Let's continue, not without first consulting:
- Directory Service with LDAP. Introduction.
- Directory Service with LDAP [2]: NTP and dnsmasq.
- Directory Service with LDAP [3]: Isc-DHCP-Server and Bind9.
- Directory Service with LDAP [4]: OpenLDAP (I)
In this post we will see:
- Local user authentication
- Populate the database
- Manage the database using console utilities
- Summary so far ...
Local user authentication
After we have the OpenLDAP server running, if we want to test or have local authentication of registered users -or that we will register- in the Directory, we must install and configure the necessary packages.
In Squeeze, the packages involved are:
libnss-ldap: Provides the Name Exchange Service (NSS Name Service Switch) that allows the LDAP server to act as a name server.
It means providing the information about User Accounts, Group IDs, information about the host, Aliases, NetGroups, and basically any other data that is normally obtained from plain text files such as / Etc / passwd, / Etc / group, etc., or a service NIS.
libpam-ldap"Pluggable Authentication Module for LDAP", Or Module PAM for LDAP. Provides an interface between the LDAP server and the authentication system through PAM.
nscd"Name Service Cache Daemon“, Or Daemon for the Name Service Cache. It handles the search for passwords, groups and hosts and stores the results of the searches in the cache for future reference.
: ~ # aptitude install libnss-ldap finger
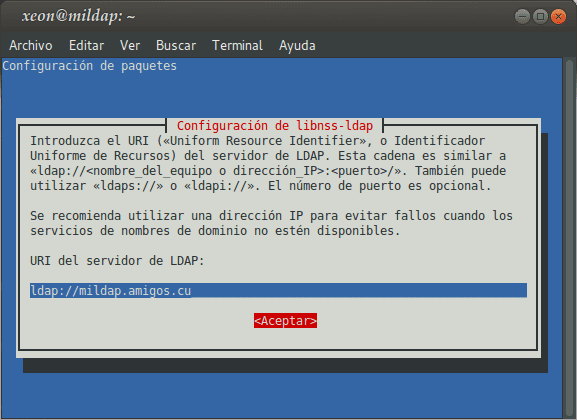
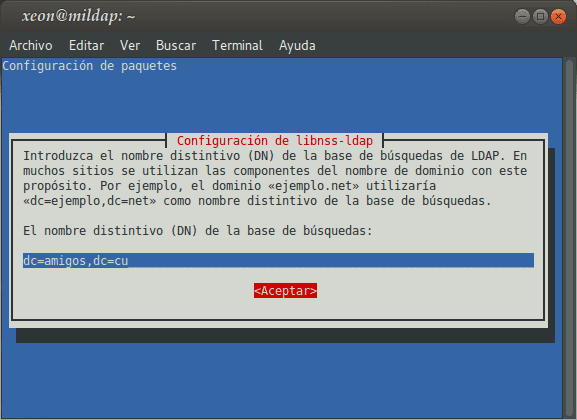
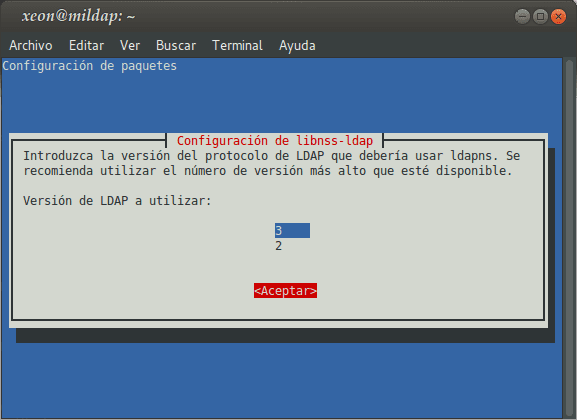
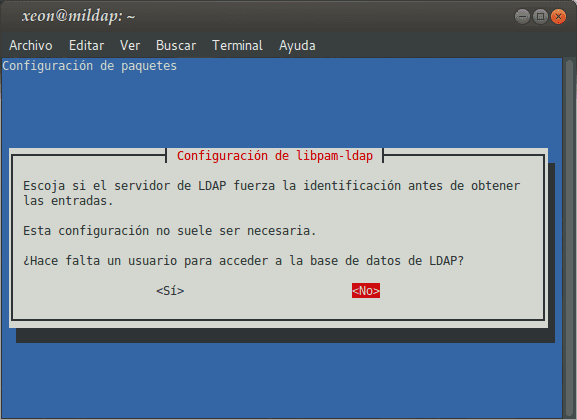
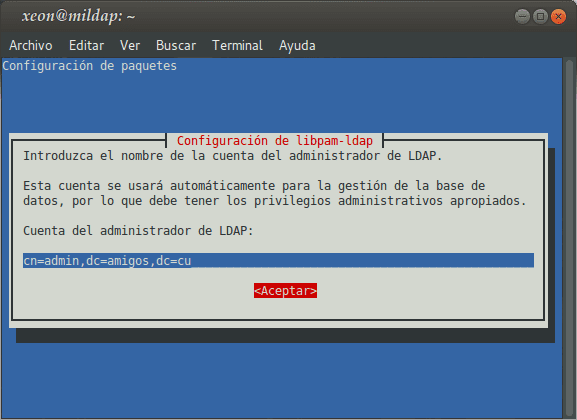
Installing the package libnss-ldap, which also installs as dependencies libpam-ldap already the devil nscd, will take us through a Configuration Wizard, whose questions we must answer appropriately:
If we want to reconfigure the packages libnss-ldap I libpam-ldap, we must execute:
: ~ # dpkg-reconfigure libnss-ldap : ~ # dpkg-reconfigure libpam-ldap
Later we modify the file /etc/nsswitch.conf and we leave it with the following content:
: ~ # nano /etc/nsswitch.conf # /etc/nsswitch.conf # # Example configuration of GNU Name Service Switch functionality. # If you have the `glibc-doc-reference 'and` info' packages installed, try: # `info libc" Name Service Switch "'for information about this file. passwd: compat ldap group: compat ldap shadow: compat ldap hosts: files dns networks: files protocols: db files services: db files ethers: db files rpc: db files netgroup: nis
For the changes made to the file /etc/nsswitch.conf take effect, we restart the service nscd:
: ~ # service nscd restart
Important detail is to modify the file /etc/pam.d/common-session for the user folder to be created on the local server when logging on to it, a user registered in the Directory:
: ~ # nano /etc/pam.d/common-session [----] session required pam_mkhomedir.so skel = / etc / skel / umask = 0022 ### The above line must be included BEFORE # here are the per-package modules (the "Primary" block) [----]
Populate the database
To populate the Directory database or start it, we must add the main Organizational Units, register at least one User Group, and add a user. To do this, we create a file in LDIF format, which we will later add to the Directory, with the following content:
: ~ # nano content.ldif dn: ou = People, dc = friends, dc = cu objectClass: organizationalUnit ou: People dn: ou = Groups, dc = friends, dc = cu objectClass: organizationalUnit ou: Groups dn: cn = rings, ou = Groups, dc = friends, dc = cu objectClass: posixGroup cn: rings gidNumber: 10000 dn: uid = frodo, ou = People, dc = friends, dc = cu objectClass: inetOrgPerson objectClass: posixAccount objectClass: shadowAccount uid: frodo sn: Bagins givenName: Frodo cn : Frodo Bagins displayName: Frodo Bagins uidNumber: 10000 gidNumber: 10000 userPassword: frodo mail: frodo@amigos.cu gecos: Frodo Bagins loginShell: / bin / bash homeDirectory: / home / frodo
We add the content of the file to the Directory:
: ~ # ldapadd -x -D cn = admin, dc = friends, dc = cu -W -f content.ldif Enter LDAP Password: adding new entry "ou = People, dc = friends, dc = cu" adding new entry "ou = Groups, dc = friends, dc = cu" adding new entry "cn = rings, ou = Groups, dc = friends, dc = cu "adding new entry" uid = frodo, ou = People, dc = friends, dc = cu "
We carry out the relevant checks:
: ~ # id frodo uid = 10000 (frodo) gid = 10000 (rings) groups = 10000 (rings) : ~ # getent passwd | grep frodo frodo: x: 10000: 10000: Frodo Bagins: / home / frodo: / bin / bas : ~ # finger frodo Login: frodo Name: Frodo Bagins Directory: / home / frodo Shell: / bin / bash Never logged in. No mail. No Plan. : ~ # ldapsearch -Y EXTERNAL -H ldapi: /// -b uid = frodo, ou = People, dc = friends, dc = cu
Now we have a Directory Service that we must manage !!!. We will develop two ways: the first through the package ldapscripts, and the second, which we will address in the next article, will be through theLdap Account Manager.
We should also say that the package ldap-utils, provides a whole series of useful commands to manage the Directory. To know what those commands are, we execute:
: ~ # dpkg -L ldap-utils | grep / bin / usr / bin / usr / bin / ldapmodrdn / usr / bin / ldapurl / usr / bin / ldapdelete / usr / bin / ldapwhoami / usr / bin / ldapexop / usr / bin / ldappasswd / usr / bin / ldapcompare / usr / bin / ldapsearch / usr / bin / ldapmodify / usr / bin / ldapadd
To learn more about each command, we recommend running man. Giving an explanation of each would make the article very long.
Manage the database using console utilities
We select the package ldapscripts for such a task. The installation and configuration procedure is as follows:
: ~ # aptitude install ldapscripts : ~ # cp /etc/ldapscripts/ldapscripts.conf \ /etc/ldapscripts/ldapscripts.conf.original : ~ # cp / dev / null /etc/ldapscripts/ldapscripts.conf : ~ # nano /etc/ldapscripts/ldapscripts.conf SERVER = localhost BINDDN = 'cn = admin, dc = friends, dc = cu' BINDPWDFILE = "/ etc / ldapscripts / ldapscripts.passwd" SUFFIX = 'dc = friends, dc = cu' GSUFFIX = 'ou = Groups' USUFFIX = 'ou = People' # MSUFFIX = 'ou = Computers' GIDSTART = 10001 UIDSTART = 10001 # MIDSTART = 10000 # OpenLDAP client commands LDAPSEARCHBIN = "/ usr / bin / ldapsearch" LDAPADDBIN = "/ usr / bin / ldapadd" LDAPDELETEBIN = " / usr / bin / ldapdelete "LDAPMODIFYBIN =" / usr / bin / ldapmodify "LDAPMODRDNBIN =" / usr / bin / ldapmodrdn "LDAPPASSWDBIN =" / usr / bin / ldappasswd "GCLASS =" posixGroup "# UTEMPLATE =" / etc / etc. /ldapadduser.template "PASSWORDGEN =" echo% u " ### Notice that the scripts use the commands of the ### ldap-utils package : ~ # sh -c "echo -n 'tupassowrd'> \ /etc/ldapscripts/ldapscripts.passwd" : ~ # chmod 400 /etc/ldapscripts/ldapscripts.passwd : ~ # cp /usr/share/doc/ldapscripts/examples/ldapadduser.template.sample \ /etc/ldapscripts/ldapadduser.template : ~ # nano /etc/ldapscripts/ldapadduser.template dn: uid = , , objectClass: inetOrgPerson objectClass: posixAccount objectClass: shadowAccount cn: sn: givenName: displayName: uid: uidNumber: gidNumber: homeDirectory: loginShell: mail: geckos: description: User Account : ~ # nano /etc/ldapscripts/ldapscripts.conf ## we remove the comment UTEMPLATE = "/ etc / ldapscripts / ldapadduser.template"
Let's try adding the user Strider The King to user group rings and let's check the data entered:
: ~ # ldapadduser strides rings [dn: uid = strides, ou = People, dc = friends, dc = cu] Enter value for "sn": The King [dn: uid = strides, ou = People, dc = friends, dc = cu] Enter value for "givenName": Strides [dn: uid = strides, ou = People, dc = friends, dc = cu] Enter value for "displayName": Strides El Rey [dn: uid = strides, ou = People, dc = friends, dc = cu] Enter value for "mail": trancos@amigos.cu Successfully added user trancos to LDAP Successfully set password for user trancos root @ mildap: ~ # ldapfinger strides dn: uid = strides, ou = People, dc = friends, dc = cu objectClass: inetOrgPerson objectClass: posixAccount objectClass: shadowAccount cn: strides sn: El Rey givenName: Strides displayName: Strides El Rey uid: strides uidNumber: 10002 gidNumber: 10000 homeDirectory: / home / trancos loginShell: / bin / bash mail: trancos@amigos.cu gecos: trancos description: User Account userPassword :: e1NTSEF9UnlmcWxCem5iUzBuSzQzTkM3ZFRFcTUwV2VsVnBqRm8 =
Let's declare a password to the user Frodo, let's list the "DN”Of registered users, and delete the newly created user Striders:
: ~ # ldapsetpasswd frodo Changing password for user uid = frodo, ou = People, dc = friends, dc = cu New Password: Retype New Password: Successfully set password for user uid = frodo, ou = People, dc = friends, dc = cu : ~ # lsldap -u | grep dn dn: uid = frodo, ou = People, dc = friends, dc = cu dn: uid = strides, ou = People, dc = friends, dc = cu : ~ # ldapfinger frodo dn: uid = frodo, ou = People, dc = friends, dc = cu objectClass: inetOrgPerson objectClass: posixAccount objectClass: shadowAccount uid: frodo sn: Bagins givenName: Frodo cn: Frodo Bagins displayName: Frodo Bagins uidNumber: 10000 gidNumber: 10000 mailNumber: 1 mail : frodo@amigos.cu gecos: Frodo Bagins loginShell: / bin / bash homeDirectory: / home / frodo userPassword :: e9NTSEF4TnI3ZXN1YXA1VnplK1ZIZXZzbFZKaWF5SVdWeUXNUMXoVjA = : ~ # ldapdeleteuser strides Successfully deleted user uid = strides, ou = People, dc = friends, dc = cu from LDAP : ~ # lsldap -u | grep dn dn: uid = frodo, ou = People, dc = friends, dc = cu
Let's check that Local Authentication works correctly:
: ~ # ssh frodo @ mildap frodo @ mildap's password: Linux mildap 2.6.32-5-686 # 1 SMP Fri May 10 08:33:48 UTC 2013 i686 [---] Debian GNU / Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law . Last login: Tue Feb 18 18:54:01 2014 from mildap.amigos.cu frodo @ mildap: ~ $ pwd / home / frodo frodo @ mildap: ~ $
There are many examples that we can write, but unfortunately the article would be very long. We always say that we give an entry point to the issues of services in general. It is impossible to replace the extensive documentation in a single post.
To learn more about the package ldapscripts and its commands, please and consult man ldapscripts.
So far, our Simple Directory Service based on OpenLDAP works fine.
Summary so far ...
Many managers of services in business networks, when they take charge of one with services based on Microsoft products, if they want to migrate to Linux, they consider the migration of Domain Controllers among other services.
If they do not choose a third-party product such as ClearOS or Zentyal, or if for other reasons they wish to become independent, then they undertake the painstaking task of becoming their own Domain Controller, or from Samba 4 their own Active Directory.
Then the problems begin and some other disappointments. Operating errors. They do not find the location of the problems to be able to solve them. Repeated installation attempts. Partial operations of the services. And a long list of problems.
The Base of any Domain Controller or Active Directory in Linux, based on OpenLDAP plus Samba, necessarily goes through the basic knowledge of What is an LDAP server, how is it installed, how is it configured and managed, and so on?. Those who have read the extensive documentation of Samba, will know well what we mean.
It is precisely to answer that question that we have written the entire series of articles up to this one, and we will continue with those that are necessary. We hope they are useful to you.





Excellent your post Fico, a query, with OpenLDAP, can domain policies be created? to apply them to connected users, such as the screen saver being activated after 5 minutes without activity, configuring the wallpaper, preventing certain applications from running, configuring startup scripts, etc.
Regards,
Oscar
Thanks for comment !!!. Oscar, remember that those policies, on Linux, are implemented differently when it comes to Linux clients. GNOME brings a tool to achieve it that now I don't remember its name. If I know we can establish user account policies directly in OpenLDAP. Many ask me the same question and I always answer more or less the same. 🙂 Those security policies only apply to Microsoft clients, NOT Linux clients. They are two different philosophies. An Active Directory is a proprietary application based on OpenLDAP, a personal Kerberos from Microsft and the Network Administrator, which I don't know what they call it now. Before, it was in Lan Manager. We cannot think of emulating an Active Directory only with LDAP. We would have to integrate Samba or use Samba 4 to see if it can be achieved. And my friend, I haven't even taken a single look at Samba 4. 🙂 Nor do I know if Zentyal with Active Directory can apply them ... but that software is not only OpenLDAP. It's OpenLDAP + Samba + Kerberos + other things that I don't know well. 🙂 In this series I only deal with OpenLDAP, and if you follow it you will see that in the compendium that I am writing of the entire series, plus other essential services, everything is based on authentication against the OpenLDAP Directory.
regards