Hello friends!. Please, I repeat, read before «Introduction to a Network with Free Software (I): Presentation of ClearOS»And download the ClearOS Step-by-Step installation images package (1,1 mega), to be aware of what we are talking about. Without that reading it will be difficult to follow us.
System Security Service Daemon
The program SSSD o Daemon for the System Security Service, is a project of Fedora, which was born from another project -also from Fedora- called FreeIPA. According to its own creators, a short and freely translated definition would be:
SSSD is a service that provides access to different Identity and Authentication providers. It can be configured for a native LDAP domain (LDAP-based identity provider with LDAP authentication), or for an LDAP identity provider with Kerberos authentication. SSSD provides the interface to the system through NSS y PAM, and an insertable Back End to connect to multiple and different account origins.
We believe that we are facing a more comprehensive and robust solution for the identification and authentication of registered users in an OpenLDAP, than those addressed in the preceding articles, an aspect that is left to the discretion of everyone and their own experiences.
The solution proposed in this article is the most recommended for mobile computers and laptops, since it allows us to work disconnected, since the SSSD stores the credentials on the local computer.
Example network
- Domain Controller, DNS, DHCP: ClearOS Enterprise 5.2sp1.
- Controller Name: centos
- Domain Name: friends.cu
- Controller IP: 10.10.10.60
- ---------------
- Debian version: wheezy.
- Name of the team: debian7
- IP adress: Using DHCP
We check that the LDAP server is working
We modify the file /etc/ldap/ldap.conf and install the package ldap-utils:
: ~ # nano /etc/ldap/ldap.conf [----] BASE dc = friends, dc = cu URI ldap: //centos.amigos.cu [----]
: ~ # aptitude install ldap-utils: ~ $ ldapsearch -x -b 'dc = friends, dc = cu' '(objectclass = *)': ~ $ ldapsearch -x -b dc = friends, dc = cu 'uid = strides' : ~ $ ldapsearch -x -b dc = friends, dc = cu 'uid = legolas' cn gidNumber
With the last two commands, we check the availability of the OpenLDAP server of our ClearOS. Let's take a good look at the outputs of the previous commands.
Important: we have also verified that the Identification Service in our OpenLDAP server works correctly.
We install the sssd package
It is also recommended to install the package finger to make checks more drinkable than the ldapsearch:
: ~ # aptitude install sssd finger
Upon completion of the installation, the service ssd does not start due to missing file /etc/sssd/sssd.conf. The output of the installation reflects this. Therefore, we must create that file and leave it with the next minimum content:
: ~ # nano /etc/sssd/sssd.conf [sssd] config_file_version = 2 services = nss, pam # SSSD will not start if you do not configure any domains. # Add new domain configurations as [domain / ] sections, and # then add the list of domains (in the order you want them to be # queried) to the "domains" attribute below and uncomment it. domains = amigos.cu [nss] filter_groups = root filter_users = root reconnection_retries = 3 [pam] reconnection_retries = 3 # LDAP domain [domain / amigos.cu] id_provider = ldap auth_provider = ldap chpass_provider = ldap # ldap_schema can be set to "rfc2307", which stores group member names in the # "memberuid" attribute, or to "rfc2307bis", which stores group member DNs in # the "member" attribute. If you do not know this value, ask your LDAP # administrator. # works with ClearOS ldap_schema = rfc2307 ldap_uri = ldap: //centos.amigos.cu ldap_search_base = dc = friends, dc = cu # Note that enabling enumeration will have a moderate performance impact. # Consequently, the default value for enumeration is FALSE. # Refer to the sssd.conf man page for full details. enumerate = false # Allow offline logins by locally storing password hashes (default: false). cache_credentials = true ldap_tls_reqcert = allow ldap_tls_cacert = /etc/ssl/certs/ca-certificates.crt
Once the file has been created, we assign the corresponding permissions and restart the service:
: ~ # chmod 0600 /etc/sssd/sssd.conf : ~ # service sssd restart
If we want to enrich the content of the previous file, we recommend executing man sssd.conf and / or consult the existing documentation on the Internet, starting with the links at the beginning of the post. Also consult man sssd-ldap. The package ssd includes an example in /usr/share/doc/sssd/examples/sssd-example.conf, which can be used to authenticate against a Microsoft Active Directory.
Now we can use the most drinkable commands finger y getent:
: ~ $ finger strides Login: strides Name: Strides El Rey Directory: / home / strides Shell: / bin / bash Never logged in. No mail. No Plan. : ~ $ sudo getent passwd legolas legolas: *: 1004: 63000: Legolas The Elf: / home / legolas: / bin / bash
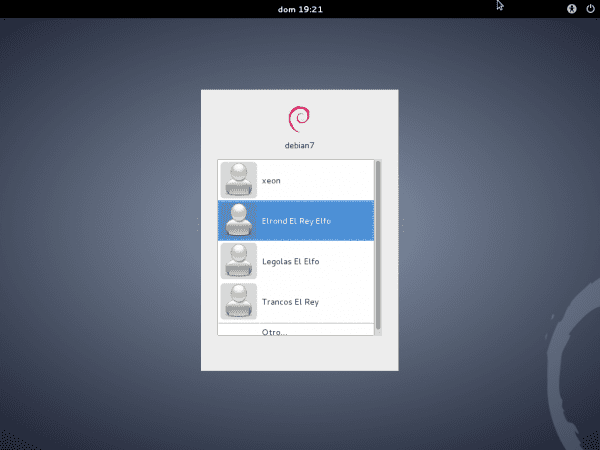
We still cannot authenticate as a user of the LDAP server. Before we must modify the file /etc/pam.d/common-session, so that the user's folder is automatically created when they start their session, if it does not exist, and then reboot the system:
[----] session required pam_mkhomedir.so skel = / etc / skel / umask = 0022 ### The above line must be included BEFORE # here are the per-package modules (the "Primary" block) [----]
We restart our Wheezy:
: ~ # reboot
After logging in, disconnect the network using the Connection Manager and log out and back in. Faster nothing. Run in a terminal ifconfig and they will see that the eth0 it is not configured at all.
Activate the network. Please log out and log in again. Check again with ifconfig.
Of course, to work offline, it is necessary to log in at least once while OpenLDAP is online, so that the credentials are saved on our computer.
Let's not forget to make the external user registered in OpenLDAP a member of the necessary groups, always paying attention to the user created during the installation.
Note:
Declare option ldap_tls_reqcert = never, in the File /etc/sssd/sssd.conf, constitutes a security risk as stated on the page SSSD - FAQ. The default value is «demand«. See man sssd-ldap. However, in the chapter 8.2.5 Configuring Domains From the Fedora documentation, the following is stated:
SSSD does not support authentication over an unencrypted channel. Consequently, if you want to authenticate against an LDAP server, either
TLS/SSLorLDAPSis required.SSSD it does not support authentication over an unencrypted channel. Therefore, if you want to authenticate against an LDAP server, it will be necessary TLS / SLL o LDAP.
We personally think that the solution addressed it is sufficient for an Enterprise LAN, from a security point of view. Through the WWW Village, we recommend implementing an encrypted channel using TLS or «Transport Security Layer », between the client computer and the server.
We try to achieve this from the correct generation of Self Signed certificates or «self-signed “On the ClearOS server, but we couldn't. It is in fact a pending issue. If any reader knows how to do it, welcome to explain it!
Excellent.
Greetings ElioTime3000 and thanks for commenting !!!
Greetings eliotime3000 and thanks for the praise of the article !!!
Excellent! I want to extend a huge congratulations to the author of the publication for sharing his vast knowledge and to the blog for allowing the publication of it.
Thank you so much!
Thank you very much for your praise and comment !!! Strength that you give me to continue sharing knowledge with the community, in which we all learn.
Good article !, note that regarding the use of certificates, when you generate the certificate you must add to the ldap configuration (cn = config):
olcLocalSSF: 71
olcTLSCACertificateFile: / path / to / ca / cert
olcTLSCertificateFile: / path / to / public / cert
olcTLSCertificateKeyFile: / path / to / private / key
olcTLSVerifyClient: try
olcTLSCipherSuite: + RSA: + AES-256-CBC: + SHA1
With this (and generating the certificates) you will have SSL support.
Regards!
Thank you for your contribution !!! However, I publish 7 articles about OpenLDAP in:
http://humanos.uci.cu/2014/01/servicio-de-directorio-con-ldap-introduccion/
https://blog.desdelinux.net/ldap-introduccion/
In them I emphasize the use of Start TLS before SSL, which is recommended by openldap.org. Greetings @phenobarbital, and thank you very much for commenting.
My email is federico@dch.ch.gob.cu, in case you want to exchange more. Accessing the Internet is very slow for me.
For TLS the configuration is the same, remembering that with SSL the transport is made transparent over an encrypted channel, while in TLS a two-way encryption is negotiated for the transport of data; with TLS the handshake can be negotiated on the same port (389) while with SSL the negotiation is done on an alternative port.
Change the following:
olcLocalSSF: 128
olcTLSVerifyClient: allow
olcTLSCipherSuite: NORMAL
(if you are paranoid about security you use:
olcTLSCipherSuite: SECURE256:!AES-128-CBC:!ARCFOUR-128:!CAMELLIA-128-CBC:!3DES-CBC:!CAMELLIA-128-CBC)
and restart, you will see later with:
gnutls-cli-debug -p 636 ldap.ipm.org.gt
Resolving 'ldap.ipm.org.gt'…
Checking for SSL 3.0 support…yes
Checking whether% COMPAT is required… no
Checking for TLS 1.0 support… yes
Checking for TLS 1.1 support… yes
Checking fallback from TLS 1.1 to… N / A
Checking for TLS 1.2 support… yes
Checking for Safe renegotiation support… yes
Checking for Safe renegotiation support (SCSV)… yes
With which the support for TLS is also enabled, you use 389 (or 636) for TLS and 636 (ldaps) for SSL; they are completely independent of each other and you don't need to have one disabled to use the other.
Regards!