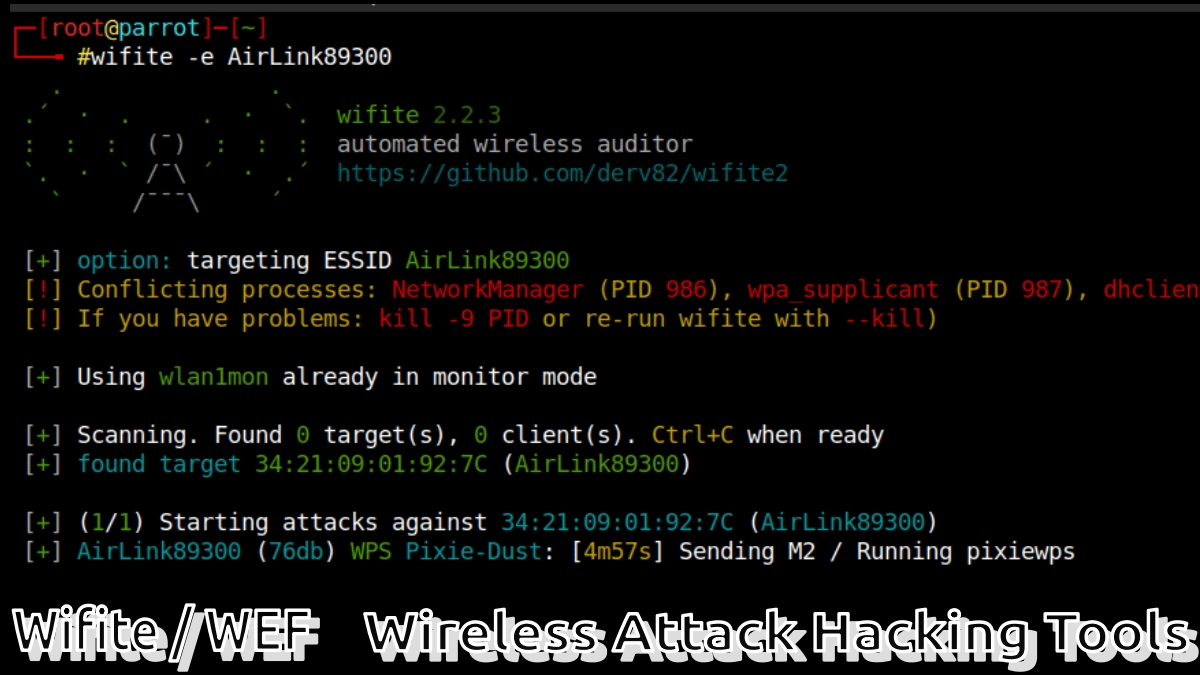
"Wifite is an application specifically designed for Linux, with the goal of being an automated wireless attack tool. Consequently, it is specially designed to be used on GNU/Linux Distributions in the field of Hacking and Pentesting, such as: Kali Linux, Parrot, Pentoo, BackBox; and any other Linux distribution with wireless drivers patched for code injection".
Other important information about Wifite is that you must run as root, since it is required by the set of programs you use. For this reason, and as good practice in terms of Computer Security, Hacking or Pentesting, the ideal is to use said application from a Live CD Kali Linux bootable, or a bootable USB stick (for persistent), or a Virtual Machine, as long as you have a wireless USB Dongle handy.
Furthermore, Wifite assumes that in the running hardware there exists a wireless card and the appropriate drivers which are patched for injection and promiscuous/monitor mode. Last but not least, its developer recommends test your new development called wifi 2, in case of not obtaining satisfactory results with Wifite. This is because Wifite does not receive frequent updates and has many bugs, while Wifite 2 adds more features, bug fixes and reliability.
Later, in another separate post, we will address its installation and use in more detailHowever, all that information is well detailed on the GitHub site, for both versions.
What is WEF?
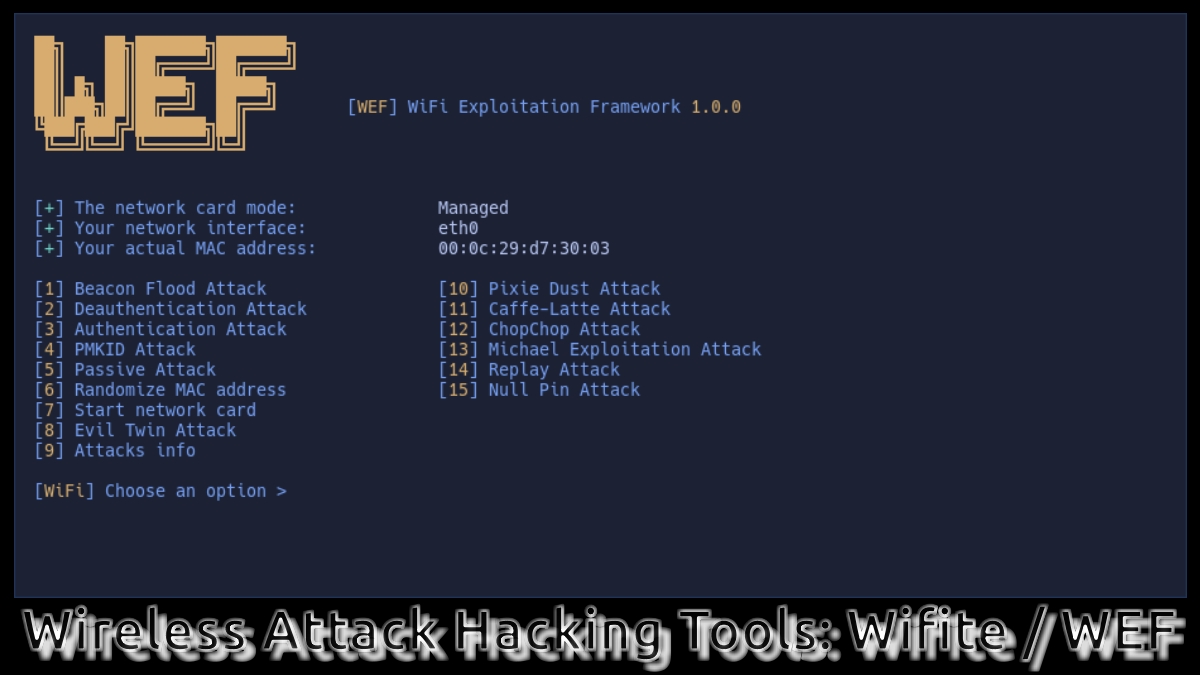
This other app called WEF (WiFi Exploitation Framework) according to your official website on GitHub It is briefly described as follows:
"A fully offensive framework for 802.11 networks and protocols with different types of attacks for WPA/WPA2 and WEP, automated hash cracking, and much more. Tested and supported on Kali Linux, Parrot OS and Arch Linux".
And just like other similar software, is capable of attacks of the following type:
- Deauthentication attack.
- Authentication Attack.
- Beacon Flood Attack.
- PMKID Attack.
- EvilTwin Attack (EvilTwin Attack).
- Passive/Stealthy Attack.
- Pixie Dust Attack.
- Null Pin Attack.
- Attacks to the WEP protocol (WEP Protocol Attacks).
- Michael Exploitation Attack.
fly more information about its installation and use is in the Wiki from their GitHub site.
Other popular Wireless Attack Hacking Tools apps
Although, when installing and using Wifi and WEF, they install and use other apps in the scope of the “Wireless Attack Hacking Tools”, we can mention separately some of them and other existing ones, such as:
- Aircrack
- airgeddon
- Fern Wifi Cracker
- Kismet
- Wifiphisher
- Others more: link 1 y Listing 2.

Kali Linux 2022.4 is the latest version of the distribution released this year.
GNU / Linux Distros for Hacking and Pentesting
And finally, we leave you a great list with many of the existing ones GNU / Linux Distros, specially dedicated to IT domain of the Hacking and Pentesting, where they could use these apps (Wife and WEF):
- Time: Based on Debian.
- Parrot: Based on Debian.
- BackBox: Based on Ubuntu.
- Caine: Based on Ubuntu.
- Demon: Based on Debian.
- Bugtraq: Based on Ubuntu, Debian and OpenSUSE.
- ArchStrike: Based on Arch.
- BlackArch: Based on Arch.
- Pentoo: Based on Gentoo.
- Fedora Security Lab: Based on Fedora.
- WiFisLax: Based on Slackware.
- Dracos: Based on based on LFS (Linux from Scratch).
- Samurai Web Testing Framework: Based on Ubuntu.
- Network Security Toolkit: Based on Fedora.
- DEFT: Based on Ubuntu.
- OnionSecurity: Based on Ubuntu.
- Santoku: Based on based on LFS.

Summary
In summary, Wifi and WEF They are undoubtedly 2 useful and interesting applications to know and try at some point, if you are one of those passionate about computers and computing, who likes Ethical hacking. These apps in the field of “Wireless Attack Hacking Tools” will undoubtedly allow you to get started in the knowledge of the exploration of wireless network traffic, facilitating, among many things, the power find faults or weaknesses in wireless networks. Everything in favor of, improve and help others, in the field of Computer Security.
Finally, do not forget to contribute your opinion on today's topic, via comments. And if you liked this post, do not stop sharing it with others. Also, remember visit our home page en «DesdeLinux» to explore more news, and join our official channel of Telegram from DesdeLinux, West group for more information on today's topic.