General index of the series: Computer Networks for SMEs: Introduction
Hello friends and friends!
With this article I say goodbye to the Community DesdeLinux. A special farewell for a Special Community. From now on I will be in my personal project which you can see at http://www.gigainside.com.
The main objective of the post is to offer a «Big Picture»About the Authentication Services with Free Software that we have at our disposal. At least that is our intention. Therefore it will be long, despite the fact that we know that it is against the general rules of writing articles. We hope the System Administrators appreciate it.
We want to point out that the common protocol to many of the modern authentication systems is the LDAP, and that it is not idle to study it carefully, from the study material that we will find on the official site http://www.openldap.org/.
We will not give detailed definitions - or links - on aspects dealt with in previous articles, or on those whose description can be easily accessible on Wikipedia or other sites or articles on the Internet, so as not to lose the objectivity of the message we want to give. We will also use a valid mix of names in English and Spanish, as we consider that most systems were born with names in English and it is very beneficial for a Sysadmin to assimilate them in their original language.
- PAM: Pluggable Authentication Module.
- NIS: Network_Information_Service.
- LDAP: Lightweight Directory Access Protocol.
- Kerberos: Security protocol to authenticate users, computers and services centrally on a network, verifying their credentials against existing entries in the Kerberos database.
- DS: Directory Server or Directory Service
- AD–DC: Active Directory - Domain Controler
PAM
We dedicate a small series to this type of local authentication, which you will see in daily practice that it is widely used when, for example, we join a workstation to a Domain Controller or an Active Directory; to map users stored in external LDAP databases as if they were local users; to map users stored in the Domain Controller of an Active Directory as if they were local users, and so on.
- Squid + PAM Authentication on CentOS 7.
- Local user and group management
- Authoritative DNS Server NSD + Shorewall
- Prosody IM and local users
- Postfix + Dovecot + Squirrelmail and local users
NIS
De Wikipedia:
- Network Information System (known by its acronym NIS, which in Spanish means Network Information System), is the name of a client-server directory services protocol developed by Sun Microsystems for sending configuration data in distributed systems such as names of users and hosts between computers on a network.NIS is based on ONC RPC, and consists of a server, a client-side library, and various administration tools.
NIS was originally called the Yellow Pages, or YP, which is still used to refer to it. Unfortunately, that name is a trademark of British Telecom, which required Sun to drop that name. However YP remains a prefix in the names of most NIS-related commands, such as ypserv and ypbind.
DNS serves a limited range of information, the most important being the correspondence between the node name and the IP address. For other types of information, there is no such specialized service. On the other hand, if you only manage a small LAN without Internet connectivity, it doesn't seem worth setting up DNS. This is why Sun developed the Network Information System (NIS). NIS provides generic database access capabilities that can be used to distribute, for example, the information contained in passwd and groups files to all nodes on your network. This makes the network look like a single system, with the same accounts on all nodes. Similarly, NIS can be used to distribute the node name information contained in / etc / hosts to all machines on the network.
Today NIS is available in practically all Unix distributions, and there are even free implementations. BSD Net-2 published one that has been derived from a public domain reference implementation donated by Sun. The library code for the client part of this version has existed in the GNU / Linux libc for a long time, and the administration programs were ported to GNU / Linux by Swen Thümmler. However, an NIS server is missing as of the reference implementation.
Peter Eriksson has developed a new implementation called NYS. It supports both basic NIS and the enhanced version of Sun NIS +. [1] NYS not only provides a number of NIS tools and a server, but also adds a whole new set of library functions that you need to compile into your libc if you want to use them. This includes a new configuration scheme for node name resolution that replaces the current scheme used by the "host.conf" file.
The GNU libc, known as libc6 in the GNU / Linux community, includes an updated version of the traditional NIS support developed by Thorsten Kukuk. It supports all the library functions provided by NYS, and also uses the advanced NYS configuration scheme. The tools and the server are still needed, but using the GNU libc saves the work of patching and recompiling the library
.
Computer and domain name, network interface and resolver
- We start from a clean installation -without graphical interface- of a Debian 8 "Jessie". The domain swl.fan means "Fans of Free Software." What better name than this?.
root @ master: ~ # hostname
master
root @ master: ~ # hostname -f
master.swl.fan
root @ master: ~ # ip addr 1: lo: mtu 65536 qdisc noqueue state UNKNOWN group default link / loopback 00: 00: 00: 00: 00: 00 brd 00: 00: 00: 00: 00: 00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 :: 1/128 scope host valid_lft forever preferred_lft forever 2: eth0: mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link / ether 00: 0c: 29: 4c: 76: d9 brd ff: ff: ff: ff: ff: ff inet 192.168.10.5/24 brd 192.168.10.255 scope global eth0 valid_lft forever preferred_lft forever inet6 fe80 :: 20c: 29ff: fe4c: 76d9 / 64 scope link valid_lft forever preferred_lft forever
root @ master: ~ # cat /etc/resolv.conf
search swl.fan nameserver 127.0.0.1
Installation of bind9, isc-dhcp-server and ntp
bind9
root @ master: ~ # aptitude install bind9 bind9-doc Nmap
root @ master: ~ # systemctl status bind9
root @ master: ~ # nano /etc/bind/named.conf
include "/etc/bind/named.conf.options"; include "/etc/bind/named.conf.local"; include "/etc/bind/named.conf.default-zones";
root @ master: ~ # cp /etc/bind/named.conf.options \ /etc/bind/named.conf.options.original
root @ master: ~ # nano /etc/bind/named.conf.options
options {directory "/ var / cache / bind"; // If there is a firewall between you and nameservers you want // to talk to, you may need to fix the firewall to allow multiple // ports to talk. See http://www.kb.cert.org/vuls/id/800113
// If your ISP provided one or more IP addresses for stable // nameservers, you probably want to use them as forwarders. // Uncomment the following block, and insert the addresses replacing // the all-0's placeholder. // forwarders {// 0.0.0.0; //}; // =============================================== ===================== $ // If BIND logs error messages about the root key being expired, // you will need to update your keys. See https://www.isc.org/bind-keys
// =============================================== ===================== $ // We don't want DNSSEC
dnssec-enable no;
// dnssec-validation auto; auth-nxdomain no; # conform to RFC1035 listen-on-v6 {any; }; // For checks from localhost and sysadmin // through dig swl.fan axfr // We don't have Slave DNS ... until now
allow-transfer {localhost; 192.168.10.1; };
}; root @ master: ~ # named-checkconf
root @ master: ~ # nano /etc/bind/zones.rfcFreeBSD
// Shared Address Space (RFC 6598)
zone "64.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "65.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "66.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "67.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "68.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "69.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "70.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "71.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "72.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "73.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "74.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "75.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "76.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "77.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "78.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "79.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "80.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "81.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "82.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "83.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "84.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "85.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "86.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "87.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "88.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "89.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "90.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "91.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "92.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "93.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "94.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "95.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "96.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "97.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "98.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "99.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "100.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "101.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "102.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "103.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "104.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "105.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "106.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "107.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "108.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "109.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "110.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "111.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "112.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "113.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "114.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "115.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "116.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "117.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "118.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "119.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "120.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "121.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "122.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "123.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "124.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "125.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "126.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
zone "127.100.in-addr.arpa" { type master; file "/etc/bind/db.empty"; };
// Link-local / APIPA (RFCs 3927, 5735 and 6303)
zone "254.169.in-addr.arpa" {type master; file "/etc/bind/db.empty"; };
// IETF protocol assignments (RFCs 5735 and 5736)
zone "0.0.192.in-addr.arpa" {type master; file "/etc/bind/db.empty"; };
// TEST-NET- [1-3] for Documentation (RFCs 5735, 5737 and 6303)
zone "2.0.192.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "100.51.198.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "113.0.203.in-addr.arpa" {type master; file "/etc/bind/db.empty"; };
// IPv6 Example Range for Documentation (RFCs 3849 and 6303)
zone "8.bd0.1.0.0.2.ip6.arpa" {type master; file "/etc/bind/db.empty"; };
// Domain Names for Documentation and Testing (BCP 32)
zone "test" {type master; file "/etc/bind/db.empty"; }; zone "example" {type master; file "/etc/bind/db.empty"; }; zone "invalid" {type master; file "/etc/bind/db.empty"; }; zone "example.com" {type master; file "/etc/bind/db.empty"; }; zone "example.net" {type master; file "/etc/bind/db.empty"; }; zone "example.org" {type master; file "/etc/bind/db.empty"; };
// Router Benchmark Testing (RFCs 2544 and 5735)
zone "18.198.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "19.198.in-addr.arpa" {type master; file "/etc/bind/db.empty"; };
// IANA Reserved - Old Class E Space (RFC 5735)
zone "240.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "241.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "242.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "243.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "244.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "245.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "246.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "247.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "248.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "249.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "250.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "251.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "252.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "253.in-addr.arpa" {type master; file "/etc/bind/db.empty"; }; zone "254.in-addr.arpa" {type master; file "/etc/bind/db.empty"; };
// IPv6 Unassigned Addresses (RFC 4291)
zone "1.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "3.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "4.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "5.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "6.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "7.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "8.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "9.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "a.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "b.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "c.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "d.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "e.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "0.f.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "1.f.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "2.f.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "3.f.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "4.f.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "5.f.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "6.f.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "7.f.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "8.f.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "9.f.ip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "afip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "bfip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "0.efip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "1.efip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "2.efip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "3.efip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "4.efip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "5.efip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "6.efip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "7.efip6.arpa" {type master; file "/etc/bind/db.empty"; };
// IPv6 ULA (RFCs 4193 and 6303)
zone "cfip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "dfip6.arpa" {type master; file "/etc/bind/db.empty"; };
// IPv6 Link-Local (RFCs 4291 and 6303)
zone "8.efip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "9.efip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "aefip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "befip6.arpa" {type master; file "/etc/bind/db.empty"; };
// IPv6 Deprecated Site-Local Addresses (RFCs 3879 and 6303)
zone "cefip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "defip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "eefip6.arpa" {type master; file "/etc/bind/db.empty"; }; zone "fefip6.arpa" {type master; file "/etc/bind/db.empty"; };
// IP6.INT is Deprecated (RFC 4159)
zone "ip6.int" {type master; file "/etc/bind/db.empty"; };
root @ master: ~ # nano /etc/bind/named.conf.local
// // Do any local configuration here // // Consider adding the 1918 zones here, if they are not used in your // organization include "/etc/bind/zones.rfc1918";
include "/etc/bind/zones.rfcFreeBSD";
// Declaration of the name, type, location, and update permission // of the DNS Record Zones // Both Zones are MASTER zone "swl.fan" {type master; file "/var/lib/bind/db.swl.fan"; }; zone "10.168.192.in-addr.arpa" {type master; file "/var/lib/bind/db.10.168.192.in-addr.arpa"; };
root @ master: ~ # named-checkconf
root @ master: ~ # nano /var/lib/bind/db.swl.fan
$ TTL 3H @ IN SOA master.swl.fan. root.master.swl.fan. (1; serial 1D; refresh 1H; retry 1W; expire 3H); minimum or; Negative caching time to live; @ IN NS master.swl.fan. @ IN MX 10 mail.swl.fan. @ IN A 192.168.10.5 @ IN TXT "For Fans of Free Software"; sysadmin IN A 192.168.10.1 fileserver IN A 192.168.10.4 master IN A 192.168.10.5 proxyweb IN A 192.168.10.6 blog IN A 192.168.10.7 ftpserver IN A 192.168.10.8 mail IN A 192.168.10.9
root @ master: ~ # nano /var/lib/bind/db.10.168.192.in-addr.arpa
$ TTL 3H @ IN SOA master.swl.fan. root.master.swl.fan. (1; serial 1D; refresh 1H; retry 1W; expire 3H); minimum or; Negative caching time to live; @ IN NS master.swl.fan. ; 1 IN PTR sysadmin.swl.fan. 4 IN PTR fileserver.swl.fan. 5 IN PTR master.swl.fan. 6 IN PTR proxyweb.swl.fan. 7 IN PTR blog.swl.fan. 8 IN PTR ftpserver.swl.fan. 9 IN PTR mail.swl.fan.
root @ master: ~ # named-checkzone swl.fan /var/lib/bind/db.swl.fan
zone swl.fan/IN: loaded serial 1 OK
root @ master: ~ # named-checkzone 10.168.192.in-addr.arpa /var/lib/bind/db.10.168.192.in-addr.arpa
zone 10.168.192.in-addr.arpa/IN: loaded serial 1 OK
root @ master: ~ # named-checkconf -zp
root @ master: ~ # systemctl restart bind9.service
root @ master: ~ # systemctl status bind9.service
Bind9 checks
root @ master: ~ # dig swl.fan axfr root @ master: ~ # dig 10.168.192.in-addr.arpa axfr root @ master: ~ # dig IN SOA swl.fan root @ master: ~ # dig IN NS swl.fan root @ master: ~ # dig IN MX swl.fan root @ master: ~ # proxyweb host root @ master: ~ # nping --tcp -p 53 -c 3 localhost root @ master: ~ # nping --udp -p 53 -c 3 localhost root @ master: ~ # nping --tcp -p 53 -c 3 master.swl.fan root @ master: ~ # nping --udp -p 53 -c 3 master.swl.fan Starting Nping 0.6.47 ( http://nmap.org/nping ) at 2017-05-27 09:32 EDT SENT (0.0037s) UDP 192.168.10.5:53> 192.168.10.245:53 ttl = 64 id = 20743 iplen = 28 SENT (1.0044s) UDP 192.168.10.5:53> 192.168.10.245 .53: 64 ttl = 20743 id = 28 iplen = 2.0060 SENT (192.168.10.5s) UDP 53:192.168.10.245> 53:64 ttl = 20743 id = 28 iplen = 3 Max rtt: N / A | Min rtt: N / A | Avg rtt: N / A Raw packets sent: 84 (0B) | Rcvd: 0 (3B) | Lost: 100.00 (1%) Nping done: 3.01 IP address pinged in XNUMX seconds
isc-dhcp-server
root @ master: ~ # aptitude install isc-dhcp-server root @ master: ~ # nano / etc / default / isc-dhcp-server # On what interfaces should the DHCP server (dhcpd) serve DHCP requests? # Separate multiple interfaces with spaces, eg "eth0 eth1". INTERFACES = "eth0" root @ master: ~ # dnssec-keygen -a HMAC-MD5 -b 128 -r / dev / urandom -n USER dhcp-key root @ master: ~ # cat Kdhcp-key. +157 + 51777.private Private-key-format: v1.3 Algorithm: 157 (HMAC_MD5) Key: Ba9GVadq4vOCixjPN94dCQ == Bits: AAA = Created: 20170527133656 Publish: 20170527133656 Activate: 20170527133656 root @ master: ~ # nano dhcp.key key dhcp-key { algorithm hmac-md5; secret "Ba9GVadq4vOCixjPN94dCQ == "; }; root @ master: ~ # install -o root -g bind -m 0640 dhcp.key /etc/bind/dhcp.key root @ master: ~ # install -o root -g root -m 0640 dhcp.key / etc / dhcp /dhcp.key root @ master: ~ # nano /etc/bind/named.conf.local include "/etc/bind/dhcp.key"; zone "swl.fan" {type master; file "/var/lib/bind/db.swl.fan"; allow-update {key dhcp-key; }; }; zone "10.168.192.in-addr.arpa" {type master; file "/var/lib/bind/db.10.168.192.in-addr.arpa"; allow-update {key dhcp-key; }; }; root @ master: ~ # named-checkconf root @ master: ~ # mv /etc/dhcp/dhcpd.conf /etc/dhcp/dhcpd.conf.original root @ master: ~ # nano /etc/dhcp/dhcpd.conf ddns-update-style interim; ddns-updates on; ddns-domainname "swl.fan."; ddns-rev-domainname "in-addr.arpa."; ignore client-updates; update-optimization false; # May be required on Debian authoritative; option ip-forwarding off; option domain-name "swl.fan"; include "/etc/dhcp/dhcp.key"; zone swl.fan. {primary 127.0.0.1; key dhcp-key; } zone 10.168.192.in-addr.arpa. {primary 127.0.0.1; key dhcp-key; } shared-network redlocal {subnet 192.168.10.0 netmask 255.255.255.0 {option routers 192.168.10.1; option subnet-mask 255.255.255.0; option broadcast-address 192.168.10.255; option domain-name-servers 192.168.10.5; option netbios-name-servers 192.168.10.5; option ntp-servers 192.168.10.5; option time-servers 192.168.10.5; range 192.168.10.30 192.168.10.250; }} root @ master: ~ # dhcpd -t Internet Systems Consortium DHCP Server 4.3.1 Copyright 2004-2014 Internet Systems Consortium. All rights reserved. For info, please visit https://www.isc.org/software/dhcp/ Config file: /etc/dhcp/dhcpd.conf Database file: /var/lib/dhcp/dhcpd.leases PID file: /var/run/dhcpd.pid root @ master: ~ # systemctl restart bind9.service root @ master: ~ # systemctl status bind9.service root @ master: ~ # systemctl start isc-dhcp-server.service root @ master: ~ # systemctl status isc-dhcp-server.service
Ntp
root @ master: ~ # aptitude install ntp ntpdate root @ master: ~ # cp /etc/ntp.conf /etc/ntp.conf.original root @ master: ~ # nano /etc/ntp.conf driftfile /var/lib/ntp/ntp.drift statistics loopstats peerstats clockstats filegen loopstats file loopstats type day enable filegen peerstats file peerstats type day enable filegen clockstats file clockstats type day enable server 192.168.10.1 restrict -4 default kod notrap nomodify nopeer noquery restrict -6 default kod notrap nomodify nopeer noquery restrict 127.0.0.1 restrict :: 1 broadcast 192.168.10.255 root @ master: ~ # systemctl restart ntp.service root @ master: ~ # systemctl status ntp.service root @ master: ~ # ntpdate -u sysadmin.swl.fan 27 May 10:04:01 ntpdate [18769]: adjust time server 192.168.10.1 offset 0.369354 sec
Global checks for ntp, bind9, and isc-dhcp-server
From a Linux, BSD, Mac OS, or Windows client check that the time is synchronized correctly. That it acquires a dynamic IP address and that the name of that host is resolved through direct and reverse DNS queries. Change the customer name and redo all the checks. Do not proceed until you are certain that the services installed so far are working correctly. For something we wrote all the articles about DNS and DHCP in Computer Networks for SMEs.
NIS Server Installation
root @ master: ~ # aptitude show nis Conflicts with: netstd (<= 1.26) Description: clients and daemons for the Network Information Service (NIS) This package provides tools for setting up and maintaining a NIS domain. NIS, originally known as Yellow Pages (YP), is mostly used to let several machines in a network share the same account information, such as the password file. root @ master: ~ # aptitude install nis Package Configuration ┌─────────────────────────┤ Nis Configuration ├──────────────── ──────────┐ │ Choose the NIS "domain name" for this system. If you want this │ │ machine to be just a client, you should enter the name of the │ │ NIS domain you want to join. │ │ │ │ Alternatively, if this machine is to be an NIS server, you can │ │ enter a new NIS "domain name" or the name of an existing NIS │ │ domain. │ │ │ │ NIS Domain: │ │ │ │ swl.fan __________________________________________________________________ │ │ │ │ │ │ │ └────────────────────────────────────────────── ─────────────────────────────┘
It will delay yours because the service configuration does not exist as such. Please wait for the process to finish.
root @ master: ~ # nano / etc / default / nis
# Are we a NIS server and if so what kind (values: false, slave, master)?
NISSERVER = master
root @ master: ~ # nano /etc/ypserv.securenets # securenets This file defines the access rights to your NIS server # for NIS clients (and slave servers - ypxfrd uses this # file too). This file contains netmask / network pairs. # A clients IP address needs to match with at least one # of those. # # One can use the word "host" instead of a netmask of # 255.255.255.255. Only IP addresses are allowed in this # file, not hostnames. # # Always allow access for localhost 255.0.0.0 127.0.0.0 # This line gives access to everybody. PLEASE ADJUST! # 0.0.0.0 0.0.0.0
255.255.255.0 192.168.10.0
root @ master: ~ # nano / var / yp / Makefile # Should we merge the passwd file with the shadow file? # MERGE_PASSWD = true | false
MERGE_PASSWD = true
# Should we merge the group file with the gshadow file? # MERGE_GROUP = true | false
MERGE_GROUP = true
We build the NIS database
root @ master: ~ # / usr / lib / yp / ypinit -m At this point, we have to construct a list of the hosts which will run NIS servers. master.swl.fan is in the list of NIS server hosts. Please continue to add the names for the other hosts, one per line. When you are done with the list, type a . next host to add: master.swl.fan next host to add: The current list of NIS servers looks like this: master.swl.fan Is this correct? [y / n: y] We need a few minutes to build the databases ... make [1]: Leaving directory '/var/yp/swl.fan' master.swl.fan has been set up as a NIS master server . Now you can run ypinit -s master.swl.fan on all slave server. root @ master: ~ # systemctl restart nis root @ master: ~ # systemctl status nis
We add local users
root @ master: ~ # adduser bilbo Adding the user `bilbo '... Adding the new group` bilbo' (1001) ... Adding the new user `bilbo '(1001) with group` bilbo' ... Creating the home directory `/ home / bilbo ' ... Copying files from `/ etc / skel '... Enter the new UNIX password: Retype the new UNIX password: passwd: password updated correctly Changing the user information for bilbo Enter the new value, or press ENTER to use the default Full Name []: Bilbo Bagins Room Number []: Work Phone []: Home Phone []: Other []: Is the information correct? [Y / n] root @ master: ~ # adduser strides root @ master: ~ # adduser legolas
and so on.
root @ master: ~ # finger legolas Login: legolas Name: Legolas Archer Directory: / home / legolas Shell: / bin / bash Never logged in. No mail. No Plan.
We update the NIS database
root @ master: / var / yp # make make [1]: Entering directory '/var/yp/swl.fan' Updating passwd.byname ... Updating passwd.byuid ... Updating group.byname ... Updating group.bygid ... Updating netid.byname. .. Updating shadow.byname ... Ignored -> merged with passwd make [1]: Leaving directory '/var/yp/swl.fan'
We add NIS options to the isc-dhcp-server
root @ master: ~ # nano /etc/dhcp/dhcpd.conf
ddns-update-style interim; ddns-updates on; ddns-domainname "swl.fan."; ddns-rev-domainname "in-addr.arpa."; ignore client-updates; update-optimization false; authoritative; option ip-forwarding off; option domain-name "swl.fan"; include "/etc/dhcp/dhcp.key"; zone swl.fan. {primary 127.0.0.1; key dhcp-key; } zone 10.168.192.in-addr.arpa. {primary 127.0.0.1; key dhcp-key; } shared-network redlocal {subnet 192.168.10.0 netmask 255.255.255.0 {option routers 192.168.10.1; option subnet-mask 255.255.255.0; option broadcast-address 192.168.10.255; option domain-name-servers 192.168.10.5; option netbios-name-servers 192.168.10.5; option ntp-servers 192.168.10.5; option time-servers 192.168.10.5;
option nis-domain "swl.fan";
option nis-servers 192.168.10.5;
range 192.168.10.30 192.168.10.250; }}
root @ master: ~ # dhcpd -t
root @ master: ~ # systemctl restart isc-dhcp-server.service
NIS Client Installation
- We start from a clean installation -without graphical interface- of a Debian 8 "Jessie".
root @ mail: ~ # hostname -f
mail.swl.fan
root @ mail: ~ # ip addr
2: eth0: mtu 1500 qdisc pfifo_fast state UP group default qlen 1000 link / ether 00: 0c: 29: 25: 1f: 54 brd ff: ff: ff: ff: ff: ff
inet 192.168.10.9 / 24 brd 192.168.10.255 scope global eth0
root @ mail: ~ # aptitude install nis
root @ mail: ~ # nano /etc/yp.conf # # yp.conf Configuration file for the ypbind process. You can define # NIS servers manually here if they can't be found by # broadcasting on the local net (which is the default). # # See the manual page of ypbind for the syntax of this file. # # IMPORTANT: For the "ypserver", use IP addresses, or make sure that # the host is in / etc / hosts. This file is only interpreted # once, and if DNS isn't reachable yet the ypserver cannot # be resolved and ypbind won't ever bind to the server. # ypserver ypserver.network.com ypserver master.swl.fan domain swl.fan
root @ mail: ~ # nano /etc/nsswitch.conf
# /etc/nsswitch.conf # # Example configuration of GNU Name Service Switch functionality. # If you have the `glibc-doc-reference 'and` info' packages installed, try: # `info libc" Name Service Switch "'for information about this file. passwd: compat nis group: compat nis shadow: compat nis gshadow: files hosts: files dns nis networks: files protocols: db files services: db files ethers: db files rpc: db files netgroup: nis
root @ mail: ~ # nano /etc/pam.d/common-session
# pam-auth-update (8) for details.
session optional pam_mkhomedir.so skel = / etc / skel umask = 077
# here are the per-package modules (the "Primary" block)
root @ mail: ~ # systemctl status nis
root @ mail: ~ # systemctl restart nis
We close the session and start it again but with a user registered in the NIS database at master.swl.fan.
root @ mail: ~ # exit logout Connection to mail closed. buzz @ sysadmin: ~ $ ssh legolas @ mail legolas @ mail's password: Creating directory '/ home / legolas'. The programs included with the Debian GNU / Linux system are free software; the exact distribution terms for each program are described in the individual files in / usr / share / doc / * / copyright. Debian GNU / Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. legolas @ mail: ~ $ pwd / home / legolas legolas @ mail: ~ $
We change the password of the legolas user and check
legolas @ mail: ~ $ yppasswd Changing NIS account information for legolas on master.swl.fan. Please enter old password: legolas Changing NIS password for legolas on master.swl.fan. Please enter new password: archer The password must have both upper and lowercase letters, or non-letters. Please enter new password: Arquero2017 Please retype new password: Arquero2017 The NIS password has been changed on master.swl.fan. legolas @ mail: ~ $ exit logout Connection to mail closed. buzz @ sysadmin: ~ $ ssh legolas @ mail legolas @ mail's password: Arquero2017 The programs included with the Debian GNU / Linux system are free software; the exact distribution terms for each program are described in the individual files in / usr / share / doc / * / copyright. Debian GNU / Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Sat May 27 12:51:50 2017 from sysadmin.swl.fan legolas @ mail: ~ $
The NIS Service implemented at the server and client level works correctly.
LDAP
From Wikipedia:
- LDAP is the acronym for Lightweight Directory Access Protocol (in Spanish Lightweight Directory Access Protocol) that refers to an application-level protocol that allows access to an ordered and distributed directory service to search for various information in an environment network. LDAP is also considered a database (although its storage system may be different) that can be queried.A directory is a set of objects with attributes organized in a logical and hierarchical way. The most common example is the telephone directory, which consists of a series of names (persons or organizations) that are arranged alphabetically, with each name having an address and a telephone number attached to it. To understand better, it is a book or folder, in which people's names, telephone numbers and addresses are written, and it is arranged alphabetically.
An LDAP directory tree sometimes reflects various political, geographic, or organizational boundaries, depending on the model chosen. Current deployments of LDAP tend to use Domain Name System (DNS) names to structure the higher levels of the hierarchy. As you move down the directory, entries may appear that represent people, organizational units, printers, documents, groups of people, or anything that represents a given entry in the tree (or multiple entries).
Usually, it stores authentication information (user and password) and is used to authenticate, although it is possible to store other information (user contact data, location of various network resources, permissions, certificates, etc.). In summary, LDAP is a unified access protocol to a set of information on a network.
The current version is LDAPv3, and it is defined in RFCs RFC 2251 and RFC 2256 (LDAP base document), RFC 2829 (authentication method for LDAP), RFC 2830 (extension for TLS), and RFC 3377 (technical specification)
.
For long, the LDAP protocol -and its databases compatible or not with OpenLDAP- is the most used in most of the authentication systems today. As an example of the previous statement, we give below some names of systems -Free or Private- that use LDAP databases as backend to store all their objects:
- OpenLDAP
- Apache DirectoryServer
- Red Hat Directory Server - 389 DS
- Novell Directory Services - eDirectory
- SUN Microsystems Open DS
- Red Hat Identity Manager
- FreeIPA
- Samba NT4 Classic Domain Controller.
We want to clarify that this system was a development of Team Samba with Samba 3.xxx + OpenLDAP as backend. Microsoft never implemented anything like it. Jumped from NT 4 Domain Controllers to their Active Directories - Samba 4 Active Directory - Domain Controler
- clearOS
- Plant
- UCS Uninvention Corporate Server
- Microsoft Active Directory
Each implementation has its own characteristics, and the most standard and compatible is the OpenLDAP.
Active Directory, be it the original from Microsoft or the one from Samba 4, constitute a union of several main components that are:
- Custom LDAP by both Microsoft and Samba.
- Microsoft Windows Domain o Windows domain. It is basically the Microsoft Network.
- Microsoft Domain Controller o Domain Controller.
- Kerberos customized by both Microsoft and Samba.
We must not confuse a Directory Services o Directory Service with a Active Directory o Active Directory. The former may or may not host Kerberos authentication, but they do not offer the Microsoft Network service that a Windows Domain provides, nor do they have a Windows Domain Controller as such.
A Directory Service or Directory Service can be used to authenticate users in a mixed network with UNIX / Linux and Windows clients. For the latter, a program must be installed on each client that acts as an intermediary between the Directory Service and the Windows client itself, such as Free Software. page.
Directory Service with OpenLDAP
- We start from a clean installation -without graphical interface- of a Debian 8 "Jessie", with the same "master" machine name used for the NIS installation, as well as the configuration of its network interface and the /etc/resolv.conf file. We installed the ntp, bind9 and isc-dhcp-server for this new server, without forgetting the global checks of the correct operation of the three previous services.
root @ master: ~ # aptitude install slapd ldap-utils Package configuration ┌────────────────────┤ Slapd configuration ├─────────────────────┐ │ Enter the password for the administrator entry of your LDAP │ │ directory. │ │ │ │ Administrator password: │ │ │ │ ******** _________________________________________________________ │ │ │ │ │ │ │ └────────────────────────────────────────────── ─────────────────────┘
We check the initial configuration
root @ master: ~ # slapcat dn: dc = swl, dc = fan objectClass: top objectClass: dcObject objectClass: organization o: swl.fan dc: swl structuralObjectClass: organization entryUUID: c8510708-da8e-1036-8fe1-71d022a16904 creatorsName: cn = admin, dc = swl, dc = fan entry createTimestamp20170531205219: 20170531205219.833955ZN entry createTimestamp000000: 000ZN000000Z Z # 20170531205219 # XNUMX # XNUMX modifiersName: cn = admin, dc = swl, dc = fan modifyTimestamp: XNUMXZ dn: cn = admin, dc = swl, dc = fan objectClass: simpleSecurityObject objectClass: organizationalRole cn: admin description: userPassword LDAP administrator :: e1NTSEF9emJNSFU1R3l2OWVEN0pmTmlYOVhKSUF4ekY1bU9YQXc = structuralObjectClass: organizationalRole entryUUID: c851178e-da8e-1036-8fe2-71d022a16904 creatorsName: cn = admin, dc = SWL, dc = fan createTimestamp: 20170531205219Z entryCSN: 20170531205219.834422Z # 000000 # 000 # 000000 modifiersName: cn = admin, dc = swl, dc = fan modifyTimestamp: 20170531205219Z
We modify the file /etc/ldap/ldap.conf
root @ master: ~ # nano /etc/ldap/ldap.conf BASE dc = swl, dc = fan URI ldap: // localhost
Organizational Units and general group «users»
We add the minimum necessary Organizational Units, as well as the Posix group «users» to which we will make all users members, following the example of many systems that have the group «users«. We denominate it with the name of «users» so as not to enter into possible conflicts with the group «user" of the system.
root @ master: ~ # nano base.ldif dn: ou = people, dc = swl, dc = fan objectClass: organizationalUnit ou: people dn: ou = groups, dc = swl, dc = fan objectClass: organizationalUnit ou: groups dn: cn = users, ou = groups, dc = swl, dc = fan objectClass: posixGroup cn: users gidNumber: 10000 root @ master: ~ # ldapadd -x -D cn = admin, dc = swl, dc = fan -W -f base.ldif Enter LDAP Password: adding new entry "ou = people, dc = swl, dc = fan" adding new entry "ou = groups, dc = swl, dc = fan"
We check the added entries
root @ master: ~ # ldapsearch -x ou = people # people, swl.fan dn: ou = people, dc = swl, dc = fan objectClass: organizationalUnit ou: people root @ master: ~ # ldapsearch -x ou = groups # groups, swl.fan dn: ou = groups, dc = swl, dc = fan objectClass: organizationalUnit ou: groups root @ master: ~ # ldapsearch -x cn = users # users, groups, swl.fan dn: cn = users, ou = groups, dc = swl, dc = fan objectClass: posixGroup cn: users gidNumber: 10000
We add several users
The password that we must declare in the LDAP must be obtained through the command slappasswd, which returns an encrypted SSHA password.
Password for the user strides:
root @ master: ~ # slappasswd
New password: Re-enter new password:
{SSHA}Fn8Juihsr137u8KnxGTNPmnV8ai//0lp
Password for user legolas
root @ master: ~ # slappasswd
New password: Re-enter new password:
{SSHA}rC50/W3kBmmDd+8+0Lz70vkGEu34tXmD
Password for user gandalf
root @ master: ~ # slappasswd
New password: Re-enter new password:
{SSHA} oIVFelqv8WIxJ40r12lnh3bp + SXGbV + u
root @ master: ~ # nano users.ldif
dn: uid = strides, ou = people, dc = swl, dc = fan objectClass: inetOrgPerson objectClass: posixAccount objectClass: shadowAccount uid: strides cn: strides givenName: Strides sn: El Rey userPassword: {SSHA}Fn8Juihsr137u8KnxGTNPmnV8ai//0lp
uidNumber: 10000 gidNumber: 10000 mail: striders@swl.fan
gecos: Strider El Rey loginShell: / bin / bash homeDirectory: / home / strider dn: uid = legolas, ou = people, dc = swl, dc = fan objectClass: inetOrgPerson objectClass: posixAccount objectClass: shadowAccount uid: legolas cn: legolas givenName : Legolas sn: Archer userPassword: {SSHA}rC50/W3kBmmDd+8+0Lz70vkGEu34tXmD
uidNumber: 10001 gidNumber: 10000 mail: legolas@swl.fan
gecos: Legolas Archer loginShell: / bin / bash homeDirectory: / home / legolas dn: uid = gandalf, ou = people, dc = swl, dc = fan objectClass: inetOrgPerson objectClass: posixAccount objectClass: shadowAccount uid: gandalf cn: gandalf givenName: Gandalf sn: The Wizard userPassword: {SSHA} oIVFelqv8WIxJ40r12lnh3bp + SXGbV + u
uidNumber: 10002 gidNumber: 10000 mail: gandalf@swl.fan
gecos: Gandalf The Wizard loginShell: / bin / bash homeDirectory: / home / gandalf
root @ master: ~ # ldapadd -x -D cn = admin, dc = swl, dc = fan -W -f users.ldif
Enter LDAP Password: adding new entry "uid = strides, ou = people, dc = swl, dc = fan" adding new entry "uid = legolas, ou = people, dc = swl, dc = fan" adding new entry "uid = gandalf, ou = people, dc = swl, dc = fan "
We check the added entries
root @ master: ~ # ldapsearch -x cn = strides root @ master: ~ # ldapsearch -x uid = strides
We manage the slpad database with console utilities
We select the package ldapscripts for such a task. The installation and configuration procedure is as follows:
root @ master: ~ # aptitude install ldapscripts root @ master: ~ # mv /etc/ldapscripts/ldapscripts.conf \ /etc/ldapscripts/ldapscripts.conf.original root @ master: ~ # nano /etc/ldapscripts/ldapscripts.conf SERVER = localhost BINDDN = 'cn = admin, dc = swl, dc = fan' BINDPWDFILE = "/ etc / ldapscripts / ldapscripts.passwd" SUFFIX = 'dc = swl, dc = fan' GSUFFIX = 'ou = groups' USUFFIX = 'ou = people' # MSUFFIX = 'ou = Computers' GIDSTART = 10001 UIDSTART = 10003 # MIDSTART = 10000 # OpenLDAP client commands LDAPSEARCHBIN = "/ usr / bin / ldapsearch" LDAPADDBIN = "/ usr / bin / ldapadd" LDAPDELETEBIN = " / usr / bin / ldapdelete "LDAPMODIFYBIN =" / usr / bin / ldapmodify "LDAPMODRDNBIN =" / usr / bin / ldapmodrdn "LDAPPASSWDBIN =" / usr / bin / ldappasswd "GCLASS =" posixGroup "# UTEMPLATE =" / etc / etc. /ldapadduser.template "PASSWORDGEN =" echo% u "
Notice that the scripts use the package commands ldap-utils. Run dpkg -L ldap-utils | grep / bin to know what they are.
root @ master: ~ # sh -c "echo -n 'admin-password'> \ /etc/ldapscripts/ldapscripts.passwd " root @ master: ~ # chmod 400 /etc/ldapscripts/ldapscripts.passwd root @ master: ~ # cp /usr/share/doc/ldapscripts/examples/ldapadduser.template.sample \ /etc/ldapscripts/ldapdduser.template root @ master: ~ # nano /etc/ldapscripts/ldapadduser.template dn: uid = , , objectClass: inetOrgPerson objectClass: posixAccount objectClass: shadowAccount uid: cn: givenName: sn: displayName: uidNumber: gidNumber: 10000 homeDirectory: loginShell: mail: @ swl.fan geckos: description: User Account root @ master: ~ # nano /etc/ldapscripts/ldapscripts.conf ## we remove the comment UTEMPLATE = "/ etc / ldapscripts / ldapadduser.template"
We add the user "bilbo" and make him a member of the group "users"
root @ master: ~ # ldapadduser bilbo users [dn: uid = bilbo, ou = people, dc = swl, dc = fan] Enter value for "givenName": Bilbo [dn: uid = bilbo, ou = people, dc = swl, dc = fan] Enter value for " sn ": Bagins [dn: uid = bilbo, ou = people, dc = swl, dc = fan] Enter value for" displayName ": Bilbo Bagins Successfully added user bilbo to LDAP Successfully set password for user bilbo root @ master: ~ # ldapsearch -x uid = bilbo # bilbo, people, swl.fan dn: uid = bilbo, ou = people, dc = swl, dc = fan objectClass: inetOrgPerson objectClass: posixAccount objectClass: shadowAccount uid: bilbo cn: bilbo givenName: Bilbo sn: Bagins displayName: Bilbo Bagins uidNumber: 10003 gidNumber: 10000 homeDirectory: / home / bilbo loginShell: / bin / bash mail: bilbo@swl.fan gecos: bilbo description: User Account
To see the hash of the password of the bilbo user, it is necessary to carry out the query with authentication:
root @ master: ~ # ldapsearch -x -D cn = admin, dc = swl, dc = fan -W uid = bilbo
To delete the bilbo user we execute:
root @ master: ~ # ldapdelete -x -D cn = admin, dc = swl, dc = fan -W uid = bilbo, ou = people, dc = swl, dc = fan Enter LDAP Password: root @ master: ~ # ldapsearch -x uid = bilbo
We manage the slapd database through a web interface
We have a functional Directory Service, and we want to manage it more easily. There are many programs designed for this task, such as the phpldapadmin, ldap-account-manager, etc., which are available directly from the repositories. We can also manage a Directory Service through the Apache Directory Studio, which we must download from the Internet.
For more information, please visit https://blog.desdelinux.net/ldap-introduccion/, and the following 6 articles.
LDAP client
Scenario:
Say we have the team mail.swl.fan as a mail server implemented as we saw in the article Postfix + Dovecot + Squirrelmail and local users, which although developed on CentOS, may well serve as a guide for Debian and many other Linux distros. We want that, in addition to the local users that we already have declared, the users stored in the OpenLDAP database existing in master.swl.fan. To achieve this we must «map»To LDAP users as local users on the server mail.swl.fan. This solution is also valid for any service based on PAM authentication. The general procedure for Debian, is the following:
root @ mail: ~ # aptitude install libnss-ldap libpam-ldap ldap-utils ┌────────────────────┤ Configuration of libnss-ldap ├─────────────────────┐ │ Enter the URI (“Uniform Resource Identifier”, or │ servidor Uniform Resource Identifier) of the LDAP server. This string is similar to │ │ «ldap: //: / ». You can also │ │ use «ldaps: // » or "ldapi: //". The port number is optional. │ │ │ │ It is recommended to use an IP address to avoid failure when domain name services │ │ are not available. │ │ │ │ LDAP server URI: │ │ │ │ ldap: //master.swl.fan__________________________________________________ │ │ │ │ │ │ │ └────────────────────────────────────────────── ───────────────────────────┘ ┌───────────────────── ┤ Configuration of libnss-ldap ├──────────────────────┐ │ Enter the distinguished name (DN) of the LDAP search base. Many sites use the domain name components for this │ │ purpose. For example, the domain "example.net" would use │ │ "dc = example, dc = net" as the distinguished name of the search base. │ │ │ │ The distinguished name (DN) of the search base: │ │ │ │ dc = swl, dc = fan ____________________________________________________________ │ │ │ │ │ │ │ └────────────────────────────────────────────── ─────────────────────────────┘ ┌─────────────────── ──┤ Configuration of libnss-ldap ├──────────────────────┐ │ Enter the version of the LDAP protocol that ldapns should use. It is │ │ recommended to use the highest version number available. │ │ │ │ LDAP version to use: │ │ │ │ 3 │ │ 2 │ │ │ │ │ │ │ │ │ └────────────────────────────────────────────── ─────────────────────────────┘ ┌─────────────────── ──┤ Configuration of libnss-ldap ├──────────────────────┐ │ Choose which account will be used for nss queries with │ │ root privileges. │ │ │ │ Note: For this option to work, the account needs permissions to │ │ be able to access the LDAP attributes that are associated with the user │ │ "shadow" entries as well as the passwords of the users and │ │ groups . │ │ │ │ LDAP account for root: │ │ │ │ cn = admin, dc = swl, dc = fan ___________________________________________________ │ │ │ │ │ │ │ └────────────────────────────────────────────── ─────────────────────────────┘ ┌─────────────────── ──┤ Configuration of libnss-ldap ├─────────────────────┐ │ Enter the password to be used when libnss-ldap tries to │ │ authenticate to the LDAP directory with the root LDAP account. │ │ │ │ The password will be saved in a separate file │ │ ("/etc/libnss-ldap.secret") that only root can access. │ │ │ │ If you enter an empty password, the old password will be reused. │ │ │ │ Password for the root LDAP account: │ │ │ │ ******** ________________________________________________________________ │ │ │ │ │ │ │ └────────────────────────────────────────────── ────────────────────────────┘ ┌──────────────────── ─┤ Configuration of libnss-ldap ├──────────────────────┐ │ │ │ nsswitch.conf is not managed automatically │ │ │ │ You must modify your file "/etc/nsswitch.conf" to use an LDAP data source if you want the libnss-ldap package to work. │ │ You can use the example file │ │ in "/usr/share/doc/libnss-ldap/examples/nsswitch.ldap" as an example of the nsswitch configuration or │ │ you can copy it over your current configuration. │ │ │ │ Note that before removing this package it may be convenient to │ │ remove the "ldap" entries from the nsswitch.conf file so that the basic services │ │ continue to function. │ │ │ │ │ │ │ └────────────────────────────────────────────── ─────────────────────────────┘ ┌─────────────────── ──┤ Configuration of libpam-ldap ├──────────────────────┐ │ │ │ This option allows password tools using PAM to change local passwords. │ │ │ │ The password for the LDAP administrator account will be stored in a separate │ │ file that can only be read by the administrator. │ │ │ │ This option should be disabled, if mounting "/ etc" via NFS. │ │ │ │ Do you want to allow the LDAP administrator account to behave as │ │ the local administrator? │ │ │ │ │ │ │ └────────────────────────────────────────────── ─────────────────────────────┘ ┌─────────────────── ──┤ Configuration of libpam-ldap ├──────────────────────┐ │ │ │ Choose whether the LDAP server forces identification before obtaining entradas │ entries. │ │ │ │ This setting is rarely necessary. │ │ │ │ Is a user required to access the LDAP database? │ │ │ │ │ │ │ └────────────────────────────────────────────── ─────────────────────────────┘ ┌─────────────────── ──┤ Configuration of libpam-ldap ├──────────────────────┐ │ Enter the name of the LDAP administrator account. │ │ │ │ This account will be automatically used for database management, que │ it must have the appropriate administrative privileges. │ │ │ │ LDAP administrator account: │ │ │ │ cn = admin, dc = swl, dc = fan ___________________________________________________ │ │ │ │ │ │ │ └────────────────────────────────────────────── ─────────────────────────────┘ ┌─────────────────── ──┤ Configuration of libpam-ldap ├──────────────────────┐ │ Enter the password for the administrator account. │ │ │ │ The password will be saved in the file "/etc/pam_ldap.secret". The │ │ administrator will be the only one who can read this file, and will allow │ │ libpam-ldap to automatically control the management of connections in the │ │ database. │ │ │ │ If you leave this field blank, the previous saved password │ │ will be used again. │ │ │ │ LDAP administrator password: │ │ │ │ ******** _________________________________________________________________ │ │ │ │ │ │ │ └────────────────────────────────────────────── ─────────────────────────────┘ root @ mail: ~ # nano /etc/nsswitch.conf # /etc/nsswitch.conf # # Example configuration of GNU Name Service Switch functionality. # If you have the `glibc-doc-reference 'and` info' packages installed, try: # `info libc" Name Service Switch "'for information about this file. passwd: compat ldap group: compat ldap shadow: compat ldap gshadow: files hosts: files dns networks: files protocols: db files services: db files ethers: db files rpc: db files netgroup: nis
Let's edit the file /etc/pam.d/common-password, we go to line 26 and eliminate the value «use_authtok«:
root @ mail: ~ # nano /etc/pam.d/common-password # # /etc/pam.d/common-password - password-related modules common to all services # # This file is included from other service-specific PAM config files, # and should contain a list of modules that define the services to be # used to change user passwords. The default is pam_unix. # Explanation of pam_unix options: # # The "sha512" option enables salted SHA512 passwords. Without this option, # the default is Unix crypt. Prior releases used the option "md5". # # The "obscure" option replaces the old `OBSCURE_CHECKS_ENAB 'option in # login.defs. # # See the pam_unix manpage for other options. # As of pam 1.0.1-6, this file is managed by pam-auth-update by default. # To take advantage of this, it is recommended that you configure any # local modules either before or after the default block, and use # pam-auth-update to manage selection of other modules. See # pam-auth-update (8) for details. # here are the per-package modules (the "Primary" block) password [success = 2 default = ignore] pam_unix.so obscure sha512 password [success = 1 user_unknown = ignore default = die] pam_ldap.so try_first_pass # here's the fallback if no module succeeds password requisite pam_deny.so # prime the stack with a positive return value if there isn't one already; # this avoids us returning an error just because nothing sets a success code # since the modules above will each just jump around password required pam_permit.so # and here are more per-package modules (the "Additional" block) # end of pam- auth-update config
In case we need the Local Login of the users stored in the LDAP, and we want their folders to be created automatically home, we must edit the file /etc/pam.d/common-session and add the following line to the end of the file:
session optional pam_mkhomedir.so skel = / etc / skel umask = 077
In the OpenLDAP Directory Service example developed earlier, the only local user that was created was the user buzz, while in LDAP we create the users strides, Legolas, gandalf, and bilbo. If the configurations made so far are correct, then we should be able to list the local users and those mapped as local but stored in the remote LDAP server:
root @ mail: ~ # getent passwd buzz: x: 1001: 1001: Buzz Debian First OS ,,,: / home / buzz: / bin / bash Strides: x: 10000: 10000: Strides El Rey: / home / strides: / bin / bash legolas: x: 10001: 10000: Legolas Archer: / home / legolas: / bin / bash gandalf: x: 10002: 10000: Gandalf The Magician: / home / gandalf: / bin / bash bilbo: x: 10003: 10000: bilbo: / home / bilbo: / bin / bash
After the changes in the system authentication, it is valid to restart the server if we do not have a critical service:
root @ mail: ~ # reboot
Later we start a local session on the server mail.swl.fan with the credentials of a user stored in the LDAP database of master.swl.fan. We can also try logging in via SSH.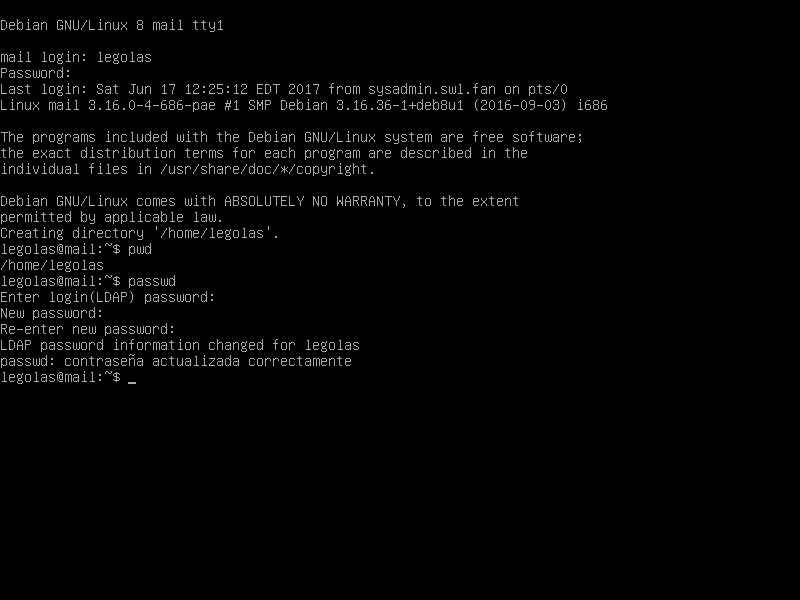
buzz @ sysadmin: ~ $ ssh gandalf @ mail gandalf @ mail's password: Creating directory '/ home / gandalf'. The programs included with the Debian GNU / Linux system are free software; the exact distribution terms for each program are described in the individual files in / usr / share / doc / * / copyright. Debian GNU / Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. gandalf @ mail: ~ $ su Password: root @ mail: / home / gandalf # getent group buzz: x: 1001: users: *: 10000: root @ mail: / home / gandalf # exit exit gandalf @ mail: ~ $ ls -l / home / total 8 drwxr-xr-x 2 buzz buzz 4096 Jun 17 12:25 buzz drwx ------ 2 gandalf users 4096 Jun 17 13:05 gandalf
The Directory Service implemented at the server and client level, works correctly.
Kerberos
From Wikipedia:
- Kerberos is a computer network authentication protocol created by the MIT that allows two computers on an insecure network to securely prove their identity to each other. Its designers first focused on a client-server model, and it provides mutual authentication: both client and server verify the identity of each other. Authentication messages are protected to prevent eavesdropping y replay attacks.
Kerberos is based on symmetric key cryptography and requires a trusted third party. In addition, there are extensions to the protocol to be able to use asymmetric key cryptography.
Kerberos is based on the Needham-Schroeder protocol. It uses a trusted third party, called a "Key Distribution Center" (KDC), which consists of two separate logical parts: an "Authentication Server" (AS or Authentication Server) and a "ticket issuing server" (TGS or Ticket Granting Server). Kerberos works on the basis of "tickets", which serve to prove the identity of users.
Kerberos maintains a database of secret keys; Each entity on the network — be it client or server — shares a secret key known only to itself and Kerberos. Knowledge of this key serves to prove the identity of the entity. For a communication between two entities, Kerberos generates a session key, which they can use to secure their problems.
Disadvantages of Kerberos
De ecured:
Despite that Kerberos removes a common security threat, it can be difficult to implement for a variety of reasons:
- Migration of user passwords from a standard password database UNIX, such as / etc / passwd or / etc / shadow, to a Kerberos password database, can be tedious and there is no quick mechanism to accomplish this task.
- Kerberos assumes that each user is trusted, but is using an untrusted machine on an untrusted network. Its main objective is to prevent unencrypted passwords from being sent over the network. However, if any other user, apart from the appropriate user, has access to the ticketing machine (KDC) for authentication, Kerberos would be at Risk.
- For an application to use Kerberos, the code must be modified to make the appropriate calls to the Kerberos libraries. Applications that are modified in this way are considered kerberized. For some applications, this can be an excessive programming effort, due to the size of the application or its Design. For other incompatible applications, changes must be made to the way the network server and its clients communicate; again, this can take quite a bit of programming. In general, closed source applications that do not support Kerberos are usually the most problematic.
- Finally, if you decide to use Kerberos on your network, you must realize that it is an all or nothing choice. If you decide to use Kerberos on your network, you must remember that if any passwords are passed to a service that does not use Kerberos to authenticate, you run the risk that the packet may be intercepted. Thus, your network will not get any benefit from using Kerberos. To secure your network with Kerberos, you should only use the kerberized versions of all client / server applications that send unencrypted passwords or not use any of these applications on the network.
Manually implementing and configuring OpenLDAP as a Kerberos Back-End is not an easy task. However, later we will see that the Samba 4 Active Directory - Domain Controller integrates in a transparent way for the Sysadmin, a DNS server, the Microsoft Network and its Domain Controller, LDAP server as Back-End of almost all of its objects, and the Kerberos-based authentication service as the fundamental components of a Microsoft-style Active Directory.
To date we have not had the need to implement a "Kerberized Network". This is why we did not write about how to implement Kerberos.
Samba 4 Active Directory - Domain Controller

Important:
There is no better documentation than the site wiki.samba.org. Sysadmin worth its salt should visit that site -in English- and browse the large number of pages entirely dedicated to Samba 4, written by Team Samba himself. I do not believe there is documentation available on the Internet to replace it. By the way, observe the number of visits reflected at the bottom of each page. An example of this is that your main page or «Main Page» was visited 276,183 times as of today June 20, 2017 at 10:10 Eastern Standard Time. In addition, the documentation is kept very up-to-date, as that page was modified on June 6.
From Wikipedia:
Samba is a free implementation of the Microsoft Windows File Sharing Protocol (formerly called SMB, recently renamed CIFS) for UNIX-like systems. In this way, it is possible that computers with GNU / Linux, Mac OS X or Unix in general look like servers or act as clients in Windows networks. Samba also allows users to validate as a Primary Domain Controller (PDC), as a domain member and even as an Active Directory domain for Windows-based networks; apart from being able to serve print queues, shared directories and authenticate with its own user archive.
Among the Unix-like systems on which Samba can be run are the GNU / Linux distributions, Solaris and the different BSD variants among the that we can find Apple's Mac OS X Server.
Samba 4 AD-DC with its Internal DNS
- We start from a clean installation -without graphical interface- of a Debian 8 "Jessie".
Initial checks
root @ master: ~ # hostname
master
root @ master: ~ # hostname --fqdn
master.swl.fan
root @ master: ~ # ip addr
1: what: mtu 65536 qdisc noqueue state UNKNOWN group default link / loopback 00: 00: 00: 00: 00: 00 brd 00: 00: 00: 00: 00: 00 inet 127.0.0.1/8 scope host lo valid_lft forever preferred_lft forever inet6 :: 1/128 scope host valid_lft forever preferred_lft forever 2: eth0: mtu 1500 qdisc pfifo_fast state UNKNOWN group default qlen 1000 link / ether 00: 0c: 29: 80: 3b: 3f brd ff: ff: ff: ff: ff: ff
inet 192.168.10.5 / 24 brd 192.168.10.255 scope global eth0
valid_lft forever preferred_lft forever inet6 fe80 :: 20c: 29ff: fe80: 3b3f / 64 scope link valid_lft forever preferred_lft forever
root @ master: ~ # cat /etc/resolv.conf
search swl.fan nameserver 127.0.0.1
- With which we declare the branch main only, it's more than enough for our purposes.
root @ master: ~ # cat /etc/apt/sources.list deb http://192.168.10.1/repos/jessie-8.6/debian/ jessie main deb http://192.168.10.1/repos/jessie-8.6/debian/security/ jessie / updates main
Postfix by Exim and utilities
root @ master: ~ # aptitude install postfix htop mc deborphan ┌────────────────────────┤ Postfix Configuration ├───────────────────── ────┐ │ Choose the type of mail server configuration that best suits your │ │ needs. │ │ │ │ No configuration: │ │ Keeps the current configuration intact. │ │ Internet site: │ │ Mail is sent and received directly using SMTP. │ │ Internet with «smarthost»: │ │ Mail is received directly using SMTP or by running a como │ tool like «fetchmail». Outgoing mail is sent using │ │ a "smarthost". │ │ Local mail only: │ │ The only mail that is delivered is for local users. No │ │ there is a network. │ │ │ │ Generic type of mail configuration: │ │ │ │ No configuration │ │ Internet site │ │ Internet with "smarthost" │ │ Satellite system │ │ Local mail only │ │ │ │ │ │ │ │ │ └────────────────────────────────────────────── ────────────────────────────┘ ┌──────────────────── ─────┤ Postfix Configuration ├─────────────────────────┐ │ The "mail system name" is the name of the domain that │ │ is used to "qualify" _ALL_ email addresses without a domain name. This includes mail to and from "root": please do not make │ │ your machine send emails from root@example.org to │ │ less than root@example.org asked. │ │ │ │ Other programs will use this name. It must be a unique │ │ qualified domain name (FQDN). │ │ │ │ Therefore, if an email address on the local machine is │ │ something@example.org, the correct value for this option will be example.org. │ │ │ │ Mail system name: │ │ │ │ master.swl.fan ___________________________________________________________ │ │ │ │ │ │ │ └────────────────────────────────────────────── ─────────────────────────────┘
We clean
root @ master: ~ # aptitude purge ~ c root @ master: ~ # aptitude install -f root @ master: ~ # aptitude clean root @ master: ~ # aptitude autoclean
We install requirements to compile Samba 4 and other necessary packages
root @ master: ~ # aptitude install acl attr autoconf bison \
build-essential debhelper dnsutils docbook-xml docbook-xsl flex gdb \
krb5-user libacl1-dev libaio-dev libattr1-dev libblkid-dev libbsd-dev \
libcap-dev libcups2-dev libgnutls28-dev libjson-perl \
libldap2-dev libncurses5-dev libpam0g-dev libparse-yapp-perl\
libpopt-dev libreadline-dev perl perl-modules pkg-config \
python-all-dev python-dev python-dnspython python-crypto\
xsltproc zlib1g -dev libgpgme11 -dev python -gpgme python -m2crypto \
libgnutls28-dbg gnutls-dev ldap-utils krb5-config
┌───────────────┤ Configuring Kerberos authentication ├───────────────┐ │ When users try to use Kerberos and specify a name │ │ principal or user without clarifying to which administrative Kerberos domain the principal │ │ belongs, the system takes the default │ │ realm. The default realm can also be used as the │ │ realm of a Kerberos service running on the local machine. │ │ Typically, the default realm is the uppercase name of the local DNS │ │ domain. │ │ │ │ Kerberos version 5 default realm: │ │ │ │ SWL.FAN __________________________________________________________________ │ │ │ │ │ │ │ └────────────────────────────────────────────── ─────────────────────────────┘ ┌───────────────┤ Configuring authentication Kerberos ├───────────────┐ │ Enter the names of the Kerberos servers in the SWL.FAN realm of │ │ Kerberos, separated by spaces. │ │ │ │ Kerberos servers for your realm: │ │ │ │ master.swl.fan ___________________________________________________________ │ │ │ │ │ │ │ └────────────────────────────────────────────── ─────────────────────────────┘ ┌───────────────┤ Configuring authentication Kerberos ├───────────────┐ │ Enter the administrative server name (password change) │ │ for the Kerberos SWL.FAN realm.
The above process took a bit of time because we don't have any DNS services installed yet. However, you chose the domain correctly by the file settings / Etc / hosts. Remember that in the file / Etc / resolv.conf we have declared as a domain name server to the IP 127.0.0.1.
We now configure the / etc / ldap / ldap / conf file
root @ master: ~ # nano /etc/ldap/ldap.conf
BASE dc = swl, dc = fan URI ldap: //master.swl.fan
For queries using the command ldapsearch made from the root user are of the type ldapsearch -x -W cn = xxxx, we must create the file /root/.ldapsearch with the following content:
root @ master: ~ # nano .ldaprc BINDDN CN = Administrator, CN = Users, DC = swl, DC = fan
The file system must support ACL - Access Control List
root @ master: ~ # nano / etc / fstab # / etc / fstab: static file system information. # # Use 'blkid' to print the universally unique identifier for a # device; this may be used with UUID = as a more robust way to name devices # that works even if disks are added and removed. See fstab (5). # # # / was on / dev / sda1 during installation UUID = 33acb024-291b-4767-b6f4-cf207a71060c / ext4 user_xattr, acl, barrier = 1, noatime, errors = remount-ro 0 1 # swap was on / dev / sda5 during installation UUID = cb73228a-615d-4804-9877-3ec225e3ae32 none swap sw 0 0 / dev / sr0 / media / cdrom0 udf, iso9660 user, noauto 0 0 root @ master: ~ # mount -a root @ master: ~ # touch testing_acl.txt root @ master: ~ # setfattr -n user.test -v test testing_acl.txt root @ master: ~ # setfattr -n security.test -v test2 testing_acl.txt root @ master: ~ # getfattr -d testing_acl.txt # file: testing_acl.txt user.test = "test" root @ master: ~ # getfattr -n security.test -d testing_acl.txt # file: testing_acl.txt security.test = "test2" root @ master: ~ # setfacl -mg: adm: rwx testing_acl.txt root @ master: ~ # getfacl testing_acl.txt # file: testing_acl.txt # owner: root # group: root user :: rw- group :: r-- group: adm: rwx mask :: rwx other :: r--
We obtain the Samba 4 source, compile it, and install it
It is highly recommended to download the source file of the version Stable from the site https://www.samba.org/. In our example we download the version samba-4.5.1.tar.gz towards the folder / Opt.
root @ master: ~ # cd / opt
root @ master: / opt # wget https://download.samba.org/pub/samba/stable/samba-4.5.1.tar.gz
root @ master: / opt # tar xvfz samba-4.5.1.tar.gz
root @ master: / opt # cd samba-4.5.1 /
Configuration options
If we want to customize the configuration options, we execute:
root @ master: /opt/samba-4.5.1# ./configure --help
and with great care select the ones we need. It is advisable to check if the downloaded package can be installed on the Linux distribution we are using, which in our case is Debian 8.6 Jessie:
root @ master: /opt/samba-4.5.1# ./configure dist check
We configure, Compile and Install samba-4.5.1
- From the previously installed requirements and the 8604 files (which make up the compact samba-4.5.1.tar.gz) that weigh about 101.7 megabytes -including the source3 and source4 folders that weigh about 61.1 megabytes- we will obtain a substitute for a Microsoft-style Active Directory, of a quality and stability more than acceptable for any production environment. We must highlight the work of Team Samba in delivering the Free Software Samba 4.
The commands below are the classic ones for compiling and installing packages from their sources. We must be patient while the entire process lasts. It is the only way to get valid and correct results.
root @ master: /opt/samba-4.5.1# ./configure --with-systemd --disable-cups root @ master: /opt/samba-4.5.1# make root @ master: /opt/samba-4.5.1# make install
During the command process make, we can see that the Samba 3 and Samba 4 sources are compiled. That is why Team Samba affirms that its version 4 is the natural update of version 3, both for Domain Controllers based on Samba 3 + OpenLDAP, and file servers, or older versions of Samba 4.
Provisioning Samba
We will use as DNS the SAMBA_INTERNAL. In https://wiki.samba.org/index.php?title=Samba_Internal_DNS_Back_End we will find more information. When they ask us for the password of the Administrator user, we must type one of a minimum length of 8 characters and also with letters - upper and lower case - and numbers.
Before proceeding with the provisioning and to make life easier, we add the path of the Samba executables in our file .bashrc, Then we close and log in again.
root @ master: ~ # nano .bashrc
# ~ / .bashrc: executed by bash (1) for non-login shells. # Note: PS1 and umask are already set in / etc / profile. You should not # need this unless you want different defaults for root. # PS1 = '$ {debian_chroot: + ($ debian_chroot)} \ h: \ w \ $' # umask 022 # You may uncomment the following lines if you want `ls 'to be colorized: # export LS_OPTIONS =' - color = auto '# eval "` dircolors` "# alias ls =' ls $ LS_OPTIONS '# alias ll =' ls $ LS_OPTIONS -l '# alias l =' ls $ LS_OPTIONS -lA '# # Some more aliases to avoid making mistakes : # alias rm = 'rm -i' # alias cp = 'cp -i' # alias mv = 'mv -i'
declare -x PATH = "/ usr / local / sbin: / usr / local / bin: / usr / sbin: / usr / bin: \ / sbin: / bin: / usr / local / samba / sbin: / usr / local / samba / bin "
root @ master: ~ # exit logout Connection to master closed. xeon @ sysadmin: ~ $ ssh root @ master
root @ master: ~ # samba-tool domain provision --use-rfc2307 --interactive
Realm [SWL.FAN]: SWL.FAN
Domain [SWL]: SWL
Server Role (dc, member, standalone) [dc]: dc
Backend DNS (SAMBA_INTERNAL, BIND9_FLATFILE, BIND9_DLZ, NONE) [SAMBA_INTERNAL]: SAMBA_INTERNAL
DNS forwarder IP address (write 'none' to disable forwarding) [192.168.10.5]: 8.8.8.8
administrator password: YourPassword2017
Change password: YourPassword2017
Looking up IPv4 addresses Looking up IPv6 addresses No IPv6 address will be assigned Setting up share.ldb Setting up secrets.ldb Setting up the registry Setting up the privileges database Setting up idmap db Setting up SAM db Setting up sam.ldb partitions and settings Setting up sam.ldb rootDSE Pre-loading the Samba 4 and AD schema Adding DomainDN: DC = swl, DC = fan Adding configuration container Setting up sam.ldb schema Setting up sam.ldb configuration data Setting up display specifiers Modifying display specifiers Adding users container Modifying users container Adding computers container Modifying computers container Setting up sam.ldb data Setting up well known security principals Setting up sam.ldb users and groups Setting up self join Adding DNS accounts Creating CN = MicrosoftDNS, CN = System, DC = swl, DC = fan Creating DomainDnsZones and ForestDnsZones partitions Populating DomainDnsZones and ForestDnsZones partitions Setting up sam.ldb rootDSE marking as synchronized Fixing provision GUIDsA Kerberos configuration suitable for Samba 4 has been generated at /usr/local/samba/private/krb5.conf Setting up fake yp server settings Once the above files are installed, your Samba4 server will be ready to use Server Role: active directory domain controller Hostname: master NetBIOS Domain: SWL DNS Domain: swl.fan DOMAIN SID: S-1-5-21-32182636-2892912266-1582980556
Let's not forget to copy the Kerberos configuration file as indicated by the output of the Provisioning:
root @ master: ~ # cp /usr/local/samba/private/krb5.conf /etc/krb5.conf
To not type the command samba-tool with your full name, we create a symbolic link with the short name tool:
root @ master: ~ # ln -s / usr / local / samba / bin / samba-tool / usr / local / samba / bin / tool
We install the NTP
A fundamental piece in an Active Directory is the Network Time Service. As the authentication is done via Kerberos and its Tickets, the synchronization of the time with the Samba 4 AD-DC is vital.
root @ master: ~ # aptitude install ntp root @ master: ~ # mv /etc/ntp.conf /etc/ntp.conf.original root @ master: ~ # nano /etc/ntp.conf driftfile /var/lib/ntp/ntp.drift ntpsigndsocket / usr / local / samba / var / lib / ntp_signd statistics loopstats peerstats clockstats filegen loopstats file loopstats type day enable filegen peerstats file peerstats type day enable filegenstats file clockstats clock type day enable server 192.168.10.1 restrict -4 default kod notrap nomodify nopeer noquery restrict -6 default kod notrap nomodify nopeer noquery restrict default mssntp restrict 127.0.0.1 restrict :: 1 broadcast 192.168.10.255 root @ master: ~ # service ntp restart root @ master: ~ # service ntp status root @ master: ~ # tail -f / var / log / syslog
If when examining the syslog using the command above or using journalctl -f we get the message:
Jun 19 12:13:21 master ntpd_intres [1498]: parent died before we finished, exiting
we must restart the service and try again. Now we create the folder ntp_signd:
root @ master: ~ # ls -ld / usr / local / samba / var / lib / ntp_signd
ls: Cannot access / usr / local / samba / var / lib / ntp_signd: File or directory does not exist
root @ master: ~ # mkdir / usr / local / samba / var / lib / ntp_signd
root @ master: ~ # chown root: ntp / usr / local / samba / var / lib / ntp_signd /
root @ master: ~ # chmod 750 / usr / local / samba / var / lib / ntp_signd / root @ master: ~ # chmod gs, g + x / usr / local / samba / var / lib / ntp_signd /
# As requested on samba.wiki.org
root @ master: ~ # ls -ld / usr / local / samba / var / lib / ntp_signd
drwxr-x --- 2 root ntp 4096 Jun 19 12:21 / usr / local / samba / var / lib / ntp_signd
We configure the Samba start using systemd
root @ master: ~ # nano /lib/systemd/system/samba-ad-dc.service [Service] Type = forking PIDFile = / usr / local / samba / var / run / samba.pid LimitNOFILE = 16384 # EnvironmentFile = - / etc / conf.d / samba ExecStart = / usr / local / samba / sbin / samba ExecReload = / usr / bin / kill -HUP $ MAINPID [Install] WantedBy = multi-user.target root @ master: ~ # systemctl enable samba-ad-dc root @ master: ~ # reboot root @ master: ~ # systemctl status samba-ad-dc root @ master: ~ # systemctl status ntp
Samba 4 AD-DC file locations
ALL -minus the newly created samba-ad-dc.service- the files are in:
root @ master: ~ # ls -l / usr / local / samba / total 32 drwxr-sr-x 2 root staff 4096 Jun 19 11:55 bin drwxr-sr-x 2 root staff 4096 Jun 19 11:50 etc drwxr-sr-x 7 root staff 4096 Jun 19 11:30 includes drwxr-sr-x 15 root staff 4096 Jun 19 11:33 lib drwxr-sr-x 7 root staff 4096 Jun 19 12:40 private drwxr-sr-x 2 root staff 4096 Jun 19 11:33 sbin drwxr-sr-x 5 root staff 4096 Jun 19 11:33 share drwxr-sr-x 8 root staff 4096 Jun 19 12:28 var
in the best UNIX style. It is always advisable to browse through the different folders and examine their contents.
File /usr/local/samba/etc/smb.conf
root @ master: ~ # nano /usr/local/samba/etc/smb.conf # Global parameters [global] netbios name = MASTER realm = SWL.FAN workgroup = SWL dns forwarder = 8.8.8.8 server services = s3fs, rpc, nbt, wrepl, ldap, cldap, kdc, drepl, winbindd, ntp_signd, kcc, dnsupdate , dns server role = active directory domain controller allow dns updates = secure only idmap_ldb: use rfc2307 = yes idmap config *: backend = tdb idmap config *: range = 1000000-1999999 ldap server require strong auth = no printcap name = / dev / null [netlogon] path = /usr/local/samba/var/locks/sysvol/swl.fan/scripts read only = No [sysvol] path = / usr / local / samba / var / locks / sysvol read only = No root @ master: ~ # testparm Load smb config files from /usr/local/samba/etc/smb.conf Processing section "[netlogon]" Processing section "[sysvol]" Loaded services file OK. Server role: ROLE_ACTIVE_DIRECTORY_DC Press enter to see a dump of your service definitions # Global parameters [global] realm = SWL.FAN workgroup = SWL dns forwarder = 192.168.10.1 ldap server require strong auth = No passdb backend = samba_dsdb server role = active directory domain controller rpc_server: tcpip = no rpc_daemon: spoolssd = embedded rpc_server: spoolss = embedded rpc_server: winreg = embedded rpc_server: ntsvcs = embedded rpc_server: eventlog = embedded rpc_server: srvsvc = embedded rvcct_server = use external rvcct_server = use external rvcct_server = use external rvcct_server: external pipes = true idmap config *: range = 1000000-1999999 idmap_ldb: use rfc2307 = yes idmap config *: backend = tdb map archive = No map readonly = no store dos attributes = Yes vfs objects = dfs_samba4 acl_xattr [netlogon] path = / usr / local / samba / var / locks / sysvol / swl.fan / scripts read only = No [sysvol] path = / usr / local / samba / var / locks / sysvol read only = No
Minimal checks
root @ master: ~ # tool domain level show Domain and forest function level for domain 'DC = swl, DC = fan' Forest function level: (Windows) 2008 R2 Domain function level: (Windows) 2008 R2 Lowest function level of a DC: (Windows) 2008 R2 root @ master: ~ # ldapsearch -x -W root @ master: ~ # tool dbcheck Checking 262 objects Checked 262 objects (0 errors) root @ master: ~ # kinit Administrator Password for Administrator@SWL.FAN: root @ master: ~ # klist -f Ticket cache: FILE: / tmp / krb5cc_0 Primary default: Administrator@SWL.FAN Valid starting Expires Service main 19/06/17 12:53:24 19/06/17 22:53:24 krbtgt/SWL.FAN@SWL.FAN renew until 20/06/17 12:53:18 PM, Flags: RIA root @ master: ~ # kdestroy root @ master: ~ # klist -f klist: Credentials cache file '/ tmp / krb5cc_0' not found root @ master: ~ # smbclient -L localhost -U% Domain = [SWL] OS = [Windows 6.1] Server = [Samba 4.5.1] Sharename Type Comment --------- ---- ------- netlogon Disk sysvol Disk IPC $ IPC IPC Service (Samba 4.5.1) Domain = [SWL] OS = [Windows 6.1] Server = [Samba 4.5.1] Server Comment --------- ------- Workgroup Master ---- ----- ------- root @ master: ~ # smbclient // localhost / netlogon -UAdministrator -c 'ls' Enter Administrator's password: Domain = [SWL] OS = [Windows 6.1] Server = [Samba 4.5.1]. D 0 Mon Jun 19 11:50:52 2017 .. D 0 Mon Jun 19 11:51:07 2017 19091584 blocks of size 1024. 16198044 blocks available root @ master: ~ # tool dns serverinfo master -U administrator root @ master: ~ # host -t SRV _ldap._tcp.swl.fan _ldap._tcp.swl.fan has SRV record 0 100 389 master.swl.fan. root @ master: ~ # host -t SRV _kerberos._udp.swl.fan _kerberos._udp.swl.fan has SRV record 0 100 88 master.swl.fan. root @ master: ~ # host -t A master.swl.fan master.swl.fan has address 192.168.10.5 root @ master: ~ # host -t SOA swl.fan swl.fan has SOA record master.swl.fan. hostmaster.swl.fan. 1 900 600 86400 3600 root @ master: ~ # host -t NS swl.fan swl.fan name server master.swl.fan. root @ master: ~ # host -t MX swl.fan swl.fan has no MX record root @ master: ~ # samba_dnsupdate --verbose root @ master: ~ # tool user list Administrator krbtgt Guest root @ master: ~ # tool group list # The output is a bunch of groups. ;-)
We manage the newly installed Samba 4 AD-DC
If we want to modify the expiration in days of the Administrator password; the complexity of passwords; the minimum length of the password; the minimum and maximum duration -in days- of the password; and change the Administrator password declared during the Provisioning, we must execute the following commands with the values adjusted to your needs:
root @ master: ~ # tool
Usage: samba-tool Main samba administration tool. Options: -h, --help show this help message and exit Version Options: -V, --version Display version number Available subcommands: dbcheck - Check local AD database for errors. delegation - Delegation management. dns - Domain Name Service (DNS) management. domain - Domain management. drs - Directory Replication Services (DRS) management. dsacl - DS ACLs manipulation. fsmo - Flexible Single Master Operations (FSMO) roles management. gpo - Group Policy Object (GPO) management. group - Group management. ldapcmp - Compare two ldap databases. ntacl - NT ACLs manipulation. processes - List processes (to aid debugging on systems without setproctitle). rodc - Read-Only Domain Controller (RODC) management. sites - Sites management. spn - Service Principal Name (SPN) management. testparm - Syntax check the configuration file. time - Retrieve the time on a server. user - User management. For more help on a specific subcommand, please type: samba-tool (-h | --help)
root @ master: ~ # tool user setexpiry administrator --noexpiry
root @ master: ~ # tool domain passwordsettings set --min-pwd-length = 7
root @ master: ~ # tool domain passwordsettings set --min-pwd-age = 0
root @ master: ~ # tool domain passwordsettings set --max-pwd-age = 60
root @ master: ~ # tool user setpassword --filter = samaccountname = Administrator --newpassword = Passw0rD
We add several DNS records
root @ master: ~ # tool dns
Usage: samba-tool dns Domain Name Service (DNS) management. Options: -h, --help show this help message and exit Available subcommands: add - Add a DNS record delete - Delete a DNS record query - Query a name. roothints - Query root hints. serverinfo - Query for Server information. update - Update a DNS record zonecreate - Create a zone. zonedelete - Delete a zone. zoneinfo - Query for zone information. zonelist - Query for zones. For more help on a specific subcommand, please type: samba-tool dns (-h | --help)
Mail server
root @ master: ~ # tool dns add master swl.fan mail A 192.168.10.9 -U administrator root @ master: ~ # tool dns add master swl.fan swl.fan MX "mail.swl.fan 10" -U administrator
Fixed IP of other servers
root @ master: ~ # tool dns add master swl.fan sysadmin A 192.168.10.1 -U administrator root @ master: ~ # tool dns add master swl.fan fileserver A 192.168.10.10 -U administrator root @ master: ~ # tool dns add master swl.fan proxy A 192.168.10.11 -U administrator root @ master: ~ # tool dns add master swl.fan chat A 192.168.10.12 -U administrator
Reverse Zone
root @ master: ~ # tool dns zonecreate master 10.168.192.in-addr.arpa -U administrator Password for [SWL \ administrator]: Zone 10.168.192.in-addr.arpa created successfully root @ master: ~ # tool dns add master 10.168.192.in-addr.arpa 5 PTR master.swl.fan. -Uadministrator root @ master: ~ # tool dns add master 10.168.192.in-addr.arpa 9 PTR mail.swl.fan. -Uadministrator root @ master: ~ # tool dns add master 10.168.192.in-addr.arpa 1 PTR sysadmin.swl.fan. -Uadministrator root @ master: ~ # tool dns add master 10.168.192.in-addr.arpa 10 PTR fileserver.swl.fan. -Uadministrator root @ master: ~ # tool dns add master 10.168.192.in-addr.arpa 11 PTR proxy.swl.fan. -Uadministrator root @ master: ~ # tool dns add master 10.168.192.in-addr.arpa 12 PTR chat.swl.fan. -Uadministrator
Checks
root @ master: ~ # tool dns query master swl.fan mail ALL -U administrator Password for [SWL \ administrator]: Name =, Records = 1, Children = 0 A: 192.168.10.9 (flags = f0, serial = 2, ttl = 900) root @ master: ~ # host master master.swl.fan has address 192.168.10.5 root @ master: ~ # host sysadmin sysadmin.swl.fan has address 192.168.10.1 root @ master: ~ # host mail mail.swl.fan has address 192.168.10.9 root @ master: ~ # host chat chat.swl.fan has address 192.168.10.12 root @ master: ~ # proxy host proxy.swl.fan has address 192.168.10.11 root @ master: ~ # host fileserver fileserver.swl.fan has address 192.168.10.10 root @ master: ~ # host 192.168.10.1 1.10.168.192.in-addr.arpa domain name pointer sysadmin.swl.fan. root @ master: ~ # host 192.168.10.5 5.10.168.192.in-addr.arpa domain name pointer master.swl.fan. root @ master: ~ # host 192.168.10.9 9.10.168.192.in-addr.arpa domain name pointer mail.swl.fan. root @ master: ~ # host 192.168.10.10 10.10.168.192.in-addr.arpa domain name pointer fileserver.swl.fan. root @ master: ~ # host 192.168.10.11 11.10.168.192.in-addr.arpa domain name pointer proxy.swl.fan. root @ master: ~ # host 192.168.10.12 12.10.168.192.in-addr.arpa domain name pointer chat.swl.fan.
For the curious
root @ master: ~ # ldbsearch -H /usr/local/samba/private/sam.ldb.d/ \ DC = DOMAINDNSZONES, DC = SWL, DC = FAN.ldb | grep dn:
We add users
root @ master: ~ # tool user
Usage: samba-tool user User management. Options: -h, --help show this help message and exit Available subcommands: add - Create a new user. create - Create a new user. delete - Delete a user. disable - Disable an user. enable - Enable an user. getpassword - Get the password fields of a user / computer account. list - List all users. password - Change password for a user account (the one provided in authentication). setexpiry - Set the expiration of a user account. setpassword - Set or reset the password of a user account. syncpasswords - Sync the password of user accounts. For more help on a specific subcommand, please type: samba-tool user (-h | --help)
root @ master: ~ # tool user create strides Trancos01
User 'trancos' created successfully
root @ master: ~ # tool user create gandalf Gandalf01
User 'gandalf' created successfully
root @ master: ~ # tool user create legolas Legolas01
User 'legolas' created successfully
root @ master: ~ # tool user list
Administrator gandalf legolas strides krbtgt Guest
Administration through graphical interface or via web client
Visit wiki.samba.org for detailed information on how to install the Microsoft RSAT o Remote Server Administration Tools. If you do not require the classic policies offered by Microsoft Active Directory, you can install the package ldap-account-manager which offers a simple interface for administration through a web browser.
The Microsoft Remote Server Administration Tools (RSAT) program package is included on Windows Server operating systems.
We join the domain to a Windows 7 client named "seven"
As we do not have a DHCP server in the network, the first thing we must do is configure the client's network card with a fixed IP, declare that the primary DNS will be the IP of the samba-ad-dc, and check that the option "Register the address of this connection in DNS" is activated. It is not idle to check that the name «seven»Is not yet registered in the Samba Internal DNS.
After we join the computer to the domain and restart it, let's try to log in with the user «strides«. We will check that everything works OK. It is also recommended to check the Windows Client logs and check how the time is correctly synchronized.
Administrators with some Windows experience will find that any checks they do on the client will yield satisfactory results.
Summary
I hope the article is useful to Community readers. DesdeLinux.
Goodbye!
Long but detailed article, very good step by step on how to do everything.
I emphasize NIS, the truth is that although I know about its existence, I never really knew how it works, since to be honest it always gave me the impression that it was practically dead next to LDAP and Samba 4.
PS: Congratulations on your new personal project! A pity that you are not going to continue writing here, but at least there is a place to follow you.
Huge tutorial as always to my favorites, Greetings Fico.
Congratulations on the project.
The NIS section is great, I sympathize with Gonzalo Martinez, I knew it briefly but had no idea how to implement it and in what situations it is used.
Thank you once for a tremendous "trunk" of theoretical and practical article.
Finally new successes in your new project «gigainside».
Thank you very much everyone for comment!!!.
regards
the smb.conf that you show does not have any link with LDAP, is this on purpose or did I leave something?
mussol: This is a Samba 4 Active Directory Domain Controler that already has its built-in LDAP server.
Could you comment on how to unite a mac (apple) to a samba 4 AD-DC?
Thank you.
How are you;
Thanks for the manual, it's great. I have a question about a message that appears to me.
root @ AD: ~ # nping –tcp -p 53 -c 3 ad.rjsolucionessac.com
Failed to resolve given hostname / IP: ad.rjsolucionessac.com. Note that you can't use '/ mask' AND '1-4,7,100-' style IP ranges
Cannot find a valid target. Please make sure the specified hosts are either IP addresses in standard notation or hostnames that can be resolved with DNS
root @ AD: ~ #